Intel AMT Vulnerability Shows Intel’s Management Engine Can Be Dangerous
Intel published a security advisory about a vulnerability that affects Active Management Technology (AMT), Intel Standard Manageability (ISM), and Intel Small Business Technology (SBT) software. The company also released detection and mitigation guides, but the firmware updates would have to come from OEMs. The vulnerability shows that Intel ME's out-of-bound functionality, such as installing software remotely on PCs, could pose serious dangers to systems, as some free software activists have already warned.
Intel ME And AMT
Intel’s Management Engine (ME) is a separate computing environment working on Intel’s chips that comes with its own separate processor, whereas AMT is the software that provides the ME functionality to system administrators. According to some researchers, the ME has access to “everything,” including network, memory, and the cryptography engine. AMT and ME can also be accessed remotely, which Intel has argued that is a feature of its processors:
Intel Active Management Technology (Intel AMT) allows IT or managed service providers to better discover, repair, and protect their networked computing assets. Intel AMT enables IT or managed service providers to manage and repair not only their PC assets, but workstations and entry servers as well, utilizing the same infrastructure and tools across platforms for management consistency. For embedded developers, this means that devices can be diagnosed and repaired remotely, ultimately lowering IT support costs.
All of this has led free software activists, such as those working on Libreboot (a free software alternative to UEFI), to brand it a “backdoor.” Even without considering it a backdoor, the Libreboot founder has argued that the capabilities of Intel ME can be exploited by others once vulnerabilities in it are found:
Intel Management Engine with its proprietary firmware has complete access to and control over the PC: it can power on or shutdown the PC, read all open files, examine all running applications, track all keys pressed and mouse movements, and even capture or display images on the screen.And it has a network interface that is demonstrably insecure, which can allow an attacker on the network to inject rootkits that completely compromise the PC and can report to the attacker all activities performed on the PC. It is a threat to freedom, security, and privacy that can't be ignored.
AMT Vulnerability And Mitigations
A vulnerability was found earlier this year by Maksim Malyutin from Embedi that affects Intel’s AMT, the software that runs in the ME environment, as well as ISM and Intel SBT versions 6.x through 11.6.
The vulnerability allows privilege escalation on a user’s machine, and it could be exploited by attackers to take over and possibly even decrypt encrypted hardware (unless the PC comes with a TPM chip). The vulnerability affects all Intel chips from 2008 up to the latest Intel Kaby Lake generation.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Intel said that this particular vulnerability doesn’t affect consumer chips. However, free software activists’ arguments about Intel ME’s dangers in general likely hold true, as this vulnerability may not be the only one out there that exists or that Intel is willing to make public. SemiAccurate said yesterday that it told Intel about this vulnerability more than five years ago, but it was mostly ignored by Intel executives. Intel didn’t confirm whether or not this is true.
Enterprise customers are affected as described below:
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel Active Management Technology (AMT) and Intel Standard Manageability (ISM).An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel Active Management Technology (AMT), Intel Standard Manageability (ISM), and Intel® Small Business Technology (SBT)
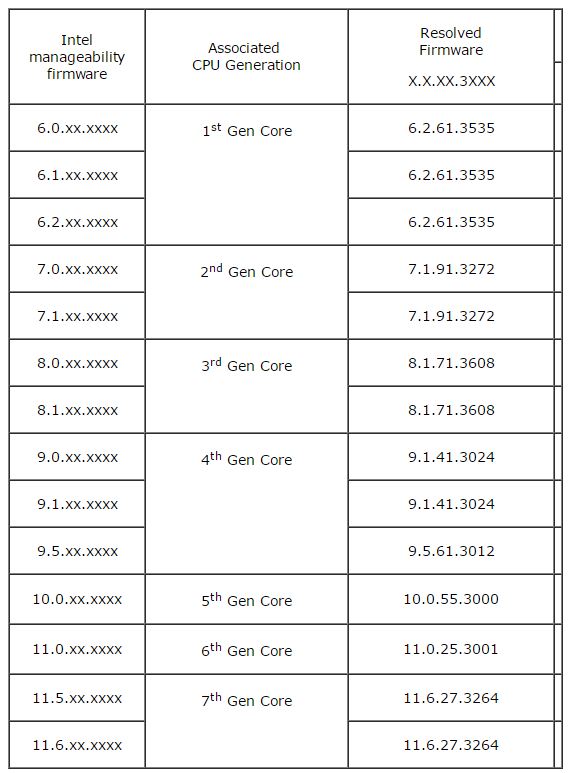
Intel released a detection guide so you can see if your company’s machines are affected by the vulnerability. You can also check in the table below to see which versions of the SBT firmware versions are impacted and which resolve the issue.
