How Secure Is The Cloud?
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Fine-Grained Access Controls
Are fine-grained access controls in place?
One place where cloud vendors are still playing catch-up to the mainframe computing world is in the area of security policies and access controls. In many cases, access is an all-or-nothing proposition, meaning that once a user authenticates to the cloud, they have the freedom to do a lot of unintentional damage, to start and stop a virtual server, or create other chaos inside the cloud environment.
Some cloud providers are better about this than others, and allow virtual networks within a particular environment or other means of segregating access for individual customers. For example, when the United States Golf Association in Far Hills, New Jersey wanted to build some new Web applications, it went with a smaller cloud provider to get this granularity, because several different applications groups were going to be using the cloud. Jessica Carroll, the managing director of information technologies for the association, says, "We wanted more personal support, and wanted our IT staff to be a little closer to our cloud vendor. We use a VPN to connect to our cloud network, but have two different development groups that are working on different servers hosted there. We set things up so that each group can only see each other's resources, so that developers can restart virtual servers or make other changes without affecting the other's equipment."
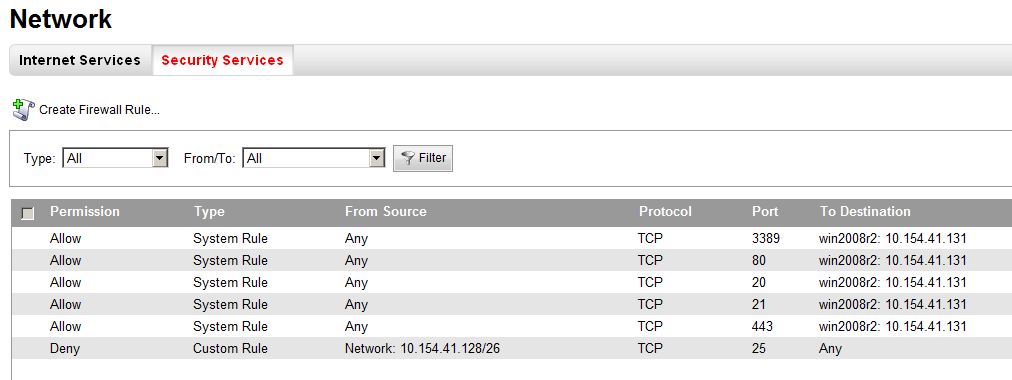
VMware has only recently added a level of granularity to its vSphere line of products. Its vShield Zones product includes a hypervisor-based firewall to enforce network and port connections on each virtual server, and set up a full collection of policies and firewall rules within the virtual environment. Users of Verizon's Computing as a Service can set up firewall rule sets by port and protocol for each virtual server, as you can see in this screenshot.
There are also third-party security tools, such as Hytrust's Appliance for VMware, which allows more granular control over which users have what kind of access to particular virtual servers. To get an idea of how Hytrust's software operates, check out this screencast video that I prepared for them here.
We can expect other cloud computing vendors to do a better of job with granular access in the near future.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Fine-Grained Access Controls
Prev Page Data Encryption Next Page Redundant InfrastructureDavid Strom is the former editor-in-chief at Tom's Hardware and the founding editor-in-chief of Network Computing magazine. He has written thousands of articles for dozens of technical publications and websites, and written two books on computer networking.
-
fstrthnu Answer: It's safe IF you play your cards right, but almost all of the time you can forget about decent securityReply -
You haven't really addressed many of the security concerns IT pros have about "the cloud". Who potentially has access to my data, what controls are in place to keep that data safe (ie could a rouge employee rip backup of my DB and take it home)? How are other legal situations handled, such as warrants/requests for data from law enforcement, will the customer be notified, will the vendor simply comply, etc? What happens *IF* the cloud vendor goes out of business one day, where is my data (one would assume there would be warning signs before this happens, but stranger things have happened)? There are tons of questions with not many good answers out there.Reply
-
babachoo This article has been brought to you by domestic datamining organizations and the people they have in their pockets.Reply -
gonebamboo Check out this cloud-based (Software as a Service) platform and its security architecture.Reply
http://www.otakhi.comhttp://www.otakhi.com/pages/security.html -
ludikraut This article barely scratches the surface of security issues surrounding cloud computing. It reads more like an executive summary than something I would expect to see on Tomshardware - very disappointing.Reply -
Cloud computing is overrated. Your data will never be secure in someone else's hands. Any encryption can be broken with time.Reply
-
I didn't really see any mention of on-site encryption in this article, only transport encryption. Also, who assures us that claims made regarding security are entirely true instead of being marketing word-play which seems so popular these days. Only when a cloud service publishes results done by a third party auditor that I trust will I use them.Reply
-
gtaker If you are in the external cloud with your company your data will be compromise.. I'm 100% sure of that... we look at this cloud stuff 8 years ago and came to that conclusion if you need to do it, do it inside your company not outside...Reply -
sadams04 Security is always a concern, but my main concern with the cloud is around someone else being responsible for up-time / availability. Those priorities rarely line up across multiple companies. While you may recover lost revenue through a breach in service level agreements, you can't recover customer perceptions and experiences in the same way.Reply -
perrakis There's an updated version of the Ponemon Cloud Security Study available from the report's sponsor, Dome9: http://www.dome9.com/resources/ponemon-cloud-security-study.Reply
Incidentally, Dome9 offers free cloud security for an unlimited number of servers. You can check them out at http://www.dome9.com. Essentially, their value prop is the ability to close administrative ports on a remote cloud server and make access available on demand. This is important in the cloud where your servers operate outside your traditional network, and leaving ports open exposes them to hackers, brute force attacks, and exploits.