New attack SLAMs into existing and future AMD, Intel and Arm CPUs
New memory allocation method, new problems!

A group of researchers at VUSec from Vrije Universiteit Amsterdam, specializing in system and network security, have discovered a new type of side-channel attack called SLAM (via Bleeping Computer). This attack can evade the security features of the latest-generation — and upcoming — CPUs by Intel, AMD, and Arm. SLAM can bypass the processor's security functions and access the root password from the kernel memory.
LAM, a term used by Intel for this kind of attack, stands for Linear Address Masking. Arm dubbed it Top Byte Ignore (TBI), and AMD calls it Upper Address Ignore (UAI), but all three implement the same function differently.
According to the white paper, LAM, UAI, and TBI provide faster security for the physical memory and manage it from the CPU. Intel explains that LAM is an extension that allows the software to locate metadata in data pointers and dereference them without the need to mask the metadata bits. This feature isn't new, but SLAM targets newer chips, using certain paging levels used in newer CPUs, a type of allocation managing method for the system's physical memory. Consequently, these CPUs ignore this attack method and exploit the same paging method. That's why it's called SLAM, which is short for Spectre-based on LAM.
How does the attack work?
SLAM relies upon a memory feature in these CPUs that enables software to store untranslated bits in 64-bit linear addresses in the kernel's metadata. It then uses a new transient execution process by exploring a set of unmasked instructions, dubbed "gadgets" in software code.
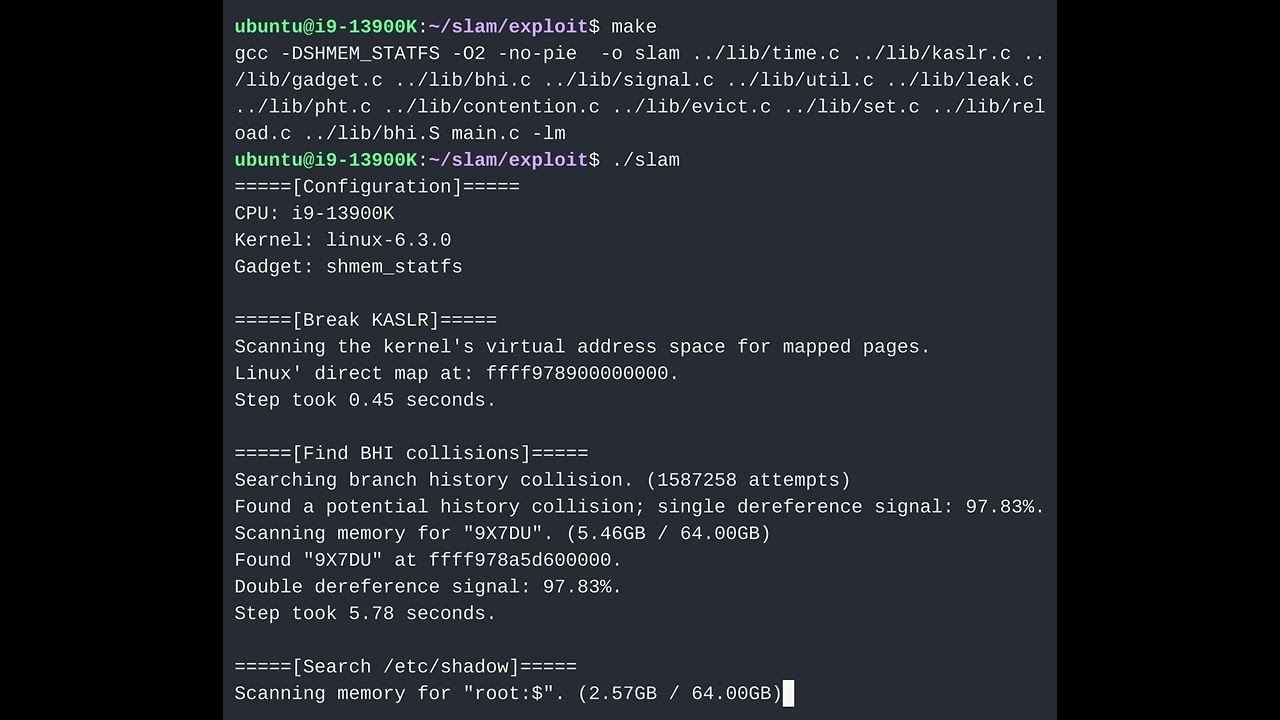
The attacker will need to use a target system code that interacts with these gadgets, which then uses a set of algorithms to extract sensitive information such as root passwords and other encryption keys from the kernel memory. This was demonstrated on an Intel Core i9-13900K-based system running on Linux 6.3.0 kernel. The research paper also shows testing was done on systems with AMD Ryzen 7 2700X CPUs.
