Is Data Encryption Worth Destroying Your NAS' Performance?
Three vendors of network-attached storage, Qnap, Synology, and Thecus, sent over Intel Atom-based NAS servers to test the effects of protecting your data via encryption. But performance and configuration options are not identical, as our testing shows.
Synology DS1010+
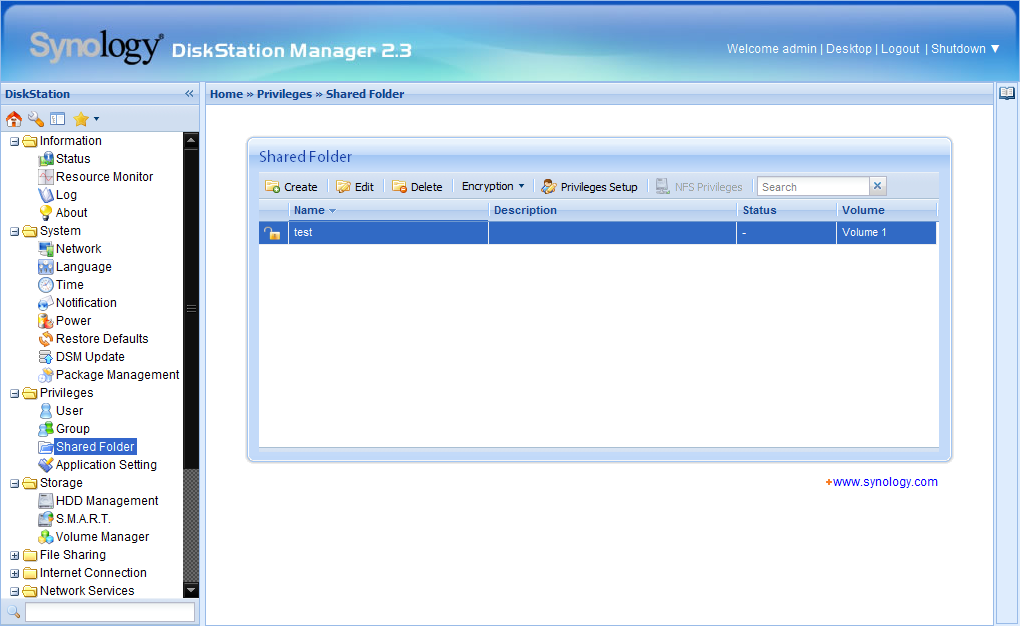
The Synology DS1010+ also comes with a dual-core Intel Atom D510 and 1 GB of DDR2 RAM. But unlike the devices from Qnap and Thecus, it encrypts data at a file level, instead of at a partition level. This is implemented via eCryptfs, which is rather similar to the popular TrueCrypt software. It creates a container that can grow or shrink in size dynamically as needed. The data stored in these container files is individually encrypted, while the information used to decrypt the files is stored in the unencrypted file header. In the following screenshots, we can see just how such a container is created, and what information from the encrypted file in it can be displayed directly in the Linux console.
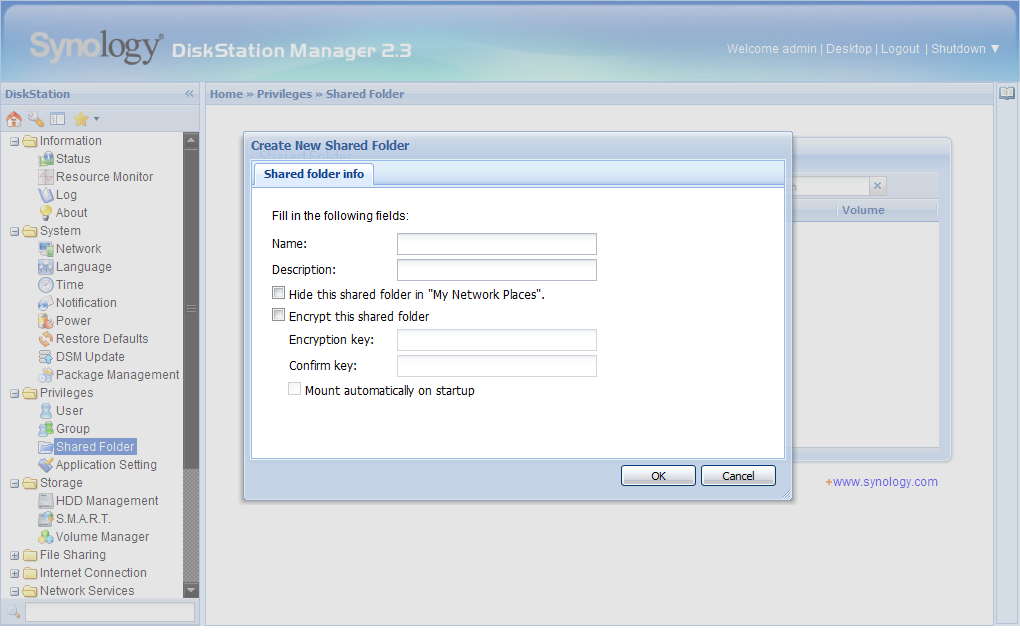
Since Synology uses eCryptfs, the RAID arrays have to be configured and ready to go before enabling encryption. Setting up the encryption can be done when configuring file or folder sharing.
