How Microsoft Should Improve Windows 10 Security (Op Ed)
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Windows 10 already looks like it's going to have quite a few interesting security features, from the Windows Hello biometric authentication to the complementary online-focused Passport authentication protocol to Device Guard, a secure execution environment that's separated from the Windows 10 OS. However, there are other significant security improvements Microsoft could do to Windows 10 to make it a much safer OS.
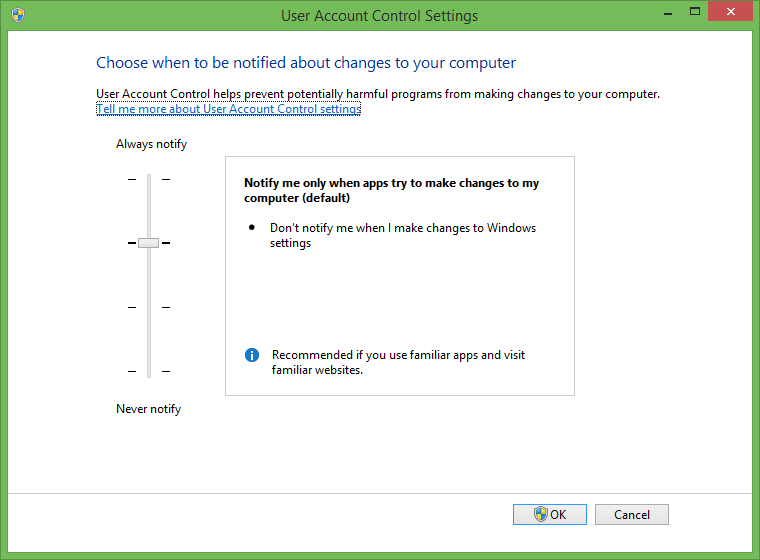
User Account Control (UAC)
When Microsoft introduced User Account Control (UAC) in Windows Vista, it was probably by far the most universally hated feature. At the same time, it was also the feature that made Vista and future iterations of Windows radically more secure than Windows XP.
In Windows XP, almost any app could do almost anything. That's because, to this day, the default account in Windows has Administrator rights. With UAC, users can remain Administrators, but app privileges are limited to the Standard mode.
The UAC is certainly not bulletproof. The system is protected against apps silently causing damage to it in the background. However, if the users themselves install a malware-infected application and click through the UAC prompts, then of course they will still become infected.
There's also the fact that there have been a handful of UAC bypasses every year. Even with these weaknesses, UAC still managed to drastically reduce the amount of malware that could exist on Windows.
UAC, or a replacement for it, could still further improve Windows security. Right now, the most effective way to infect someone's computer is to get them to install an app for you. Human error and gullibility is still the easiest attack vector.
The UAC needs to be upgraded in such a way that an app can't do anything it wants even after it's installed with Administrator rights. Most apps should be properly sandboxed from each other, and the apps that actually need some potentially dangerous privileges should display a different type of warning.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
In fact, Microsoft should make the "basic" UAC prompts/alerts much less threatening so as to not train users to click through the more seemingly dangerous ones. The warnings that require more powerful privileges should be one or two steps above the basic ones, and they should appear much less often.
Ideally, the app sandboxing would be so good that "basic alerts" wouldn't even be needed, therefore making UAC even less annoying than it is today. That would also make the stronger warnings that much more eye-catching and should force users to pay more attention to the privileges requested by the app. Suffice it to say that Microsoft should be making the warnings as easy to understand as possible by regular computer users.
Both iOS and Android use strong sandboxing systems, and despite all the headlines about Android malware, the truth is the malware that exists doesn't usually affect a large percentage of people. Even better, that "malware" usually can't do much damage to the operating system itself or other apps. The times when it's most dangerous is when the user has root access, which means that malware also has root access and can therefore bypass the sandboxing system.
Microsoft is working on an alternative to UAC that uses cryptographically signed apps. That, combined with the Windows Store's review process, should (almost) guarantee that the apps users are installing are safe.
The problem with this solution is that it's currently quite limited, because it only applies to apps from the Windows Store. Unless Microsoft demands that all apps are signed (and verified) by default in Windows 10, this solution won't significantly improve anything. This is why Microsoft needs to come up with a complementary solution that still provides strong enough protection for non-Windows Store apps.