VUSec researchers pointed out CPUs by all three vendors using their respective paging levels:
- Existing AMD CPUs vulnerable to CVE-2020-12965
- Sierra Forest, Grand Ridge, Arrow Lake, and Lunar Lake Intel CPUs supporting LAM (both 4- and 5-level paging)
- Future AMD CPUs supporting UAI and 5-level paging
- Future Arm CPUs supporting TBI and 5-level paging
The researchers also pointed out that the method of targeting unmasked gadgets is common with software and, hence, is usually exploited to gain arbitrary ASCII Kernel data. What makes this attack any different is that the new CPUs lack strong canonicality checks in the new paging levels and hence bypass any CPU level security. They were able to find multiple exploitable gadgets in the Linux Kernel as they made a scanner specifically for this purpose.
The industry responds to SLAM
Currently, this exploit is CPU agnostic but is shown to work only on Linux, which has already created a patch to disable LAM by default until further guidance is available. ARM published an advisory explaining there's no need to implement further action against SLAM as it can already fend off attacks. AMD told VUSec that it also didn't need to provide any updates as it said its Spectre V2 mitigations address SLAM attacks.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Intel told VUSec that it contacted potentially affected software vendors and made plans to provide software guidance before the future release of Intel CPUs that support LAM. It requires the vendor to deploy a feature using Linear Address Space Separation (short for LASS) extension to prevent any such access through the Kernel.
This is the second hardware-level exploit found this week that ignores CPU security instruction sets. Many such attacks, while found to be hardware-level exploits, either work on certain operating systems or are platform agnostic. While such research is usually addressed very quickly, it becomes imperative that the respective vendor respond accordingly, which is mentioned in the whitepaper. Of course, usually, such exploits rely on the deployment method to execute such attacks. While this type of attack doesn't exist yet, it has a vulnerability. Regardless of how this can be installed on the user's system, it must be patched.
VUSec made the code and data for users to reproduce SLAM attacks in its GitHub repository.

Roshan Ashraf Shaikh has been in the Indian PC hardware community since the early 2000s and has been building PCs, contributing to many Indian tech forums, & blogs. He operated Hardware BBQ for 11 years and wrote news for eTeknix & TweakTown before joining Tom's Hardware team. Besides tech, he is interested in fighting games, movies, anime, and mechanical watches.
-
ezst036 Does anybody (website) track when CPU exploits and side attacks get resolved in hardware?Reply -
Findecanor I am getting a bit appalled by the sheer number of security vulnerabilities in hardware that have cropped up.Reply
Back when Spectre and Meltdown were divulged to the public back in Jan 2018, that was seen as an anomaly. Few people expected that it was just the start of a seemingly endless stream of new vulnerabilities being divulged every few months. -
Amdlova Reply
People who uses tinfoil hat. Try https://www.bleepingcomputer.com/ezst036 said:Does anybody (website) track when CPU exploits and side attacks get resolved in hardware? -
ezst036 Reply
I did not see a list or a table of CPUs and corresponding known attacks/exploits.Amdlova said:People who uses tinfoil hat. Try https://www.bleepingcomputer.com/
Is there a more specific URL? -
steviejay Reply
Only by threat vector.ezst036 said:I did not see a list or a table of CPUs and corresponding known attacks/exploits.
Is there a more specific URL?
Intel security center or AMD security will list advisories but it’s up to you to determine if your CPU is affected by drilling down into the detail.