Wi-Fi Security: Cracking WPA With CPUs, GPUs, And The Cloud
WPA Cracking: It Starts With Sniffing
There are three steps to penetrating a WPA-protected network.
- Sniffing: Intercepting packets in order to get the data necessary to perform an attack.
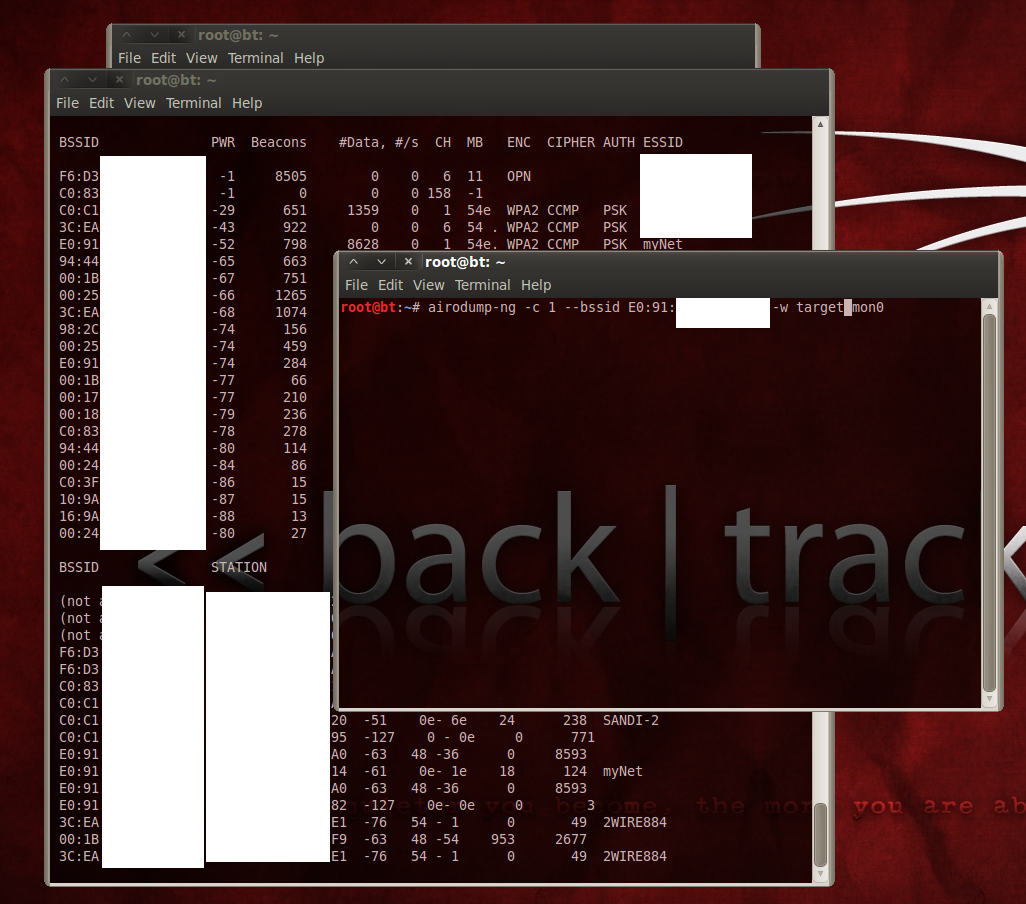
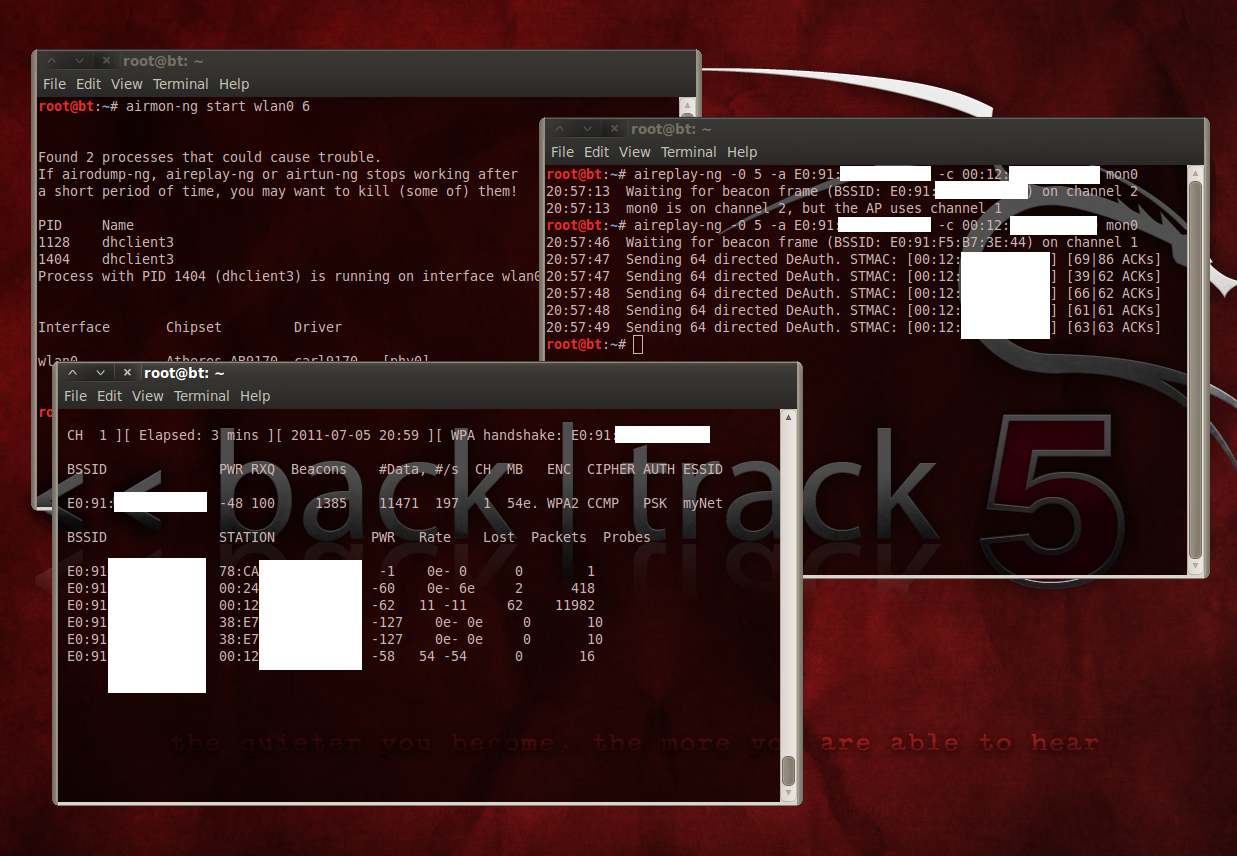
- Parsing: Inspect the harvested packets to see if there's a valid handshake. This is the critical step. The information you're trying to capture consumes less than 1 MB, but it's important that it includes packets that contain PTK authentication information. This means that someone needs to log on to the network while you're sniffing.
- Attacking: Employ brute-force password cracking.
The entire process of sniffing, parsing, and attacking tends to be modular, but the exact procedure is a little different, depending on the operating system. At the moment, Linux is the preferred route for many networking ninjas, but there are tools in Windows that streamline the process too.
