Protect Your Data! TrueCrypt 7.0a's Performance, Analyzed
Version 7.0a of TrueCrypt offers many new features, including hardware-accelerated AES encryption via processors that support the technology. We discuss the new features and look at the performance impact of running an encrypted system partition.
Benchmark Results: Iometer
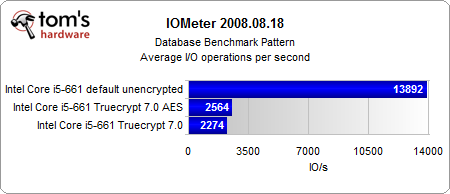
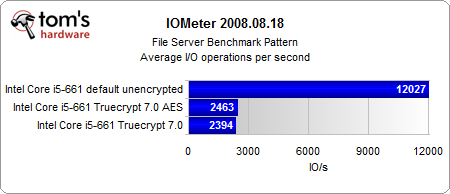
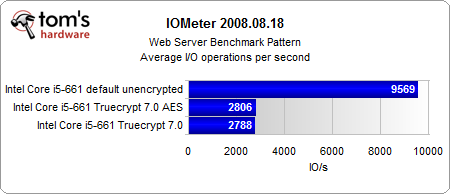
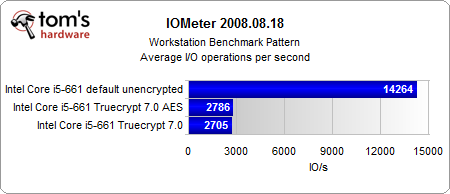
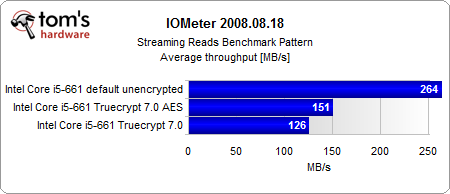
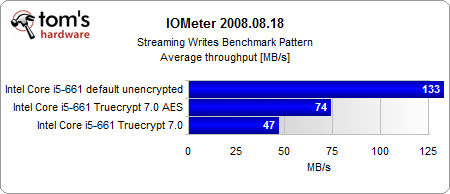
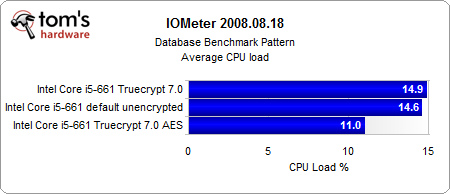
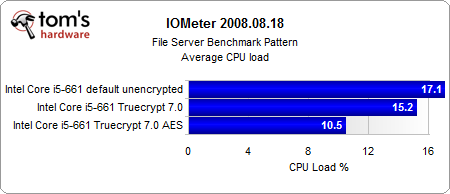
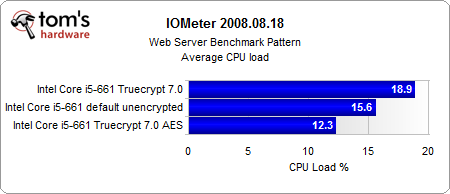
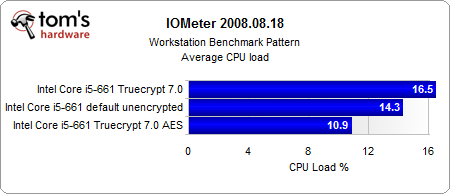
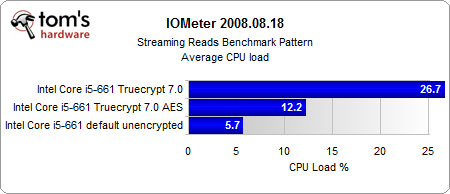
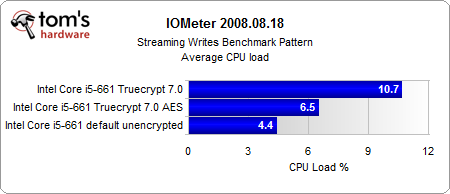
The most interesting results come from our Iometer benchmarks.