The main problem may be that the firmware needs to be released by the makers of those computers, and some of them may not release firmware updates for machines that are more than a few years old. In that case, you may want to follow Intel’s mitigation guide for how to protect your computers against exploits that use this vulnerability.
Intel ME’s Future In Question
The free software and Linux communities, as well as some companies such as Purism, have been working on ways to disable the Intel ME and AMT software, with some degree of success. Mainly, it’s difficult to fully disable Intel ME because, it seems, Intel designed it that way; usually, if you try to hack and disable the ME, the computer will shut down.
If Intel redesigned the ME environment on its chips, it should be possible to allow users to easily and completely disable Intel ME. If the company decides against that, it may be less of a technical decision and more of a political and strategic one. Intel may not want to give up on certain CPU features that the company may consider mandatory, such as DRM.
The free software community has also lately been encouraging AMD to open source the firmware for its ARM-based Platform Security Processor (PSP), which is the equivalent to Intel’s ME. It’s not clear whether or not open sourcing the firmware would actually fix any of the dangers these types of environments pose, but it may be a step in the right direction. It could also be a strategic advantage for AMD, if Intel continues to ignore these concerns.
Tom’s Hardware asked Intel if it plans to alleviate these concerns in any way in the future (such as by creating ME-less chips, as Purism has proposed), but we haven't yet received a response.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
genz This sounds like the perfect backdoor for government agencies and hackers imo. I would disable it on any internet connected.Reply -
jimmysmitty Reply19637505 said:So basically iDRAC for intel machines.
In essence, yes. It also has management features.
Intel said that this particular vulnerability doesn’t affect consumer chips. However, free software activists’ arguments about Intel ME’s dangers in general likely hold true, as this vulnerability may not be the only one out there that exists or that Intel is willing to make public.
The free software activists need to do more research before claiming this.
The reason consumer chips are not affected is because consumer chips do not come with vPro which is the component that allows for connections anyways. AMT is part of all systems but not every feature is part of every system.
I have done this on past articles but will do it again and I think the author of the article should as well as all this does is get people into frenzies and they start to spread rumors which are not true.
vPro, the ability to connect remotely to an Intel platform, is required to be supported on 3 components; the CPU, chipset and NIC. Lets look at consumer grade chipsets first:
Consumer:
Z270 - No vPro
H270 - No vPro
Business:
Q270 - vPro
Q250 - No vPro
B250 - No vPro
So in order for a new PC to even begin to support all of AMT and even worry about this potential risk, you need to have a business chipset and a top end one at that, the Q270.
Then we have the CPU. The most common consumer chip that we buy, the i7 7700K or i5 7600K, do not support vPro. The 7700/7700T do and are more normally found in business PCs.
Last we have the NIC. In the consumer realm it is a mix. Most boards have an Intel NIC but some have a KILLER NIC while others will have a Realtek NIC. Of the consumer boards they almost all use the I219-V which does not support vPro, that is the I219-LM.
The majority of people here will get either a H270 or Z270 chipset, alone which kills vPro, a K series CPU and a board with a I219-V NIC or other brand NIC thus disabling vPro from working at all.
