Ransomware Shows Devastating Potential With Disruptive Global Attack
A vulnerability that Microsoft silently patched in March, after it oddly skipped a whole month's worth of updates, has been used to launch a worldwide ransomware attack against at least 99 countries, including the UK, Spain, Russia, Japan, and the United States.
The vulnerability was being exploited by the NSA for potentially months or years, before the Shadow Brokers group leaked it to the public. Once it was publicly disclosed, anyone could have leveraged it against computers that haven’t been patched since before March.
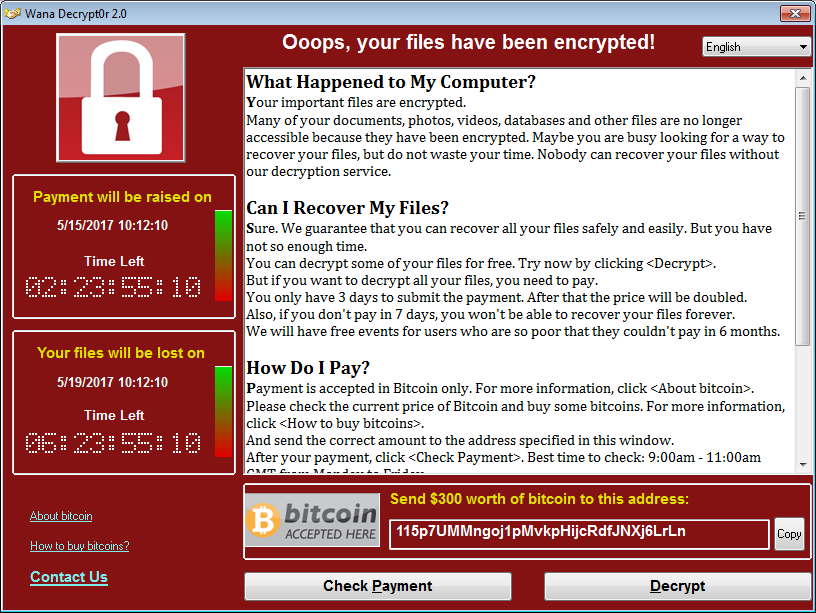
WannaCry Ransomware
Ransomware is a type of malware that infects your computer, encrypts your files, and then it demands a sum of money before it will decrypt them for you. In other words, it asks you for a “ransom” before it will let you access your files again.
One of the groups that has begun exploiting this Windows vulnerability in unpatched systems made the ransomware "WannaCry." The malware also goes by the names Wcry, Wana Decrypt0r, or WannaCryptor.
Antivirus companies such as Avast and Kaspersky saw many more of their users being attacked by this ransomware today than they usually do. One of the countries that seems to have been attacked most by the ransomware is Russia, but the UK’s National Health Service (NHS), Spain’s Telefonica wireless operator, and even the U.S.'s FedEx service have also been hit, causing significant disruption.
The NHS released a statement saying that it believes the malware is tied to WannaCry and that at this stage, there is no evidence that patient data has been affected. The ransomware showed a message saying that the ransom will double if it’s not paid in three days. (The ransom is currently $300 worth of Bitcoin.) If seven days have passed with no ransom, the group will keep the files encrypted forever.
Ransomware Is Coming Of age
Ransomware has been on a growth path over the past few years for one simple reason: It makes money for its creators. Users who get infected aren’t supposed to pay the ransom, because that would encourage the ransomware makers to keep infecting other PCs. However, not everyone listens to this advice, because some files may be worth much more than the amount of the ransom.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Up until recently, the ransomware threat wasn’t considered that significant. The number of computers that could be affected by a particular type of ransomware was in the hundreds of thousands over a period of many months. That isn’t a lot, compared to the almost billion and a half Windows PCs out there. Eventually, the collective thought process seemed to go, enough systems would get patched, and the ransomware wouldn’t be able to spread anymore.
