Newly Discovered Security Weakness Affects Most Laptops
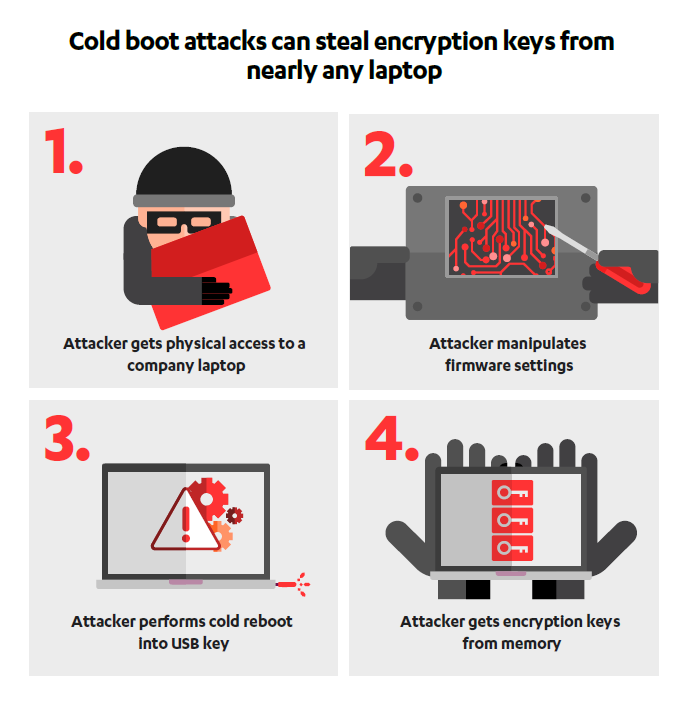
What's old becomes new again. That saying holds true for music, fashion and now, decade-old vulnerabilities that laptop makers have long since mitigated against. Cybersecurity vendor F-Secure announced today that "nearly all modern computers" are vulnerable to a cold boot attack that overrides existing safeguards. This attack can give someone access to laptop firmware and, therefore, encryption keys and other private data.
F-Secure explained that a cold boot attack lets hackers recover data available in RAM when a computer is rebooted without following the proper shutdown process. Attacks of this sort were discovered in 2008, and most laptop makers have since made their laptops automatically overwrite RAM to defend against them. This new attack lets someone with physical access to a laptop (and the right equipment) bypass those protections.
This vulnerability is particularly worrisome for organizations that regularly handle sensitive information, such as banks or government agencies, because the information gathered from a compromised laptop could let hackers work their way into other systems. Even secure networks can be accessed if someone is able to get their encryption keys, passwords and other relevant data by accessing a trusted laptop.
F-Secure said it confirmed that laptops from Apple, Dell and Lenovo are vulnerable to this modified attack and that it notified Microsoft, Intel and Apple about the problem so they could start to address it. But there isn't a convenient fix available for laptops that are already being used; organizations will have to adopt numerous safeguards in response.
F-Secure principal security consultant Olle Segerdahl explained in a blog post: "When you think about all the different computers from all the different companies and combine that with the challenges of convincing people to update, it’s a really difficult problem to solve easily. It will take the kind of coordinated industry response that doesn’t happen overnight. In the meantime, companies will need to manage on their own.”
Because the attack requires physical access, it's also hard to know if someone has already discovered and used it. F-Secure characterized the attack as something that a low-level hacker might not discover but that anyone interested in corporate espionage or the like would be very interested in. Organizations have to decide if they want to proceed as if they were affected, which could be costly, or if they'll ignore the issue.
F-Secure advised concerned organizations to require Bitlocker PIN entry when a laptop powers up or restarts, to make sure employees force the laptops to shut down or hibernate instead of going into sleep mode and to keep laptops safe and have a plan for if they go missing. Aside from those steps, however, it's up to the laptop industry to make sure their products aren't susceptible to this modified attack.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.
-
Co BIY So the attacker has to steal a laptop that is currently running, before performing the firmware switch and cold boot. Because the data they could potentially steal is wiped out during a normal shutdown ?Reply
This would be a pretty advanced and complicated attack. -
Pat Flynn OK... I work in IT... if you have physical access to a device that isn't supposed to be accesed., the security is compromised. PERIOD.Reply
I think we really need the media to chill on these 'security flaws', all you're doing is scaring the sheeple. -
dextermat I repair computer and sometimes clients forget their password (stored in outlook or web browser) When I show them how easy it is to get them they are mostly shocked. If you have physical access to computer, it is really easy to download tools and get info you want. This is not a new security issue.Reply -
stdragon Reply21317840 said:OK... I work in IT... if you have physical access to a device that isn't supposed to be accesed., the security is compromised. PERIOD.
I think we really need the media to chill on these 'security flaws', all you're doing is scaring the sheeple.
Short of an exploit I"m not aware of, I'm not sure a machine encrypted with BitLocker (FIPS certified encryption) can be cracked. I suppose it might be possible if the hibernation file (a RAM dump in a large file) was left in an unencrypted state, but I'm certain it's not, no?
-
anbello262 This is inportant for companies that keep big trade secrets, not for consumers (the same as most security issues discovered recently).Reply
So I wouldn't ignore it, but also it's important to know about the demographics targeted. -
mihen Watch out for this major security flaw. The hacker must convince the user to login to their account and wire them money.Reply -
Dosflores Reply21317956 said:I repair computer and sometimes clients forget their password (stored in outlook or web browser) When I show them how easy it is to get them they are mostly shocked. If you have physical access to computer, it is really easy to download tools and get info you want. This is not a new security issue.
Are you talking about computers that are protected by BitLocker? If you don't use BitLocker, data isn't protected at all. -
Dosflores Reply21318551 said:Short of an exploit I"m not aware of, I'm not sure a machine encrypted with BitLocker (FIPS certified encryption) can be cracked. I suppose it might be possible if the hibernation file (a RAM dump in a large file) was left in an unencrypted state, but I'm certain it's not, no?
Hibernation is safe. This new vulnerability only affects computers that are in sleep mode. -
Long__T123 once someone has physical access all they really have to do is take the hard drive and place it in a different computer to get everythingReply -
newsonline5000000 Reply21317840 said:OK... I work in IT... if you have physical access to a device that isn't supposed to be accesed., the security is compromised. PERIOD.
I think we really need the media to chill on these 'security flaws', all you're doing is scaring the sheeple.
You should be fired . PERIOD.
Physical access to a device does not mean security is compromised . it means the IT department is ignorant.
The best protection is being smart when you use your device . not open 100 Apps and sites and then cry when some one Hacks into your PC in standby mode