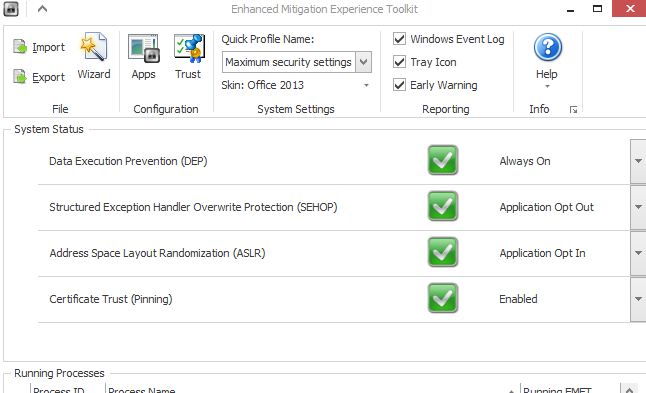
Enhanced Mitigation Experience Toolkit (EMET)
The Enhanced Mitigation Experience Toolkit (EMET) is one of the most powerful security applications Microsoft has built in recent years. Unfortunately, adoption has been low because not enough people are aware that it exists, even though it's a free tool that Microsoft has had available for many years.
EMET protects against a wide class of zero-day vulnerabilities that can appear because of poorly written code (which can easily happen, especially with unsafe C++ code). EMET is actually a suite of mitigation technologies such as Address Space Layout Randomization (ASLR), Data Execution Protection (DEP), Structured Exception Handler Overwrite Protection (SEHOP), Certificate Pinning, Null Page Protection, and more.
By default, the tool is set to "Recommended Settings" which mainly protects Microsoft's apps, but you can set it to "Maximum Protection," which enforces all the protections on all apps by default. It's good to be aware that this can prevent some apps from loading, but it's usually very rare and happens with very old apps.
Antiviruses and other malware tools usually function by maintaining a known database of malware. Effectively, what that means is that before an antivirus maker can discover the bug and update its software accordingly, some PCs will need to be infected first.
By contrast, EMET can protect against exploits and hacks without having to "know" in advance what those exploits are. To hack into a computer using a zero-day vulnerability, an attacker would also have to bypass EMET, which is usually quite hard to do.
For instance, last year at the browser hacking competition Pwn2Own, researchers managed to hack into Internet Explorer 11, but they couldn't do it when EMET was enabled. In fact, the IE11+EMET was the only browser configuration that proved unhackable. Until more recently, EMET was also a good way to significantly increase security for those who were still on Windows XP (which is no longer supported).
The good thing about EMET is that it doesn't require too much technical expertise after the quick initial setup. It's more of a "set it and forget it" type of software, not unlike an antivirus in that respect. That also means that it should be relatively easy to integrate into Windows 10.
Some developers may not like it, especially if they don't want certain mitigation technologies to be implemented because they would mess with the way their apps are currently written, but this is one of those things where Microsoft just needs to show leadership for a good cause.
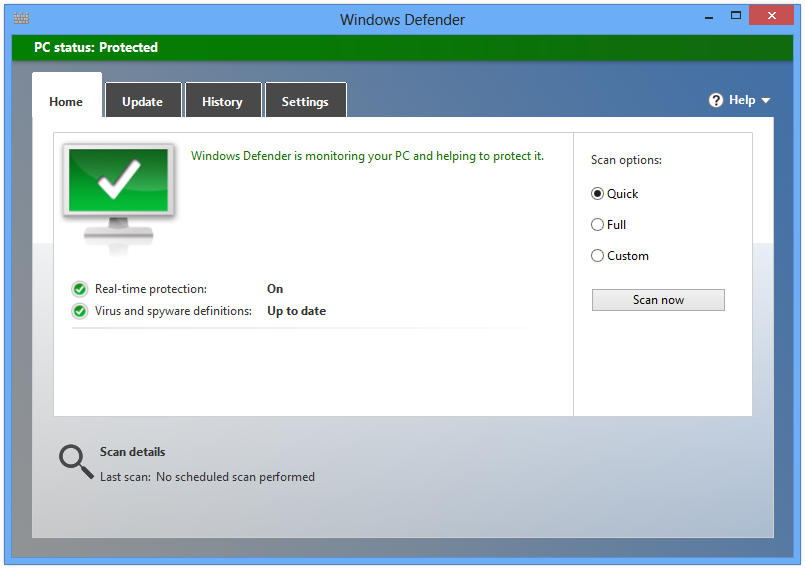
Microsoft Security Essentials (Windows Defender)
There was a time when "Microsoft Security Essentials" was arguably the best and easiest-to-use free antivirus out there. That is until Windows 8 came along, and Microsoft decided to integrate MSE into the new OS. Since then, it seems that the built-in antivirus (now named Windows Defender) has gotten worse with each passing year, falling further and further down the ranks in antivirus competitions.
Why this is happening is not exactly known, but it could be either because Microsoft has made the antivirus division a lower priority or because most attackers have already learned how to bypass it. It could even be a combination of both.
Although there was a time when I would recommend just using MSE/Windows Defender, I don't feel nearly as comfortable doing so today. In fact, what I suggest these days is to disable Windows Defender and install some other free antivirus such as Avira (to avoid conflicts and/or resource waste).