The previous type of ransomware also spread more randomly, depending on who would click on a malicious email link or who would see a malicious ad. With this latest attack, though, ransomware seems to have arrived a point where it doesn’t just randomly infect users through malicious ads and links anymore; it can now spread quickly to and throughout large organizations and disrupt their functioning for days at a time, if not longer.
The new version of Wana Decrypt0r has reportedly infected tens of thousands of computers within hours. The number soon could grow much higher, because the types of medical devices that use unpatched versions of Windows will likely remain vulnerable to this attack much longer.
One reason the malware was able to spread so fast is because it was designed to spread like a worm inside a network, self-replicating on all vulnerable systems. If this is the type of attacks we can expect from ransomware from now on, then everyone will have to take this type of malware much more seriously. (People also need to update their systems in a timely manner.)
How To Prevent WannaCry And Other Ransomware
if you haven’t installed the March patch bundle on your computer yet, it’s time to do so. Keeping your system up to date is one of the best ways to keep it secure. It won’t save you from malware that uses zero-day vulnerabilities, but it should keep your system safe from the vast majority of exploits that rely on publicly disclosed vulnerabilities--such as the one used by the WannaCry malware.
If for some reason you can’t patch your system, having an antivirus or similar security solution that has confirmed it can block the latest version of WannaCry and other ransomware would be a good way to stop it, too.
According to Cisco’s Talos threat intelligence team, the ransomware looks for open 139 and 445 internet ports. If your organization uses these ports, it may be time to disable them, at least until your systems are patched.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Herc08 I am a IT Admin at OUHSC and we just found out about this. I think it's called WannaCry or something, and it uses 4 different types of file extensions. If I'm not mistaken, Microsoft has released a patch back in March, so keeping Windows updated should take care of this.Reply -
therealduckofdeath I think, the most important lesson organisations should learn from this exploit is, reconsider sticking to processes like ITIL. ITIL worked great in the old days. Today, most exploits are too sophisticated to be stopped just by keeping your software at the "last known good state". It needs to be patched and updated a lot faster than that.Reply -
ern88 I wonder if this could infect Windows 7 users as well? Or is this just a Windows 10 thing. I know a lot of businesses uses Windows 7.Reply -
Alex Atkin UK From Wired: "The vulnerability (MS17-010) is linked to Microsoft machines and can affect Windows Vista, 7, 8, 10 and versions of the Windows Server software.Reply
Microsoft fixed MS17-010 in its March release but it is likely organisations affected did not patch their devices before the spread of the malware."
This is interesting as it has previously been reported that most of the NHS still use XP, so is that vulnerable too or was it ironically only that small percentage that HAD upgraded that got infected? -
alextheblue Reply
XP is incredibly vulnerable. I wouldn't run XP outside of a virtualized environment at this point, at least not on a machine that has internet access.19683870 said:From Wired: "The vulnerability (MS17-010) is linked to Microsoft machines and can affect Windows Vista, 7, 8, 10 and versions of the Windows Server software.
Microsoft fixed MS17-010 in its March release but it is likely organisations affected did not patch their devices before the spread of the malware."
This is interesting as it has previously been reported that most of the NHS still use XP, so is that vulnerable too or was it ironically only that small percentage that HAD upgraded that got infected?
-
qazzi the main question in my mind is how did they get infected? phishing email? inserting already infected usb? because most of the time people who use pc needs to be trained/seminar about phishing email/scams, virus etc. i think they need to train/give a seminar on all those people who use pc. (because let's face it, most ppl that is not tech savy will just click a link in a email telling them they won something then boom ransomware installed.)Reply -
alidan Reply
apparently its just load a website with the worm and your hit, no execute anything, from my understanding an nsa "tool" that got leaked19684030 said:the main question in my mind is how did they get infected? phishing email? inserting already infected usb? because most of the time people who use pc needs to be trained/seminar about phishing email/scams, virus etc. i think they need to train/give a seminar on all those people who use pc. (because let's face it, most ppl that is not tech savy will just click a link in a email telling them they won something then boom ransomware installed.) -
sh4dow83 People who are technically proficient should REALLY read that Cisco article above everything else.Reply