How Hardware-Based Security Protects PCs
Trusting The Trusted Platform Module
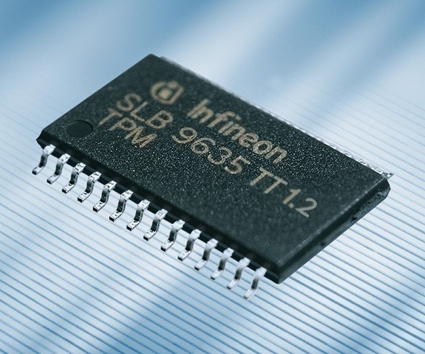
The TPM chip may be a separate chip on the motherboard, integrated in the network controller or placed inside the Southbridge; anywhere it can be connected to the Low Pin Count bus.
Originally designed by IBM and controlled by an alliance of companies through the Trusted Computing Group, you can think of the Trusted Platform Module (TPM) as a smartcard soldered onto the motherboard - the hardware is identical to a SIM, but with different firmware. IBM's original Embedded Security System chip was on a daughterboard that connected to the LPC and could be unplugged, but the TPM is permanently attached to the motherboard (connected to the southbridge or I/O Controller Hub by the 33 MHz Low Pin Count bus). You don't get a TPM chip in all systems, but any PC labeled as vPro or Centrino Pro will have a TPM. When Apple first switched to Intel processors, it put a TPM on Mac motherboards (used to check that Mac OS X was running on Apple hardware) but it dropped the chip after a few months, allegedly to reduce hardware costs.
The TPM has a small number of functions, including a random number generator and a key generator, so it can create signatures and key pairs for encryption. These encryption keys are stored in shielded locations inside the TPM, so they're harder to attack. Your private keys never come out of the TPM; instead, the TPM compares keys and either verifies them or signs public keys. There are root keys for encrypting storage and for reporting on the keys stored in the TPM. The TPM also has its own private key, the endorsement key created by the manufacturer, that can't be read by anything outside the TPM. There are initialization and management functions that let you turn TPM functionality on or off, reset the chip to clear your keys, and take ownership of a new or reset TPM (so you can pass a computer on to someone else). If a security system only needs to know that your PC has a TPM without knowing more about you, the TPM supports a Direct Anonymous Attestation protocol.
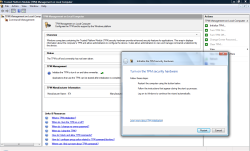
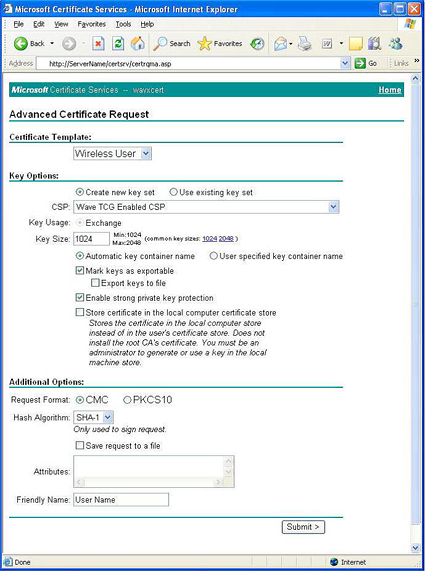
The TPM chip is disabled by default, so you need to enable it, via a jumper, the BIOS or both, depending on your system. Even when it's enabled, the TPM doesn't initiate interrupts, it only responds to requests from software. To use the TPM, you need to take ownership of it using the TPM utility software supplied with your PC: Intel uses Wave's Embassy Security Center. To use the TPM to generate keys, you choose it as the Cryptographics Service Provider (CSP) for whatever certificate you're creating.
The Trusted Platform Module is disabled by default, and must be configured before software can use it for security. Click the image to see a larger version.
Once you have activated the TPM and taken ownership you can use the Advanced options to use it as the Cryptographic Service Provider whenever you generate a certificate. Click the image to see a larger version.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Trusting The Trusted Platform Module
Prev Page Security systems like biometrics can work without a Trusted Platform Module, but they're more secure with it. Click the image to see a larger version. Next Page Trusting The Trusted Platform Module, Continued-
isaacio Yes,the security system once known as "Palladium".Discount Security Systems protect your own home against danger, damage, loss and criminal activity.Reply