In short, the majority of consumers will not have vPro which disables remote access via Intels AMT.
On the business side it is important to note however there are always other security measures a good network should have in place. Honestly I doubt it will be a major issue as not many IT networks utilize vPro, the majority use iDRACs for the servers (which have their own vulnerabilities) and go on site to diagnose hardware related issues.
-
problematiq Sweet you can enable it remotely. just require a signed cert with one of the trusted hashes. go-daddy certs work.Reply -
genz Reply19637665 said:19637505 said:So basically iDRAC for intel machines.
In essence, yes. It also has management features.
Intel said that this particular vulnerability doesn’t affect consumer chips. However, free software activists’ arguments about Intel ME’s dangers in general likely hold true, as this vulnerability may not be the only one out there that exists or that Intel is willing to make public.
The free software activists need to do more research before claiming this.
The reason consumer chips are not affected is because consumer chips do not come with vPro which is the component that allows for connections anyways. AMT is part of all systems but not every feature is part of every system.
For Wikipedia: Intel vPro technology is an umbrella marketing term used by Intel for a large collection of computer hardware technologies, including Hyperthreading, Turbo Boost 3.0, VT-x, VT-d, Trusted Execution Technology (TXT), and Intel Active Management Technology (AMT). When the vPro brand was launched (circa 2007), it was identified primarily with AMT, thus some journalists still consider AMT to be the essence of vPro.
The only component missing from vPro in modern systems is TXT, which is absent because most modern systems don't have a Trusted Platform Module. Either way, it's pretty irrelevant to the functionality of AMT as AMT operates out-of-band and in hardware... falsifying an AMT node would require fabrication on the nm scale (pretty much govt only), and if it did tie into TPM tech, well that crypto was beaten back in 2010. TPM 2.0 was actually designed with a backdoor to govt in the first place. See: http://investmentwatchblog.com/leaked-german-government-warns-key-entities-not-to-use-windows-8-links-the-nsa/
19637665 said:I have done this on past articles but will do it again and I think the author of the article should as well as all this does is get people into frenzies and they start to spread rumors which are not true.
vPro, the ability to connect remotely to an Intel platform, is required to be supported on 3 components; the CPU, chipset and NIC. Lets look at consumer grade chipsets first:
Consumer:
Z270 - No vPro
H270 - No vPro
Business:
Q270 - vPro
Q250 - No vPro
B250 - No vPro
So in order for a new PC to even begin to support all of AMT and even worry about this potential risk, you need to have a business chipset and a top end one at that, the Q270.
Wrong. Firstly vPro is a practically meaningless brand-name spec on its own, all the other things you are stating are AMT. vPro support is deliberately disabled in some CPU's to sell others, yes, but other than that vPro is not itself a tangible technology or hardware, rather a software capability based on a few pieces of hardware and a SoC of sorts on the CPU that runs when the PC is off. Said SoC exists on EVERY Core i and Xeon CPU since Sandy Bridge. The question is whether it will speak to you or not (and thus your management application). Either way, it's an incredibly large and untraceable potential backdoor as should the SoC be possible to activate sans TPM, it would allow complete and untraceable access to every Intel CPU since the Sandy Bridge era.
http://www.intel.co.uk/content/www/uk/en/products/processors/core/core-vpro.html
https://forum-en.msi.com/index.php?topic=285449.0 <---- Has Z270 TPM socket as an example and full vPro compliance.
The reason why all these processors support vPro is the existence of TPM socket headers on many consumer motherboards. This header is the difference between full vPro support and none if you look at the rest of the spec. It looks like this and is even present on mobile devices. http://www.laptopmag.com/images/wp/purch-api/incontent/2016/06/51y1v71qrwl.jpg
19637665 said:
Then we have the CPU. The most common consumer chip that we buy, the i7 7700K or i5 7600K, do not support vPro. The 7700/7700T do and are more normally found in business PCs.
