Is Data Encryption Worth Destroying Your NAS' Performance?
Three vendors of network-attached storage, Qnap, Synology, and Thecus, sent over Intel Atom-based NAS servers to test the effects of protecting your data via encryption. But performance and configuration options are not identical, as our testing shows.
Thecus N4200
Thecus positions the N4200 as a business solution for small- to medium-sized companies, and it costs around $660. Customers can equip the NAS with up to four hard drives, and then apply RAID 0, 1, 5, 6, or 10. You can also integrate the N4200 using iSCSI. Again, it comes with a dual-core Intel Atom D510 processor and 1 GB of DDR2 SDRAM.
Encryption Setup
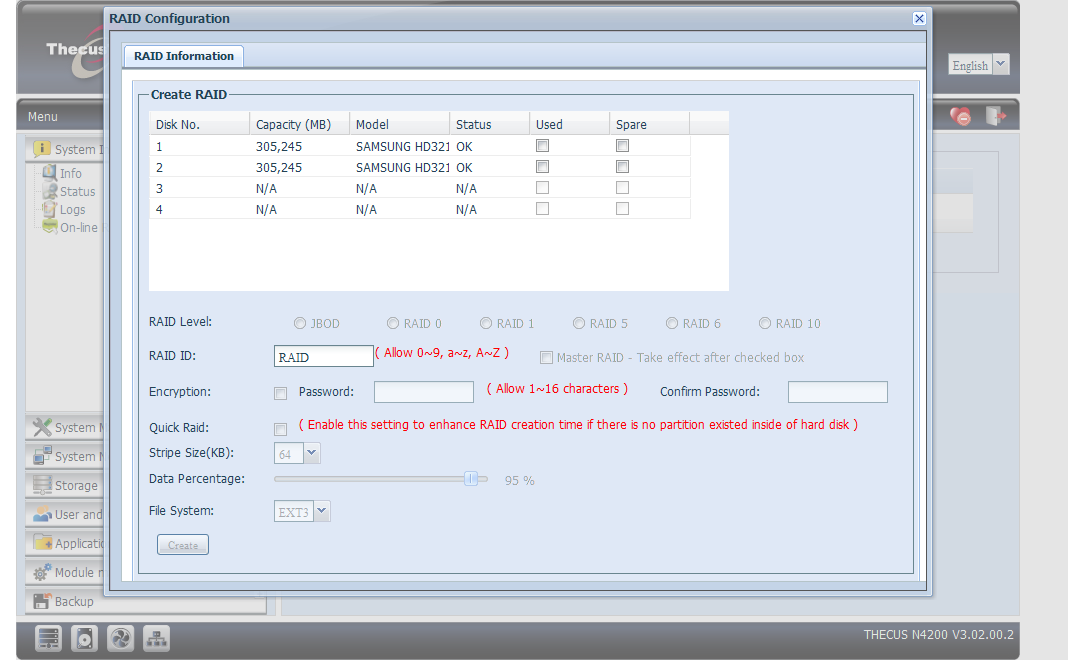
The encryption setup is easily accessible via Thecus' Web interface, similar to the other two devices we're testing. When creating a RAID array, you can enable the encryption option. After the array built, its storage space is completely encrypted via a partition-level approach. The encryption password can be any string consisting of anywhere from one to sixteen characters.
