Protect Your Data With Encryption
Wipe Blanks, Pretest, And Encryption
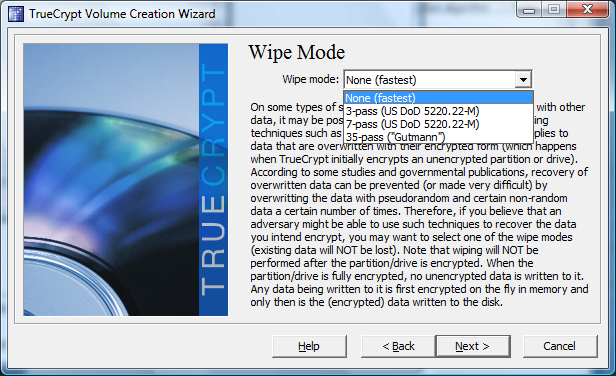
This feature probably seems like overkill, but if you don’t want any traces to remain on a hard drive and only work with the encrypted data, it is important. The procedure effectively removes existing file fragments that may still be on a hard drive from previous system installations. Select 3-pass, 7-pass, or a solid 35-pass wiping of unused areas and these will systematically be overwritten.
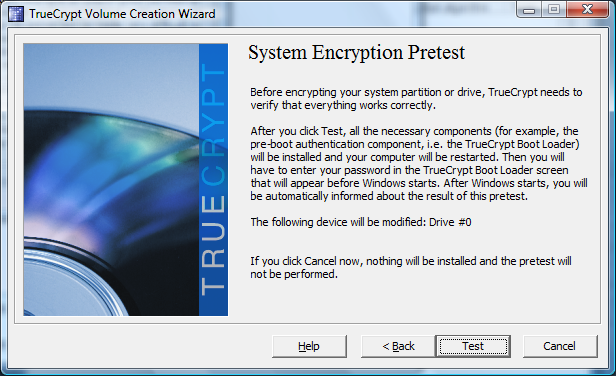
Before actually encrypting your system, TrueCrypt verifies that the system boots correctly using the boot loader, not yet using encryption nor the password.
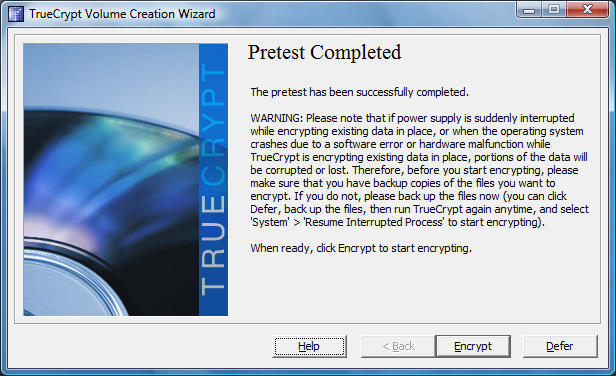
Once restarted, the actual encryption process may begin.
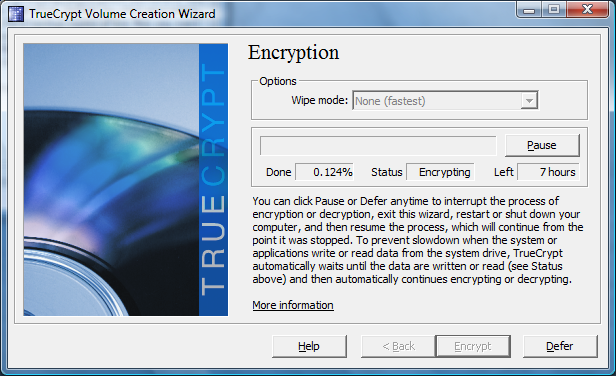
Our test system, a Dell Latitude D610, was equipped with a 45 nm Core 2 Duo Penryn T9500 processor (2.6 GHz) and a brand new Western Digital WD5000BEVT 500 GB Scorpio drive, one of the fastest mainstream drives available today. The entire encryption process using AES took eight hours, during which we could keep using the system (though we did not do much). The process takes place in the background and only consumes CPU resources during system idle times. This obviously means that working with the system intensively results in a longer encryption period.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Wipe Blanks, Pretest, And Encryption
Prev Page Encryption Algorithm, Performance, Rescue Disc Next Page First-Start, Limitations, Decrypting