Binning. And marketing. No sense assisting the creation of overclocked consumer hardware server farms.
19637665 said:Last we have the NIC. In the consumer realm, it is a mix. Most boards have an Intel NIC but some have a KILLER NIC while others will have a Realtek NIC. Of the consumer boards they almost all use the I219-V which does not support vPro, that is the I219-LM.
It's not a mix at all, it's a monopoly. Intel desktop e1000 variants make up well over 60% of the market alone. I've never owned a non-intel NIC in an Intel PC. It's only in laptops and AMD PCs that stregnth weakens as multifeature Bluetooth/Wi-Fi/ethernet chips from Boardcom and Realtek start to make more sense.
For you and I maybe. That is small comfort for me. I may be locked out, but the decades of warez around the world suggests that I am not the greatest unlocker of these things.19637665 said:The majority of people here will get either a H270 or Z270 chipset, alone which kills vPro, a K series CPU and a board with a I219-V NIC or other brand NIC thus disabling vPro from working at all.
In short, the majority of consumers will not have vPro which disables remote access via Intels AMT.
-
PC-Cobbler This was another good article from Lucian. However, he omitted three important points. First, only processors that support vPro are vulnerable to AMT. Second, only Q-chipsets are fully vulnerable to AMT. And third, ME software is optional on all pre-10 Windows OS, though W-8.1 considers it to be an important update.Reply
Intel believes that AMT is above the malware scrum, with one senior Intel engineer declaring that "there is still a lot of AMT misinterpretation and FUD there."
https://communities.intel.com/thread/104419 -
jimmysmitty Reply19638046 said:19637665 said:19637505 said:So basically iDRAC for intel machines.
In essence, yes. It also has management features.
Intel said that this particular vulnerability doesn’t affect consumer chips. However, free software activists’ arguments about Intel ME’s dangers in general likely hold true, as this vulnerability may not be the only one out there that exists or that Intel is willing to make public.
The free software activists need to do more research before claiming this.
The reason consumer chips are not affected is because consumer chips do not come with vPro which is the component that allows for connections anyways. AMT is part of all systems but not every feature is part of every system.
For Wikipedia: Intel vPro technology is an umbrella marketing term used by Intel for a large collection of computer hardware technologies, including Hyperthreading, Turbo Boost 3.0, VT-x, VT-d, Trusted Execution Technology (TXT), and Intel Active Management Technology (AMT). When the vPro brand was launched (circa 2007), it was identified primarily with AMT, thus some journalists still consider AMT to be the essence of vPro.
The only component missing from vPro in modern systems is TXT, which is absent because most modern systems don't have a Trusted Platform Module. Either way, it's pretty irrelevant to the functionality of AMT as AMT operates out-of-band and in hardware... falsifying an AMT node would require fabrication on the nm scale (pretty much govt only), and if it did tie into TPM tech, well that crypto was beaten back in 2010. TPM 2.0 was actually designed with a backdoor to govt in the first place. See: http://investmentwatchblog.com/leaked-german-government-warns-key-entities-not-to-use-windows-8-links-the-nsa/
19637665 said:I have done this on past articles but will do it again and I think the author of the article should as well as all this does is get people into frenzies and they start to spread rumors which are not true.
vPro, the ability to connect remotely to an Intel platform, is required to be supported on 3 components; the CPU, chipset and NIC. Lets look at consumer grade chipsets first:
Consumer:
Z270 - No vPro
H270 - No vPro
Business:
Q270 - vPro
Q250 - No vPro
B250 - No vPro
So in order for a new PC to even begin to support all of AMT and even worry about this potential risk, you need to have a business chipset and a top end one at that, the Q270.
