Researcher: Secure Boot Disabled on 290 MSI Motherboards
MSI accidentally disables Secure Boot on hundreds of its motherboards.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
One of the latest MSI UEFI updates accidentally disabled Secure Boot technology on hundreds of its motherboards, reports Bleeping Computer. As a consequence, over 290 motherboards for AMD and Intel processors can run insecure operating systems, which can be harmful.
MSI's firmware update version 7C02v3C released on January 18, 2022, comes with Image Execution Policy set to 'Always Execute' by default, which allows the PC to boot an operating system that lacks proper signature by its developer. This means that a computer can boot an OS that may have been tampered with, which is an insecure policy as the operating system may be infected or have malicious intent.
The discovery was recently made by Polish security researcher named Dawid Potocki. The researcher noted that he contacted MSI, but did not receive any response, which essentially means that so far the motherboard maker has not fixed its Secure Boot.
"If you are curious, yes, I have tried contacting MSI about this issue, but they ignored my emails and other forms of communication I have tried," said Potocki.
Affected Motherboards
At a high level we can see that many Intel and AMD motherboards are affected. Potocki has compiled a complete list in an issue raised on GitHub.
- AMD:
- Every X670(E) motherboard
- Every B650(E) motherboard
- X570:
- MEG X570S ACE MAX
- MEG X570S UNIFY-X MAX