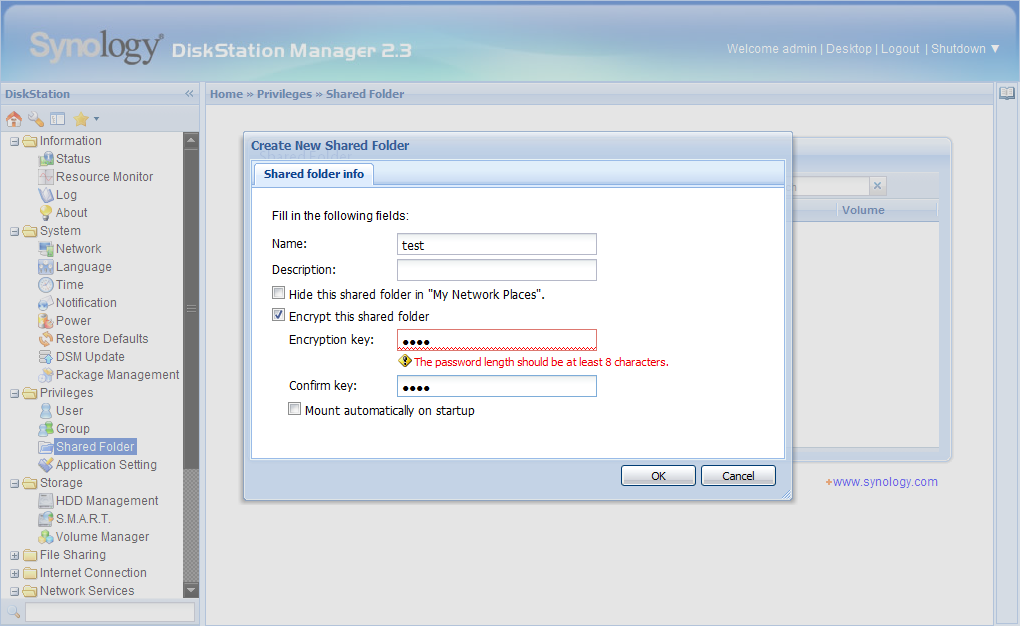
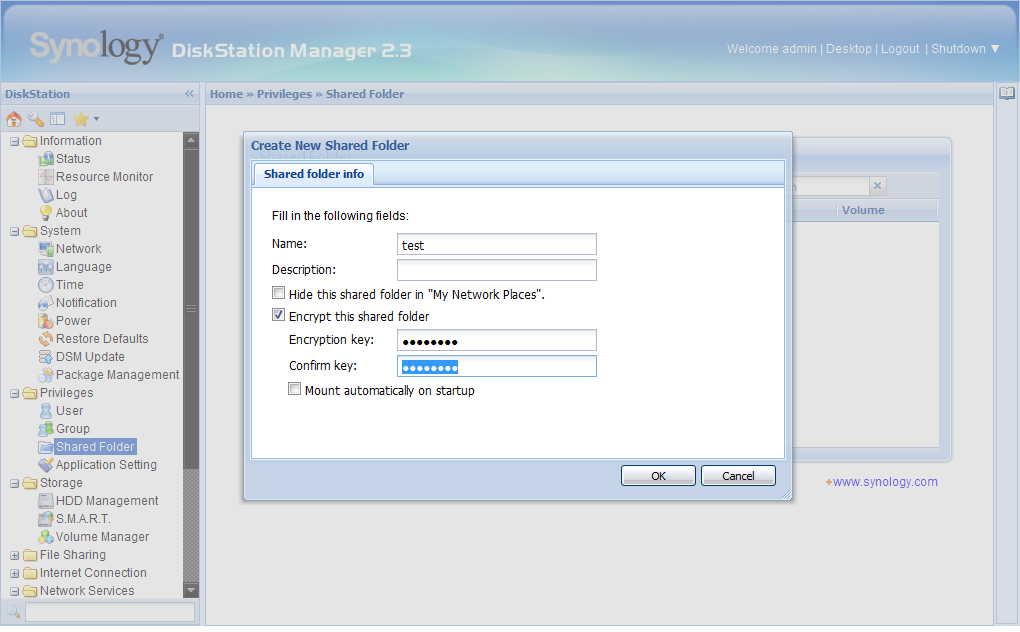
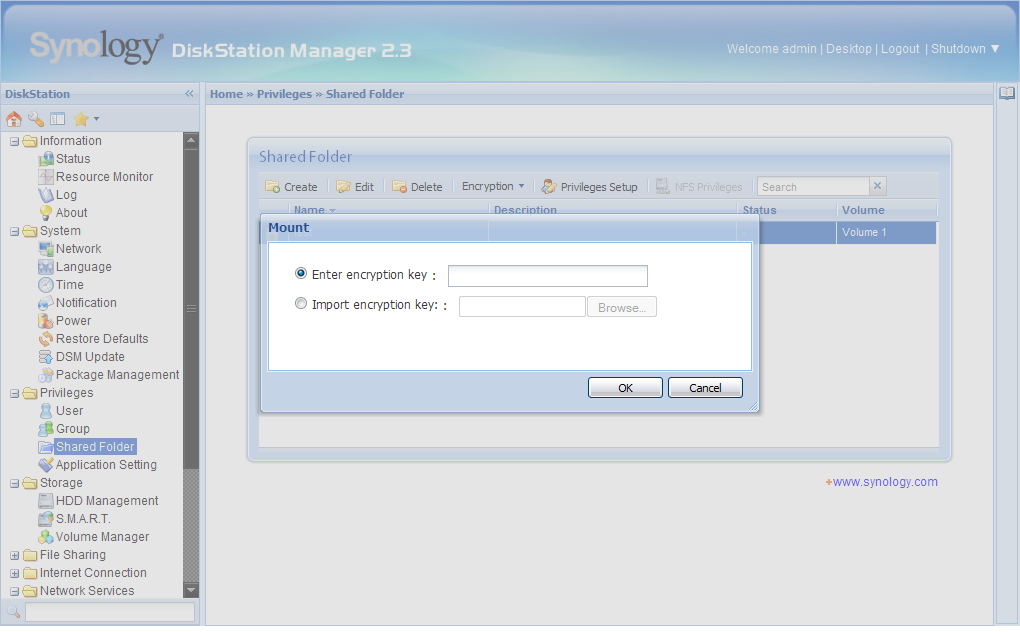
When sharing a folder there is a menu item in the Web interface called “Encrypt this shared folder.” This also requires the user to enter a password string that the encryption is based upon, and it has to be at least eight characters long.
If the menu item “Mount automatically on startup” is selected, the password is saved on the NAS device. This option allows you to automatically mount the encrypted folder after rebooting the device. But just like with the Qnap NAS, you should not use this feature if you are concerned about security (and if you're enabling encryption, there's a fair chance that you are).
