Yubico 'Security Key' Launches With Support For New FIDO2 Candidate Protocol
The FIDO Alliance and the W3C have been working together on the FIDO2 project, which promises to allow users to authenticate their identities to websites from their desktops or mobile devices without using a password. The two groups announced that FIDO2 is now in the the Candidate Recommendation stage for W3C’s Web Authentication (WebAuthn) protocol, which is the precursor stage before the final approval.
At the same time, Yubico announced a new Yubikey that supports the new FIDO2 specifications.
FIDO2 And WebAuthn
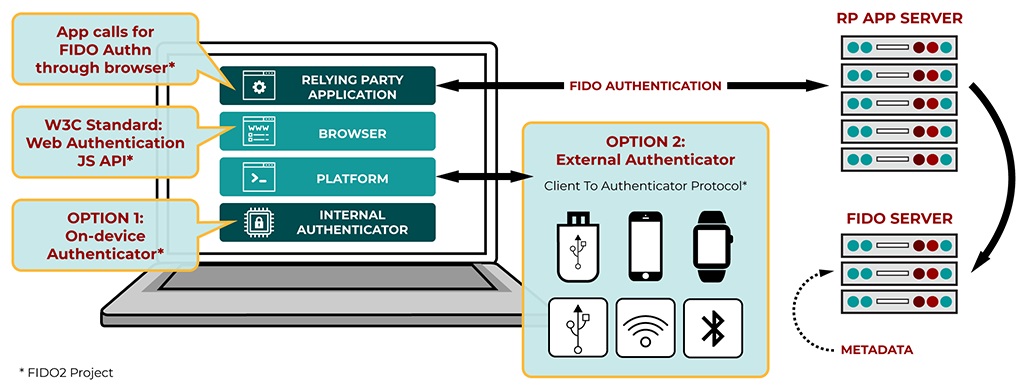
WebAuthn has been developed as a core component of the FIDO2 project, which also includes FIDO’s Client to Authenticator Protocol (CTAP) specification. CTAP enables an external authenticator such as a security key or a mobile device to communicate strong authentication credentials over NFC, Bluetooth, or USB to a user’s primary computing device such as a PC or another smartphone.
The main idea behind the FIDO2 project was to make logging in to websites as easy and as secure as using a FIDO U2F security key, which enables public-key cryptography. The private key is stored locally on the device, while the server to which the user authenticates would receive the corresponding public key. This way, even if there is a data breach, the hackers would have no passwords to steal, which should minimize your risk of exposure online.
Brett McDowell, executive director of the FIDO Alliance, said:
With the new FIDO2 specifications and leading web browser support announced today, we are taking a big step forward towards making FIDO Authentication ubiquitous across all platforms and devices. After years of increasingly severe data breaches and password credential theft, now is the time for service providers to end their dependency on vulnerable passwords and one-time-passcodes and adopt phishing-resistant FIDO Authentication for all websites and applications.
Google, Microsoft, and Mozilla have already committed to supporting the new specifications. Microsoft was one of the first to mention it for Edge in 2015 with its passwordless login feature for Windows 10.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Apple has avoided joining the FIDO Alliance so far. However, now that the specifications are expected be standardized soon by the W3C under the WebAuthn protocol, Apple will probably also integrate them in its devices sometime in the future.
There will be two ways to implement the new specifications:
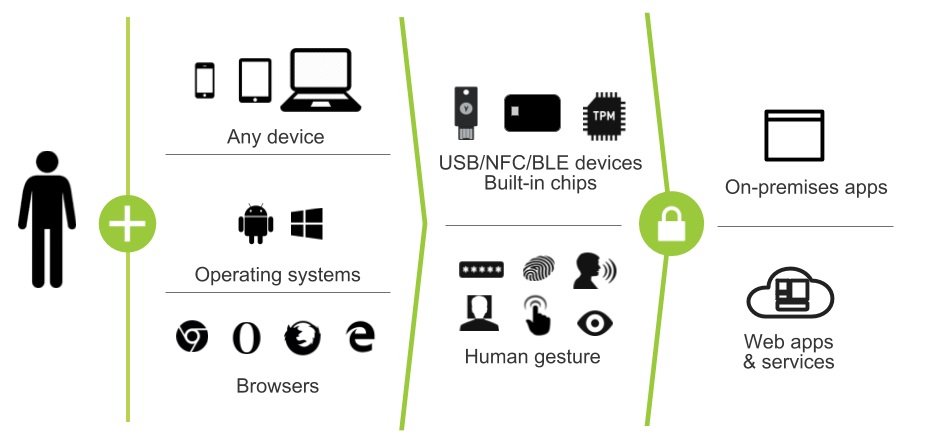
a) Simpler authenticationSimpler authentication: users simply log in with a single gesture using:Internal or built-in authenticators (such as fingerprint or facial biometrics) in PCs, laptops and/or mobile devicesConvenient external authenticators, such as security keys and mobile devices, for device-to-device authentication using CTAP, a protocol for external authenticators developed by the FIDO Alliance that complements WebAuthnb) Stronger authentication: FIDO Authentication is much stronger than relying only on passwords and related forms of authentication, and has these advantages: User credentials and biometric templates never leave the user’s device and are never stored on serversAccounts are protected from phishing, man-in-the-middle and replay attacks that use stolen passwords
New FIDO 2 Yubikey
Yubico, the creator of the Yubikey security keys typically used for two-factor authentication, is one of the co-creators of the FIDO U2F standard (along with Google). The company announced a new hardware token called “Security Key by Yubico” that supports the new FIDO 2 protocols, including WebAuthn and CTAP.
The Security Key can be used to authenticate to websites that support the FIDO2 standards directly, without needing any password. However, users can optionally enable the use of a PIN or biometric, too, to turn it into a two-factor authentication solution.
The difference between this solution and how things worked before is that the password was mandatory, and the user could only use a security key as a second-factor. Now it’s the password or biometric that’s optional.
The new Security Key by Yubico costs $20 and will start shipping globally from its website on April 13. The company will demonstrate its FIDO2 functionality at the RSA South Expo hall at Booth #2241.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
stdragon If you lose your key, the supporting website will often provide alternative means of regaining access to the account; most likely through a password reset sent to an email address associated with the account.Reply
I’ve been told that with LastPass, you’re SOL if you lose the key, and to have another key as a physical backup (can associate up to five) stored in a lockbox/safe someplace. However, according to LastPass, you can contact them in such an event.