Unpatched Windows Flaw Lets Attackers Backdoor Systems (Updated)
Update, 10/18/18, 10:20 a.m. PT: Microsoft responded to request for comment about this security flaw and why it remains unpatched:
“Microsoft has a strong commitment to security and a demonstrated track record of investigating and resolving reported vulnerabilities. We're looking into this report, and if we determine we need to take further action to help keep customers protected, we will," said Jeff Jones, Senior Director at Microsoft.
Original, 10/18/18, 8:58 a.m. PT:
Sebastián Castro, a security researcher from Colombia working for the CSL security company, has found a Windows vulnerability that could allow an attacker to install a permanent backdoor in users' systems. The researcher said Microsoft is yet to fix this flaw.
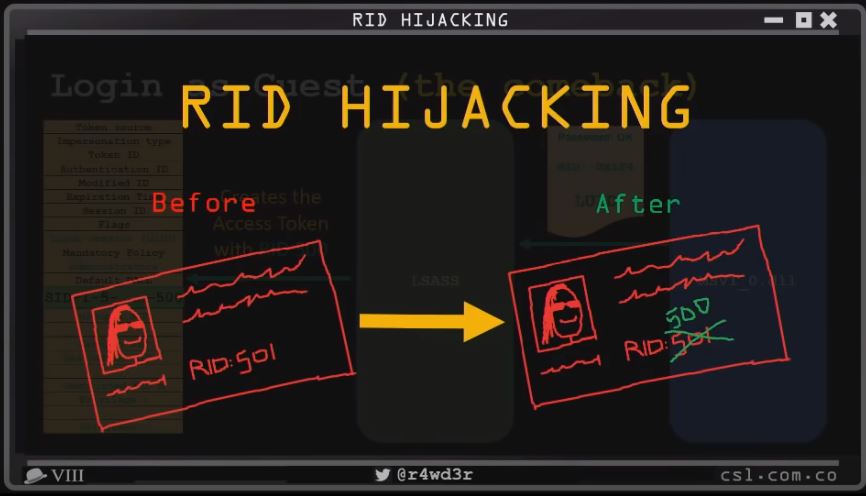
Windows RID Hijacking
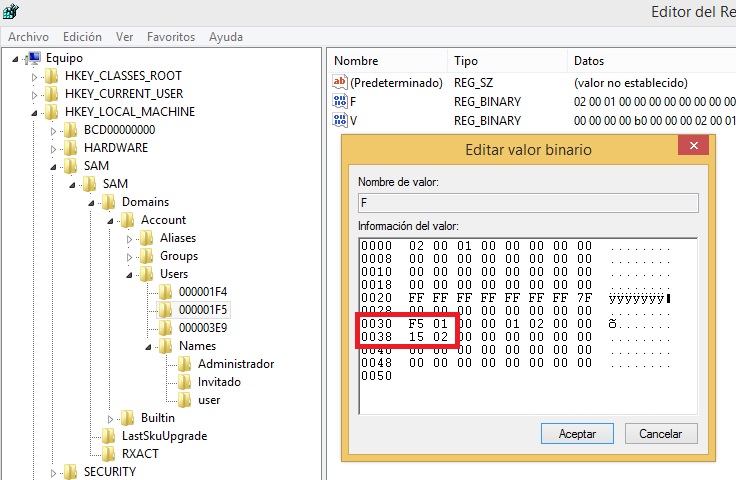
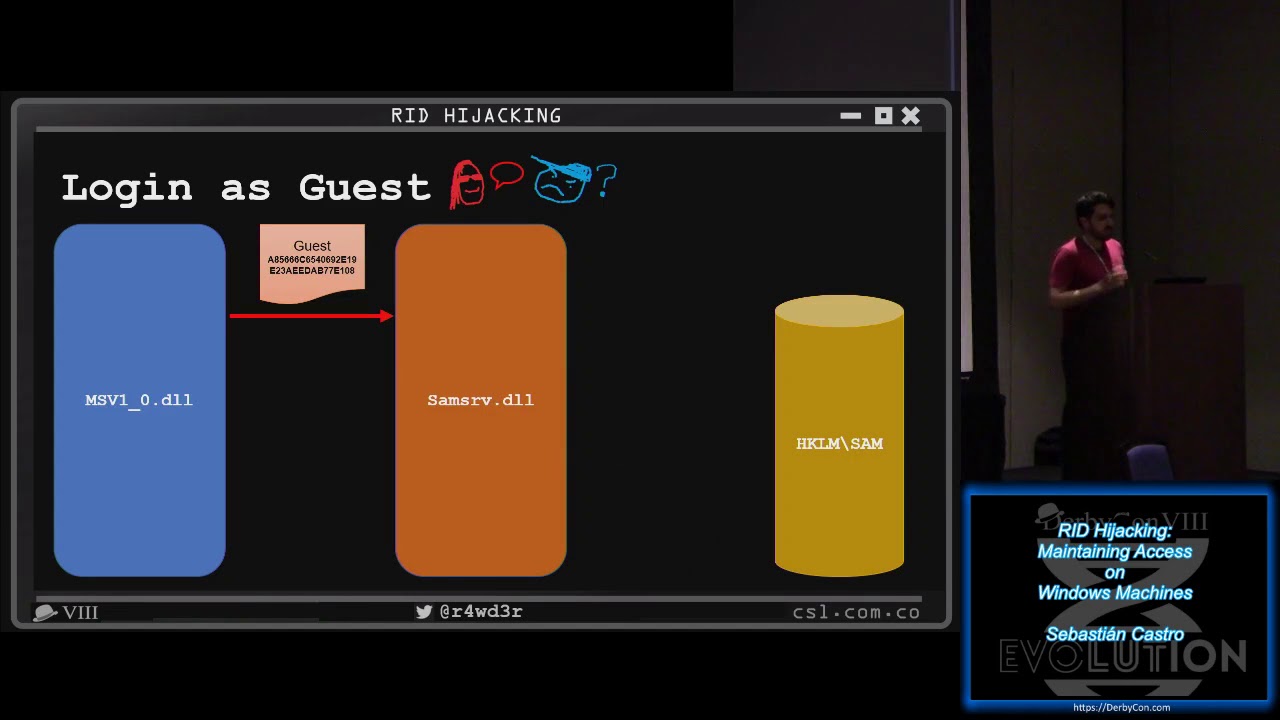
Castro found that the Relative Identifier (RID) that is assigned to Windows user accounts to describe their respective permission group could be modified with a simple registry change. Attackers could use the technique to gain administrative privileges and take control of the user’s system.
Attackers can’t make this change remotely, unless the user’s PC is somehow already exposed to attacks from the internet via open and non-secure ports or if the attackers already gained remote access to the system via malware.
However, if the hackers can brute force a user’s account password or get the user to install an infected file via email or some other medium, then they can gain a permanent backdoor with full system access.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Castro described the attack as highly reliable and working on all Windows versions from XP to 10, as well as on Windows Server 2003 to 2016. According to the researcher, the attack is not easily noticeable, as the hacker would use regular Windows resources. However, if you want to check if your limited or guest accounts have been backdoored this way, you can check to see if their RID has been modified to "500," which is the RID for administrator accounts.
Microsoft Hasn’t Fixed the Vulnerability
