ORWL, The ‘Tamper-Proof’ Computer, Becomes Even More Secure With Qubes OS Support
ORWL is a crowdfunded small computer that promises “physical security,” meaning its insides can’t be modified or backdoored once it leaves the factory floor. ORWL already supported Windows 10 and Ubuntu 16.04 LTS, but it will now gain support for Qubes OS, to take its software security to the next level.
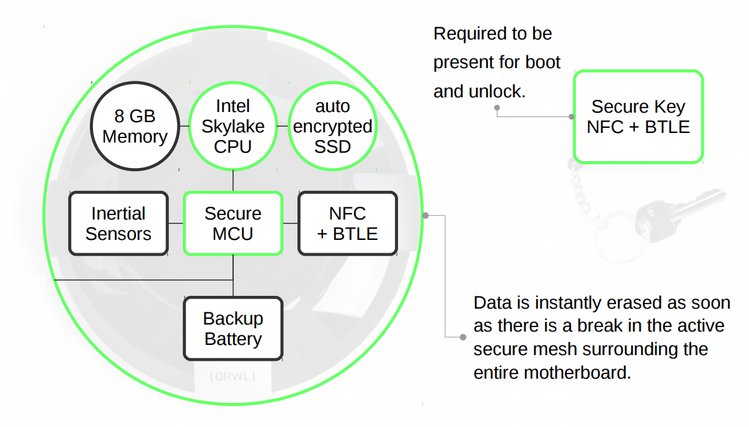
ORWL Active Mesh
ORWL was designed as a computer that is tamper-proof, encrypted, and requires a secure fob for authentication. The tamper-proof technology is provided by an enveloping “active mesh,” which is made of resin material with finely printed circuitry that can shatter when drilled. This is what prevents access to the computer’s internals, because as soon as someone tries to open the active mesh case, the SSD’s encryption key is wiped. Therefore, physical access to data should be impossible.
Usually, when hackers have physical access to a device, that makes it exploitable, but ORWL is designed to protect itself against that threat model. The technology is used by the banking, defense, telecom, and healthcare industries for Hardware Secure Modules (HSMs), ATMs, telecom cryptographic key protection, and in some medical devices.
Secure Key Fob
ORWL’s secure key fob works in the same way a smart card would for authentication, but with proximity detection. The key fob uses NFC and Bluetooth for authentication, but the ORWL team seems to have done this in a clever way. In general, security keys with wireless authentication either use NFC or Bluetooth to authenticate. Each scenario presents its own challenges.
NFC's range is too short (a few centimeters), so if you want the computer to lock itself after the key is no longer in range, that could cause some usability problems.
The alternative is to use Bluetooth, which typically has a range of up to 30 meters. This is also not ideal. Its long range means someone could also try to unlock it from a safe distance, which is the same reason mobile payment systems use NFC rather than Bluetooth.
The ORWL team seems to have found a sweet spot by using both technologies: The device unlocks only through NFC, but it can remain unlocked as long as you’re in Bluetooth range.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Qubes OS
The ORWL team has strived so far to make its computer as physically secure as possible. However, most of the people interested in buying such a device likely want the most secure operating system running on it, as well. That’s why the team will soon support Qubes OS.
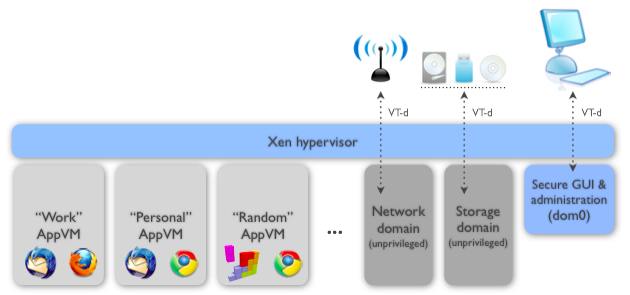
Qubes OS is an operating system, or rather a “platform” for operating systems, that allows the user to separate tasks in different virtual machines (where each can run its own OS). In this way, it minimizes the risk that one PDF or document file, or a certain browsing session, can hijack the whole system.
Users can use either more permanent VMs, which they can separate into “work,” “personal,” “banking,” and so on, but they can also instantly create “disposable VMs” for tasks such opening an email attachment. The disposable VMs will be wiped as soon as they are closed.
Qubes OS also puts the networking software stack and USBs in virtual machines, and the team behind it generally tries to isolate as many risky software components as possible into their own virtual machines. This is a rather unique but also highly effective way to deal with security issues, and it’s why the ORWL team is now going to support Qubes OS for its hardware. The two together should make the whole solution more appealing to security-minded people.
The ORWL team is currently doing a crowdfunding campaign and has already met 80% of its goal. The cheapest ORWL variant costs $699 and comes with a Skylake Core m3 processor and a 120GB self-encrypting SSD. The company plans to ship the ORWL computer on January 16, 2017, with free shipping costs in the U.S., and $80 shipping worldwide.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
DeadlyDays tempting, I've been thinking about putting together a Qubes system for a central workstation for myself.Reply -
SillieAbbe However nicely designed and implemented, devices, tokens, cards and phones are easily left behind, lost, stolen and abused. Then the remembered password would be the last resort.Reply
And, in a world where we live without remembered passwords, say, where our identity is established without our volitional participation, we would be able to have a safe sleep only when we are alone in a firmly locked room. It would be a Utopia for criminals but a Dystopia for most of us.
Are you aware of this?
https://youtu.be/-KEE2VdDnY0