New Windows Installer Zero-Day Exploit Is in the Wild
Following a security researcher's public disclosure of the vulnerability - and the means to exploit it.
A recently disclosed Microsoft Windows Installer zero-day vulnerability is now being explored by malware creators. Publicly disclosed by security researcher Abdelhamid Naceri on a Github post last Sunday, the vulnerability allows for local privilege escalation from user-level privileges up to SYSTEM level - the highest security clearance possible. According to the security researcher, this exploit works in all supporting versions of Windows - including fully-patched Windows 11 and Windows Server 2022 installations. Before posting the exploit on GitHub, Naceri first disclosed it to Microsoft and worked with the company to analyze the vulnerability.
Microsoft introduced a mitigation for the CVE-2021-41379 zero-day exploit in November 2021's Patch Tuesday - but apparently failed to remediate the issue completely. Naceri then took to his GitHub post to provide a proof-of-concept exploit of the vulnerability that works even after Microsoft's mitigations were applied.
For the more technically-minded, Naceri's exploit leverages the discretionary access control list (DACL) for Microsoft Edge Elevation Service - this allows an attacker to replace any executable file on the system with an MSI file - and to run code as an administrator. BleepingComputer has tested Naceri's exploit and was able to open a command prompt with SYSTEM permissions from an account with low-level 'Standard' privileges.
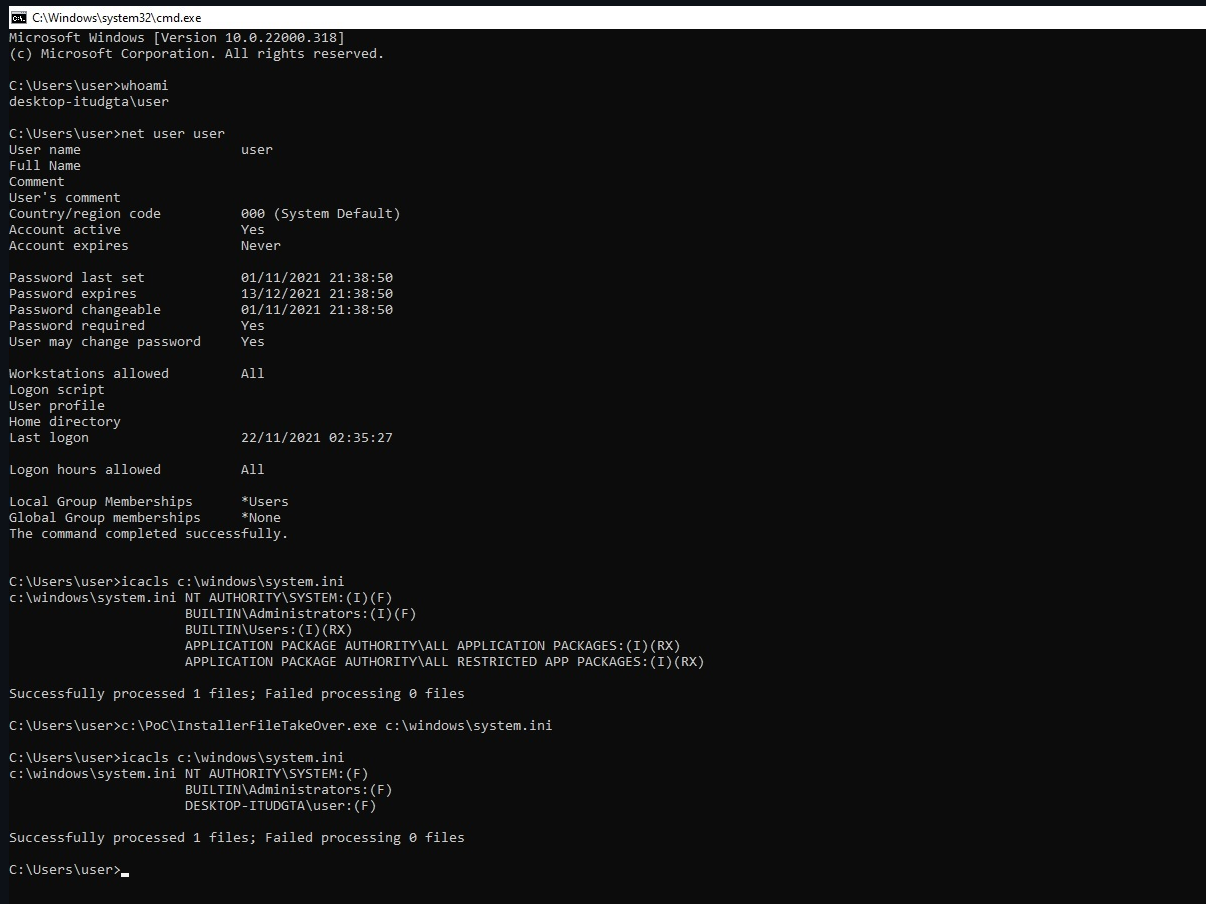
Cybersecurity company Cisco Talos has provided a statement about the exploit, reporting that they've already seen instances of malware in the wild that are currently attempting to exploit the flaws. As Cisco Talos' Head of Outreach Nick Biasini told BleepingComputer, these exploitation attempts seem to be focused on testing and tweaking the exploits as preparation for larger-scale attacks.
Naceri explained that "the proof of concept is extremely reliable and doesn't require anything, so it works in every attempt." When it comes to mitigations, however, the researcher passes the ball to Microsoft: "The best workaround available at the time of writing this is to wait [for] Microsoft to release a security patch, due to the complexity of this vulnerability," explained Naceri.
