Top Laptop Makers Still Don’t Seem To Care About Security
Last year, there were quite a few security scandals that affected both Lenovo and Dell. Duo Security, a security company that offers two-factor authentication and endpoint security products, uncovered that it’s not just those two laptop companies that are putting their customers in danger of getting hacked, but others as well, including Acer, Asus, and HP.
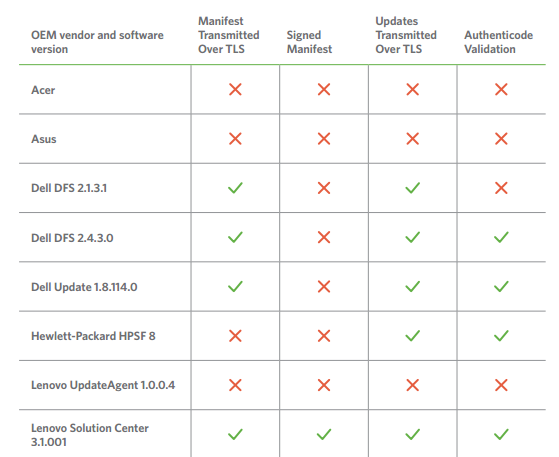
Duo Security investigated laptops from all five companies and found that all of the updaters either don’t use HTTPS encryption at all, or if they do, it’s not set up properly and can still be susceptible to man-in-the-middle attacks.
Bloatware - More Than Just A Waste Of Resources
The company believes that these laptop makers are installing “bloatware” on PCs that not only waste resources, but also put users at risk, despite all the security features that Microsoft may have implemented in its latest Windows operating system. Often, these software tools completely bypass Windows’ defenses, which means that attackers that take advantage of them can bypass those protections as well.
“It doesn’t take much for one piece of software to negate the effectiveness of many, if not all defenses. One non-ASLR DLL, a predictably mapped RWX memory segment, a trivially exploitable command injection bug — these all make an attacker’s life easier — and OEM software is full of them,” said Duo Security’s researcher in a recent paper.“Rob Joyce, Chief of NSA’s TAO group made abundantly clear what most of us already know: why do what’s difficult and risky when you simply don’t have to? Hacking in practice means taking the path of least resistance, and OEM software is often a weak link in the chain. All of the sexy exploit mitigations, desktop firewalls, and safe browsing enhancements can’t protect you when an OEM vendor cripples them with pre-installed software,” added the researchers.
OEMs, Making Windows Hacking Easy
The researchers discovered that all of the five major OEMs shipped custom software with their laptops, and that software contained at least one vulnerability that resulted in arbitrary remote code execution capabilities, allowing for complete control of the machines by potential attackers.
Duo Security also mentioned that using the vulnerabilities wouldn’t require sophisticated technical knowledge, which means they could be exploited easily. The exploitation would also be made easier by the large attack surfaces offered by these updaters.
The security company thought that the biggest problem was the lack of HTTPS encryption for updates, as well as a lack of code-signing and certificate pinning. These features would significantly increase the security of these OEM and third-party updaters and make them much more resilient to exploitation.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Not verifying the update manifest for authenticity can also pose a great danger for users, because malware can stop various updates that would otherwise patch certain vulnerabilities.
Another issue the researchers discovered was with silent updates without user notification. Automatic updates tend to generally benefit users, but for security reasons, users should at least be notified when they happen. Otherwise, there’s the risk that an attacker can take advantage of that silent update to install malware without the user knowing about it.
Duo Security also called out OEMs such as Dell and Asus, which seem to add pointless obfuscation and encryption features to its updaters that demonstrate a security through obscurity mentality. The security researchers found the obfuscation trivial to reverse engineer.
Signature Edition Not So Clean After All
Microsoft has been offering “Signature Edition” devices for some time, and at least in theory, they should be free of bloatware from PC OEMs. However, OEM-supplied updaters still seem to be present on these machines in most cases, therefore making Signature Edition devices just as vulnerable as other devices sold directly from the OEMs.
The OEMs seem to be using a combination of their own updaters as well as third-party updaters, with various degrees of security implementations. Duo Security researchers mentioned, for instance, that Lenovo had one updater that was protected against MITM attacks, while another one had no protections whatsoever.
Mitigations For Users And OEMs
The main mitigation strategy Duo Security recommended is to wipe any OEM installation as soon as you get a new laptop. Otherwise, the company recommended that users uninstall all OEM components in the Windows operating system.
To laptop OEMs, the company recommended using TLS encryption, manifest signing to prevent the modification of the manifest contents, as well as code signing through Microsoft’s Authenticode service.
Lenovo and Dell security scandals from last year don't seem to have phased either company, or the other major laptop OEMs, too much. They continue to update their software over unencrypted connections or don't sign their packages at a time when it's never been easier or cheaper to do either of those things. Because this seems to be an industry-wide practice already, and competition alone hasn't had the desired effect, it will be up to users to put pressure on the OEMs to fix these problems.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
innocent bystander If these guys can't get their act together it bodes really well for the security shitstorm that is IoT.Reply -
mavikt I forsee Microsoft empowering the OEM's further by not allowing this bloatware to be uninstalled in Win10 to further the sales of "Signature Edition".Reply
How about charging the customer the real, full price for the product instead of packing this toxic waste along with it!?
Does any major company engage in honest business today without EULA's upon EULA's upon EULA's selling your soul? Gaah! -
drtweak This is why when ever i deploy Dells to my clients, I have images of CLEAN installs with NO DELL software. Just good old windows and all its updates. Honestly all their OEM stuff is crap. Half the time their updates break software/drivers.Reply -
falchard Where is MSI, Clevo, and Sager? I am sure they fail to protect as much as the ASUS, but it feels like a diss not including them.Reply -
Vatharian That's just funny, considering Lenovo drops bugged executable binaries trough EFI right into your vanilla Windows installation - what's the point of having 'update center' then?Reply -
wifiburger easy fix, buy a notebook with perfect unix / linux compatibility and wipe that garbage oem install,Reply -
ethanolson Uh... HP has a consumer line and a commercial line. The commercial line checks all the boxes. Lenovo and the author are not getting the whole story. HP's consumer line is pretty much garbage, though.Reply -
Kimonajane This is why you buy Mac or take these MS infected machines and fix them by wiping the drive and installing Linux.Reply