Wi-Fi Security: Cracking WPA With CPUs, GPUs, And The Cloud
WEP Is Dead, Haven't You Heard?
Wired Equivalent Privacy (WEP) was the first security algorithm used by wireless networks to restrict access. It was originally introduced in 1999 as part of the 802.11 standard. However, it has long been considered to be a "broken" algorithm, and was effectively replaced by Wi-Fi Protected Access (WPA).
If you're still using WEP on an older wireless router, try not to feel too safe. The Wi-Fi Alliance abandoned WEP in 2003 because it's very easy to crack. With $20 and some basic technical know-how, a neighbor can procure your WEP password in about 10 minutes using publicly-available tools. It really is time to upgrade to at least WPA.
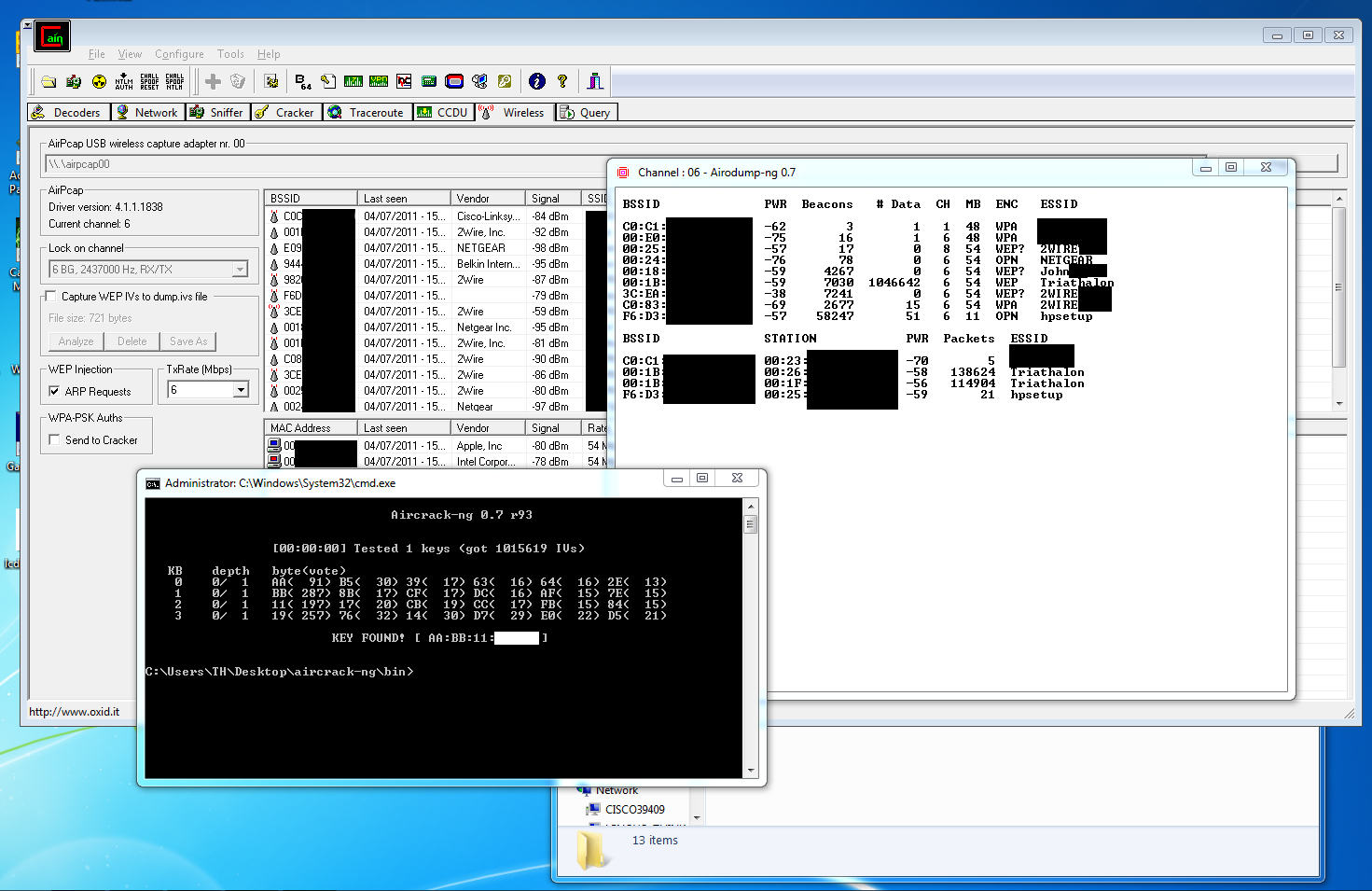
The process of breaking a WEP password can vary, but we've seen it done enough times that there's little reason to detail this bit of deviousness here on Tom's Hardware. Think of us like AMC's Breaking Bad. We're not here to show you how to cook meth. But our story hinges on the process. An enthusiast using WEP should know how easy it is to circumvent, and we did it so that you don't have to learn the hard way. To give you an idea of what's involved, we used Cain & Abel, Aircracking-ng, and an AirPcap Nx adapter to find a nearby network's WEP key in about five minutes. The length of the key doesn't affect recovery time, either.
The fundamental problem is that it's incredibly easy to eavesdrop on a WEP network and sniff out the information needed to crack the RC4 cipher backing the protocol. Even if there aren't enough packets traveling between the router and clients inside the network, it's possible to send packets in such a way to simulate reply packets, which then can be used to find the key. It's even possible to forcibly boot users off a router in order to generate packets with authentication information. Scary stuff; avoid it at all costs if security truly matters to you.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: WEP Is Dead, Haven't You Heard?
Prev Page Network Security: The First Line Of Defense Next Page Understanding WPA/WPA2: Hashes, Salting, And Transformations-
fstrthnu Well it's good to see that WPA(2) is still going to hold out as a reliable security measure for years to come.Reply -
runswindows95 The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply -
Pyree runswindows95The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply
Then either beer at your place is really expensive or internet is really cheap. Need 6x12 pack for me. -
compton Thanks for another article that obviously took a lot of work to put together. The last couple of articles on WiFi and archive cracking were all excellent reads, and this is a welcome addition.Reply -
mikaelgrev "Why? Because an entire word is functionally the same as a single letter, like "a." So searching for "thematrix" is treated the same as "12" in a brute-force attack."Reply
This is an extremely wrong conclusion. Extremely wrong. -
What about the permutations of the words?Reply
i.e ape can be written:
ape, Ape, aPe, apE, APe, aPE, ApE, APE.
Thats 2^3=8 permutations. Add a number after and you get (2^3)*(10^1)=80 permutations.
You can write PasswordPassword in 2^16=65536 ways.
How about using a long sentence as a password?
i.e MyCatIsSuperCuteAndCuddly, thats 2^25 permutations :) -
molo9000 Any word on MAC address filtering?Reply
Can you scan for the MAC addresses? It's probably easy to get and fake MAC adresses, or it would have been mentioned.
*scans networks*
12 networks here,
1 still using WEP
10 allowing WPA with TKIP
only 1 using WPA2 with AES only (my network) -
agnickolov Considering my WPA password is over 20 characters long I should be safe for the foreseeable future...Reply -
aaron88_7 "12345, that's amazing, I've got the same combination on my luggage!"Still makes me laugh every time!Reply