Wrong. Firstly vPro is a practically meaningless brand-name spec on its own, all the other things you are stating are AMT. vPro support is deliberately disabled in some CPU's to sell others, yes, but other than that vPro is not itself a tangible technology or hardware, rather a software capability based on a few pieces of hardware and a SoC of sorts on the CPU that runs when the PC is off. Said SoC exists on EVERY Core i and Xeon CPU since Sandy Bridge. The question is whether it will speak to you or not (and thus your management application). Either way, it's an incredibly large and untraceable potential backdoor as should the SoC be possible to activate sans TPM, it would allow complete and untraceable access to every Intel CPU since the Sandy Bridge era.
http://www.intel.co.uk/content/www/uk/en/products/processors/core/core-vpro.html
https://forum-en.msi.com/index.php?topic=285449.0 <---- Has Z270 TPM socket as an example and full vPro compliance.
The reason why all these processors support vPro is the existence of TPM socket headers on many consumer motherboards. This header is the difference between full vPro support and none if you look at the rest of the spec. It looks like this and is even present on mobile devices. http://www.laptopmag.com/images/wp/purch-api/incontent/2016/06/51y1v71qrwl.jpg
19637665 said:
Then we have the CPU. The most common consumer chip that we buy, the i7 7700K or i5 7600K, do not support vPro. The 7700/7700T do and are more normally found in business PCs.
Binning. And marketing. No sense assisting the creation of overclocked consumer hardware server farms.
19637665 said:Last we have the NIC. In the consumer realm, it is a mix. Most boards have an Intel NIC but some have a KILLER NIC while others will have a Realtek NIC. Of the consumer boards they almost all use the I219-V which does not support vPro, that is the I219-LM.
It's not a mix at all, it's a monopoly. Intel desktop e1000 variants make up well over 60% of the market alone. I've never owned a non-intel NIC in an Intel PC. It's only in laptops and AMD PCs that stregnth weakens as multifeature Bluetooth/Wi-Fi/ethernet chips from Boardcom and Realtek start to make more sense.
For you and I maybe. That is small comfort for me. I may be locked out, but the decades of warez around the world suggests that I am not the greatest unlocker of these things.19637665 said:The majority of people here will get either a H270 or Z270 chipset, alone which kills vPro, a K series CPU and a board with a I219-V NIC or other brand NIC thus disabling vPro from working at all.
In short, the majority of consumers will not have vPro which disables remote access via Intels AMT.
Instead of using Wikipedia I will use a direct quote from Intel:
http://www.intel.com/content/www/us/en/architecture-and-technology/intel-active-management-technology.html
While vPro is a more blanket term now it was originally the term coined for its remote management system and still covers it. That's why I focus on vPro and not AMT. AMT is still in the CPUs but vPro has to have full support and the majority of consumer PCs will not have vPro on them. It also has to have the other end active in order to work. It is almost like RDP in that the PC has to allow it and the server has to support it.
This is an old video but this is when vPro was first introduced: https://www.youtube.com/watch?v=bBuhg4IAB3o
I am not wrong though. Systems without vPro cannot work with vPro. Again vPro is what Intel calls it and AMT is part of it. Me using the term does not make it wrong.
https://ark.intel.com/products/98089/Intel-Z270-Chipset ,_ Per Intel that chipsert does not support vPro
Just because YOU have not had anything but an Intel NIC does not mean there is not a mix. Have you don computer repair? Because I have. And Realtek is in a ton of consumer OEM systems as it is cheaper than the Intel NIC. Slower but cheaper. Look up the drivers for the Dell Inspiron 3668. That is what would be the common Dell desktop. It has a Realtek NIC.
And 60% is not a monopoly, although I can't find anything on how much any one company has with that. A real monopoly is what Intel has in the server market, which is over 90%. But to be fair AMD didn't present much competition there.
