New SSDs Have Built-in Protection Against Ransomware, Data Theft
Cigent and Phison make self-defending SSDs available to broader audiences.
Phison and Cigent introduced a co-developed SSD platform that protects against ransomware and data theft with mechanisms built directly into the SSD's firmware. The drives even automatically encrypt and hide data from prying eyes in the event of an attack. These 'self-defending' drives will be available to everyone this year.
Antiviruses can detect already-known malware and analyze programs' behavior to detect potentially illicit behavior patterns. However, custom ransomware developed by hacker groups can remain undetected until it is too late, leaving systems open to attack. Therefore, it makes sense to protect data at the hardware level in many cases since this is usually secure from manipulation.
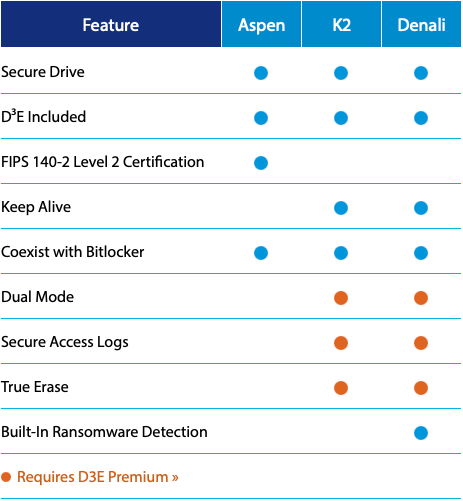
Cigent's Secure SSD K2 and Secure SSD Denali drives are based on Phison's PS5012-E12DC Crypto-SSD NVMe controllers and come with embedded firmware-based security features as well as Cigent Dynamic Data Defense Engine for Windows (D³E).
When a threat is detected, these drives automatically encrypt and hide sensitive files completely from the OS layer in 'safe rooms.' In fact, Cigent's drives can work in a 'Dual Mode' that splits an SSD into independent private/secure and non-private storage partitions that are invisible to one another and adversaries. Meanwhile, to protect data against physical theft, Cigent's drives also come equipped with attack detectors and sensors.
Furthermore, the Cigent Denali Secure SSD can actually detect ransomware (although it is unclear whether the firmware detects that a program encrypts data or the D³E software does it) and will support machine learning-based data protection later this year.
"The Cigent Secure SSD product family was developed by Cigent's team of experts in data recovery and cybersecurity working in close cooperation with the cutting-edge storage experts at Phison," said Greg Scasny, CTO of Cigent. "This combined team developed holistic data protection solutions with security built-in, making it virtually impossible for critical data and applications to be accessed from unauthorized sources. Software-only security is often easily bypassed, but our multi-patented, multi-layered self-defending storage can make critical data completely inaccessible and literally invisible to adversaries, giving customers peace of mind that their sensitive data and digital assets are safely stored and protected."
Previously only available to select government agencies and the U.S. army, Cigent's Secure SSDs will now be available to broader audiences. The K2 Secure SSD and D³E software are available now, starting at $299 for a 480GB drive. The Cigent Denali Secure SSDs will be available in Summer 2021. The drives come in 480GB, 1TB, and 2TB configurations.
Additionally, Cigent has developed its FIPS 140-2 Level 2-certified Secure SSDs exclusively for the U.S. government and military.
Recently Singapore-based company Flexxon launched its X-Phy SSDs with 'AI-based' security features that seem to work similarly to the SSD platform developed by Cigent and Phison. It is unclear whether these drives use Phison's E12DC controller, though.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Anton Shilov is a contributing writer at Tom’s Hardware. Over the past couple of decades, he has covered everything from CPUs and GPUs to supercomputers and from modern process technologies and latest fab tools to high-tech industry trends.
-
CerianK The drive has firmware... in addition to normal testing, firmare resistance to focused attack would have to be fully demonstrated, otherwise it is just another bot device (e.g. like some USB flash drives, motherboards, etc., have become).Reply -
InvalidError Reply
On the privacy side, this drive is just a fancier take on FDE which has been around for 10+ years ago.CerianK said:The drive has firmware... in addition to normal testing, firmare resistance to focused attack would have to be fully demonstrated
I'm guessing the ransomware protection part works by having an underlying media that is 2-3X the usable capacity so the drive can do a block roll-over with history on protected files and the software be used to roll back changes up to however far back the block history goes. -
hotaru.hino If I'm reading this correctly, the drives by themselves don't protect against ransomware, they have to have an app running to detect something fishy going on and then the drive can start doing the compartmentalization.Reply -
CerianK Reply
That does not say much about protection of the firmware, since the goal of malware isn't always about the data on the drive.InvalidError said:On the privacy side, this drive is just a fancier take on FDE which has been around for 10+ years ago.
As an example of the potential danger: I wrote an entire remote KVM server for instrumentation (with load balancing, RLL compression, IRQ tail-hooking, UART control, error side-channel, etc.) using assembly language for DOS (client was VB on Windows) years ago... all in less than 1024 bytes. Now I see even more sophisticated remotes (Bomgar, etc.) with billion dollar valuation, and cry that I couldn't market it (as I didn't own the code I wrote).