Harden Up: Can We Break Your Password With Our GPUs?
Archive Encryption: WinZip And WinRAR
The data in an encrypted archive, like one you'd open with WinZip or WinRAR, is generally less safe than it would be on a fully-encrypted drive. That's because we are talking about dissimilar concepts.
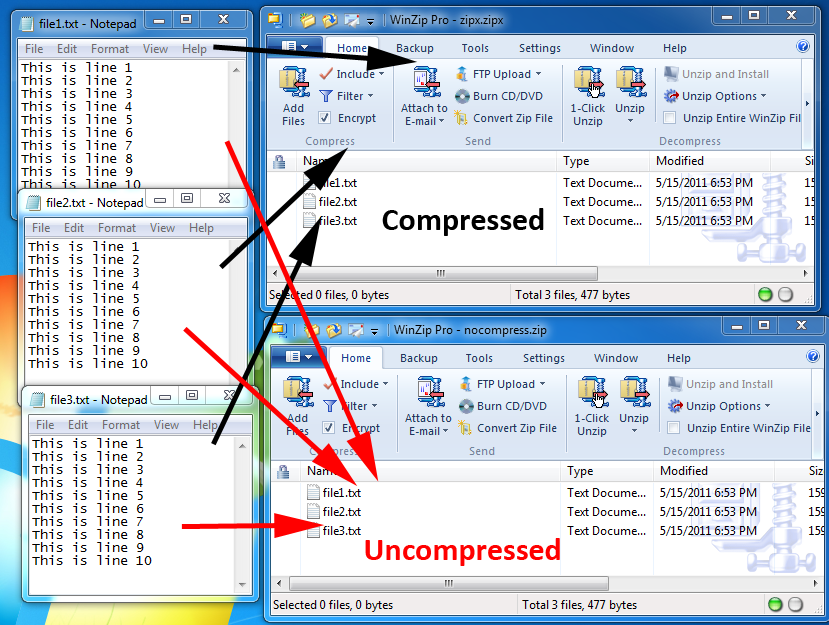
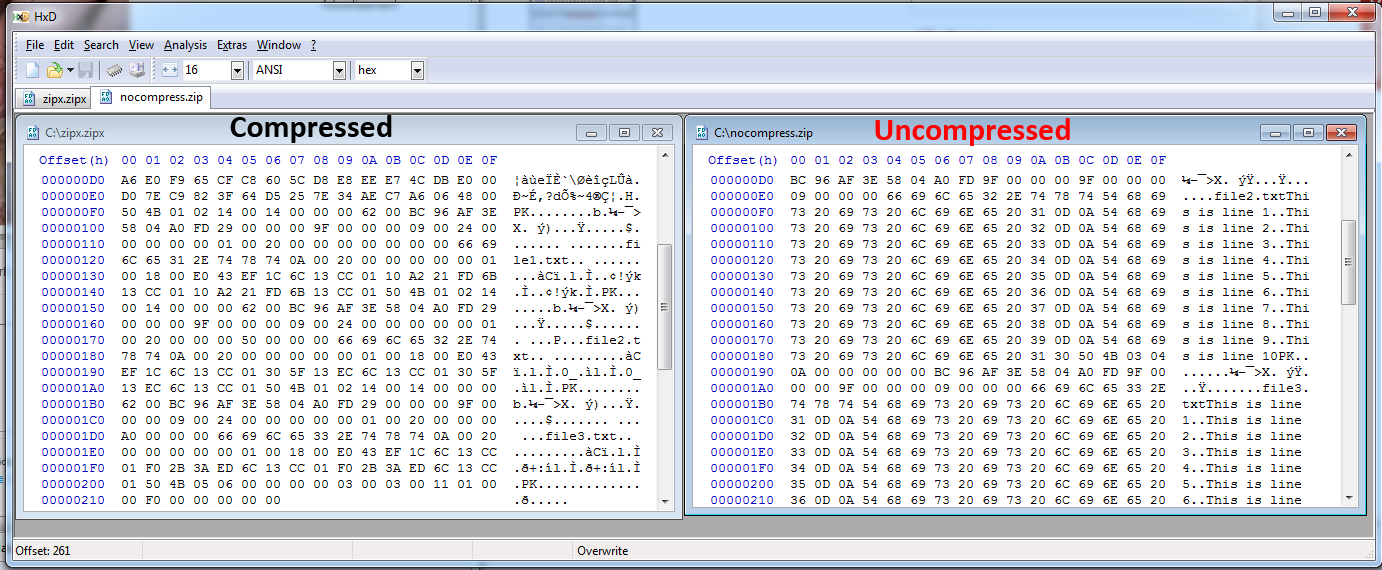
Data compression involves wrapping a file or a set of files in a container and removing redundant data bits to conserve storage space. You can actually see the difference with a simple file comparison in a hex editor. Notice that there are fewer rows due to compression.