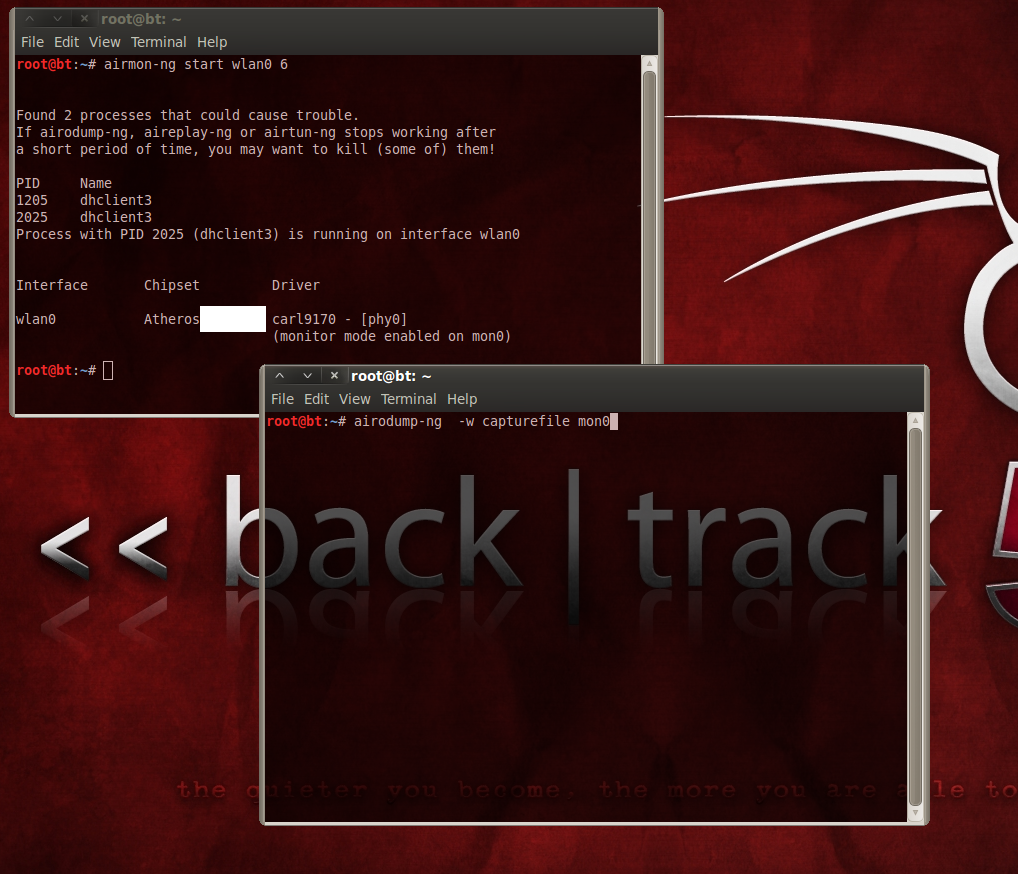
No matter what software route you take, making this happen isn't as easy as typing in the right commands. Getting past the sniffing step is perhaps the most difficult part because it requires a particular type of wireless card. Specifically, you need one that has drivers able to provide access to low-level 802.11 protocol information. The majority of wireless cards don't cut it because they use a driver that filters the RAW 802.11 packets and hides them from the upper layers of the operating system.
But the right equipment doesn't cost an arm and a leg. Many compatible wireless cards cost less than $50. Ultimately, skill is what separates the beginners from hackers. Without giving you the blow-by-blow, these screenshots give you an idea of how easy it can get. In all, I spent about 10 minutes getting the information needed to set up the password attack, which is step three.
There is one caveat worth mentioning. Capturing the authentication information (four-way handshake) requires you to monitor for the packets transmitted when a client attempts to connect with an access point (AP). The act of connecting is what generates the packets that hackers are interested in exploiting. If there are no wireless clients connected, a hacker must wait for someone to establish a connection. Checking your morning email just got a little more real, didn't it?
If a client is already connected, it is still possible to capture the requisite information by forcing a reconnection attempt. How, you ask? By targeting a specific user and booting them off the network with one simple command-line instruction.
After we're done sniffing, we have to use a cracker to brute-force every master key against the PTK. Between Linux and Windows, there are fewer than 10 programs that actually perform the brute-force attack. The majority of them, such as Aircrack-ng and coWPAtty, rely on a dictionary attack. That means you need to provide a discrete database of words to check against. In the end, there are really only two programs that perform truly random brute-force attacks: Pyrit (combined with John the Ripper in Linux) and Elcomsoft's Wireless Security Auditor (Windows).
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
It should come as no surprise that coordinating an attack in Linux is more involved than Windows. Aircrack-ng is used to sniff and parse. Then you switch to Pyrit in pass-through mode via coWPAtty (PMK-PTK conversion) for the brute-force attack. In comparison, Elcomsoft offers a much more fluid experience with its Wireless Security Auditor. Admittedly, that app is so easy to use, a caveman could do it. It sniffs (provided you have an AirPcap adapter), parses, and attacks a WPA-protected network in no more than 10 mouse clicks.
