Intel engineer's Linux patch would alert users of outdated microcode — Flagging the system as vulnerable
Your Linux system will inform you if your CPU is using an old microcode.

Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
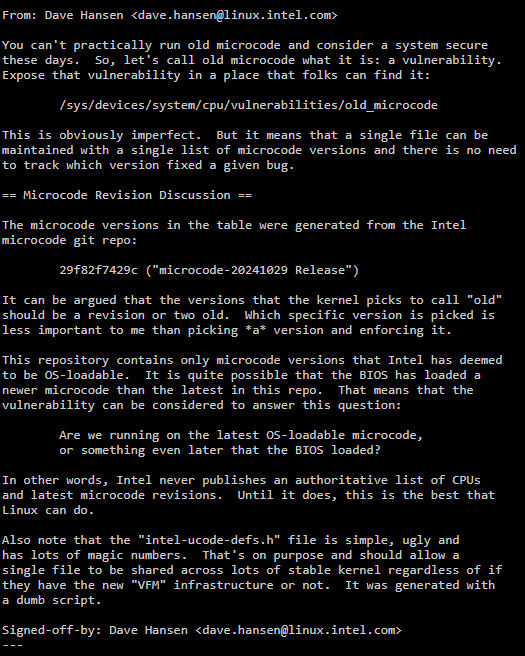
A Linux patch suggests that Intel engineers plan to implement a feature that tags your system as vulnerable if you're running outdated microcodes, (via Phoronix). This comes in light of the recent Intel 13th Generation and 14th Generation degradation fiasco, which is now pushing Team Blue towards a class action lawsuit.
The patch argues that you cannot run a system with old microcode and consider it safe. Microcode is basically a set of instructions in the CPU that can be updated post-launch to fix critical flaws and security vulnerabilities. The patch proposes that users should be informed clearly and concisely that their PC is potentially unsafe - marking the system as vulnerable or not vulnerable. The author calls to report this vulnerability in "/sys/devices/system/cpu/vulnerabilities/old_microcode", so that a single file can be used to prompt the user to update their microcode.
A new X86_BUG_OLD_MICROCODE flag has been introduced which will be used to identify if the CPU is running old microcode. For most CPUs, Linux will maintain a list featuring the latest microcode versions based on Intel's git repository.
This approach has a slight flaw, since microcodes can be updated through the BIOS or the Operating System's kernel. The CPU generally chooses the most recent microcode, however, if the BIOS's microcode is newer, then the system might report a false positive, even though the CPU itself is using the latest release. This is because the aforementioned git repository only hosts OS-loadable microcodes. If a particular BIOS vendor pushes a new microcode (not a part of the git repo), the kernel will not be able to tell if the CPU is on the latest version. To resolve this issue, the author suggests Intel publish an "Authoritative List" of all CPUs alongside their respective microcodes for ease of use and access.
Of course, this will not restrict you from running old microcode. The motive behind this update is to inform the end-user that their system is susceptible to flaws, or more specifically, CPU degradation. On the topic of degradation, Intel has started to roll out microcode updates through the kernel itself to save users the hassle of dabbling into the BIOS. On the flip side, Intel reported that its 0x129 microcode - which addresses a significant uptick in the minimum voltage to the CPU (Vmin), will not be offered through Windows Updates.
We'll see if mainstream forks of Linux will catch on to this notion and even implement something similar for AMD's Ryzen series. The idea is solid but the implementation requires some refinement, particularly in distinguishing between OS-loaded and BIOS-loaded microcodes.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Hassam Nasir is a die-hard hardware enthusiast with years of experience as a tech editor and writer, focusing on detailed CPU comparisons and general hardware news. When he’s not working, you’ll find him bending tubes for his ever-evolving custom water-loop gaming rig or benchmarking the latest CPUs and GPUs just for fun.