Unpatched Microsoft Office Flaws Used to Steal Files
Security company FireEye reported today that a new hacking campaign, Felixroot, uses old Microsoft Office flaws to install backdoors and steal files from victims’ machines. Felixroot was previously linked to another campaign from September 2017 targeting Ukrainian computers.
Felixroot
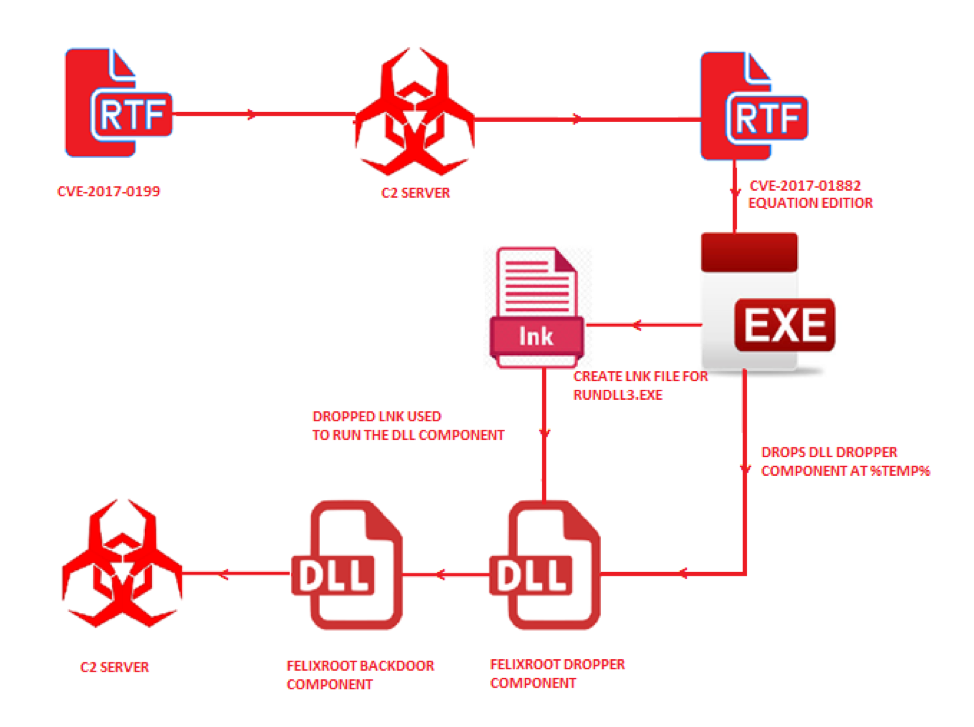
In September 2017, FireEye saw the Felixroot campaign for the first time. It was sending malicious Office bank documents to Ukranian users. The documents contained a macro script that would later download the Felixroot malware to the victims' PCs.
Fireeye observed a new version of the campaign recently. This time the campaign is using documents related to environmental protection. The malware in these documents was exploiting the unpatched CVE-2017-0199 and CVE-2017-11882 security flaws found in Microsoft Office last year. The first flaw is used to download the backdoor, while the second one is used to weaponize it.
The Technical Details
The downloaded Seminar.rtf file comes with another embedded file that is downloaded in Windows’ %temp% directory, from where the downloaded backdoor is later executed. The backdoor executable arrives encrypted via custom encryption.
This executable is then decrypted and run directly in memory, without ever being stored on the disk. The backdoor sleeps for 10 minutes before being executed by the rundll32.exe Windows component. Afterwards, it connects to the command and control (C2) server, from where the attackers can send remote commands to the victim's PC or steal files.
All data sent over the network to the C2 server is first encrypted with AES encryption and then converted to Base64 encoding to ensure that the data is not lost during transmission. The malware then sleeps before executing the next task.
FireEye said that the CVE-2017-0199 and CVE-2017-11882 Microsoft Office bugs are among attackers’ favorite flaws to exploit lately and warned that malicious parties will continue to exploit them until most organizations bring their Office software up to date.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.