- MPG X570S CARBON MAX WIFI / MPG X570S CARBON EK X
- B550:
- B550 GAMING GEN3
- MAG B550 TOMAHAWK MAX WIFI
- PRO B550M-P GEN3
- PRO B550-P GEN3
- PRO B550-VC
- Intel:
- Every Z790 motherboard
- Every B760 motherboard
- Z590:
- MEG Z590 UNIFY-X
- B660:
- MAG B660M MORTAR MAX WIFI DDR4
- PRO B660M-A CEC WIFI DDR4 V2
- H610:
- PRO H610M 12VO
- PRO H610M VDHP DDR4
- PRO H610M-E DDR4
- H410:
- PRO H410M-B
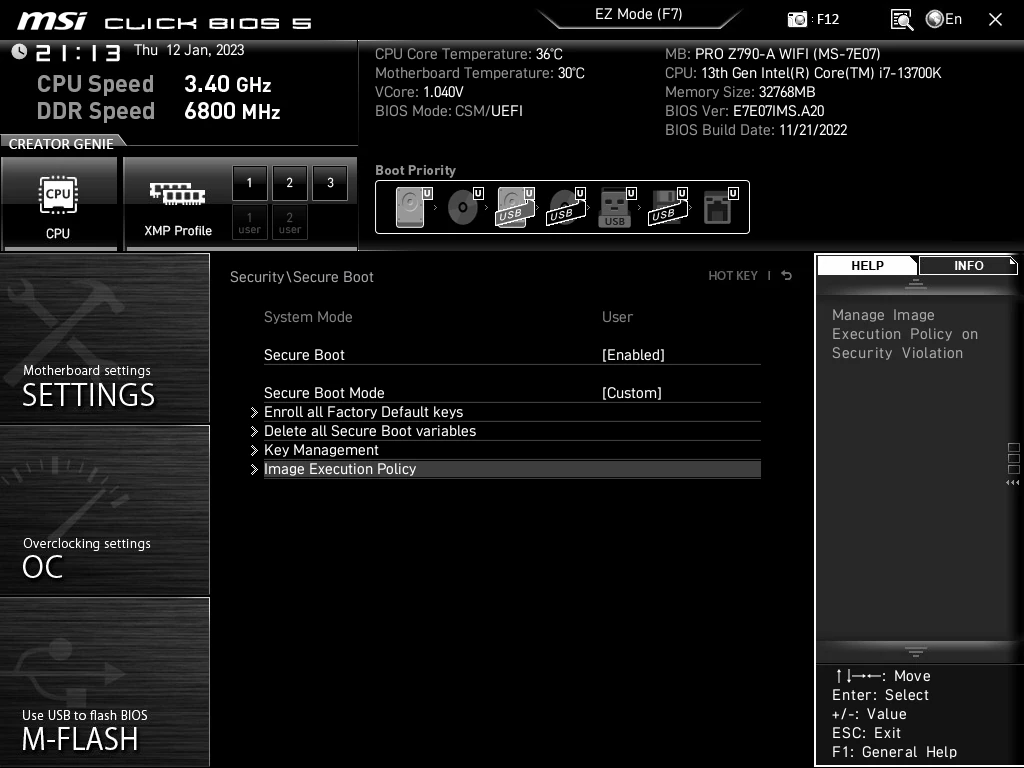
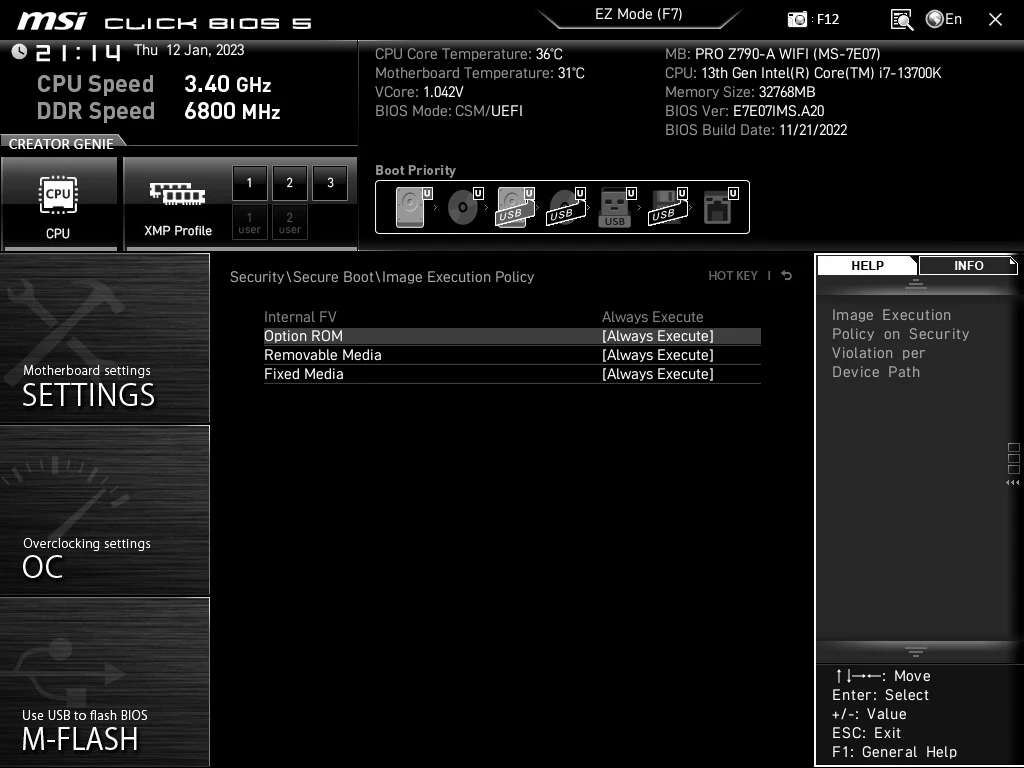
The Secure Boot technology is designed to ensure that only operating systems that are trusted by the PC can boot. When the PC starts up, the Secure Boot firmware checks the signature of each piece of boot software, including UEFI firmware drivers, EFI applications, and the operating system. If the signatures are valid, the PC boots, and the firmware gives control to the operating system. If signatures are not valid, the PC is not going to start. Meanwhile, firmware update version 7C02v3C essentially disables Secure Boot and allows all applications to boot even if they are infected.
The smart thing to do right now would be to check your BIOS settings "Image Execution Policy" to ensure that your system is safe. We are hopeful that an update will soon be released to resolve this issue.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Anton Shilov is a contributing writer at Tom’s Hardware. Over the past couple of decades, he has covered everything from CPUs and GPUs to supercomputers and from modern process technologies and latest fab tools to high-tech industry trends.