Looking purely at the encryption, the AES-NI instruction set provides a consistent performance gain. And even if the performance gain is rather small, the CPU load is several times lower than in the conventionally-encrypted system. However, the encrypted systems are significantly slower than the unencrypted system, with or without hardware acceleration.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Benchmark Results: Iometer
Prev Page Benchmark Results: SYSmark Next Page Conclusion: AES-NI Preserves Performance Reserves-
eddieroolz I like the jab at Sony in the opening page!Reply
Anyhow. I've used TrueCrypt 7.0a for about a year now to secure my sensitive information. I've only encrypted a non-system partition as of now, but for the purpose of storing sensitive files the performance hit is unnoticeable. Took a bit of time to set up, but in the end, all worth it. -
kikireeki TrueCrypt is the best, but anyone who uses it should keep in mind that the data encrypted by it is not meant to be recoverable.Reply -
I encrypted my HP dm1z "netbook" system partition with Truecrypt. Even without AES-NI support by AMD E-350 the computer is still very responsive for non-gaming tasks. Thanks to Truecrypt for their great encryption utility and also to AMD for making a decent low-end APU.Reply
-
alidan a strong password and change it often...Reply
yea thats so not happening.
i could make my password look like that,
€‡“ŸeVmAE•kvÕbœ
but it would be REALY HARD to remember, and changeing it on a, lets say, monthly basis.... who are you kidding.
i have a 5 letter password
i have an 8 letter password
and i have a 6 letter password for when places force me to use a number, but at the same time, wont let me have 2 letters that are the same in a password.
i find it agonizingly annoying that i cant use a 5 letter password for everything, because i despise having more than 1. its my account, i will make it as secure as i want. i pay 10$ a month for id theft protection, is an account is lost because of "hacker" i tell someone about it and the account is dead to me.
i have only had 1 hacker in my life go for any one of my 100's of accounts (i mean 100's literally) and that is my gaia account that i made when gaia was new, and someone tried to brute force the account, 5 times back in 2008 (i have the emails in a special folder labeled F@$#ING BRUTEFORCER, without the censoring) and not a f@#$ was given by gaia (i didn't care, i stopped using it years before, i just informed them that some a$$hole was hacking my account to hopefully ban them, but they told me to p!SS off in almost those exact words). honestly security is overrated, yea id theft is bad, if you are parinoid, get protection and stop worrying, get a password that is 10 letters and number long, as no one is bruteforceing that, refuardless of where the account it, as long as they don't have your info or actually hacked the service. -
memadmax alidan,Reply
hackers use bruteforce as last resort as it takes so long.
Now they do the sneaky worm into your keyboard with a keylogger most times. Or if they are really targeting you, or want you bad, they will dig in your garbage....
Net Security 101...
-
sudeshc You want best encryption deal with the drawbacks as you find them or else write your own encryption logic.Reply -
alidan memadmaxalidan,hackers use bruteforce as last resort as it takes so long.Now they do the sneaky worm into your keyboard with a keylogger most times. Or if they are really targeting you, or want you bad, they will dig in your garbage....Net Security 101...Reply
not realy, what they do first and formost, is check any online foot mark you have. usualy your password is something you know, such as mothers maden name or a birthday. i use to use my birthday completely spelt out, but that is to long for MANY passwords, and, as you can see, my spelling is atrocious, so i spell it wrong 9 times out of 10.
but its my point exactly, they will get the info weather you want them to or not, and odds are, they will dumpser dive a hospital, dentist office, or doctors to get the info before they will ever go online.
-
Wamphryi I think that some may be missing the point about the benefits of encryption. For data on more portable media Truecrypt is most excellent. Also to be considered is that the data thief you should worry most about is not the Super Hacker on line but the opportunist thief who happens to steal your laptop. Your mail and photos etc in the hands of some petty thief?Reply