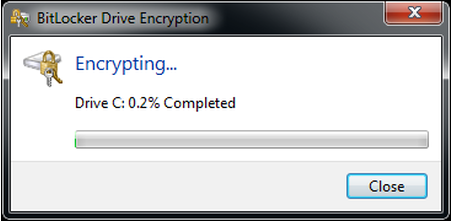
BitLocker And Encrypting File System (EFS)
Windows Vista brought another good security feature in the BitLocker software, which provides full drive encryption. Microsoft has also offered the EFS (Encrypting File System) feature to encrypt files and folders since Windows 2000. There is one major issue with these tools, though: they are both available only for Pro and Enterprise users, which means most regular users can't benefit from them.
Encrypting your own local data is the most basic form of security, and Microsoft should be offering it to every single Windows 10 user, whether we're talking smartphones or PCs. Further, wherever possible, the encryption should be done automatically.
All smartphones based on ARMv8 chips should have support for fast encryption instructions, and Intel and AMD chips have supported hardware encryption for quite some time. It wouldn't be a radical move for Microsoft to require that all the new devices that come with Windows 10 should be encrypted by default. Apple and Google are already moving to default local storage encryption, and Microsoft should follow suit.
Windows 10: A Golden Opportunity
Windows 10 is going to be a once-in-a-decade opportunity for Microsoft to start fresh with its operating system. One of the reasons why the company is going to allow users to install Windows 10 for free in the first year is to get as many people as possible to leave their older, less secure operating systems and to jump on a more secure platform.
Windows 10 is already a rather significant upgrade in terms of security features. However, adding the above features could make the OS a must-have, even if it isn't easy to migrate away from Windows 7 or Windows 8 for some users (especially for companies and institutions).
A solid sandboxing/privilege system, EMET suite of zero-day protections, a much-improved antivirus, and default encryption could make Windows 10 not just the most secure Windows version ever, but one of the most secure operating systems on the market.
Follow us @tomshardware, on Facebook and on Google+.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
mwryder55 The one thing that would help UAC the most is for it to remember your responses. Once a program is allowed to run remember that unless there is a change to the program. The user should not have to click through the prompt every time they run a program. This just leads to them turning it off when it becomes too obnoxious.Reply -
CaedenV @mwryder55Reply
But then software could pretend to be the OK'd software and get through making it almost as useless as turning UAC off entirely.
@article
I think a lot of that is already in play. Obviously there are some rather large pressures to not turn off legacy applications (just one of many reasons why windows RT, which only ran winRT apps, was such a massive failure). If they did limit things to just the store then it would really help a lot of security as MS would get a good look at all code as it was compiled, and it would all be managed code to begin with.
I think this is one of the reasons why MS is moving more and more of it's own apps into the app store; mainly just to prove that you can write big full-featured apps in fully managed code, and still have it work well and efficiently. Granted, I am not quite sure that Spartian or the new metro version of Office are exactly proof of the concept, but it is at least a start; and once there eventuially are some good apps in the app store then maybe more people would go there first for their software purchases instead of some web 1.0 website to download an exe.
Another thing that is being implemented is the use of internal keys and cryptography within the OS itself; basically a way to have the left hand of the OS prove to the right hand what it is before it is allowed to do anything. This could prove to be a huge step forward for OS level security. You may be able to infect a PC, but at that point it would always be one refresh away from being clean again.
Speaking of refreshing the PC, another nice thing about win10 is that when you do a refresh or reinstall of the OS it finally asks you for a local user name and password before it will do it! This was a scary (though often convenient) 'feature' of win8 in that you could take anyone's computer, do a fresh OS install, and it was essentially your machine at that point. At least with win10 you are going to have to take a few extra steps to format the drive and do a full installation if you want to rip off someone's computer rather than putting in an express lane to do so.
Never even heard about EMET before, I'll have to look into that. Something that powerful should certainly be part of the OS even if it is not enabled by default.