-
RoadieGhost What's the line between 'accident' and incompetent? If 10 models are affected I'd call it an unintended code interaction. 100+ models affected? That's a serious lack of QA and should be at minimum called negligence.Reply -
KyaraM Hmmm. Neither the Pro Z690-A nor the Pro B660M-A without WiFi are listed I see. Will check the Z690-A immediately and the B660M-A when it arrives for my secondary system upgrade I guess (though after a year, I should get a newer BIOS on it... well, I'll see I guess). The question I have is, what if it is indeed disabled? Can I enable it in the BIOS myself, or do I need to update the BIOS? Unfortunately not stated in the artice, but I guess the former?Reply -
Senile Otaku Well, this is virtually the opposite of the problem with their B450-A Pro Max boards, where their firmware update insists upon enabling (in)Secure Boot, regardless of what you had it set to before. And the newer firmware also ignores your boot-order settings in EFI, regardless of how you configure it in efibootmgr.Reply -
ComputePronto At least in my experience, MSI motherboards have poor UEFI implementations in their BIOS. It tends to cause boot entries to be randomly deleted. I have never seen another brand's motherboards do this. Even if Secure Boot works, you're still on thin ice.Reply
It's really unfortunate that so much of MSI's hardware is hindered by BIOS problems. It would otherwise be usable, at the very least. -
KyaraM Reply
Considering that I'm using two of their boards already and soon get a third, and never had issues, I would say you already can.ComputePronto said:It's really unfortunate that so much of MSI's hardware is hindered by BIOS problems. It would otherwise be usable, at the very least. -
Dawid's Throwaway ReplyRoadieGhost said:What's the line between 'accident' and incompetent? If 10 models are affected I'd call it an unintended code interaction. 100+ models affected?
It's most likely not an accident. There is nothing to point that it was, it seems like a deliberate change by MSI.
KyaraM said:Hmmm. Neither the Pro Z690-A nor the Pro B660M-A without WiFi are listed I see. Will check the Z690-A immediately and the B660M-A when it arrives for my secondary system upgrade I guess (though after a year, I should get a newer BIOS on it... well, I'll see I guess). The question I have is, what if it is indeed disabled? Can I enable it in the BIOS myself, or do I need to update the BIOS? Unfortunately not stated in the artice, but I guess the former?
PRO Z690-A / PRO Z690-A WIFI: 7D25vA42 (2022-05-23) PRO B660-A / PRO B660M-A WIFI: 7D59vA31 (2022-05-23)
I have posted the full list on GitHub, not my fault that Tom's Hardware decided to only copy 1/10 of it.
https://github.com/Foxboron/sbctl/issues/181
Also websites decided to for some reason mention version 7C02v3C which is a version for B450 TOMAHAWK MAX which only applies to this motherboard. Nobody seems to care to actually read what I have wrote and instead the news sites just copy off each other.
If you want the original source without all the mistakes, go read here: https://dawidpotocki.com/en/2023/01/13/msi-insecure-boot/ -
icesenshi Are you serious? What a joke, and poor excuse for an article. Secure boot is a joke created by Microsoft. Did you know that every linux distro has to ask Microsoft for a key just to boot their operating system? And if Microsoft refuses to a key, you're out of luck. There is nothing secure about secure boot, only Microsoft controlling what operating systems are allowed.Reply -
KyaraM Reply
Yeah, thank you for posting the full list. I went into BIOS and changed it last night already; but hopefully more people see it and act on it now that it is posted here!Dawid's Throwaway said:It's not an accident. There is nothing to point that it was, it has been a deliberate change by MSI like how I pointed in my source article. It's just bad reporting at this point.
I have posted the full list on GitHub, not my fault that Tom's Hardware decided to only copy 1/10 of it.
https://github.com/Foxboron/sbctl/issues/181
Also websites decided to for some reason mention version 7C02v3C which is a version for B450 TOMAHAWK MAX which only applies to this motherboard. Nobody seems to care to actually read what I have wrote and instead the news sites just copy off each other.
If you want the original source without all the mistakes, go read here: https://dawidpotocki.com/en/2023/01/13/msi-insecure-boot/
Also thank you for your hard work unveiling the issue! This should affect quite a few users and hopefully this helps them make their computers a bit more secure. -
TerryLaze Reply
First of all, not letting just any random into your house is the main basis for security.icesenshi said:Are you serious? What a joke, and poor excuse for an article. Secure boot is a joke created by Microsoft. Did you know that every linux distro has to ask Microsoft for a key just to boot their operating system? And if Microsoft refuses to a key, you're out of luck. There is nothing secure about secure boot, only Microsoft controlling what operating systems are allowed.
Second of all, MS has nothing to do with the keys for anybody else, whoever curates each linux distro would have to supply a valid private key to every mobo maker and of course the mobo makers would have to care enough about the distro to go into the trouble of including the key.