Researchers Use Ambient Light Sensors To Steal Browser Data
Security researchers have discovered that ambient light sensors used in smartphones, laptops, and tablets can be used to steal browser data. Normally, light sensors are used to detect the level of surrounding light to automatically adjust screen brightness to save battery life, but due to the fact that most mobile apps and websites don’t need to ask permission to access many of the sensors in your device, sensitive information such as browsing history, touch actions, and PINs are at risk.
The attack works in current versions of Chrome, Firefox, Android, and laptop computers with light sensors (such as the MacBook Pro) by taking advantage of a design flaw in a special API developed by the World Wide Web Consortium (W3C) that allows websites to interact with ambient light sensors through a browser without the need for user permission. Security researchers were able to use ambient light sensors to detect the color of links in your browsing history, allowing attackers to determine if a link has been visited or not. This makes it possible for malicious sites to violate the same-origin policy, steal cross-origin data, and extract information about the user’s browser history.
Privacy expert Lukasz Olejnik, lead researcher on the project stated:
This research was spurred by a recent W3C discussion about the generic sensor API, where one of the leading proposals posits that access to certain sensor data should not require asking the user for permission. As a response, we decided to investigate the malicious potential behind ambient light sensors.
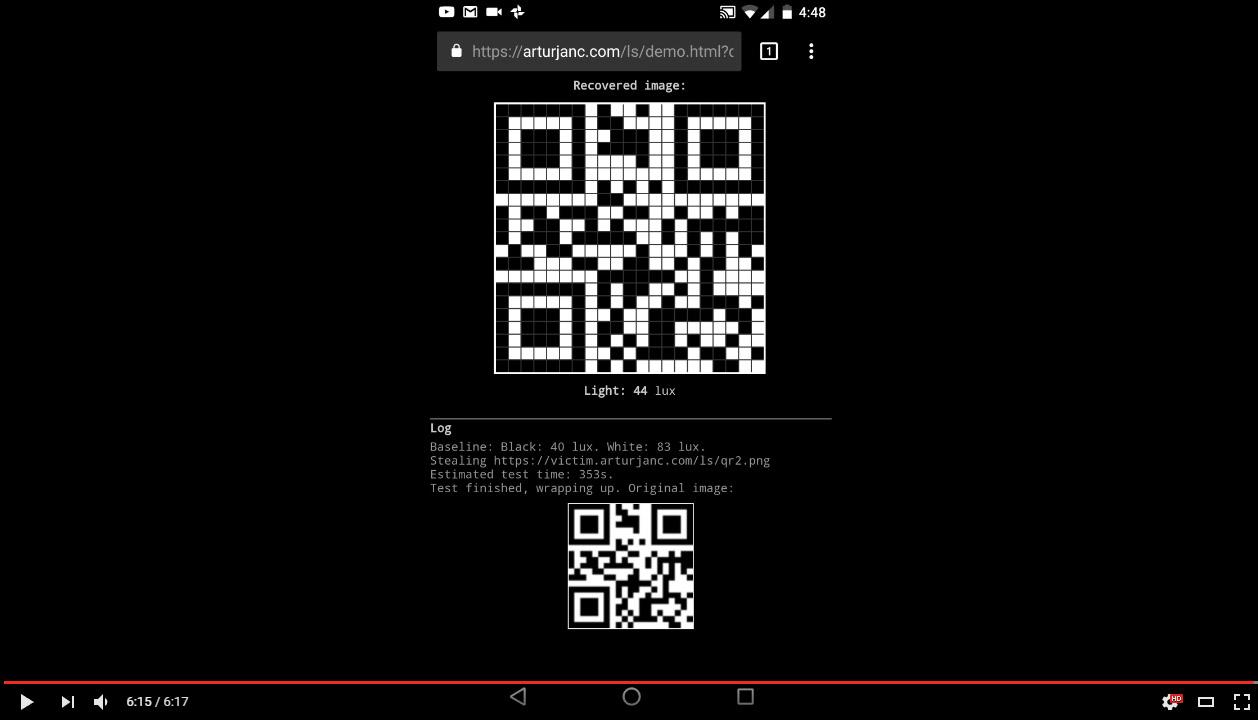
Olejnik went on to say that that attackers can essentially discover how a given site or image looks for the attacked user allowing the exfiltration of all image resources and data from any document. This makes it possible to hijack a victim's account from sites that use QR codes for account recovery.
Most troubling is the fact that just last month the Google Chrome team proposed that most sensors, including ambient light sensors, accelerometers, and gyroscopes, should be exempt from the browser permissions system. This means that websites wouldn't be required to seek user permission before accessing the any of the sensors on your device.
Fortunately there is a silver lining: Mitigating this attack is rather easy, as it requires only the W3C and browser makers to limit the frequency of sensor readings and the precision of sensor output. This wouldn't prevent the attack, but as the report noted, it would make it far more difficult to conduct in real word scenarios.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Steven Lynch is a contributor for Tom’s Hardware, primarily covering case reviews and news.
-
LORD_ORION Figures Google would want an exemption, obviously they figured this out and went the path of stealing your data for monetization purposes, rather than security disclosure.Reply -
bit_user Reply
That makes no sense! Google already has your data. They should want to make it harder for other people to get your data, to make the data they have on you more valuable. Anyway, this isn't about data collection for marketing purposes - this is sort of like a more sophisticated phishing scam.19594629 said:Figures Google would want an exemption, obviously they figured this out and went the path of stealing your data for monetization purposes, rather than security disclosure.
If you want to be cynical about this, you could say that google is trying to make web apps less secure, in order to make android seem less bad. Though, I don't really think that's their motivation. I think they just felt it was harmless enough, and wanted web developers to be able to take advantage of these things. -
LORD_ORION It makes perfect sense if they can simply adjust your sensors and get a hit of your locked down browsing habits whenever you are doing something they are interested in.Reply -
TadashiTG Why would the browser need these sensors in the first place? Permission should be denied by default.Reply -
Gilles_2 after reading the original articleReply
all we can see is that with this sensor, the website can very slowly steal information, so slowly that any normal user would have close that damn page already