New AMD Side Channel Attacks Discovered, Impacts Zen Architecture (AMD Responds)
AMD processors from 2011 to 2019 impacted
Update #3 3/9/2020 7:20am PT: We've moved the two previous updates to the bottom of the article, and added the latest statement from AMD. A summation:
AMD responded to our queries with an advisory the company posted to its website. This advisory does not point to any mitigations for the attack in question, merely citing other mitigated speculative executions that were used as a vehicle to attack the L1D cache predictor. AMD's posting also lists general advice for protecting against the incredibly large family of side channel attacks, but there aren't any specific mention of firmware patches for the Take A Way vulnerabilities.
AMD responded for our request for more information and says there are no new mitigations required, as this issue is covered by the existing side channel attack mitigations.
The researchers do not agree, stating that this vulnerability is still active. Until the two sides agree it isn't possible to ascertain which viewpoint is more accurate. We'll update as necessary and keep an eye out for a CVE.
Original Article:
A new paper released by the Graz University of Technology details two new "Take A Way" attacks, Collide+Probe and Load+Reload, that can leak secret data from AMD processors by manipulating the L1D cache predictor. The researchers claim that the vulnerability impacts all AMD processors from 2011 to 2019, meaning that the Zen microarchitecture is also impacted. (PDF)
The university says it disclosed the vulnerabilities to AMD on August 23, 2019, meaning it was disclosed in a responsible manner (unlike the CTS Labs debacle), but there isn't any word of a fix yet. We've pinged AMD for comment.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
We've become accustomed to news of new Intel vulnerabilities being disclosed on a seemingly-weekly basis, but other processor architectures, like AMD and ARM, have also been impacted by some vulnerabilities, albeit to a lesser extent. It's hard to ascertain if these limited discoveries in AMD processors are triggered by a security-first approach to hardened processor design, or if researchers and attackers merely focus on Intel's processors due to their commanding market share: Attackers almost always focus on the broadest cross-section possible. We see a similar trend with malware being designed for Windows systems, by far the predominant desktop OS, much more frequently than MacOS, though that does appear to be changing.
In either case, we expect AMD's architectures to gain more attention from researchers as the company gains more prominence in the semiconductor market.
Like we've seen with many of the recent attacks against modern processors, the two AMD vulnerabilities center on side-channel approaches, in this case a Spectre-based attack (deep dive here), that enable researchers to tease out what would normally be protected information. Here's a description of the technique from the whitepaper:
"We reverse-engineered AMD’s L1D cache way predictor in microarchitectures from 2011 to 2019, resulting in two new attack techniques. With Collide+Probe, an attacker can monitor a victim’s memory accesses without knowledge of physical addresses or shared memory when time-sharing a logical core. With Load+ Reload, we exploit the way predictor to obtain highly-accurate memory-access traces of victims on the same physical core. While Load+Reload relies on shared memory, it does not invalidate the cache line, allowing stealthier attacks that do not induce any last level-cache evictions."
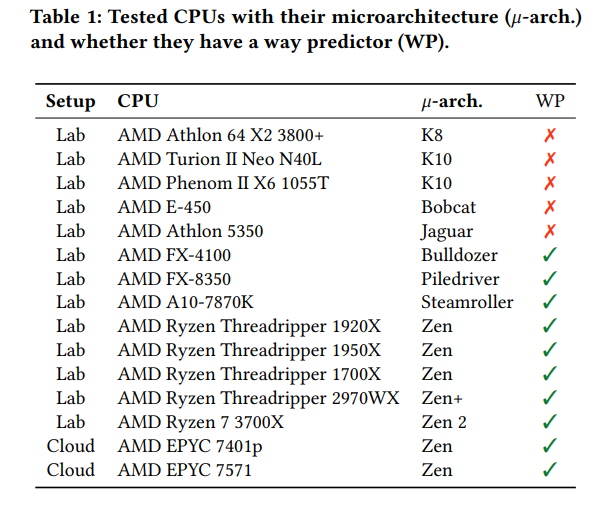
The researchers exploited the vulnerability via JavaScript run on Chrome and Firefox browsers, and also gained access to AES encryption keys. The exploit can also purportedly be used to penetrate cloud deployments in the data center. The paper suggests several possible remedies for the vulnerability through a combined software and hardware approach, but doesn't speculate on the performance hit associated with the suggested fixes. The researchers also noted that unlike the Spectre and Meltdown vulnerabilities, the Take A Way exploits only leak a "few bits of metadata," as opposed to providing full access to data (example of Meltdown exploit here).
The paper lists a wide array of funding from multiple sources, including the Austrian Research Promotion Agency, the European Research Council, and the French National Research Agency.
However, as spotted by Hardware Unboxed, the paper also says that "Additional funding was provided by generous gifts from Intel. Any opinions, findings, and conclusions or recommendations expressed in this paper are those of the authors and do not necessarily reflect the views of the funding parties."
This has, of course, generated plenty of attention, but it is noteworthy that the study's Intel-funded co-authors have also disclosed Intel vulnerabilities in the past (10 on Intel, including Spectre, Meltdown, and Zombieload, three on ARM, two on AMD, and one on IBM). The lead researcher also responded on Twitter, disclosing that Intel funds some of its students and the university fully discloses the sources of its funding. He also noted that Intel doesn't restrict the universities' academic freedom and independence, and that Intel has funded the program for two years.
