Locking up Linux: Creating a Cryptobook
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Test Setup
Our test rig is a Dell Latitude C610, an aging but agile performer representative of technology from around 2002. On battery power, the C610 will throttle the CPU to 733 MHz, so it was left plugged in to exercise the full capability of all the components at their optimal speeds. The table below describes the most important aspects of this setup.
| Test Setup Table | |
|---|---|
| Processor | Intel Pentium III M (1200 MHz) |
| Memory | 256 MB PC133 SDRAM |
| I/O Controller | Intel 82801CA/CAM |
| Disk Drive | Hitachi 20 GB 2.5" UltraATA/100 |
| Linux Distribution | Fedora Core 5 |
Results are charted using the EXT3 file system format under Linux, which may not be the best performer in all test cases when compared against other journaling file systems. However, experimenting with the fine-tuning of file system formats, block sizes, drive parameters, and so forth is beyond the scope of this exercise - it takes away from the ease of setup and configuration. The goal here is to provide a cursory examination of the areas of simplicity, performance, and cost-effectiveness, using Linux cryptographic storage solutions.
Installation Process
All of LUKS, FUSE and EncFS are available directly from Fedora distribution sources, so no extra effort is necessary. CryptoFS must be obtained separately.
CryptoFS Setup Process
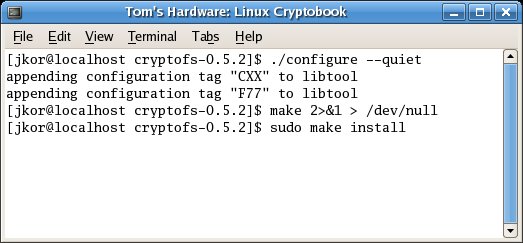
Compilation of CryptoFS from sources is simple. Unfurl the archive and issue the configuration script in the resulting directory, then proceed with the make process, as demonstrated in the accompanying screenshot. The configuration file contains only four parameters: encryption cipher, message digest algorithm, block size, and encryption salt count.
The CryptoFS installation process is simple.
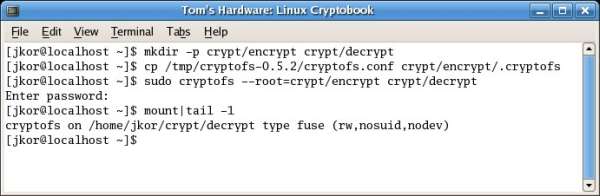
Setup consists of designating source and target directory paths (for encrypted and decrypted content) and issuing the cryptofs command accordingly, as shown in the next image.
Setting-up the CryptoFS implementation.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Issue the mount command to see the newly loaded partition.
Current page: Test Setup
Prev Page Encryption Products For Linux, Continued Next Page EncFS Setup Process