Espionage Group Using Flash And Windows Kernel 'Zero-Days' Ramps Up Attacks Before Patches Propagate
Antivirus and security company Trend Micro announced that it has discovered that the espionage group called “Pawn Storm” (also known as “Fancy Bear,” “Sofacy,” “APT28,” or “Strontium”) has been ramping up attacks against two Flash and Windows kernel zero-day vulnerabilities.
Windows Kernel And Flash Zero-Days
The two vulnerabilities were recently disclosed by Google as being "actively exploited," after Adobe issued an emergency update for its video player plugin, but before Microsoft had a chance to fix its own vulnerability. Microsoft started delivering its patch to Windows machines yesterday. However, it takes some time before it propagates to everyone, if users have their updates set to be deferred or disabled.
Meanwhile, the espionage group seems to want to take advantage of this last window of opportunity and achieve as many of its espionage goals as possible before the zero-day vulnerabilities are rendered useless. According to Trend Micro, Pawn Storm’s targets are embassies and other governmental agencies, which implies it may be sponsored by a nation state.
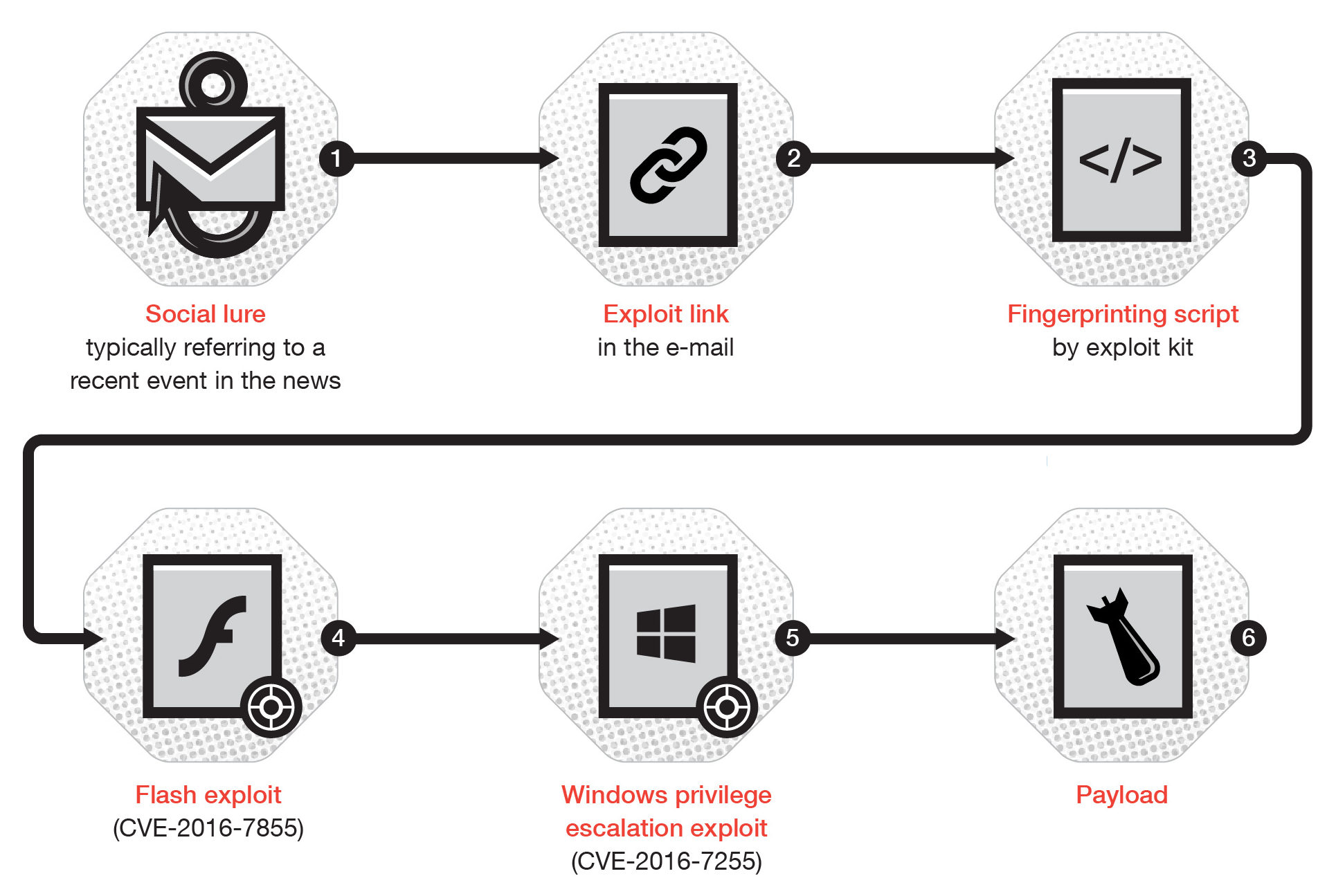
How Pawn Storm Infected Its Targets
The attackers used email spearphishing attacks to try to get the targets to download malware-infected documents that would contain the invitation details to a real cybersecurity conference in November. The Rich Text Format (RTF) document includes an embedded Flash file that downloads additional files from a remote server.
The downloaded Flash file contained an exploit that tried to take advantage of the recently-patched Flash zero-day (CVE-2016-7855). A second file was also downloaded, which Trend Micro said would crash the company’s Microsoft Word program.
The security company also noticed that several other campaigns were launched by the Pawn Storm group between the time the zero-days were discovered by Google’s engineers and until they were patched by Adobe and Microsoft. This would suggest that the group was trying to ramp up its attacks before most devices and Flash players would be patched.
To avoid being one of the group’s victims, Trend Micro strongly recommended users to update their Windows OS and Flash as soon as possible.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.