Although cracking is slightly more complicated to pull off in Linux, it's also less expensive. The fully-automated version of WSA runs $1199, but it lets you use up to 32 CPU cores and eight GPUs, it adds sniffer support, and it features support for dedicated cracking hardware like Tableau's TACC1441 (the serious FPGA-based stuff). The standard version is more limited. It's restricted to two CPU cores and one GPU and only costs $399. You do need a third-party app for the sniffing step, though.
| OS | Linux | Windows | Windows (fully automated) |
|---|---|---|---|
| Sniffing | Aircrack-ng | Aircrack-ng | Wireless Security Auditor Pro Edition |
| Parsing | Aircrack-ng | Wireless Security Auditor Std. Edition | Wireless Security Auditor Pro Edition |
| Cracking | Pyrit via CoWAPtty | Wireless Security Auditor Std. Edition | Wireless Security Auditor Pro Edition |
| Software Cost | Free | $399 | $1199 |
Brute-Force Cracking
If you want more information on how brute-force attacks work, we suggest that you read page four of Harden Up: Can We Break Your Password With Our GPUs?. In a nutshell, brute-force attacks involve "guessing and checking" on a much larger and faster scale in an attempt to defeat passwords.
Unlike online banking passwords, WPA doesn't have any authentication restriction. If you're persistent enough, you can keep guessing passwords until hell freezes over.
| Available Characters Using The English Language | Possible Passwords, Two Characters | Possible Passwords, Four Characters | Possible Passwords, Six Characters |
|---|---|---|---|
| Lower-case | 676 | 456 976 | 308 915 776 |
| Lower- and Upper-case | 2704 | 7 311 616 | 19 770 609 664 |
| Lower-case, Upper-case, and Numbers | 3844 | 14 776 336 | 56 800 235 584 |
| All (Printable) ASCII Characters | 8836 | 78 074 896 | 689 869 781 056 |
Brute-force attacks are only effective when they can check passwords at a high speed, as the number of potential passwords grows exponentially with a larger character set and longer password length (possible passwords =n[password length] , where n is the number of possible characters).
Most of the time, hackers don't know the length of your password, though. That's why they have to perform an exhaustive search of all possible combinations, starting from a list of single-character options.
Current page: WPA Cracking: It Starts With Sniffing
Prev Page Understanding WPA/WPA2: Hashes, Salting, And Transformations Next Page CPU-Based Cracking: Like Watching Paint Dry-
fstrthnu Well it's good to see that WPA(2) is still going to hold out as a reliable security measure for years to come.Reply -
runswindows95 The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply -
Pyree runswindows95The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply
Then either beer at your place is really expensive or internet is really cheap. Need 6x12 pack for me. -
compton Thanks for another article that obviously took a lot of work to put together. The last couple of articles on WiFi and archive cracking were all excellent reads, and this is a welcome addition.Reply -
mikaelgrev "Why? Because an entire word is functionally the same as a single letter, like "a." So searching for "thematrix" is treated the same as "12" in a brute-force attack."Reply
This is an extremely wrong conclusion. Extremely wrong. -
What about the permutations of the words?Reply
i.e ape can be written:
ape, Ape, aPe, apE, APe, aPE, ApE, APE.
Thats 2^3=8 permutations. Add a number after and you get (2^3)*(10^1)=80 permutations.
You can write PasswordPassword in 2^16=65536 ways.
How about using a long sentence as a password?
i.e MyCatIsSuperCuteAndCuddly, thats 2^25 permutations :) -
molo9000 Any word on MAC address filtering?Reply
Can you scan for the MAC addresses? It's probably easy to get and fake MAC adresses, or it would have been mentioned.
*scans networks*
12 networks here,
1 still using WEP
10 allowing WPA with TKIP
only 1 using WPA2 with AES only (my network) -
agnickolov Considering my WPA password is over 20 characters long I should be safe for the foreseeable future...Reply -
aaron88_7 "12345, that's amazing, I've got the same combination on my luggage!"Still makes me laugh every time!Reply