The researcher also mentioned that his work in circumventing Microsoft's CVE-2021-41379 patch attempts resulted in him finding two possible exploits: the disclosed one which we're reporting on here, and a second one that also triggers a unique behavior in the Windows Installer Service and allows for the same sort of privilege escalation technique. Naceri did say that he'll be waiting for Microsoft to completely patch the CVE-2021-41379 vulnerability before releasing the second exploit method.
On the issue, a Microsoft spokesperson told BleepingComputer that "We are aware of the disclosure and will do what is necessary to keep our customers safe and protected. An attacker using the methods described must already have access and the ability to run code on a target victim's machine." And while Microsoft initially classified this vulnerability as medium-severity (with a base CVSS score of 5.5, and a temporal score of 4.8), the fact that functional proof-of-concept code is already out in the wild and being actively exploited by malware developers should bolster the severity of the vulnerability and prompt a faster, more decisive fix from Microsoft.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Francisco Pires is a freelance news writer for Tom's Hardware with a soft side for quantum computing.
-
RodroX OMG!Reply
lol so tpm, secure boot and all that crap we have from Microsoft to install Windows 11 was basically for nothing. -
USAFRet Reply
TPM, or any other security measure, does not protect against everything.RodroX said:OMG!
lol so tpm, secure boot and all that crap we have from Microsoft to install Windows 11 was basically for nothing.
There will always be exploits. -
RodroX ReplyUSAFRet said:TPM, or any other security measure, does not protect against everything.
There will always be exploits.
Exactly my point. Forcing users, including some that may not have the expertise, to all the extra steps and probably issues and errors, just to enable something thats shouldn't be mandatory. -
USAFRet Reply
But....the TPM can ward off other issues.RodroX said:Exactly my point. Forcing users, including some that may not have the expertise, to all the extra steps and probably issues and errors, just to enable something thats shouldn't be mandatory.
Security is built in layers. TPM is one of those layers.
And given recent hardware, there are few if any 'hoops' to jump through for Win 11.
Given new hardware sold today, NO hoops at all. -
RodroX ReplyUSAFRet said:But....the TPM can ward off other issues.
Security is built in layers. TPM is one of those layers.
And given recent hardware, there are few if any 'hoops' to jump through for Win 11.
Given new hardware sold today, NO hoops at all.
An we could buy or use any TPM funcionality since when? years ago, same as secure boot.
Anyone who wanted to take advantage of both could do it, no need of Windows 11 either. But now they decided to make it mandatory. And yes I know there are works around. But still it shouldn't be.
This is just another move from MS to make people and business who may think this will keep their PCs and network safe, to go out and spend a lot of money on new hardware (with Win 11), when the weakest link in the security chain is always the user.
But yeah I agree with you 100%. But I been sick and mad about this for months. Because in the end this creates a false sense of security. -
Gillerer ReplyRodroX said:An we could buy or use any TPM funcionality since when? years ago, same as secure boot.
Anyone who wanted to take advantage of both could do it, no need of Windows 11 either. But now they decided to make it mandatory. And yes I know there are works around. But still it shouldn't be.
This is just another move from MS to make people and business who may think this will keep their PCs and network safe, to go out and spend a lot of money on new hardware (with Win 11), when the weakest link in the security chain is always the user.
But yeah I agree with you 100%. But I been sick and mad about this for months. Because in the end this creates a false sense of security.
I'd rather think it's more a move by Microsoft to make a clean break and clearly distinguish between the
"does not require TPM" era Windows 10 and
"does require TPM" era Windows 11among other more noticeable changes that also took place. (Also the shiny "new" thing to use for marketing new computers, which helps make MS's partners happy.)
Having a completely new Windows version is much easier to communicate to customers - going as far as having "Windows 11" stickers on new products. Computer manufacturers also have easier time announcing "support for Windows 11" on a recent laptop than some obscure version of Windows 10.
Imagine having to check the version number... "'21H1' - what is that?" Most people have never even heard about it, paid any attention, or were overwhelmed enough the update process to not be able to absorb it. -
RodroX ReplyGillerer said:I'd rather think it's more a move by Microsoft to make a clean break and clearly distinguish between the
"does not require TPM" era Windows 10 and
"does require TPM" era Windows 11among other more noticeable changes that also took place. (Also the shiny "new" thing to use for marketing new computers, which helps make MS's partners happy.)
Having a completely new Windows version is much easier to communicate to customers - going as far as having "Windows 11" stickers on new products. Computer manufacturers also have easier time announcing "support for Windows 11" on a recent laptop than some obscure version of Windows 10.
Imagine having to check the version number... "'21H1' - what is that?" Most people have never even heard about it, paid any attention, or were overwhelmed enough the update process to not be able to absorb it.
Of course is easy to sell. Whatever the "end" is/was, the result is the same, more money for them. You can use TPM and Secureboot on Win 10 (unless you own a really old PC without a TPM chip or compatible CPU with its funcionality), no need for 11.
We have over 4000 PC at work they all support and already have TPM and Secure Boot enable (been that way for years). Im just mad people with no knowladge gets the wrong idea about this kind of stuff and may feel secure, when they are not. -
USAFRet Reply
There is no 100% secure. Never has been, never will be.RodroX said:Im just mad people with no knowladge gets the wrong idea about this kind of stuff and may feel secure, when they are not.
TPM is one added layer in this security realm. -
wifiburger omg are you telling me TPM, VBS and all that garbage didn't help Windows 11 here ?Reply
I'm shocked ! ... not -
wifiburger ReplyUSAFRet said:There is no 100% secure. Never has been, never will be.
TPM is one added layer in this security realm.
there's not much "TPM" security layer in Windows 11
hello login (webcam), disk encryption & secure boot... yeah not much help there for protection against exploits once your OS is already booted / working !