Overall though I think win10 is going to prove to be a big step forward on the security front. The OS still has some bugs to squash before release, but I already like it a lot more than win7/8/8.1. -
Quixit Forcing existing Windows Apps to run sandboxed would break the vast majority, if not all of them so it's not particularly feasible. In fact WinRT was an attempt to do just that, introduce a sandboxed app model and WinRT apps haven't exactly become the next big thing have they?Reply
I'm not entirely convinced the majority of users actually cares about security. UAC is probably the least time-intensive security system in any OS I've ever used (compare to sudo on 'nix or Mac's similar solution) and yet still a fair number of people disable on every system they use. A lot of them still don't even set a log-in password either or if they do they pick something without any complexity, that could be cracked in a few seconds. Look at all the people jail-breaking their phones, people care more about freedom than they do about security. -
Shin-san I prefer UAC over Apple's solution. Apple made fun of Microsoft for it, but I hate having to type in a password EVERY TIME I update some software on Mac OS X. To have a safe password, you need a mix of letters/numbers/symbols/etc and that password sometimes has to be tied to an online account. Yuck. Instead of the depressed "allowed"/"confirmed"/"okay" in that Apple commercial, I get "ENTER YOUR GODDAMNED PASSWORD!"Reply
Someone said that UAC goes "Terror Alert" and hates only that part. He liked that you could deny an application access to the Internet. I overall agree with this. I also like the idea of application sandboxing, with giving the user the ability to elevate the access so that it can go outside the install directory
-
mapesdhs Most of Windows' security problems over the past decades would haveReply
been avoided if the OS had been built from the start with a proper
foundation of file ownership and access permission concepts (oh wait,
that's UNIX...) Instead, Windows has a bucket load of bolted on nonsense
which has never worked properly, full of glitches and crazy behaviours.
I'm not buying the notion they can turn Windows around into something
inherantly secure, their track record shows no intent to do this. Always
amazes me the planet's corporations have never tried a vast lawsuit to
force MS to sort it all out.
Ian.
PS. The downvotes are amusing. :D Facts are facts, Windows never had
any inherant concept of file ownership, and that made it an utter security
nightmare from the very beginning. Ever since NT it's just been a bolt-on
mess which doesn't really work. Tried meddling with file ownership, etc?
It's utter garbage in Windows, always has been.
-
daglesj MS should start to include and switch on more of the security by default. I think they hold back due to many older bits of software not being compatible (especially with EMET) but maybe it's time for those old insecure or badly coded bits of software to be put out to pasture. I think MS is worried it would then be classed as a security Nazi which means damned if they do and damned if they don't. I will be disappointed however, if EMET isn't built into Windows 10. The time is right for that.Reply
As for MS Security Essentials/Defender, thats a tough one. As it's installed as standard in Windows 8 it's basically the one AV to beat as a first step so it's going to get hit hard. I still think it has value. I find it finds stuff that MBAM etc. doesn't find such as Cryptolocker stuff. What I think is more damaging is OEMs bundling in a 3 month trial of McAfee or Norton with 8. I find so many year old Windows 8 laptops still running those outdated trials whilst Defender is switched off. I'd rather have up to date Defender than out of date McAfee. -
Morbus ReplyThe one thing that would help UAC the most is for it to remember your responses. Once a program is allowed to run remember that unless there is a change to the program. The user should not have to click through the prompt every time they run a program. This just leads to them turning it off when it becomes too obnoxious.
EXACTLY this, and ONLY this.
I liked the read and this is a useful article, but Microsoft only needs to do THIS, and they'll improve my experience immeasurably, I turn off UAC on all my computers, even though I've given it a try.
In the end, I was willing to live through the clicks, but as soon as I figured that UAC wouldn't let me autorun SOFTWARE (fruck that apps bs) that required administrator access, I disabled it without a second though.
What a load of BS that UAC is.
-
zodiacfml I don't agree but Microsoft has done well considering many factors (except the weakening Windows Defender probably to allow AV makers to thrive)Reply
It's the browser though which needs a lot of help.
But, thanks for mentioning EMET. I have never heard of it and might try it now on my machine. -
Achoo22 Good article. I'd also like to see Microsoft rework the svchost and dllhost mechanisms to allow greater transparency. Most firewalls and other system tools only pickup the base executable, so having so many processes (especially privileged processes) under the svchost/dllhost aegis is terrible for security.Reply
The ideal sandbox would be on that virtualizes all devices. An application "thinks" it has installed files/services all over the disk where it has really been constrained to one easy to delete directory with more sensible permission control than the half-hearted program files method. Internet Access/IPC/etc should be easily toggle-able for any running app.
Also, and this is a big one, allowing the built-in firewall to be programmatically bypassed is ridiculous. With so many people behind NAT routers, the greatest benefit of a personal/software firewall is in limiting data leakage from within. If every application can override user settings by changing its own firewall rules (in Windows, it doesn't even require a user prompt), the firewall is useless.
It's long past time that it became safe to run unsafe applications. -
Grandmastersexsay Who even gets viruses anymore? Malware? Adware? It's all easily delt with. I remember the good old xp days where you had to reformat every year because of all the crap that got through.Reply
People don't care about security as much as they used too, mainly because they don't have to.
Microsoft should put all their effort into making windows 10 an enjoyable experience. Give people a real start menu. Stop with the windows store. Stop this stupid app nonsense. They're called programs. Let the engineers and programmers oversee the design. Trash the boardroom focus group nonsense.