Flexible Data Storage Across Networks: iSCSI put to the Test
How ISCSI Works
Source: Adaptec
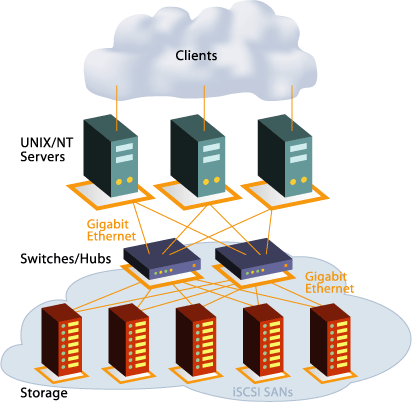
The diagram above details the working principles behind iSCSI. The storage systems are supposed to be able to utilize network infrastructure independently of servers. The consolidation of storage subsystems we discussed before only means that a storage system can be accessed from several servers, with minimal management complexity. Alternatively, it is also possible to offer the additional storage space in existing systems, and attach them via iSCSI.
The advantages of this approach are many, and mostly pretty obvious. Many businesses already have an efficient network infrastructure in place, usually consisting of mature and reliable technology such as Ethernet. No new technologies need to be introduced, tested and validated for the incorporation of iSCSI systems or others such SANs (Storage Area Networks). Additionally, there is usually no need to hire expensive specialists for implementation.
This means any network administrator can manage iSCSI clients and servers with very little training, since these are subordinate to the existing systems and rely on well-established technology. Also, iSCSI can be considered a high-availability solution, since iSCSI servers can be connected to several switches or network segments. Finally, the architecture is scalable by design, thanks to Ethernet switching technology.
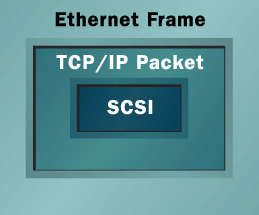
In principle, an iSCSI server (target) can be realized either in software or in hardware. However, due to the high CPU load of software implementations, it works best with dedicated hardware. The main workload of the iSCSI server consists of embedding SCSI packets in TCP/IP packets, as mentioned earlier, which must be done in real time. A software solution incorporates the CPU(s) into the iSCSI system, while a hardware solution can rely on a TCP/IP-offload unit as well as a SCSI-offload unit.
Through an iSCSI client (initiator) the storage resources on the iSCSI-server can now be integrated into the client system as a device, which can be used as if it were a local drive. The great advantage of this compared to a classic network share is in the area of security, as iSCSI puts great emphasis on proper authentication of the iSCSI packets, which are transported through the network encrypted.
Of course, the attainable performance will be slightly lower than that of a local SCSI system due to the network's higher latencies. Still, today's networks, with their bandwidths of up to 1Gbit/s (=128 MB/s), already have a lot of capacity, most of which is not being fully utilized.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Every iSCSI node possesses its own name, which is 255 Bytes long, and an alias, both of which are independent of its IP address. This way, a storage array in the network can still be located even after it has been moved to another subnet.
Source: Adaptec
Current page: How ISCSI Works
Prev Page Testing ISCSI-based Network Storage Solutions Next Page ISCSI In Practice
Patrick Schmid was the editor-in-chief for Tom's Hardware from 2005 to 2006. He wrote numerous articles on a wide range of hardware topics, including storage, CPUs, and system builds.