Double Backdoor Exposed In Arris Cable Modems

Bernardo Rodrigues, a Brazilian security researcher, said that he uncovered not one, but two backdoors in some Arris cable modems (TG862A, TG862G, DG860A). Over 600,000 cable customers are affected by this, and according to Rodrigues, the vendor hasn't committed to fixing the software flaws yet. Arris cable modems are used by some of the largest U.S. ISPs, including Comcast, Time Warner Cable, Charter and Cox.
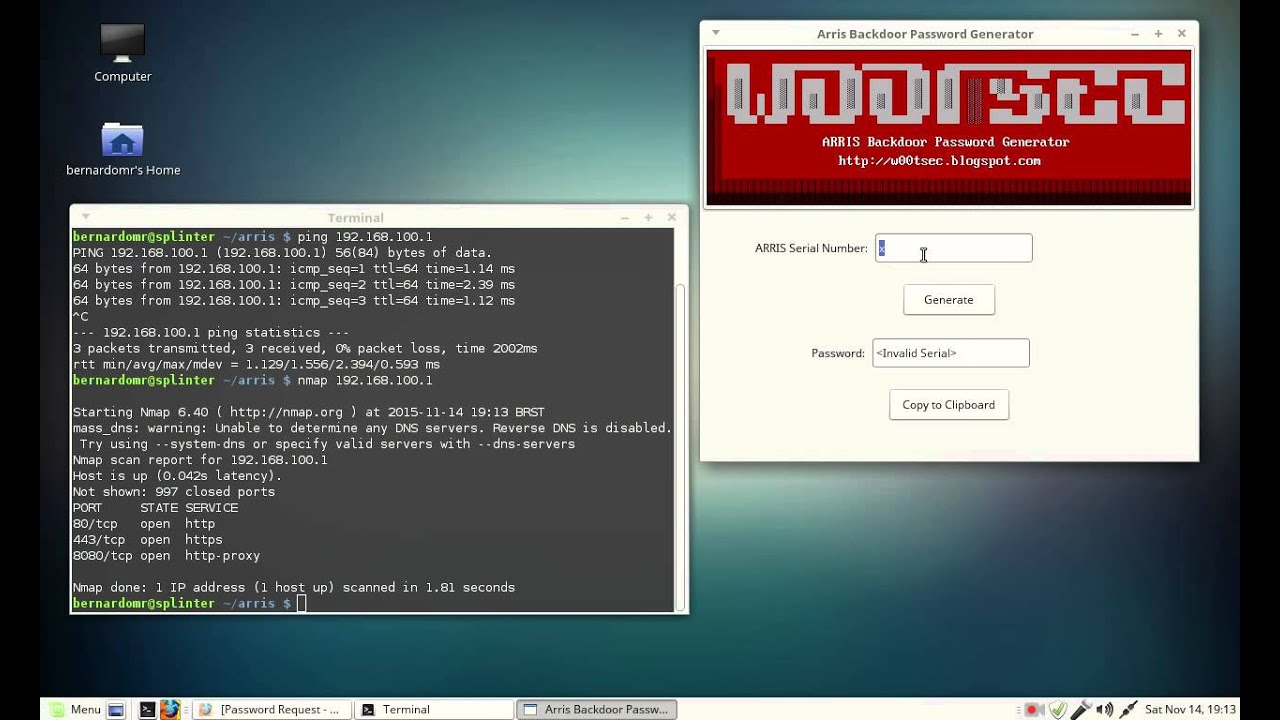
The firmware of the cable modems in question came with an undocumented "libarris_password.so" library that acted as a backdoor by allowing privileged account logins with a different custom password for each day of the year. This backdoor actually dates to 2009, but Arris never fixed it.
When users or attackers exploit this backdoor, they can access the modem through SSH or Telnet ports over a hidden HTTP administrative interface. The default password for the SSH user "root" is "arris." When SSH or Telnet sessions were created, the system launched a "mini_cli" shell that asked for the backdoor's password.
While the researcher was analyzing the backdoor, he discovered that there was another backdoor inside the first backdoor. This second backdoor could be accessed through SSH/Telnet by using the last five digits of the modem's serial number as its password. Once accessed, a full busybox session is opened, giving the attackers even more capabilities.
Rodrigues was asked by the vendor not to disclose the password generating algorithm, but he didn't think this will do much to slow down attackers, considering the extent of the vulnerabilities in these Arris cable modems.
"I'm pretty sure bad guys had been exploiting flaws on these devices for some time (just search for ARRIS DNS on Twitter, for example)," said Rodrigues.
Rodrigues reported the vulnerabilities to the CERT/CC, a major center for addressing Internet security problems that's funded by the U.S. federal government, which has a policy of waiting 45 days before software bugs are disclosed to the public. The researcher and CERT/CC have already waited more than 65 days for Arris to fix the problem, but that hasn't happened yet, which is why the researcher is now making it all public.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Rodrigues believes that if modem software can't be open sourced so everyone could audit the software in their modems, as Vint Cert and others recently suggested, then researchers should at least be allowed to reverse-engineer modem firmware. This way, white hat security experts could find and help fix more security issues in our modems without being potentially liable to lawsuits against them by the modem companies who don't want their vulnerabilities exposed.
