Memcached Amplification Attacks Are Already Breaking DDoS Records

Earlier this week, Cloudflare announced that it had started to see some significant distributed denial-of-service (DDoS) attacks against its customers, reaching up to 260 Gb/s in bandwidth. Now Akamai has announced that one of its customers also experienced a record-breaking DDoS attack of 1.3 Tb/s, surpassing even last year’s attack against Dyn, which took out multiple internet services.
Memcached-Enabled DDoS Attacks
As Cloudflare recently explained, attackers have found a way to send spoofed requests to vulnerable memcached servers that also have UDP support enabled. Due to how memcached works, the servers then respond to the requests with much larger packet sizes. The servers send those packets to the target IP (chosen by the attackers), which ends-up overwhelming that targets’ systems and interrupting its proper functioning.
Cloudflare saw attacks of up to 260 Gb/s against its customers. These were significant, but nowhere near the much larger attacks in the 1 Tb/s range we saw last year. On the other hand, one of Akamai's customers seems to have experienced a memcached amplification attack that was five times larger than the 260 Gb/s attack Cloudflare saw earlier, reaching a peak of 1.3 Tb/s.
New DDoS Record
According to Wired, the impacted Akamai customer was GitHub, which uses Akamai for protection against DDoS attacks and for its content delivery network services. Akamai seems to have learned from last year’s Mirai botnet attack, which peaked at 623 Gb/s, because this time it was much better prepared to handle DDoS attacks in the Tb/s range. Akamai was able to mitigate and then stop the 1.3 Tb/s attack less than 10 minutes after it started.
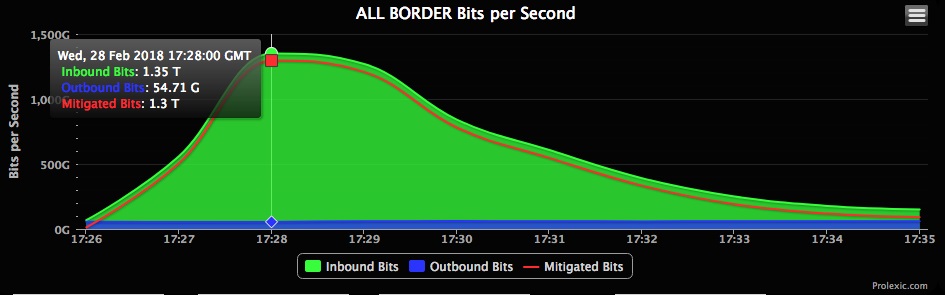
Akamai warned that it’s still early days for attackers using the memcached amplification DDoS technique and that we could be seeing much larger attacks in the future. The memcached amplification technique allows attackers to scale up their requests by over 50,000 times, so it shouldn’t take long until other malicious actors adopt it.
Akamai believes that the attacks could be largely mitigated if memcached server operators can rate limit traffic from source port 11211 and prevent traffic from entering and exiting their networks, but it noted that this could take time.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
bit_user Reply
The Chinese government was rumored to have done so, a few years ago. I think the story was they didn't like some software designed to circumvent their Great Firewall, and were trying to pressure Github to take the project offline. The attack lasted for days.20762324 said:What sick **** tries to ddos a github?
It's nice that Github can afford this protection, but think of small, independent online news or advocacy sites.