Protect Your Data With Encryption
Encryption Algorithm, Performance, Rescue Disc
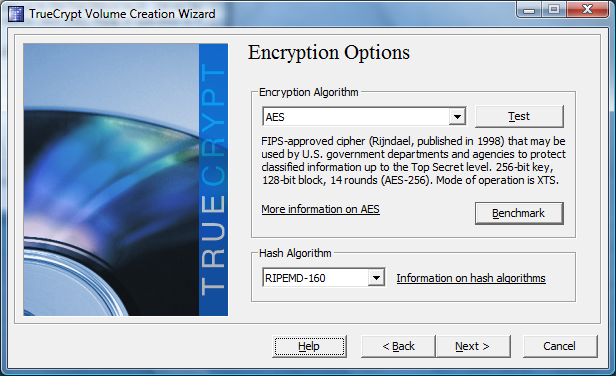
Now things get a little more technical: the fifth window provides you with the option to pick your desired algorithm, to check its performance on your system and drive, and also to select the hash algorithm you want TrueCrypt to use. We tried two different options for our testing: on the first run we chose AES, while the second test used AES-Twofish-Serpent, which offers double encryption at the cost of reduced performance.
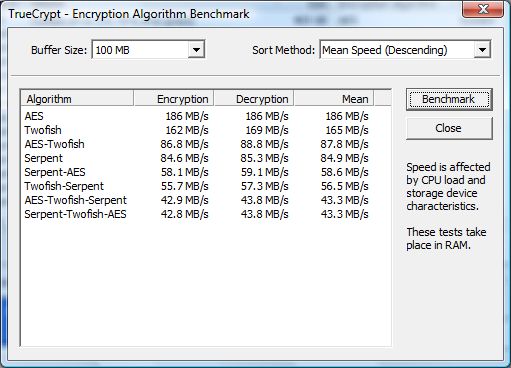
The TrueCrypt encryption wizard includes a benchmarking tool, which you can access when selecting the encryption algorithm (see above). The benchmark shows varying performance and highly depends on the processor, followed by the drive you are about to encrypt: AES and Twofish provide highest throughput on our Core 2 Duo notebook Dell Latitude D610. Once you start combining multiple encryption algorithms, e.g. Twofish and Serpent, performance drops considerably. While this isn’t noticeable while working with Windows and popular applications, increasing system load—such as may occur during heavy multi-tasking or when taking on intensive workloads such as video transcoding—will reduce system performance considerably.
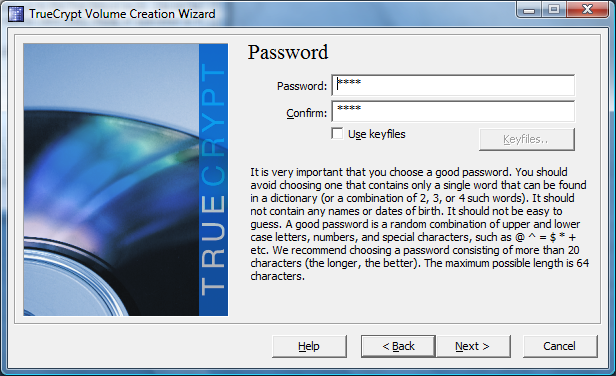
Next, you have to select a master password, which the system will use to grant access to the encrypted system.
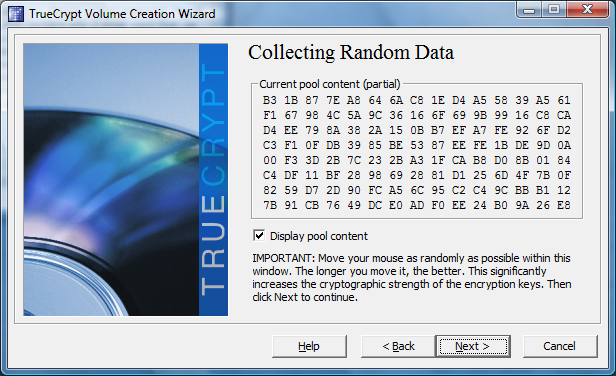
TrueCrypt prompts you to create random data for the encryption keys by moving your mouse in a random fashion. The more creative you are, the more security you will get.
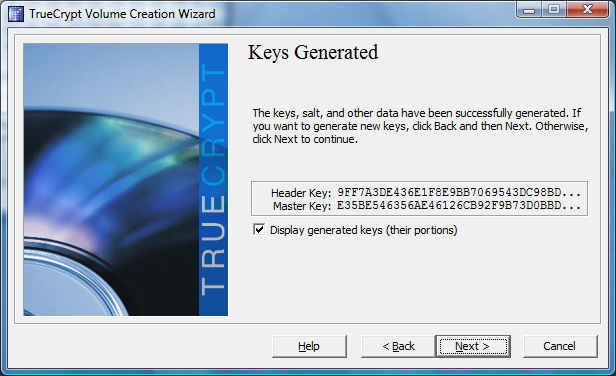
Done! The header key for the encrypted drive and the master key have been created.
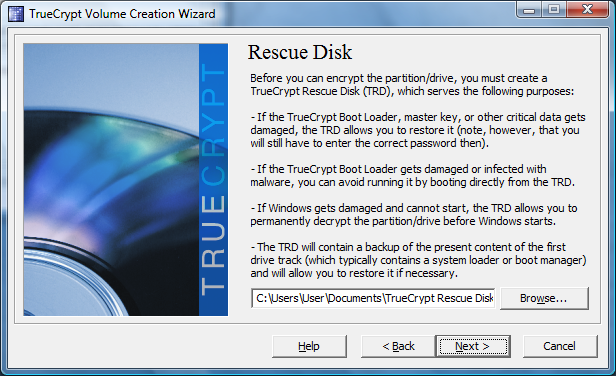
Finally, you need to create a rescue disc. This is mandatory for a TrueCrypt installation, because it is the only way to access your encrypted data should the boot loader be damaged or removed from the encrypted drive. This is not something you would do deliberately, but could occur by accident or due to hard drive failure. Make sure you store the rescue disc in a safe location.
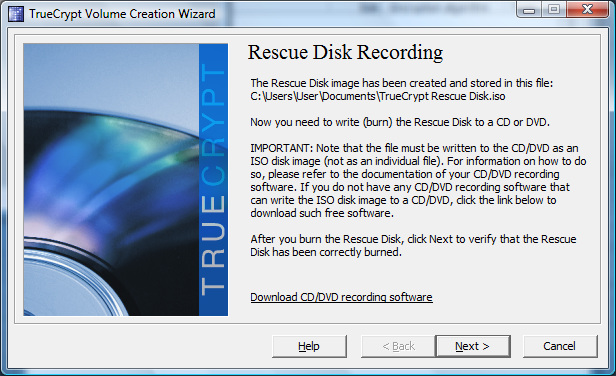
TrueCrypt creates an ISO image, so you can store it on hard drives or create a CD or DVD right away.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Encryption Algorithm, Performance, Rescue Disc
Prev Page Commencing Encryption For A Windows System Next Page Wipe Blanks, Pretest, And Encryption