Castro told ZDNet that he reached out to Microsoft, but the company was unresponsive. He also made it clear that the vulnerability has not been patched.
To put some fire under Microsoft’s feet, the researcher has already released a fully working exploit for the popular Metasploit exploit framework, which means malicious actors will soon be able to integrate this exploit into their own exploit suites and malware too.
Castro also presented the attack at several security conferences over the past several months, so chances are Microsoft is well aware about it by now. We've contacted the company for further details, and we'll update this post if we receive a response.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Nintendork Sure, strong commitment to security then it deletes your personal data for the lulz on a broken OS.Reply -
derekullo If some one gains write access to your registry aren't you already pwned?Reply
Needing the user to install an infected program to then edit the registry just sounds like every other virus/trojan out there.
Am I missing something? -
jimmysmitty Reply21412463 said:Sure, strong commitment to security then it deletes your personal data for the lulz on a broken OS.
A single bug does not a broken OS make. 10 is a good OS that runs fine. The bug affected a minimal amount of people and was not being actively pushed to unaware users, meaning these people all manually started the update. Microsoft pulled the update before major damage to a much larger populace happened and as well it probably would not have affected the vast majority since the vast majority do not know how or use redirected folders.
21412678 said:If some one gains write access to your registry aren't you already pwned?
Needing the user to install an infected program to then edit the registry just sounds like every other virus/trojan out there.
Am I missing something?
No you are not missing anything. This requires quite a few things to be in play. Either they have physical access to the system and can crack or know the users password or they have to have the user install a program that gives them administrator rights to the registry. In a typical business environment the user normally should not be an administrator. Even in a personal environment the user should be a power user with a admin account they have to allow installs to happen.
