Bluetooth Technology 101
From keyboards to headsets to mobile computing, Bluetooth provides the personal wireless network needed to get around without a bunch of cables entangling our lives. Here's a close look at a key technology that empowers our mobile world.
The Stack And Packet Exchange
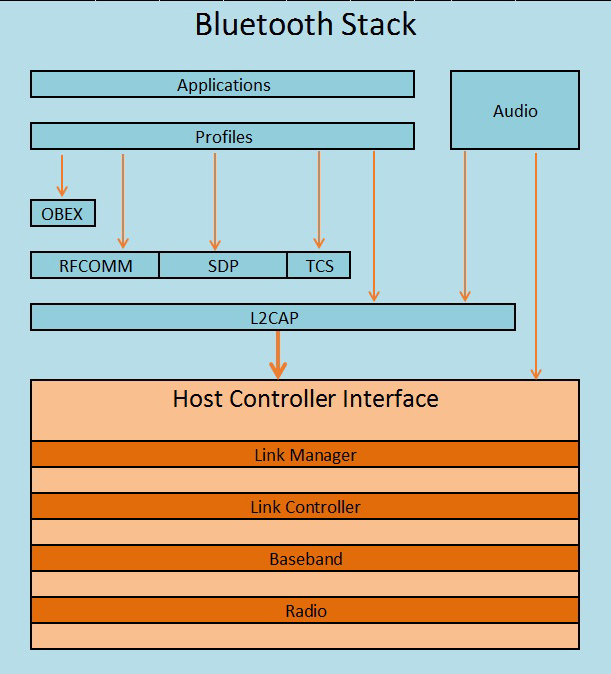
The Bluetooth Stack
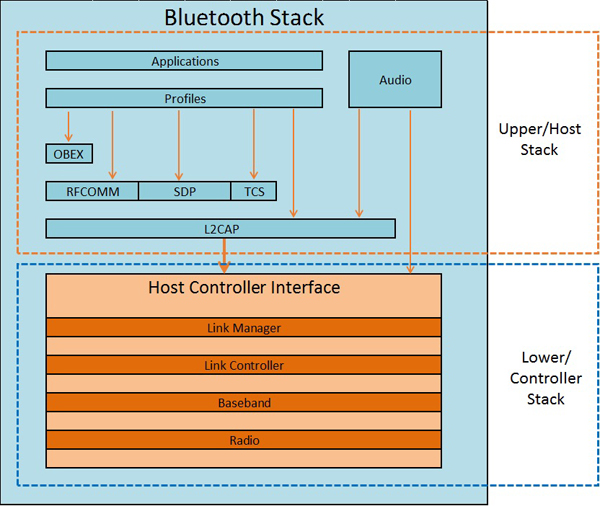
The Bluetooth stack is a set of hierarchical protocols designed to deal with the data required to make a successful Bluetooth session. These protocols can be divided into two areas. First is the lower stack, also called a “controller stack”, which contains the timing and radio control protocol (where the Bluetooth header information is used to determine channel-hopping synchronization, for example, or rejecting a channel for too much interference). Then there's the upper stack, also called the “host stack,” which deals with the higher-level data, for example the “how” of dealing with a two-way VoIP call’s audio requirements over a Bluetooth connection.
The controller stack is most commonly implemented in the hardware of the Bluetooth module/chip itself. The relevant protocols are:
- ACL, or Asynchronous Connection-Less, a protocol for sending error-sensitive data like a document. The connection is asynchronous because the receiver and transmitter take turns sending while the other receives. ACL implements forward error-correction and retransmission of a data packet in the absence of acknowledgement.
- SCO, or Synchronous Connection-Oriented, a link protocol used for voice data, where each transmitter in the link simply sends data during its time slot without waiting for acknowledgement. There is no retransmission of data, but forward error-correction can be implemented.
- LMP, or Link Manager Protocol, used to handle link establishment between radios, queries and power control.
- LE LL, or Low Energy Link Layer, an equivalent of LMP for Bluetooth Low Energy links.
- HCI, or Host Controller Interface, a standardized communication protocol used to bridge the host stack and the control stack. There are multiple standards for HCI, and multiple hardware implementations.
The host stack most commonly sits at the operating system level of a PC, smartphone or other advanced device. In certain cases, like Bluetooth headsets, there may be no host stack at all, or a simplified host stack implemented in the device firmware. Protocols inherent in the host stack are:
- L2CAP, or Logical Link Control and Adaptation Protocol, used to pass packets from the host to the HCI, or, when the HCI is omitted, directly to the LMP. L2CAP multiplexes data between different higher-layer protocols (voice data for a phone call transmitted alongside data input from a Bluetooth keyboard, for example), segments and reassembles Bluetooth data packets.
- BNEP, or Bluetooth Network Encapsulation Protocol, used to deliver network packets above L2CAP.
- RFCOMM, or Radio Frequency Communication, a protocol used to emulate RS-232 serial ports.
- SDP, or Service Discovery Protocol, used to allow devices to discover each others' service parameters and which Bluetooth profiles are supported.