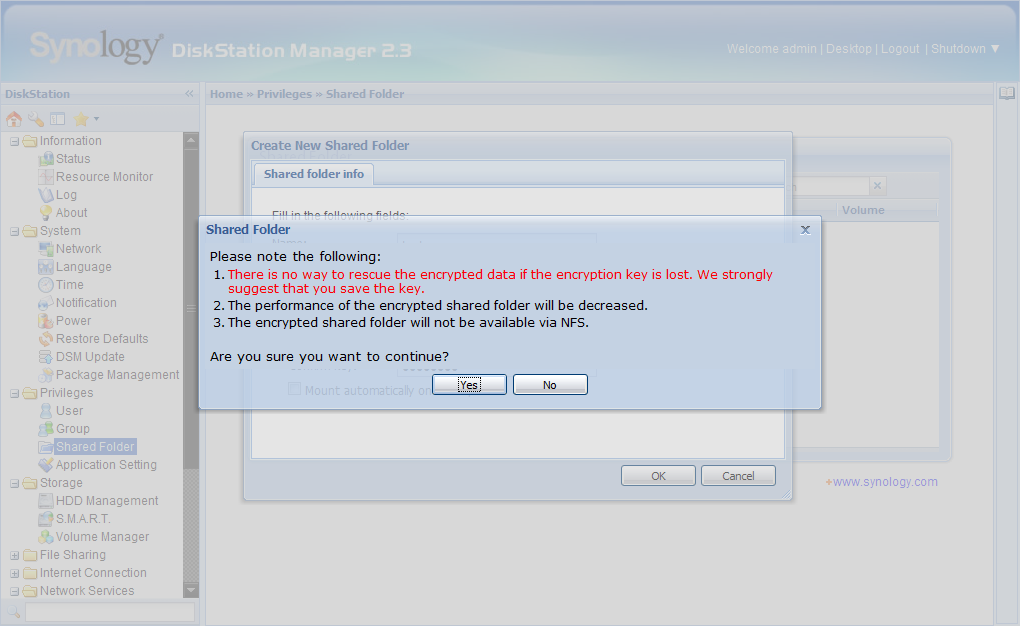
Again, we receive a dialog box warning the user to store the key in a safe place, as the data cannot be decrypted without it. It also says that there might be a performance impact as a result of the encryption, and that the folder will not be available via NFS.
After confirming the operation, the encrypted folder is available just a few seconds later and the download of the key file that was generated from the password you entered is automatically accessed.
If you choose not to store the encryption password on the NAS, you can still access the encrypted folders after rebooting. This can be done either by entering the password via the Web interface or by using the downloaded key file.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
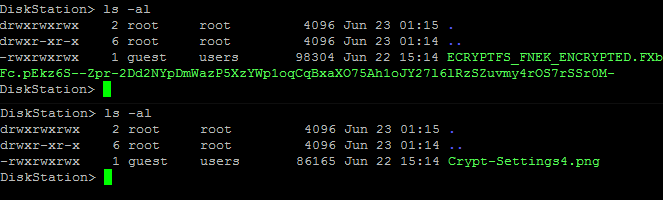
If the encrypted folders are not mounted via eCryptfs, you just see a list of unintelligible letters and numbers when displaying the drive contents in the Linux console. After mounting them using the password, they are displayed as usual.
-
und3rsc0re You guys should do this test using a few solid state drives, im interested to know the results if encryption affects the performance of them much.Reply -
compton What about a Core i5 or better based server? You could turn an i5 with aes-ni into a cheap server for the same price as these diskless enclosures. Couldn't it be turned into a Linux based NAS with hardware encryption? I'm not hip to all of the issues, but that was my first thought.Reply -
rhangman What about a VIA based solution? Low power like an Atom, cheap and has the padlock hardware encryption engine.Reply
http://www.via.com.tw/en/initiatives/padlock/hardware.jsp -
maybe you could test the other nas´tooReply
http://www.tomshardware.com/charts/multi-bay-nas-charts-2011/benchmarks,121.html
already has a performance overview so just add encryption test -
huron I like what you guys are doing here at Toms...very interesting article. Any chance you guys can get your hands on a better processor to see what the results would be - I know how resource heavy encryption/decryption can be, and worry these don't really have enough horsepower to handle the job well.Reply
Continue this as a series with better CPUs? -
bwcbwc The implication for all of these devices is that the data is encrypted/decrypted within the device, which in turn means that the data is transmitted over the network in unencrypted form.Reply
The risk of a packet sniffer on the LAN seems a lot higher than someone walking out the door with your NAS array (or a piece of it), so I think you need to weigh your priorities when you choose this type of solution. If you are ready to address the physical security of data on a network attached drive, you should already have taken steps to ensure the security of the data during transmission. -
freggo What if one where to use TrueCrypt partitions on these servers instead ?Reply
I tested it extensively first and use it now for 2 years on my regular drives, hardly a 'noticable' performance hit compared to the unencrypted drives in the PC and 'zero' errors or problems so far.
-
Prey In a commercial environment, especially medical, hell yes! Go to the HITECH Act and see the breach list over 500 due to unencrypted files that are stolen or lost.Reply
It shouldn't be a performance issue, but more a, is it worth the risk issue. -
Niva Definitely a good article, I'd been thinking about buying the Thecus. Tests with TrueCrypt would be appreciated since that's my tool of choice.Reply