My entire point was that the majority of consumers have no worries unless they bought a business class desktop for some reason. Even then there is more to it as it has to be activated from both ends with a secure key to even start working. The "Free Software Group" failed to state this and thinks otherwise. -
Outernational Here's a concise, plain English guide on how to follow the mitigation steps: https://mattermedia.com/blog/disabling-intel-amt/Reply -
genz Reply19643087 said:19638046 said:19637665 said:19637505 said:So basically iDRAC for intel machines.
In essence, yes. It also has management features.
Intel said that this particular vulnerability doesn’t affect consumer chips. However, free software activists’ arguments about Intel ME’s dangers in general likely hold true, as this vulnerability may not be the only one out there that exists or that Intel is willing to make public.
The free software activists need to do more research before claiming this.
The reason consumer chips are not affected is because consumer chips do not come with vPro which is the component that allows for connections anyways. AMT is part of all systems but not every feature is part of every system.
For Wikipedia: Intel vPro technology is an umbrella marketing term used by Intel for a large collection of computer hardware technologies, including Hyperthreading, Turbo Boost 3.0, VT-x, VT-d, Trusted Execution Technology (TXT), and Intel Active Management Technology (AMT). When the vPro brand was launched (circa 2007), it was identified primarily with AMT, thus some journalists still consider AMT to be the essence of vPro.
The only component missing from vPro in modern systems is TXT, which is absent because most modern systems don't have a Trusted Platform Module. Either way, it's pretty irrelevant to the functionality of AMT as AMT operates out-of-band and in hardware... falsifying an AMT node would require fabrication on the nm scale (pretty much govt only), and if it did tie into TPM tech, well that crypto was beaten back in 2010. TPM 2.0 was actually designed with a backdoor to govt in the first place. See: http://investmentwatchblog.com/leaked-german-government-warns-key-entities-not-to-use-windows-8-links-the-nsa/
19637665 said:I have done this on past articles but will do it again and I think the author of the article should as well as all this does is get people into frenzies and they start to spread rumors which are not true.
vPro, the ability to connect remotely to an Intel platform, is required to be supported on 3 components; the CPU, chipset and NIC. Lets look at consumer grade chipsets first:
Consumer:
Z270 - No vPro
H270 - No vPro
Business:
Q270 - vPro
Q250 - No vPro
B250 - No vPro
So in order for a new PC to even begin to support all of AMT and even worry about this potential risk, you need to have a business chipset and a top end one at that, the Q270.
Wrong. Firstly vPro is a practically meaningless brand-name spec on its own, all the other things you are stating are AMT. vPro support is deliberately disabled in some CPU's to sell others, yes, but other than that vPro is not itself a tangible technology or hardware, rather a software capability based on a few pieces of hardware and a SoC of sorts on the CPU that runs when the PC is off. Said SoC exists on EVERY Core i and Xeon CPU since Sandy Bridge. The question is whether it will speak to you or not (and thus your management application). Either way, it's an incredibly large and untraceable potential backdoor as should the SoC be possible to activate sans TPM, it would allow complete and untraceable access to every Intel CPU since the Sandy Bridge era.
http://www.intel.co.uk/content/www/uk/en/products/processors/core/core-vpro.html
https://forum-en.msi.com/index.php?topic=285449.0 <---- Has Z270 TPM socket as an example and full vPro compliance.
The reason why all these processors support vPro is the existence of TPM socket headers on many consumer motherboards. This header is the difference between full vPro support and none if you look at the rest of the spec. It looks like this and is even present on mobile devices. http://www.laptopmag.com/images/wp/purch-api/incontent/2016/06/51y1v71qrwl.jpg
19637665 said:
Then we have the CPU. The most common consumer chip that we buy, the i7 7700K or i5 7600K, do not support vPro. The 7700/7700T do and are more normally found in business PCs.
Binning. And marketing. No sense assisting the creation of overclocked consumer hardware server farms.
19637665 said:Last we have the NIC. In the consumer realm, it is a mix. Most boards have an Intel NIC but some have a KILLER NIC while others will have a Realtek NIC. Of the consumer boards they almost all use the I219-V which does not support vPro, that is the I219-LM.