______________________________________________________________________

Lucian Armasu joined Tom’s Hardware in early 2014. He writes news stories on mobile, chipsets, security, privacy, and anything else that might be of interest to him from the technology world. Outside of Tom’s Hardware, he dreams of becoming an entrepreneur.
You can follow him at @lucian_armasu. Follow us on Facebook, Google+, RSS, Twitter and YouTube.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
CaedenV So glad my model number isn't listed... but it makes me wonder if I should replace it anyways...Reply -
SkyBill40 As above, I'm glad my SB6141 isn't on that list. This is pretty negligent on the part of ARRIS; however, at least there are some good natured and intelligent people out there to catch things like this and elicit change.Reply -
LotusTeaDragon Is there anything that can be done, in the meantime, for those of us with one of these modems? I have no money to replace a cable modem, and I doubt TWC will issue me a new one because this one isn't secure.Reply -
Ddt3 I am an engineer for a US top ten cable company, and we were given access to the firmware fix for this issue before this article was even posted. The amount of fear mongering in this post is disappointing. Arris came to us and told us themselves and then had the new firmware sent to us two days after. There will be some needed testing of the firmware, but the article is completely wrong about saying Arris hasn't acknowledged or worked to fix this.Reply -
LotusTeaDragon Reply16985970 said:I am an engineer for a US top ten cable company, and we were given access to the firmware fix for this issue before this article was even posted. The amount of fear mongering in this post is disappointing. Arris came to us and told us themselves and then had the new firmware sent to us two days after. There will be some needed testing of the firmware, but the article is completely wrong about saying Arris hasn't acknowledged or worked to fix this.
I sincerely hope you're right. I don't like having a security issue outside of my control. It's one thing to tighten down one's own security holes, and quite another to wait while the necessary steps are carried out well above one's own head. You say that you work for a top ten cable company in the U.S., so do you think this article, as it gets posted elsewhere across the internet, will force your company (and others as well) to move up the release date on this patch? -
Ddt3 Reply16986115 said:16985970 said:I am an engineer for a US top ten cable company, and we were given access to the firmware fix for this issue before this article was even posted. The amount of fear mongering in this post is disappointing. Arris came to us and told us themselves and then had the new firmware sent to us two days after. There will be some needed testing of the firmware, but the article is completely wrong about saying Arris hasn't acknowledged or worked to fix this.
I sincerely hope you're right. I don't like having a security issue outside of my control. It's one thing to tighten down one's own security holes, and quite another to wait while the necessary steps are carried out well above one's own head. You say that you work for a top ten cable company in the U.S., so do you think this article, as it gets posted elsewhere across the internet, will force your company (and others as well) to move up the release date on this patch?
There's many steps that can be taken the mitigate the risk, which most cable companies do in the first place. We block all traffic to the cable modem itself unless it sources from a network we specify. You can't exploit a modem you can't connect to. With that said, public knowledge of the threat makes us move up our time line as much as we can, but that doesn't mean deploying a firmware load we aren't certain won't break or service to customers. This is a concerning exploit, but I think the article overstated the risk to customers. -
alidan Reply16986115 said:16985970 said:I am an engineer for a US top ten cable company, and we were given access to the firmware fix for this issue before this article was even posted. The amount of fear mongering in this post is disappointing. Arris came to us and told us themselves and then had the new firmware sent to us two days after. There will be some needed testing of the firmware, but the article is completely wrong about saying Arris hasn't acknowledged or worked to fix this.
I sincerely hope you're right. I don't like having a security issue outside of my control. It's one thing to tighten down one's own security holes, and quite another to wait while the necessary steps are carried out well above one's own head. You say that you work for a top ten cable company in the U.S., so do you think this article, as it gets posted elsewhere across the internet, will force your company (and others as well) to move up the release date on this patch?
There's many steps that can be taken the mitigate the risk, which most cable companies do in the first place. We block all traffic to the cable modem itself unless it sources from a network we specify. You can't exploit a modem you can't connect to. With that said, public knowledge of the threat makes us move up our time line as much as we can, but that doesn't mean deploying a firmware load we aren't certain won't break or service to customers. This is a concerning exploit, but I think the article overstated the risk to customers.
with this one line "but that doesn't mean deploying a firmware load we aren't certain won't break or service to customers." and the service we have come to expect in the us, i have to doubt the legitimacy of your claim. i'm just remembering the week+ at the end of our stint with direct tv where everything was broken and they told us to pound sand till they learned we had options. -
Calvin Huang ReplyIs there anything that can be done, in the meantime, for those of us with one of these modems? I have no money to replace a cable modem, and I doubt TWC will issue me a new one because this one isn't secure.
Your modem itself shouldn't be directly accessible from WAN IPs. So the main risk is from someone on your LAN or if you're targeted with a very complex CSRF attack. If your LAN is secure, then you just need to avoid going to untrusted sites.