Intel vPro In 2012, Small Business Advantage, And Anti-Theft Tech.
One year ago, we took a look at three generations of Intel's vPro, charting how its features evolved. Now, we have a new version to explore. Additionally, we're putting Anti-Theft technology to the test, along with the new Small Business Advantage suite.
Intel Anti-Theft Technology, In Practice
Symantec's solution comes with a free eight-day demo. In practice, the other solutions all work similarly (Ed.: I've used Absolute Software's, and it is indeed very much like what's illustrated here).
First things first. You have to sign up for Norton's Anti-Theft service. This easily integrated with my existing account, which I admittedly had forgotten about. After signing up, you download the Norton Anti-Theft package and install the software. Then, you see the following confirmation message:
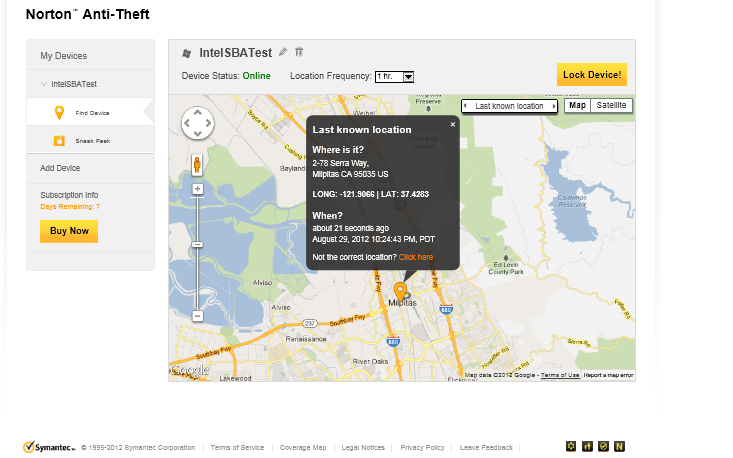
From your Anti-Theft account page, you can see the laptop's current location on a map.
As an aside, the device that shows up in Milpitas, California is actually located down the freeway in Mountain View, California, about four city blocks from Symantec's global headquarters. The desktop we're testing doesn't have a GPS receiver or cellular card in it, so the service is likely tracing our machine to a broadband service provider's facility.