Intel has disclosed, as recently as two weeks ago, that it funds research into product security and also awards prizes to researchers for finding holes in its architectures (Intel Bug Bounty program PDF), so this doesn't appear to be a case of Intel directly funding research against its competitor. The paper also engages in responsible disclosure of its funding sources, which makes any nefarious intent questionable. To cover the bases, we've also reached out to Intel for comment on the matter. According to the paper, Intel has already patched a similar vulnerability in its processors.
All modern processors have vulnerabilities, they are the most complex devices designed by humankind, after all, so crafty researchers will continue to find holes in the architectures. But that's better than discoveries made by those with malicious intent, particularly state actors, that could be exploited for years unbeknownst to the masses.
We'll update as we learn more.
Update #2 3/8/2020 3:00pm PT: The researchers contend that this vulnerability is still active.
Update #1 3/8/2020 8:10am PT: AMD responded to our queries with an advisory the company posted to its website:
"We are aware of a new whitepaper that claims potential security exploits in AMD CPUs, whereby a malicious actor could manipulate a cache-related feature to potentially transmit user data in an unintended way. The researchers then pair this data path with known and mitigated software or speculative execution side channel vulnerabilities. AMD believes these are not new speculation-based attacks."
It's noteworthy that this advisory does not point to any mitigations for the attack in question, merely citing other mitigated speculative executions that were used as a vehicle to attack the L1D cache predictor. The researchers also used other methods to exploit the vulnerability, so the advisory is a bit nebulous. AMD's posting also lists general advice for protecting against the incredibly large family of side channel attacks, but we can't find any specific mention of firmware patches for the Take A Way vulnerabilities. We're reached out to AMD for more clarity, including if there are any publicly available firmwares that specifically mitigate the newly-disclosed vulnerabilities.

Paul Alcorn is the Editor-in-Chief for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
valeman2012 Reply
These people were hyped to see that. It really really disappointing that the discovery was more than 90 days ago and yet no attempt to resolve 2 very major security flaw on AMD CPU.USAFRet said:For those of you who thought Intel was the only line vulnerable... -
InvalidError Reply
As I wrote back when the first bugs in Intel's chips were discovered: only a matter of time until AMD-specific bugs are found, AMD just wasn't getting as much attention previously as the minority player.USAFRet said:For those of you who thought Intel was the only line vulnerable... -
Deicidium369 There are ZERO real world exploits for any of the vulnerabilities - they are lab tests and are not exploitable in the wild... it's not like it's a piece of malware. This goes for Intel and AMD. If you allow someone unfettered physical access to your server in the real world - you need to look for another job.Reply
More and more of these vulnerabilities will be coming for AMD - until now they were a novel niche CPU with no real installed base - if you aren't looking, you aren't finding. I would be more worried about the rowhammer type attacks - those can be exploited rather easily. -
valeman2012 ReplyInvalidError said:As I wrote back when the first bugs in Intel's chips were discovered: only a matter of time until AMD-specific bugs are found, AMD just wasn't getting as much attention previously as the minority player.
Its alarming and i betting these amd individuals would say "this discovery was paid by Intel" on community forums in order to cover their major disappointment of being wrong.Deicidium369 said:There are ZERO real world exploits for any of the vulnerabilities - they are lab tests and are not exploitable in the wild... it's not like it's a piece of malware. This goes for Intel and AMD. If you allow someone unfettered physical access to your server in the real world - you need to look for another job.
More and more of these vulnerabilities will be coming for AMD - until now they were a novel niche CPU with no real installed base - if you aren't looking, you aren't finding. I would be more worried about the rowhammer type attacks - those can be exploited rather easily. -
ingtar33 Reply
this is a specter style attack, which means it requires physical access to the computer, adjustments to the bios and administrative passwords to work.USAFRet said:For those of you who thought Intel was the only line vulnerable...
In short it's a nothing burger. that's not to say AMD isn't vulnerable to security risks, but this one is a whole lot of nothing. because if someone has that much access to the computer, they don't need a virus. -
USAFRet Reply
And how many comments have we seen in the last couple of years with:ingtar33 said:this is a specter style attack, which means it requires physical access to the computer, adjustments to the bios and administrative passwords to work.
In short it's a nothing burger. that's not to say AMD isn't vulnerable to security risks, but this one is a whole lot of nothing. because if someone has that much access to the computer, they don't need a virus.
"I'll never buy Intel again because of these vulnerabilities!" Spectre, Metldown, etc.
Given enough access and poking around, all code has a hole. -
deksman No one ever said that AMD's CPU's are 'untouchable' by potential security exploits... however, AMD remains LEAST AFFECTED (at least compared to Intel), and are usually quick to respond with security patches.Reply
The sheer amount of security vulnerabilities that affect Intel are usually more important for servers and data centres (where big money is).
On an individual user level, a person is not very likely to encounter issues related to these exploits... however, out of the two, Zen uArch is (and I am repeating myself here) 'least affected'. -
InvalidError Reply
It is possible to write secure code, albeit on the smaller end of things. A lot of the insecurity in modern software comes from pervasive use of off-the-shelf blobs, rarely vetting those blobs and how they are used. Kind of hard to fully vet code in modern environments where "hello world" involves 50 million lines of external code most people have zero visibility into.USAFRet said:Given enough access and poking around, all code has a hole.