- TCS, or Telephony Control Protocol Specification, used to set up and control calls (voice and data) between devices.
- AVCTP, or Audio/Video Control Transport Protocol, used to transfer Audio Video Control over the L2CAP link.
- AVDTP, or Audio/Video distribution Transport Protocol, designed for audio and video distribution (such as streaming music to stereo headsets).
- OBEX, or Object Exchange, used for simple data exchange between devices, for example a document or image.
- ATT, or low energy ATTribute Protocol, the low-energy equivalent of SDP
- SMP, or Low Energy Security Manager, a protocol used for pairing and specific key distribution.
Apart from the location of implementation, the stack can be divided according to the type of link:
- Physical Links: a baseband connection between two devices, associated with exactly one physical channel. Physical link properties include power control, link supervision and encryption.
- Logical Transports: data transport between master and slaves. These include SCO and ACL.
- Logical Links: “virtual” links that control various transports. These are defined to be Link Control, ACL Control, User Asynchronous/Isochronous (ACL-U), User Synchronous (SCO-S) and User Extended Synchronous (eSCO-S).
Bluetooth Packets And Packet Exchange
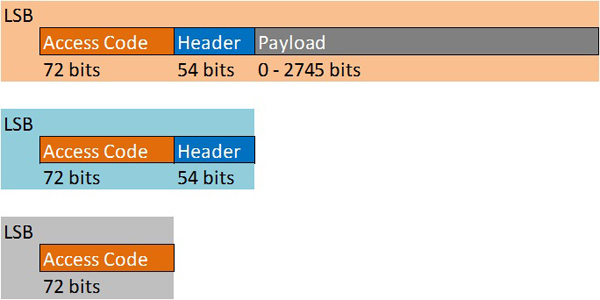
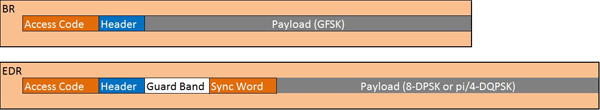
With the Enhanced Data Rate implemented as of Bluetooth v3.0, data packets are split into two types: the Basic Rate packet, which consists of the access code, header and payload, and the Enhanced Data Rate Packet, which consists of the access code, header, guard period, synchronization sequence, enhanced data rate payload and trailer. Here is what the basic data rate Bluetooth packet structure looks like:
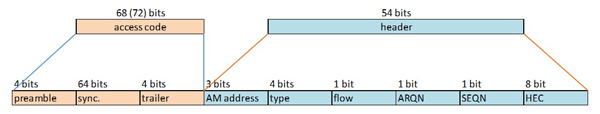
Packet handling and packet sub-components defined by the Bluetooth specification can become rather involved. For example, the Access Code begins with a preamble, a sync-word and a trailer. The preamble and first bit of the sync word provide bit-synchronization, allowing the receiver to set a "decision threshold" of incoming signal strength for the lowest possible BER. The last portion of the sync word and the trailer provide data for decoding the header, which follows the Access Code. Further, there are multiple types of access codes, depending on the operation to be performed: the Channel Access Code (CAC) is included in all packets and is used by piconet members to determine whether they should accept the rest of the packet, the Device Access Code (DAC) is used by the master to page a specific device, the General Inquiry Access Code (GIAC) is used by the master to inquire which Bluetooth devices are within range and the Dedicated Inquiry Access Code (DIAC) is used by the master to page only a specific type of device (to page only printers in the building, for instance, not headsets or smartphones).
The packet header is a 54-bit, six-field entry providing the real data a piconet needs to function, including the addresses of the active slaves the master is addressing, the type of packet being sent (ACL or SCO, for example), the flow of packets to control buffering, an acknowledgement of successful receipt, a sequential number bit to prevent acceptance of duplicate or retransmitted packets and a unique sequence generated from a given polynomial function in order to protect the device from accepting an incorrect packet.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Packets consisting of only an access code and header are called NULL and POLL. They're used to convey flow, acknowledgement or ping a slave for a response.
The payload itself is the biggest chunk of data transmitted, and its structure varies depending on what kind of data is being transmitted.
Current page: The Stack And Packet Exchange
Prev Page Bluetooth Wireless Communication Next Page Bluetooth Security-
Fernando_engen Bluetooth is pretty much the future. I have just started developing Bluetooth Low Energy Services/profiles for specific use cases along with the application layer. Its an awesome new world.Reply -
YunFuriku Actually hearing aids with button cell batteries these days can use Bluetooth Smart or to be exactReply
bastardized proprietary version of it by Apple and GN Resound which enables them to have wireless audio streaming from
various devices with Bluetooth. Comes with expense of range naturally because hearing aids need to use low power version of it (1,5V doesn't give much choice on this )
Max 10m in ideal conditions.
Sadly, the audio stack they use is Apple Exclusive so direct connection is Apple devices only.
Non-apple devices require intermediary devices such as TV streamer or Phone Clip to other Bluetooth Capable phones. These devices are relatively cheap compared
to old FM tech hearing aids used to use where transmitter prices were measured in 0,5-2k range, about ~$200-300 at most.