Of course, the concept of a file container is what also allows you to open up an encrypted WinZip file. The container is not encrypted; the contents are. This means you don't need a password to see the contents of an archive. File names are not protected.
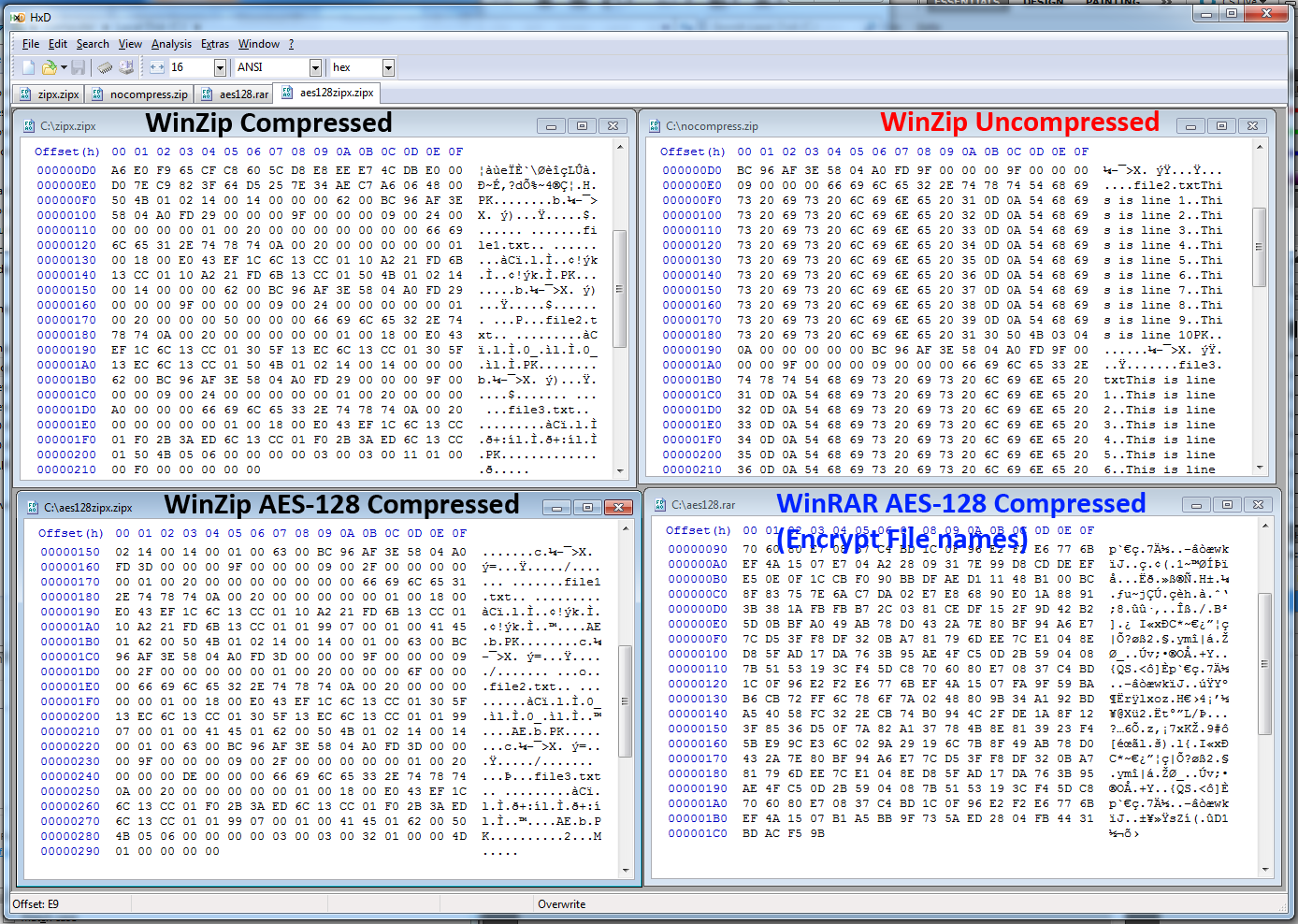
WinRAR relies on the same concept. But now you have the option of encrypting file names. It's possible to do this by securing access to the entire container. This prevents you from even opening the file unless you have a password.
