Wi-Fi Security: Cracking WPA With CPUs, GPUs, And The Cloud
CPU-Based Cracking: Like Watching Paint Dry
If the guy trying to get into your network is only armed with a conventional desktop processor, don't fret about the security of your WPA-protected network. Those 16 388 SHA1 transformation invocations really bog down brute-force attacks. While we were able to crack WinZip archives at 20 million passwords per second in our previous piece, we're only able to manage about 5000 against WPA using an Intel Core i5-2500K.
| Total Search Time Search, Assuming 5000 WPA Passwords/Second | Passwords Between 1 and 4 Characters | Passwords Between 1 and 6 Characters | Passwords Between 1 and 8 Characters | Passwords Between 1 and 12 Characters |
|---|---|---|---|---|
| Numbers | Instant | 4 minutes | 6.5 hours | 7.5 years |
| Lower-case | 2 minutes | 18 hours | 1.5 years | 662 263 years |
| Alphanumeric (including Upper-case) | 52 minutes | 140 days | 1481 years | Next Big Bang |
| All (Printable) ASCII characters | 5 hours | 5 years | 48 644.66 years | Next Big Bang |
How's this for a sense of futility? There's really no way to brute-force an alphanumeric password longer than six characters using our Core i5 processor. If you're using the entire (printable) ASCII set, a WPA password longer than five characters is reasonably safe.
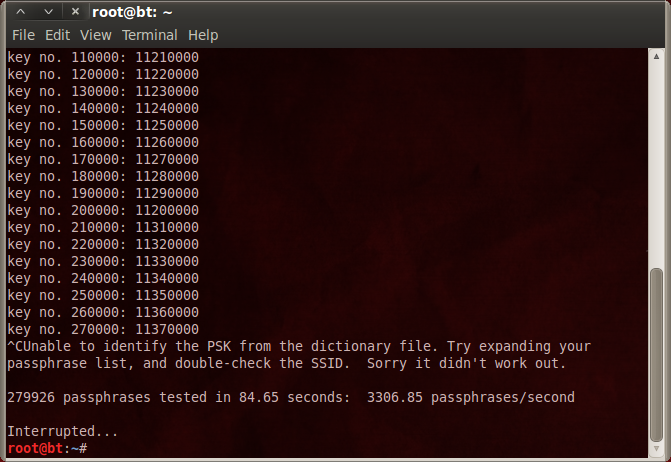
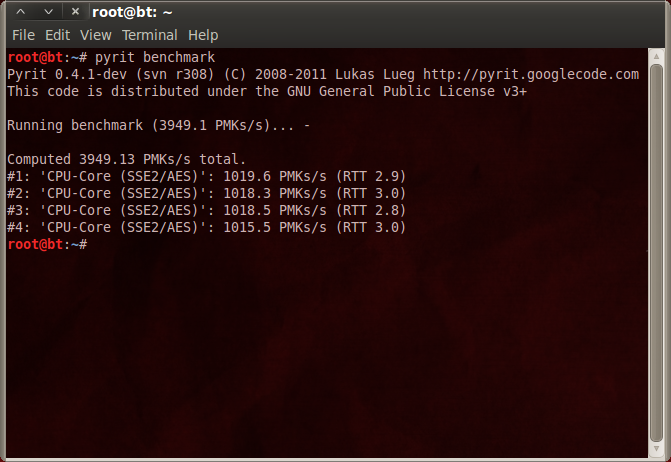
The calculations above assume you're running WSA in Windows, because the Linux route yields slightly worse CPU performance. Using CoWPAtty and Pyrit, we're down to 3307 passwords per second.
In the pages to come, we're going to present two numbers from Linux: the result from Pyrit's benchmark command and the figure reported by CoWPAtty using the Pyrit pass-through function. The Pyrit benchmark command is commonly used to highlight GPU performance, but it doesn't figure in the last couple of transformations needed to go from PMK to PTK. There is some overhead there because the PMK-PTK conversion occurs outside of Pyrit.
CoWPAtty and Elcomsoft's Wireless Security Auditor test the speed at which master keys are checked against the PTK information contained within captured packets. As such, those are the real-world numbers you would see in mounting a brute-force attack against a WPA-protected network.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: CPU-Based Cracking: Like Watching Paint Dry
Prev Page WPA Cracking: It Starts With Sniffing Next Page GPU-Based Cracking: AMD Vs. Nvidia In Brute-Force Attack Performance-
fstrthnu Well it's good to see that WPA(2) is still going to hold out as a reliable security measure for years to come.Reply -
runswindows95 The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply -
Pyree runswindows95The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply
Then either beer at your place is really expensive or internet is really cheap. Need 6x12 pack for me. -
compton Thanks for another article that obviously took a lot of work to put together. The last couple of articles on WiFi and archive cracking were all excellent reads, and this is a welcome addition.Reply -
mikaelgrev "Why? Because an entire word is functionally the same as a single letter, like "a." So searching for "thematrix" is treated the same as "12" in a brute-force attack."Reply
This is an extremely wrong conclusion. Extremely wrong. -
What about the permutations of the words?Reply
i.e ape can be written:
ape, Ape, aPe, apE, APe, aPE, ApE, APE.
Thats 2^3=8 permutations. Add a number after and you get (2^3)*(10^1)=80 permutations.
You can write PasswordPassword in 2^16=65536 ways.
How about using a long sentence as a password?
i.e MyCatIsSuperCuteAndCuddly, thats 2^25 permutations :) -
molo9000 Any word on MAC address filtering?Reply
Can you scan for the MAC addresses? It's probably easy to get and fake MAC adresses, or it would have been mentioned.
*scans networks*
12 networks here,
1 still using WEP
10 allowing WPA with TKIP
only 1 using WPA2 with AES only (my network) -
agnickolov Considering my WPA password is over 20 characters long I should be safe for the foreseeable future...Reply -
aaron88_7 "12345, that's amazing, I've got the same combination on my luggage!"Still makes me laugh every time!Reply