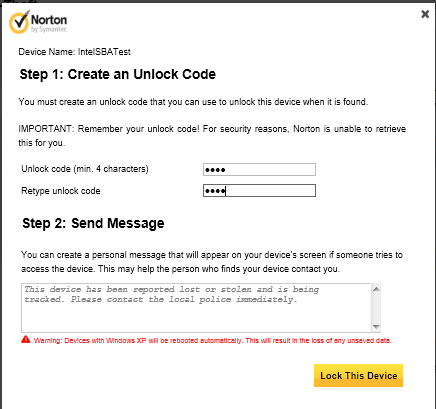
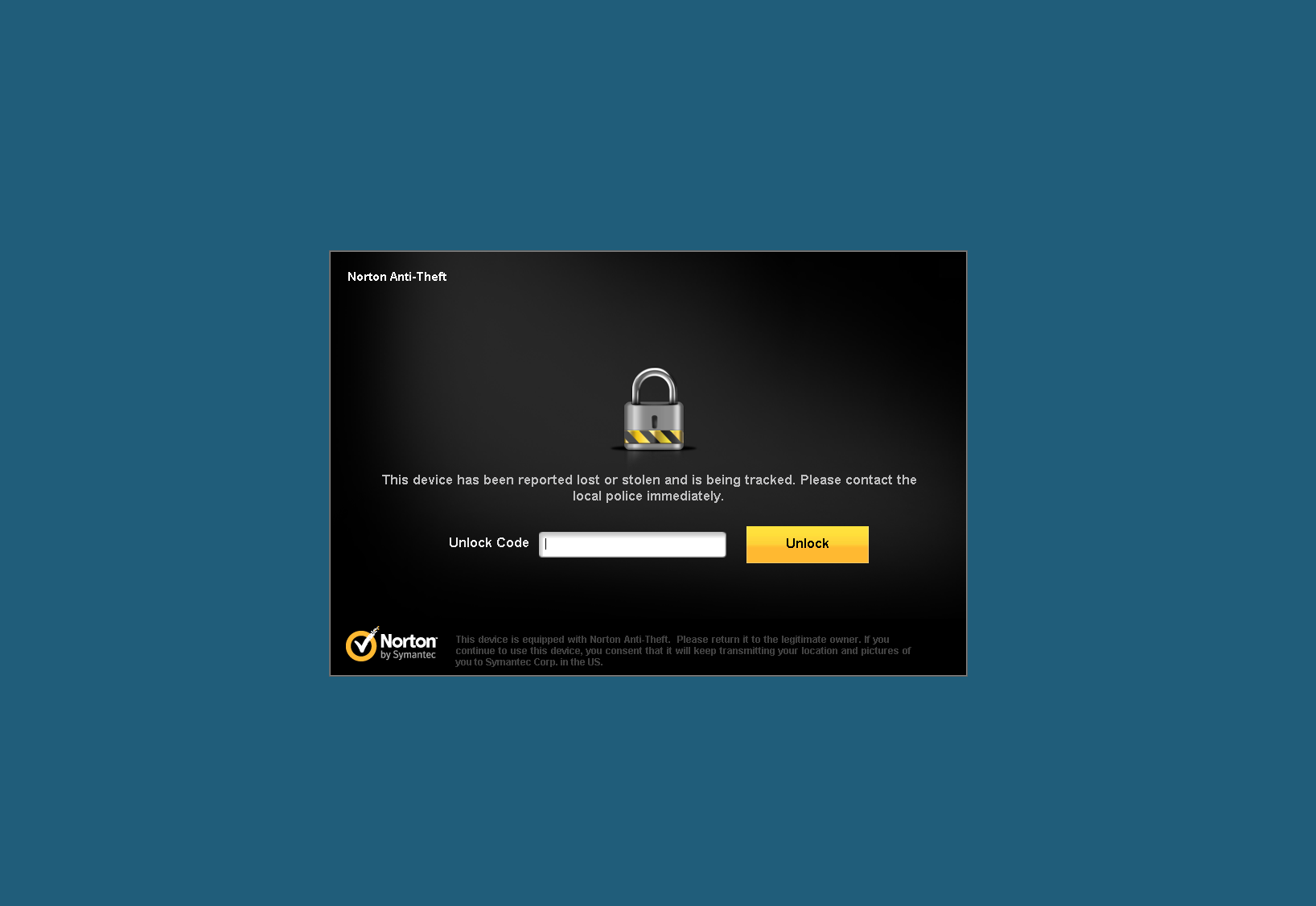
With the system protected, and assuming you lose it (or just want to test the service's functionality), you can log in to your Norton account and lock the device remotely.
At this point, you get to create a lock code and type in a personal message, if you want. The default notification assumes your machine is in the hands of a do-gooder; it requests that they turn the machine into police. You can also customize the message a bit, depending on your humor or angst.
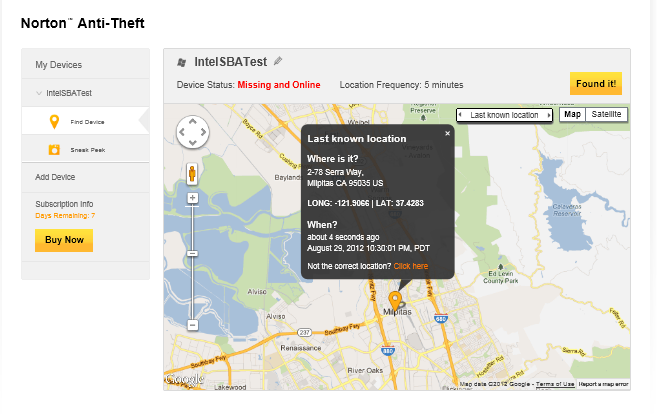
You can then use the same map view to track your machine. In the example below, it shows up as Missing and Online.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Within about 45 seconds, my "lost" machine (which I was logged into), suddenly logged out of Windows and displayed the following message:
I verified that this worked locally, and by checking through Windows 7's remote desktop functionality. The lock screen conveys the default message you specified, plus a space to enter a PIN created on the website. Fortunately, I remembered the PIN and removed the Symantec lock myself.