Unfortunate side is that if you want to use it with non-Apple phones you'll have to have intermediary device which serves as bluetooth handsfree mic/answer/volume
buttons too beause of the audio stack which Apple won't license to others.
At the same time Apple is pushing their made for iPhone hearing aid tech to FCC to be recognised as standard.
Here's to hoping hardcore android fan like me won't have to buy iPhone as my next phone if this doesn't come to other phones directly because of silly audio stack :P
-
RIluske Is the graphic about memberships correct? I thought the article said the third tier was free to join, but the graphic has it costing the same amount as second tier.Reply -
zodiacfml I feel WiGig has a better future eventually. Bluetooth will be left to activation or turning on devices or IoT as already mentioned in the article.Reply -
DotNetMaster777 Very useful article !! bluesniping can be done over one km away wow !?!?Reply
Are there any performance tests between wifi and bluetooth ?? -
exnemesis Just give me bluetooth tech that can allow me to walk away 40-50m from my phone and penetrate better through walls and objects and still retain the quality of whatever it is I'm listening to on my phone.Reply -
TripleHeinz This is the best article I've ever read in Tom's. Didn't have a clue that bluetooth was related with Thor the god of thundervolt ;)Reply -
yasminpriya15 Welcome to Bluetooth 101. Here are the top things you need to know about Bluetooth technology.Reply
My Bluetooth doesn’t work. What do I do?
The Bluetooth SIG does not make, manufacture or build any Bluetooth products. We simply support our membership and help them to help make the best products on the market. The best way to solve your problem is to contact the manufacturer directly or start by researching solutions on the Internet.
What is Bluetooth?
Bluetooth is a global wireless communication standard that connects devices together over a certain distance. Think headset and phone, speaker and PC, basketball to smartphone and more. It is built into billions of products on the market today and connects the Internet of Things (IoT). If you haven’t heard of the IoT, go here.
How does Bluetooth work?
A Bluetooth device uses radio waves instead of wires or cables to connect to a phone or computer. A Bluetooth product, like a headset or watch, contains a tiny computer chip with a Bluetooth radio and software that makes it easy to connect. When two Bluetooth devices want to talk to each other, they need to pair. Communication between Bluetooth devices happens over short-range, ad hoc networks known as piconets. A piconet is a network of devices connected using Bluetooth technology. The network ranges from two to eight connected devices. When a network is established, one device takes the role of the master while all the other devices act as slaves. Piconets are established dynamically and automatically as Bluetooth devices enter and leave radio proximity. If you want a more technical explanation, you can read the core specification or visit the Wikipedia page for a deeper technical dive.
Are there different kinds of Bluetooth?
There are actually several “kinds”—different versions of the core specification—of Bluetooth. The most common today are Bluetooth BR/EDR (basic rate/enhanced data rate) and Bluetooth with low energy functionality. You will generally find BR/EDR in things like speakers and headsets while you will see Bluetooth Smart in the newest products on the market like fitness bands, beacons—small transmitters that send data over Bluletooth—and smart home devices.
What can Bluetooth do?
Bluetooth can wirelessly connect devices together. It can connect your headset to your phone, car or computer. It can connect your phone or computer to your speakers. Best of all? It can connect your lights, door locks, TV, shoes, basketballs, water bottles, toys—almost anything you can think of—to an app on your phone. Bluetooth takes it even further with connecting beacons to shoppers or travelers in airports or even attendees at sporting events. The future of Bluetooth is limited only to a developer’s imagination.
What makes Bluetooth better than other technologies?
The short answer is because Bluetooth is everywhere, it operates on low power, it is easy to use and it doesn’t cost a lot to use. Let’s explore these a bit more.
Bluetooth is everywhere—you will find Bluetooth built into nearly every phone, laptop, desktop and tablet. This makes it so convenient to connect a keyboard, mouse, speakers or fitness band to your phone or computer.
Bluetooth is low power—with the advent of Bluetooth Smart (BLE or Bluetooth low energy), developers were able to create smaller sensors that run off tiny coin-cell batteries for months, and in some cases, years. This is setting the stage for Bluetooth as a key component in the Internet of Things.
Bluetooth is easy to use—for consumers, it really can’t get any easier. You go to settings, turn on your Bluetooth, hit the pairing button and wait for it start communicating. That’s it. From a development standpoint, creating a Bluetooth product starts with the core specification and then you layer profiles and services onto it. There are several tools that the SIG has to help developers.
Bluetooth is low cost—you can add Bluetooth for a minimal cost. You will need to buy a module/system on chip (SoC)/etc. and pay an administrative fee to use the brand and license the technology. The administrative fee varies on the size of the company and there are programs to help startups. http://www.traininginsholinganallur.in/qtp-training-in-chennai.html
http://www.traininginsholinganallur.in/primavera-training-in-chennai.html
http://www.traininginsholinganallur.in/big-data-analytics-training-in-chennai.html