Staying In Control With Trusted Platform Modules
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Systems With TPM
We received a pre-production model of the HP Compaq DC7600 to evaluate. Unfortunately, apart from the TP module itself, nothing on this computer is prepared for trusted computing. The HP/Altiris administrative software is not in qualified condition, nor did HP provide other TC software, nor are the hard drive partitions encoded. Also the current Windows XP, even in its newest x64 flavor, is not able to make use of TPM hardware or their encoding inherently. All feature descriptions concerning this computer's TPM is based solely on HP/Compaq information.
HP/Compaq DC7600
The HP board comes in MicroATX format and can be expanded via a daughterboard with two additional PCI slots.
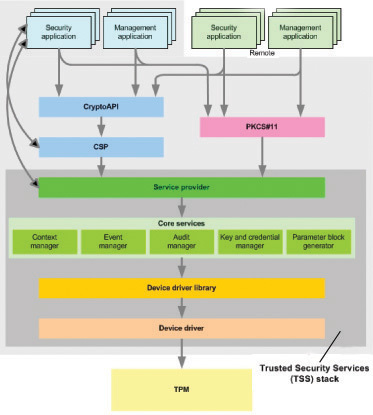
HP Compaq's DC7600 features one of the first HP desktop motherboards with a TPM unit. The 7x00 series are computers with TP module version 1.2, available as a configure-to-order option. However, HP integrates not a single TPM chip, but implants the Broadcom NetXTreme Gigabit chip BCM5752, which fulfills the latest trusted computing specifications. According to information on the Internet, activation of the chip's TC functions costs [the manufacturer] a surcharge of $10.
For TPM administration, HP adds an additional security layer, summarized as "ProtectTools". This tool is used by the Altiris "HP Client Manager," which is also suitable for hardware administration. In its current stage of development, the ProtectTools provide two functions only: Securing identification information during the user login, as well as encoding the hard disk(s). Of course, every TP module equipped HP Compaq computer is clearly identifiable.
As quintessential points of its trusted computing products HP Compaq notes the following possible features:
- Embedded Security for HP Tools makes root encoding available
- Virtual Smart Card enhances functions of genuine SmartCards or Token IDs
- Extension of other safety products such as SmartCards, fingerprint readers
- Improved encoding of wireless usage, as well as protection of the data and data integrity (spoofing protection)
- File and folder encoding (usable also when sharing)
- Encoded mailing (code keys produced via TPM)
- Controlling of access and access rights in networks
- Protection from hacker attacks (system attacks, DOS/network attacks)
- Secure single sign-on, a "global" user authentication
Broadcom's latest Gigabit chip has a TPM onboard.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Systems With TPM
Prev Page How Does This Compare To Intel's AMT? Next Page A Closer View-
jimmy99099099 Could you give some detailed information about this board? i was given one a few weeks back and i have been trying to find out the information. (Decent selling price, How much RAM it supports, The best CPU for it (Currently a intel pentium 4,) and the basic conclusion of being able to use this as a standalone PC motherboard?) Also a wiring diagram would be appreciated as i have had no luck in wiring the thing up.Reply