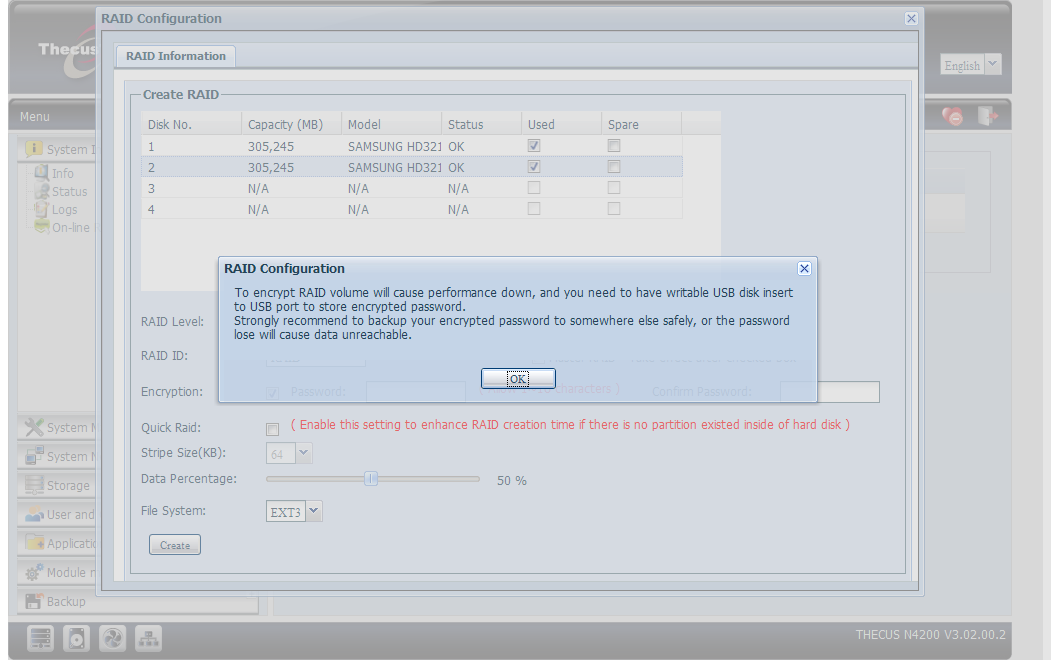
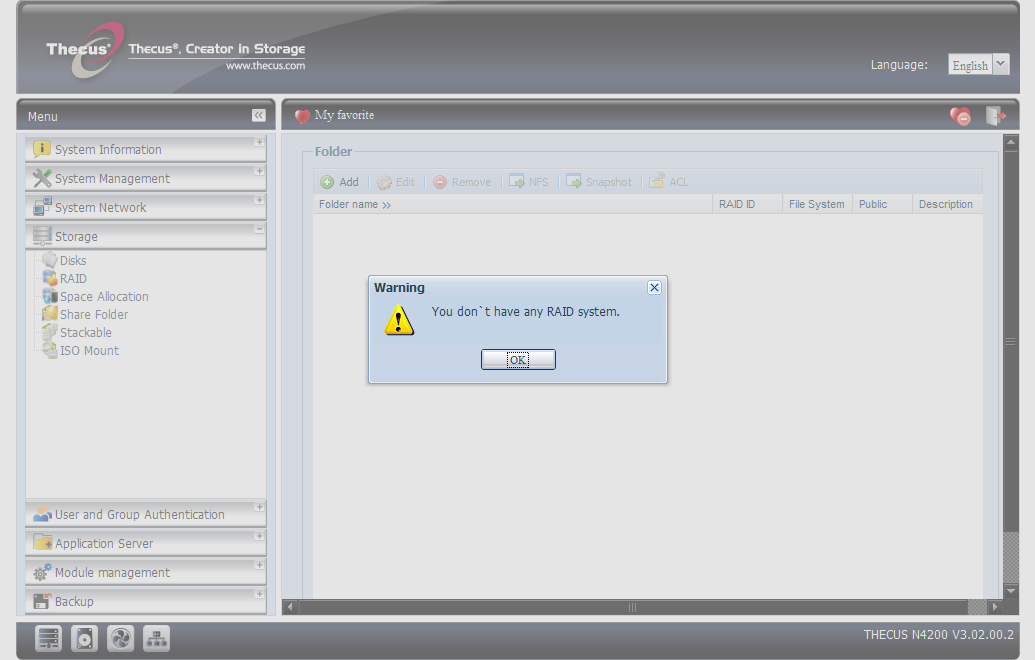
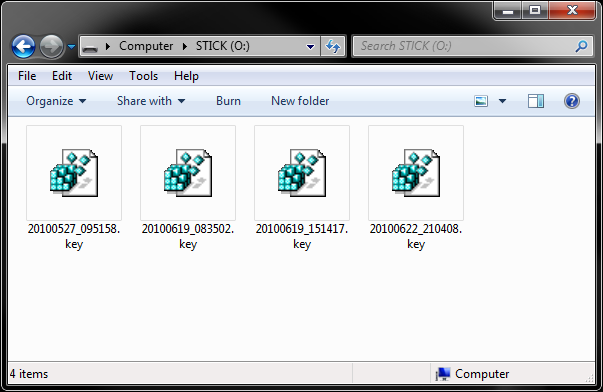
Here's another interesting detail: you need an external drive connected to one of the N4200's USB ports when you create an encrypted partition on Thecus' NAS. This is just one more hassle, of course, but it's all in the name of security. For practical reasons, you'll probably want to use a thumb drive, on which key to decrypt data stored on the partition is stored.
