How Hardware-Based Security Protects PCs
Encrypt Everything With TPM
Although it generates keys, the TPM doesn't run any software, and security software has to be written specifically to use it. Many desktop and notebooks sold since 2003 have TPMs built in; if your notebook has a fingerprint reader, the fingerprint scan and the passwords you save with your fingerprint may be secured by the TPM. Linux has had support for a TPM since version 2.6.12 of the kernel. Some password vaults use the TPM, like Wave's Personal Information Manager and Document Manager applications.
The TPM-secured software tools you're most likely to come across are encryption options like PGP Whole Disk Encryption, CompuSec FDE, Securstar DriveCrypt Plus Pack and Vista's BitLocker.
These tools encrypt the entire Windows volume and use the TPM to check the boot components; you can't boot if the system has been tampered with, and a thief can't boot from a CD or take your hard drive out and put it into a PC running another operating system to decrypt it.
For BitLocker, which comes free with the Ultimate version of Vista, your hard drive must be formatted with NTFS, and you need two volumes. The system volume only needs to be 1.5 GB, because it stores only the files needed to load Windows, which aren't encrypted. Vista itself will be on the boot volume, which will be encrypted by BitLocker with a full volume encryption key. That key is encrypted with a volume master key, so that if you change something in your system, or lose a key, you can get a new key without taking the time to decrypt and encrypt the whole volume again. You can also turn BitLocker off temporarily to update the BIOS (which changes the measurement in the TPM); again, the disk doesn't have to be decrypted and then encrypted again, because the boot volume stays encrypted but the volume master key is unencrypted. When you turn BitLocker back on, only the volume master key needs re-encrypting.
Once BitLocker verifies the key with the TPM and authenticates you, the Vista file system encrypts and decrypts disk sectors as you write and read data, which isn't enough to slow the system down significantly. If you hibernate the PC, the hibernation file is encrypted, and then decrypted again when you wake the PC. If you have other volumes, you don't need to run BitLocker on them directly - instead, you can use the Windows Encrypting File System, because the keys for that are stored on the boot volume, where they're protected by BitLocker.
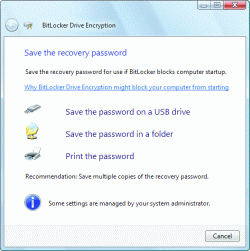
You can add a PIN or a startup key stored on a USB flash drive to make BitLocker more secure. You also need to create a recovery password or a recovery key that you save on a USB drive so that you can recover the encrypted drive if your PC fails and you need to read it on another system.
BitLocker ties your hard drive to your current PC and your current setup; you'll need the recovery details to get at encrypted files on any other machine. Click the image to see a larger version.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Encrypt Everything With TPM
Prev Page The Future Of TPM In The Chipset Next Page AMT Improves Security As Well As Remote Support-
isaacio Yes,the security system once known as "Palladium".Discount Security Systems protect your own home against danger, damage, loss and criminal activity.Reply