Wi-Fi Security: Cracking WPA With CPUs, GPUs, And The Cloud
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
GPU-Based Cracking: AMD Vs. Nvidia In Brute-Force Attack Performance
So, what happens when we put GPUs to work on the same task?
| Header Cell - Column 0 | Intel Core i5-2500K | Nvidia GeForce GTX 460 1 GB |
|---|---|---|
| Cores | 4 (no HT) | 336 |
| Clock Speed | 3.3 GHz (base) | 1350 MHz |
| Wireless Security Auditor | 4752 passwords/s | 18 105 passwords/s |
| Pyrit Benchmark | 3949.13 PMKs/s | 17 771.6 PMKs/s |
| Pyrit w/CoWPAtty | 3306.85 passwords/s | 19 077.15 passwords/s |
| Time To Crack Passwords Between 1 and 6 Characters (Alphanumeric) | 140 days, 14 hours (WSA) | 35 days (Pyrit) |
| Time To Crack Passwords Between 1 and 8 Characters (Alphanumeric) | 1480 years, 311 days (WSA) | 368 years, 319 days (Pyrit) |
Compared to CPUs, the performance difference is incredible. A single GeForce GTX 460 manages roughly 4x the performance of a Core i5-2500K.
That Forensic Computers, Inc. Tableau TACC1441 mentioned earlier should have been an indication that GP-GPU computation would outperform desktop CPUs. After all, the FPGA-based accelerator consists of a massively parallel array of processors that operate in concert to attack multiple types of encryption schemes. This is a problem better-addressed by many cores operating concurrently.
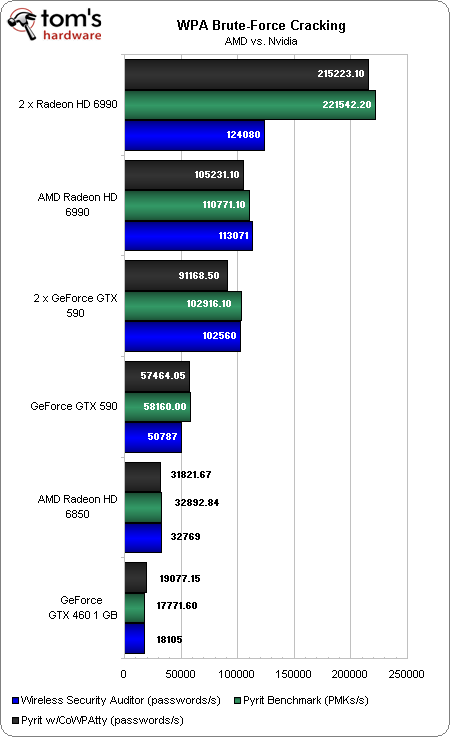
Now, we know how a mid-range graphics card fares against a fairly mid-range CPU. What happens when we start ratcheting up the complexity of our graphics configuration?
It's striking to see how much faster AMD's cards are than Nvidia's. The Radeon HD 6990 sports a greater number of ALUs than the GeForce GTX 590, though. Moreover, it has been shown that there are certain operations AMD's ALUs are able to execute more efficiently.
For some reason, we did have to enable CrossFire to get the second Radeon HD 6990 to appear under WSA (generally, multi-GPU configurations don't need to be running in CrossFire or SLI to operate cooperatively). Both technologies can slow down a brute-force attack because they're designed to help balance GPU workloads. In this case, CrossFire actually works to the detriment of performance. With AMD's multi-card feature disabled, we achieve the expected linear performance scaling in Linux.
Brute-force password cracking in a reasonable amount of time is wholly dependent on the number of cores you wield and the speed at which they operate.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
| Time To Find Crack... | Passwords Between 1 and 6 Characters (Alphanumeric) | Passwords Between 1 and 8 Characters (Alphanumeric) |
|---|---|---|
| Nvidia GeForce GTX 460 1 GB | 35 days (Pyrit w/ CoWPAtty) | 368.9 years (Pyrit w/ CoWPAtty) |
| Nvidia GeForce GTX 590 | 11.6 days (Pyrit w/ CoWPAtty) | 122.5 years (Pyrit w/ CoWPAtty) |
| 2 x Nvidia GeForce GTX 590 | 6.5 days (WSA) | 68.66 years (WSA) |
| AMD Radeon HD 6850 | 20.4 days (WSA) | 214.75 years (WSA) |
| AMD Radeon HD 6990 | 5.88 days (WSA) | 62.24 years (WSA) |
| 2 x AMD Radeon HD 6990 | 3.08 days (Pyrit w/ CoWPAtty) | 32.97 years (Pyrit w/ CoWPAtty) |
Though not common, a pair of GeForce GTX 590s or Radeon HD 6990s in a high-end gaming rig isn't unheard of. Clearly, passwords consisting of seven characters or more are fairly safe. But bear in mind also that we're also looking at worst-case scenarios. The numbers cited above are indicative of searching for a password between 00 and 99, and the right answer ends up being 99. The correct answer is just as likely to be 00, slashing the compute time.
Current page: GPU-Based Cracking: AMD Vs. Nvidia In Brute-Force Attack Performance
Prev Page CPU-Based Cracking: Like Watching Paint Dry Next Page Nvidia's Tesla And Amazon's EC2: Hacking In The Cloud-
fstrthnu Well it's good to see that WPA(2) is still going to hold out as a reliable security measure for years to come.Reply -
runswindows95 The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply -
Pyree runswindows95The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply
Then either beer at your place is really expensive or internet is really cheap. Need 6x12 pack for me. -
compton Thanks for another article that obviously took a lot of work to put together. The last couple of articles on WiFi and archive cracking were all excellent reads, and this is a welcome addition.Reply -
mikaelgrev "Why? Because an entire word is functionally the same as a single letter, like "a." So searching for "thematrix" is treated the same as "12" in a brute-force attack."Reply
This is an extremely wrong conclusion. Extremely wrong. -
What about the permutations of the words?Reply
i.e ape can be written:
ape, Ape, aPe, apE, APe, aPE, ApE, APE.
Thats 2^3=8 permutations. Add a number after and you get (2^3)*(10^1)=80 permutations.
You can write PasswordPassword in 2^16=65536 ways.
How about using a long sentence as a password?
i.e MyCatIsSuperCuteAndCuddly, thats 2^25 permutations :) -
molo9000 Any word on MAC address filtering?Reply
Can you scan for the MAC addresses? It's probably easy to get and fake MAC adresses, or it would have been mentioned.
*scans networks*
12 networks here,
1 still using WEP
10 allowing WPA with TKIP
only 1 using WPA2 with AES only (my network) -
agnickolov Considering my WPA password is over 20 characters long I should be safe for the foreseeable future...Reply -
aaron88_7 "12345, that's amazing, I've got the same combination on my luggage!"Still makes me laugh every time!Reply