
Leading Linux publication Phoronix has investigated the performance impact of mitigating the latest Load Value Injection (LVI) vulnerability on Intel processors.
Load Value Injection, which carries the CVE-2020-0551 identifier, allows the attacker to steal sensitive information from the victim by penetrating Intel's Software Guard Extensions (SGX). SGX essentially acts as a vault for storing important data. Both Intel and the researchers who exposed LVI have tagged the vulnerability as a theoretical threat, meaning that it's very unlikely that a malicious attacker will exploit it. Either way, Intel has released updates to the SGX Platform Software (PSW) and SDK to mitigate the security flaw.
Phoronix notes that Intel has basically added LFENCE walls before susceptible instructions. Therefore, the publication evaluated the processor's performance in five different scenarios: without Intel's mitigations, loading LFENCE before indirect branches, before RET instructions, after loads, and with all three options in tandem.
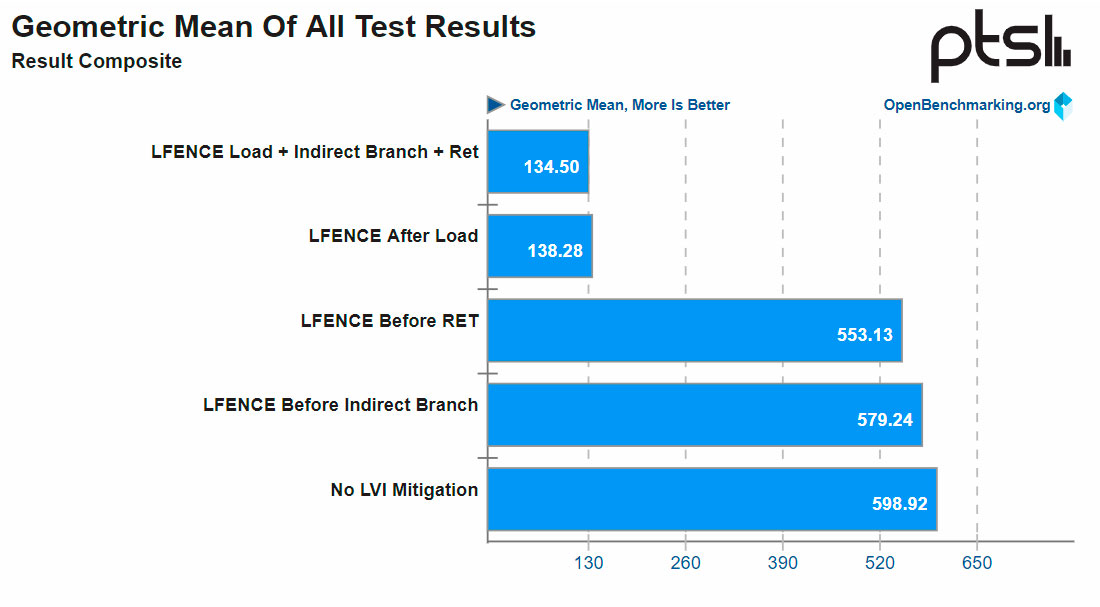
Phoronix tested the repercussions of the mitigations extensively in a real-word scenario with a Xeon E3-1275 v6 (Kaby Lake) processor. The publication's results show that enabling LFENCE before direct branches or before RET instructions has minimum impact on performance. The performance loss is less than 10%.
On the other hand, implementing LFENCE after every load instruction or all three assembler options can really cripple a processor's performance. The performance toll increases as much as 77%.
Luckily, LVI shouldn't be a big issue for consumer users since it's not common to see SGX usage on a mainstream PC. Theoretically, attackers can pull LVI off with JavaScript, however, the task is very complex. On the contrary, enterprise users should be more worried due to the frequent usage of SGX and virtualization.
For now, Phoronix considers the mitigations necessary for users that constantly interact with SGX or highly security-sensitive applications. Nonetheless, Bitdefender states that LVI could be a stepping stone for future attacks, so enterprise users might have to eventually implement the measures and take the performance hit.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
According to Intel's list of LVI affected processors, the more recent offerings, including Cascade Lake and certain steppings of Coffee Lake and Comet Lake, are only partially affected, while Ice Lake is protected against LVI.

Zhiye Liu is a news editor, memory reviewer, and SSD tester at Tom’s Hardware. Although he loves everything that’s hardware, he has a soft spot for CPUs, GPUs, and RAM.