It's not a mix at all, it's a monopoly. Intel desktop e1000 variants make up well over 60% of the market alone. I've never owned a non-intel NIC in an Intel PC. It's only in laptops and AMD PCs that stregnth weakens as multifeature Bluetooth/Wi-Fi/ethernet chips from Boardcom and Realtek start to make more sense.
For you and I maybe. That is small comfort for me. I may be locked out, but the decades of warez around the world suggests that I am not the greatest unlocker of these things.19637665 said:The majority of people here will get either a H270 or Z270 chipset, alone which kills vPro, a K series CPU and a board with a I219-V NIC or other brand NIC thus disabling vPro from working at all.
In short, the majority of consumers will not have vPro which disables remote access via Intels AMT.
Instead of using Wikipedia I will use a direct quote from Intel:
http://www.intel.com/content/www/us/en/architecture-and-technology/intel-active-management-technology.html
While vPro is a more blanket term now it was originally the term coined for its remote management system and still covers it. That's why I focus on vPro and not AMT. AMT is still in the CPUs but vPro has to have full support and the majority of consumer PCs will not have vPro on them. It also has to have the other end active in order to work. It is almost like RDP in that the PC has to allow it and the server has to support it.
This is an old video but this is when vPro was first introduced: https://www.youtube.com/watch?v=bBuhg4IAB3o
I am not wrong though. Systems without vPro cannot work with vPro. Again vPro is what Intel calls it and AMT is part of it. Me using the term does not make it wrong.
https://ark.intel.com/products/98089/Intel-Z270-Chipset ,_ Per Intel that chipset does not support vPro
Just because YOU have not had anything but an Intel NIC does not mean there is not a mix. Have you don computer repair? Because I have. And Realtek is in a ton of consumer OEM systems as it is cheaper than the Intel NIC. Slower but cheaper. Look up the drivers for the Dell Inspiron 3668. That is what would be the common Dell desktop. It has a Realtek NIC.
And 60% is not a monopoly, although I can't find anything on how much any one company has with that. A real monopoly is what Intel has in the server market, which is over 90%. But to be fair AMD didn't present much competition there.
My entire point was that the majority of consumers have no worries unless they bought a business class desktop for some reason. Even then there is more to it as it has to be activated from both ends with a secure key to even start working. The "Free Software Group" failed to state this and thinks otherwise.
I tire of arguing with you about something I clearly know more about so I will refer you to the actual technical document. You should stop reading marketing pages and taking them literally. Just as 4G is not LTE, marketing tends to lie. A lot.
In addition, the reason I use wikipedia links is that they have these funny little things called sources. When you go to University and write your first Bibliography you will understand their use, but they help tie together a huge amount of verifiable data from across the internet.
Firstly, vPro is not a technology, it's a 'standard', a brand. A bunch of checkboxes required by Intel to run the vPro software that Intel provides. The whitepaper, from Intel's mouth is here:
http://www.intel.co.uk/content/dam/www/public/us/en/documents/guides/vpro-technology-reference-guide.pdf
I refer you to page 41, clearly stating what I said above about what vPro is. Remember, this is not a vPro vulnerability, this is a ME/AMT vulnerability. vPro is an authenticated, secured management interface for ME/AMT, but in essence Intel could design a very dangerous non-authenticating version of vPro tomorrow and it would work in ALL Intel desktops back to Sandy Bridge. So could a hacker with the right code and workarounds. When millions, perhaps billions of dollars could be gained from this (how many banks have Intel processors in servers), it's not a big deal to recreate a program that could, even partially access part of the vPro spec.
-
andyz0976 How about the Xeon platforms? Do they have these craps as well? Maybe integrated deeper? My system is E3 1275 v5, C236 and an I210-T1 for network, is there anyway to disable AMT?Reply