The high-point of Anti-Theft is its ability to lock down potentially vulnerable assets using a Web-based service. Consequently, it's an effective deterrent for any would-be criminal who knows what Anti-Theft does. Hopefully, he or she will move on to the next unprotected notebook without the security feature. Of course, the same smart crook might also know that staying off a network prevents the Anti-Theft service from reaching it. In that case, you're able to set up a trigger whereby the passage of time without a check-in automatically locks the machine.
Current page: Intel Anti-Theft Technology, In Practice
Prev Page An Introduction To Intel Anti-Theft Technology Next Page Business-Class Features Evolving In 2012-
bit_user Toms, you really need to blow the lid off the incredibly dangerous security flaws in vPro that can enable undetectable and irremovable rootkits. semiaccurate.com did some reporting on this. Please alert the mainstream. The exploit was already demonstrated some time ago.Reply
Thanks.
-
bit_user I don't know if it's allowed, but here's the link:Reply
http://semiaccurate.com/2012/05/15/intel-small-business-advantage-is-a-security-nightmare/
Maybe the editors will read it before they remove this post. It's not a terribly well-written article. That's where you can help, Tom's.
-
freggo Why not integrate a GPS receiver into the motherboard and than have an option to define 'allowed' active areas for the system. For desktops that should be no problem as they do not get moved much.Reply
For laptops you may have to take a bit more time defining your typical usage area of course; you could even let the laptop track your typical usage location patterns so it can make recommendations for the best setup.
If the systems is outside the area either request a special password or some other form of identification to unlock the machine either for one time or for inclusions of the current location into the allowed area.
Damn, I should get that patented :-)
-
bigdragon I have a hard time reading this lengthy article after all the trouble I've had with Intel's DBS1200KP and DBS1200KPR. Intel keeps promoting virtualization, but they failed to implement VT-d on that product even though there's no reason for it not to be supported.Reply -
StitchExperiment626 Backup is my complaint! Doing a full backup every night there isn't enough time.Reply -
jkflipflop98 Keep in mind, all the garbage you read on that site is by Charlie Demerjian. . . who honestly doesn't know much about anything.Reply -
labtech drew Having owned an MSP (Managed Service Provider), with hundreds of customers, and thousands of machines under management, vPro add's enormous cost savings when implemented.Reply
Customer has a blue screen? No problem, you can KVM right in and see the issue.
Workstation hung after remotely applying patches - calling the user and saying "Can you go over and hold the power button for me?" is no longer necessary. Simply shutdown the machine via vPro and power it back on. Even remotely re-imagine a machine from backup is possible.
However, my favorite use case is the instant back to work use case. End user hard drive fails - obviously a truck roll is needed, but the most important thing is to get the user productive again. Leverage vPro's ability to redirect IDE (IDEr) to a network Live Linux CD at least gets the user in to Web Outlook, if not 100% back in business.
How about power savings? Schedule machines to auto shutdown at night, and for your patch window, use vPro to power up the workstations, apply the patches, power down (from windows) and if a machine hangs on shutdown use the vPro power off command. Allows for nightly maintenance and keeps costs savings maximized.
Rolling out vPro can be a bit of work using native tools, but there are solutions available (shameless plug) like LabTech Software (http://www.labtechsoftware.com) which can remotely provision and manage vPro along with any other IT management function you can think of.
-Drew
Full disclosure: Having ran an MSP and worked with many enterprises, out of band management tools were critical in every mature organization I worked with. As a co-founder of LabTech Software, I have engaged Intel and we are working closely to build out solutions that vPro truly solves for.