Microsoft Details LemonDuck and LemonCat Monero-Mining Malware
Lemonade? No, we need LemonHelp
The Microsoft 365 Defender Threat Intelligence Team on Thursday published a detailed look at the LemonDuck and LemonCat malware used to mine the Monero cryptocurrency, among other things, after gaining access to vulnerable devices.
Microsoft said devices in "the United States, Russia, China, Germany, the United Kingdom, India, Korea, Canada, France, and Vietnam" are most frequently affected by LemonDuck. The malware exploits vulnerabilities in both Windows and Linux, too, which helps it cast as wide a net as possible in its search for potential victims.
LemonDuck isn't a novel threat—it's been active since at least 2019. Security companies like Trend Micro and Cisco Talos have followed it in the months since. Starting in January, however, there appeared to be two different versions of the malware that shared many characteristics but diverged in several notable ways.
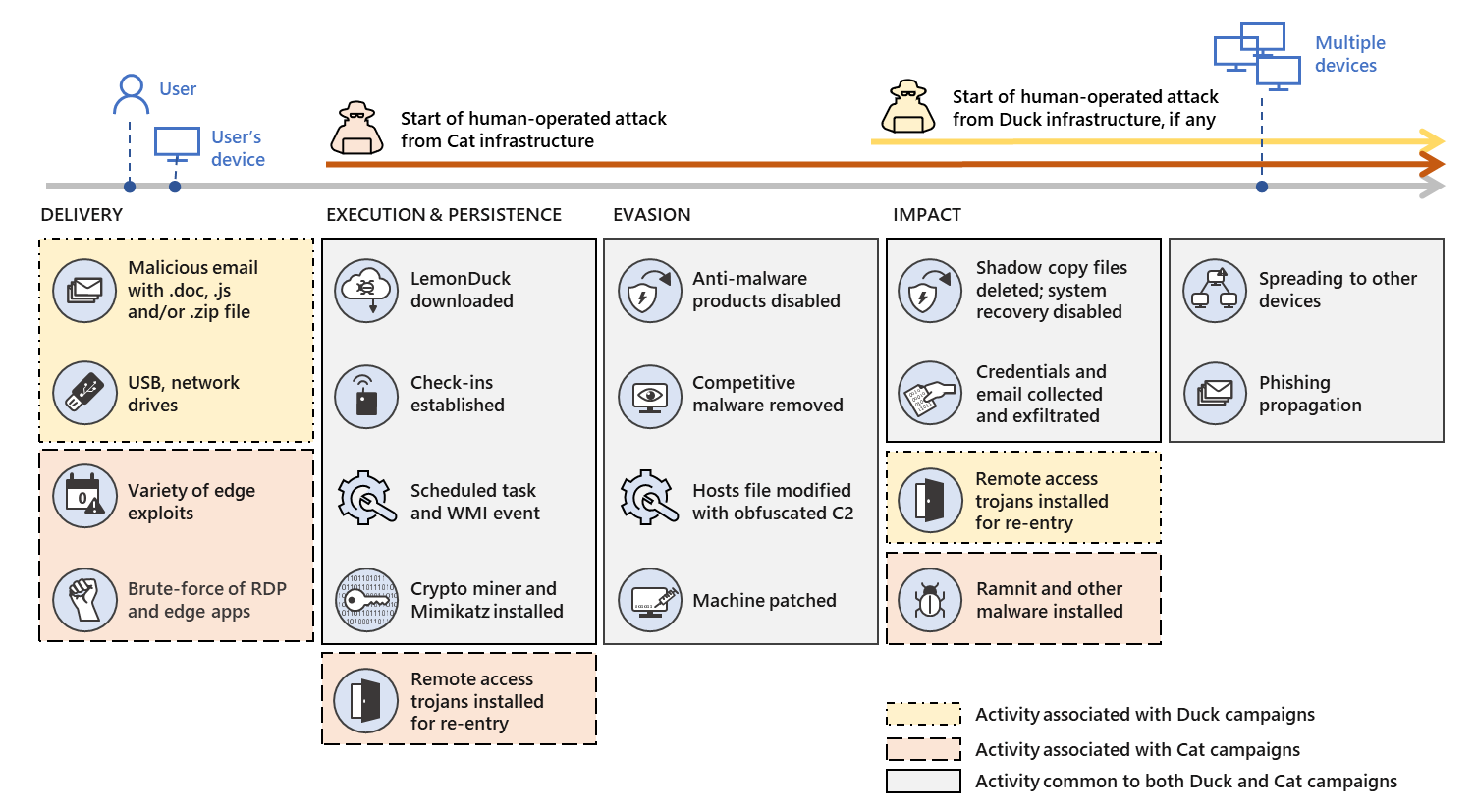
Microsoft said it's "aware of two distinct operating structures, which both use the LemonDuck malware but are potentially operated by two different entities for separate goals." It decided to keep the LemonDuck moniker for the first operating structure, but for the second, it decided a new name was in order. Meet LemonCat.
According to Microsoft the LemonCat infrastructure "is used in attacks that typically result in backdoor installation, credential and data theft, and malware delivery." That means attacks based on LemonCat are typically more dangerous than those based on LemonDuck, the company said, but that doesn't mean the latter are harmless.
LemonDuck and LemonCat also have many things in common. Microsoft said:
"The Duck and Cat infrastructures use similar subdomains, and they use the same task names, such as 'blackball'. Both infrastructures also utilize the same packaged components hosted on similar or identical sites for their mining, lateral movement, and competition-removal scripts, as well as many of the same function calls."
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The company also provided a graphic showing how LemonDuck and LemonCat compare to one another at various stages of the attack process:
Microsoft said it plans to publish a companion piece featuring "in-depth technical analysis of the malicious actions that follow a LemonDuck infection" along with "guidance for investigating LemonDuck attacks, as well as mitigation recommendations for strengthening defenses against these attacks," at some point.
But for now LemonDuck and LemonCat are noteworthy because of their broad reach, their ability to affect multiple operating systems, their methods of spreading across networks, and their continued operation long after their initial discovery. (Or at least the first publication detailing LemonDuck's method of attack.)
The malware could also have a notable impact on the hardware it infects. Cryptocurrency mining can affect the performance of other software, put additional strain on components, and lead to increased power usage. LemonDuck's operators get to receive the mined Monero without having to deal with those drawbacks.
So the best case scenario with a LemonDuck or LemonCat infection is that it causes hardware problems to mine Monero. That's better than the worst case—which leaves the system open to further exploits and steals information and credentials—but not by much. There's no lemonade to be made from these lemons.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.