It actually sounds like a meh vulnerability. Microsoft should patch it but it is not something that I would worry about too much unless you have hackers walking around your office/house daily. -
derekullo Reply21412727 said:21412463 said:Sure, strong commitment to security then it deletes your personal data for the lulz on a broken OS.
A single bug does not a broken OS make. 10 is a good OS that runs fine. The bug affected a minimal amount of people and was not being actively pushed to unaware users, meaning these people all manually started the update. Microsoft pulled the update before major damage to a much larger populace happened and as well it probably would not have affected the vast majority since the vast majority do not know how or use redirected folders.
21412678 said:If some one gains write access to your registry aren't you already pwned?
Needing the user to install an infected program to then edit the registry just sounds like every other virus/trojan out there.
Am I missing something?
No you are not missing anything. This requires quite a few things to be in play. Either they have physical access to the system and can crack or know the users password or they have to have the user install a program that gives them administrator rights to the registry. In a typical business environment the user normally should not be an administrator. Even in a personal environment the user should be a power user with a admin account they have to allow installs to happen.
It actually sounds like a meh vulnerability. Microsoft should patch it but it is not something that I would worry about too much unless you have hackers walking around your office/house daily.
This almost seems unpatchable in the sense that if some one steals the keys to your house the only ways to fix the issue is to steal the keys back or change locks.
The solution they are suggesting here feels like the thieves already have the keys to your house and their solution/patch is to install a lock on the wine cooler.
-
audiospecaccts Reply21412858 said:21412727 said:21412463 said:Sure, strong commitment to security then it deletes your personal data for the lulz on a broken OS.
A single bug does not a broken OS make. 10 is a good OS that runs fine. The bug affected a minimal amount of people and was not being actively pushed to unaware users, meaning these people all manually started the update. Microsoft pulled the update before major damage to a much larger populace happened and as well it probably would not have affected the vast majority since the vast majority do not know how or use redirected folders.
21412678 said:If some one gains write access to your registry aren't you already pwned?
Needing the user to install an infected program to then edit the registry just sounds like every other virus/trojan out there.
Am I missing something?
No you are not missing anything. This requires quite a few things to be in play. Either they have physical access to the system and can crack or know the users password or they have to have the user install a program that gives them administrator rights to the registry. In a typical business environment the user normally should not be an administrator. Even in a personal environment the user should be a power user with a admin account they have to allow installs to happen.
It actually sounds like a meh vulnerability. Microsoft should patch it but it is not something that I would worry about too much unless you have hackers walking around your office/house daily.
This almost seems unpatchable in the sense that if some one steals the keys to your house the only ways to fix the issue is to steal the keys back or change locks.
The solution they are suggesting here feels like the thieves already have the keys to your house and their solution/patch is to install a lock on the wine cooler.
Well to air the dirty windows laundry:
There was 85 security vulnerabilities that 60 of them was "patched" in August 2018
so there is still 20 of them.
Unfortunately, they are associated with Dot Net, VB C++ compiler and the xml language.
To make things worse, the security vulnerability with xml has been transferred to the hardware when anyone who develops firmware and firmware drivers on the windows platform.
I remember leaving a non corporate meeting with some software engineers that work for various software companies, including Microsoft (which that guy turned pale during this discussion), and they speak under their breath "we are doomed" about eight years ago.
A lot of the server farms have gotten rid of the IIS servers except: GoDaddy and Facebook because all were found to be hijacked by dark-web activity.
About 10 years ago I switched to Linux and I refuse to develop for the Microsoft platform. I also encourage others to explore it. Its a great operating system. Hardware seem to run faster too.
The US consumer should switch to Linux just for the simple fact its a lot safer for internet. To even go a little bit further, people should do it regardless if they used a piece of software for years and have to abandon it because they will not develop on a safer platform. -
Tinchote Microsoft is not "doing anything" because there is nothing to be done. This "exploit" depends on gaining system privileges; if you have system privileges you have full control of the system. There is no "vulnerability" to be patched.Reply -
audiospecaccts Reply21421453 said:Microsoft is not "doing anything" because there is nothing to be done. This "exploit" depends on gaining system privileges; if you have system privileges you have full control of the system. There is no "vulnerability" to be patched.
problem is, that there can be one than one root account.
Personally, they need to "rethink" things. This acount-networking scheme the average consumer wouldn't use, and quite frankly should not be ingrained into the OS, rather, it needs to be a module the customer installs at their discretion. On another level, there should be restrictions like making things read only, and denying remote servers access to the computer's storage, even when they go to a web site.
Speaking of which, I like the fact my Linux computer will not play certain streaming services because they connect an unknown server (to the user) to preform write services by direct disk access.