File names are part of what’s known as metadata. This is akin to data's data, and it's one characteristic that separates WinRAR and WinZip. The latter allows you to see the contents of an encrypted archive while former is able to encrypt metadata.
That, in and of itself, doesn't necessarily make WinRAR more secure. But persistent password hackers try to exploit metadata, as it’s usually unencrypted. By finding weaknesses, it's possible to engineer an exploit that takes advantage of flaws in the way encryption is used.
Now, you shouldn't be too concerned if have a strong password and you use a good encryption scheme (AES-128 or AES-256). At the same time, if you don't want people to know what you are encrypting in WinZip, it's better to use a nondescript file name instead of something like "2011 1040 Tax Form." Of course, strong security cuts both ways. If you obscure file names, you won't know what's in the encrypted file until it's full decrypted. Making access less convenient for prying eyes generally means it becomes less convenient for you, too.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
So what happens when you heed our call, tighten the bolts on all of your digital locks, and then forget how to get them open again?
Current page: Archive Encryption: WinZip And WinRAR
Prev Page Test Setup Next Page Exploring Password Strength-
jeff77789 "While it would take a longer time to find a password made up of nine or 10 passwords, it's definitely doable between a few gaming buddies. "Reply
9 or 10 characters? -
ryandsouza "Think of this as generating every single combination of numbers that can be used to solve that same Sodoku puzzle, starting from an all zeros all the way through all nines. "Reply
Sudoku puzzles have numbers from 1 through 9! -
rpmrush This reminds me of Bitcoin GPU crunching. 6990s are favored right now. I wonder how many were sold specifically to Bitcoin miners? I tried it with my dual 6850s but the heat was rediculous. I didn't like the stress on my hardware so I gave up mining. I'm sure it's the same with password software. Maxing out your GPUs. Great for Winter, not Summer!Reply -
mediv42 I've always wondered about this: why don't they just code a delay into the decryption program, so you can't check a billion passwords a second?Reply
-
joshyboy82 I like the scale, but in your small example (a,b,c) you were right and wrong at the same time. Based on your configuration 6 possibilities are correct, but because you tell someone that they can use A or B or C in the password doesn't stop them from choosing aaa, therefor the combination is 9, not 6. Otherwise, interesting article.Reply -
acku Reply9515787 said:"Think of this as generating every single combination of numbers that can be used to solve that same Sodoku puzzle, starting from an all zeros all the way through all nines. "
Sudoku puzzles have numbers from 1 through 9!
Fixed! Sorry. I usually play Sudoku variants. :)
9515790 said:I like the scale, but in your small example (a,b,c) you were right and wrong at the same time. Based on your configuration 6 possibilities are correct, but because you tell someone that they can use A or B or C in the password doesn't stop them from choosing aaa, therefor the combination is 9, not 6. Otherwise, interesting article.
I could understand that, but I left out that since I was trying to show a simple example of how permutations differ from combinations. As you pointed out, repetitions are allowed in passwords. I actually mention that in the sentence that follows in the next paragraph. -
webdev511 Password Haystacks Yes Steve Gibson has already covered something like this. Passphrases with upper lower number and speical are the way to go. Yes, please avoid shortcuts.Reply -
acku Reply9515789 said:I've always wondered about this: why don't they just code a delay into the decryption program, so you can't check a billion passwords a second?
It wouldn't be easy from a design standpoint, cause now you're talking about fiddling with the design of the program.
The easiest way to slow down the verification portion of the password authentication process is increasing the number of transformation invocations for key generation. The problem is that this slows down the performance of your machine, even if you have the correct password.
jj463rdHow about adding some extended ASCII codes to a password.
That assumes WinZip and WinRAR supports them. To be honest, I haven't looked into that. Though, I'm inclined to believe that neither program supports them. -
shin0bi272 the tables in this review are horrible... they go from lengths of time to number of passwords and theres no discernible notation when they do.Reply