Restart with the USB Drive
Once the encryption process is complete, the USB drive can be removed. Thecus recommends that you make a copy of the key and keep both the USB drive and the file in a safe place.
The USB drive is also required whenever you migrate or expand the RAID configuration. Once you're done with it, put it back in its safe place.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
When creating the RAID configuration, you must select the option “Encryption” and enter a password in order to use the feature.
When creating an encrypted partition, Thecus notifies you of the fact that a USB drive is required and that this drive should be kept at a safe location. The dialog window does not mention that encryption might slow down data throughput, but the PDF manual does.
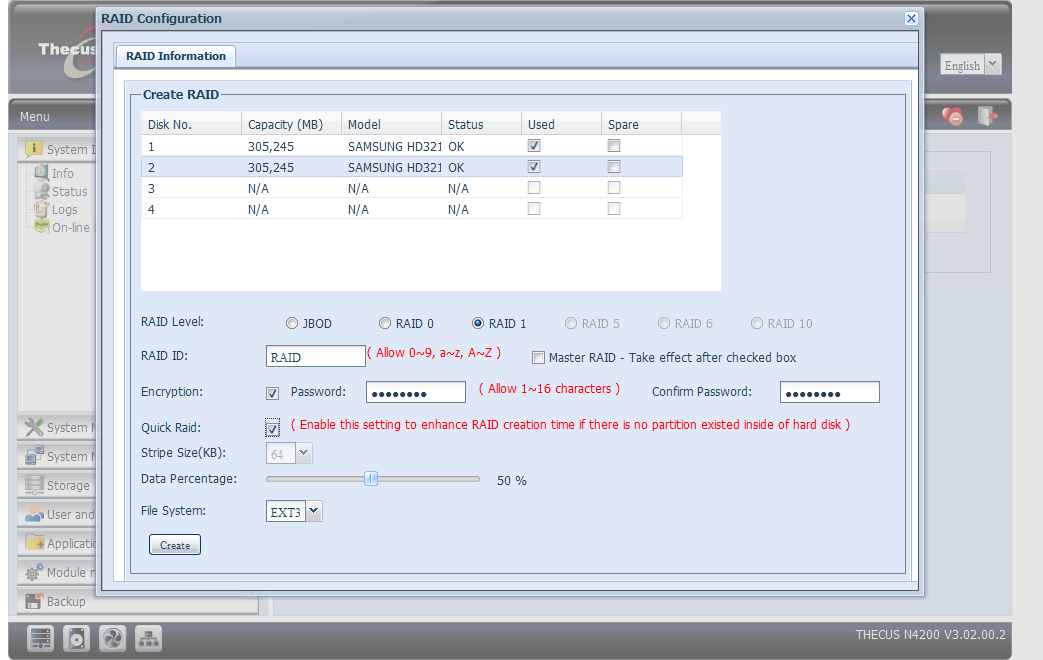
A password must be entered if the encryption mode is selected, and the encryption/decryption key file is generated based on what you enter.
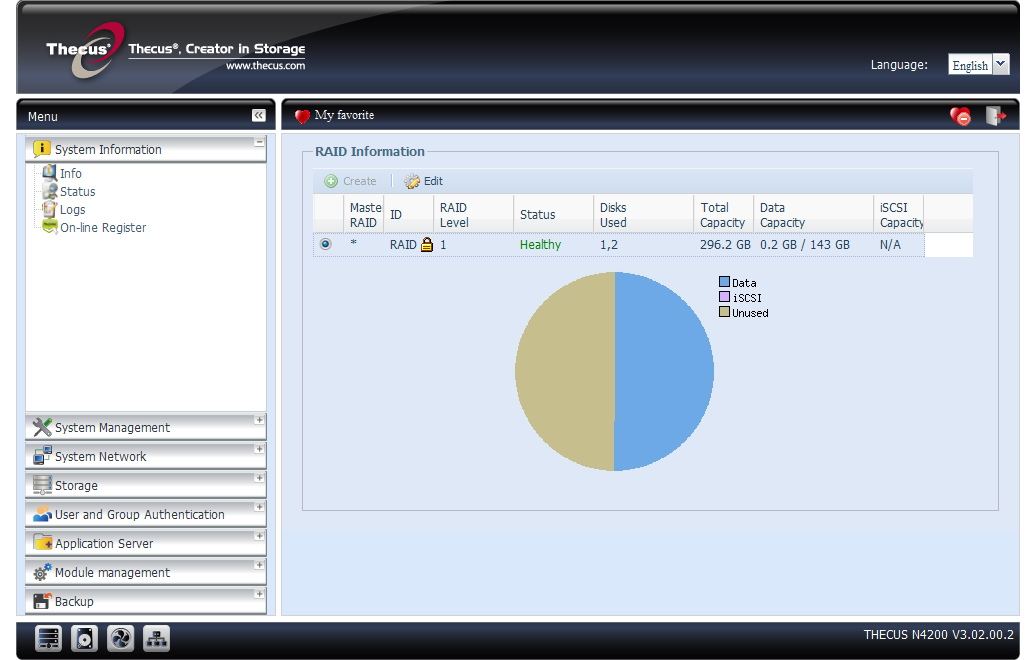
A padlock icon indicates that the partition is encrypted when the operation is successfully completed.
Be careful: if the NAS is started without the USB drive, it does not indicate that there are any RAID configurations available.
The key files required for encryption/decryption are stored on an external drive that should be kept at a safe location, protected from unauthorized access.
-
und3rsc0re You guys should do this test using a few solid state drives, im interested to know the results if encryption affects the performance of them much.Reply -
compton What about a Core i5 or better based server? You could turn an i5 with aes-ni into a cheap server for the same price as these diskless enclosures. Couldn't it be turned into a Linux based NAS with hardware encryption? I'm not hip to all of the issues, but that was my first thought.Reply -
rhangman What about a VIA based solution? Low power like an Atom, cheap and has the padlock hardware encryption engine.Reply
http://www.via.com.tw/en/initiatives/padlock/hardware.jsp -
maybe you could test the other nas´tooReply
http://www.tomshardware.com/charts/multi-bay-nas-charts-2011/benchmarks,121.html
already has a performance overview so just add encryption test -
huron I like what you guys are doing here at Toms...very interesting article. Any chance you guys can get your hands on a better processor to see what the results would be - I know how resource heavy encryption/decryption can be, and worry these don't really have enough horsepower to handle the job well.Reply
Continue this as a series with better CPUs? -
bwcbwc The implication for all of these devices is that the data is encrypted/decrypted within the device, which in turn means that the data is transmitted over the network in unencrypted form.Reply
The risk of a packet sniffer on the LAN seems a lot higher than someone walking out the door with your NAS array (or a piece of it), so I think you need to weigh your priorities when you choose this type of solution. If you are ready to address the physical security of data on a network attached drive, you should already have taken steps to ensure the security of the data during transmission. -
freggo What if one where to use TrueCrypt partitions on these servers instead ?Reply
I tested it extensively first and use it now for 2 years on my regular drives, hardly a 'noticable' performance hit compared to the unencrypted drives in the PC and 'zero' errors or problems so far.
-
Prey In a commercial environment, especially medical, hell yes! Go to the HITECH Act and see the breach list over 500 due to unencrypted files that are stolen or lost.Reply
It shouldn't be a performance issue, but more a, is it worth the risk issue. -
Niva Definitely a good article, I'd been thinking about buying the Thecus. Tests with TrueCrypt would be appreciated since that's my tool of choice.Reply