AMD Zenbleed Vulnerability Fix Tested: Some Apps Drop 15%, Gaming Unaffected
We put a patch for the Zenbleed vulnerability to the test.

A Google security researcher recently unveiled the startling new Zenbleed vulnerability that lays bare the most sensitive information passing through AMD's Zen 2 processors, like encryption keys and user logins, thus allowing an attacker to steal data and compromise a system entirely. We learned about a workaround that can patch the issue, and even though the fix doesn't persist through reboots, it allowed us to run a series of tests to determine the performance impact of enabling a patch, which AMD will be releasing in the near future.
Our testing revealed that some workloads, like encoders and renderers, can suffer performance losses of up to ~15%, while other types of desktop PC applications are either unimpacted or can even experience a slight uptick in performance after the patches. Those focused solely on gaming can breathe a sigh of relief, though, as our tests didn't reveal any significant performance penalties in several titles.
The Zenbleed flaw (CVE-2023-20593) spans the entire Zen 2 product stack, including AMD's EPYC data center processors and the relevant Ryzen 3000/4000/5000 CPUs, but AMD has only released official firmware-based patches for its data center chips. The impacted Ryzen chips for desktop PCs won't receive firmware patches until the November-to-December timeframe, depending on the model (schedule here), leaving users potentially exposed to attackers in the meantime.
As with the most dangerous vulnerabilities, Zenbleed exploits an inherent flaw in the chip architecture, so unless the attack is delivered via known malware, a direct attack would be undetectable to malware scanners or other traditional detection methods. At the time of disclosure, AMD said it wasn't aware of the vulnerability being exploited in the wild, but the statement isn't too comforting — the very nature of the vulnerability means an attack would be undetectable; the chip works as it is designed, but it has a flaw.
Tavis Ormandy, the researcher with Google Information Security who discovered the bug, also released a POC (proof of concept code that demonstrates an exploit) that is freely downloadable, meaning that it is conceivable that nefarious actors have crafted attacks using this approach. AMD says the problem is fixable, but the firmware patches will result in as-yet-undefined performance reductions that vary by workload.
Once a Zenbleed attack is underway, the attacker can exfiltrate data at a rate of 30Kb per core per second, thus stealing data passing through the registers inside the chip. The attack works on all software running in the system, including virtual machines, sandboxes, containers, and processes, posing a significant threat to cloud service providers and their customers. That perhaps explains why AMD prioritized the microcode patches for its data center EPYC processors, while Ryzen PC users have to wait until later in the year.
I can reproduce this on my laptop as well. #zenbleed https://t.co/J9LGmIIWhF pic.twitter.com/i5UH9NCzdZJuly 25, 2023
If you expand the above tweet, you can see the Zenbleed exploit in action. Zenbleed leverages the CPU's speculative execution engine to steal sensitive data, but it isn't as direct of an attack on the engine as we see with vulnerabilities like Meltdown and Spectre. Instead, the Zenbleed 'use-after-free' attack takes advantage of AMD's incorrect recovery behavior after the register is 'freed' due to a branch misdirection for a vector instruction (vzeroupper), thus allowing data to be observed (deep dive explanation here).
AMD describes the flaw succinctly, saying, "Under specific microarchitectural circumstances, a register in “Zen 2” CPUs may not be written to 0 correctly. This may cause data from another process and/or thread to be stored in the YMM register, which may allow an attacker to potentially access sensitive information."
The Zenbleed vulnerability joins a long list of chip flaws that have been discovered over the last several years, including other recent additions, like the AMD Inception vulnerability that works against the Zen 3 and 4 architectures and can result in significant performance losses in some data center workloads (we're waiting on patches for PCs to test), and also Intel's GDS / Downfall vulnerability, which impacts chips spanning Skylake to Rocket Lake generations, that can result in up to a 39% performance loss in some workloads.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
We're planning on testing the impact of the Downfall and Inception vulnerabilities soon — these patches will certainly impact our CPU benchmarks hierarchy — but here's our Zenbleed testing in the meantime.
How to Enable a Zenbleed Patch
We enabled the Zenbleed patch using a software-triggered approach — not a hardware-based method that will be used in AMD's coming firmware patches. As such, it is possible that this patching method isn't quite as efficient as a microcode update. It's possible, but not assured, that the few performance reductions that we observed in our testing could be reduced with a microcode patch. However, AMD's patch will likely trigger the same chicken bit we're flipping for our testing.
AMD has confirmed that this is a viable means of patching the system, but it is a fleeting fix — this patch will not persist through a reboot, so your system will return to an unprotected state. Obviously, that isn't tenable for a normal user, but it allowed us to conduct testing to assess the impact of the patch. Naturally, a firmware fix will work after reboots.
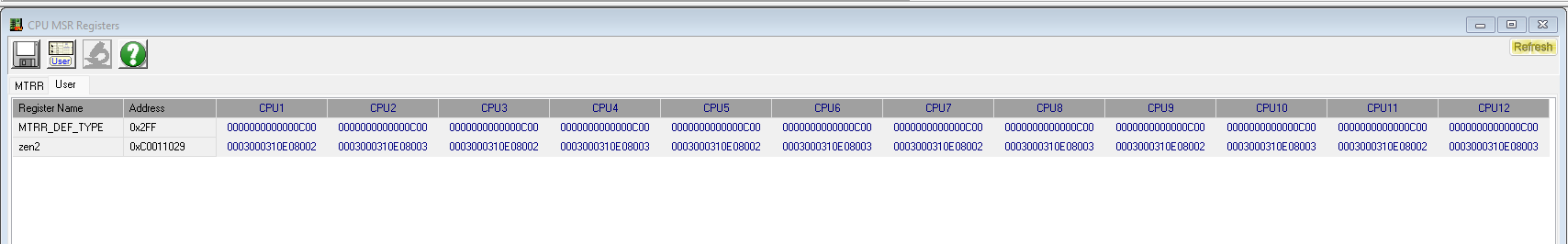
We patched the bug by setting an MSR parameter using RWEverything, a free tool that's commonly used by engineers of multiple disciplines to control the system at the lowest levels. Ironically enough, you have to disable Memory Integrity (HVCI), a controversial security feature that can result in lost performance, and the Microsoft Vulnerable Driver Blocklist to use this patch. That means that while this workaround fixes one vulnerability, it also opens the door to other potential attacks, so use it with care.
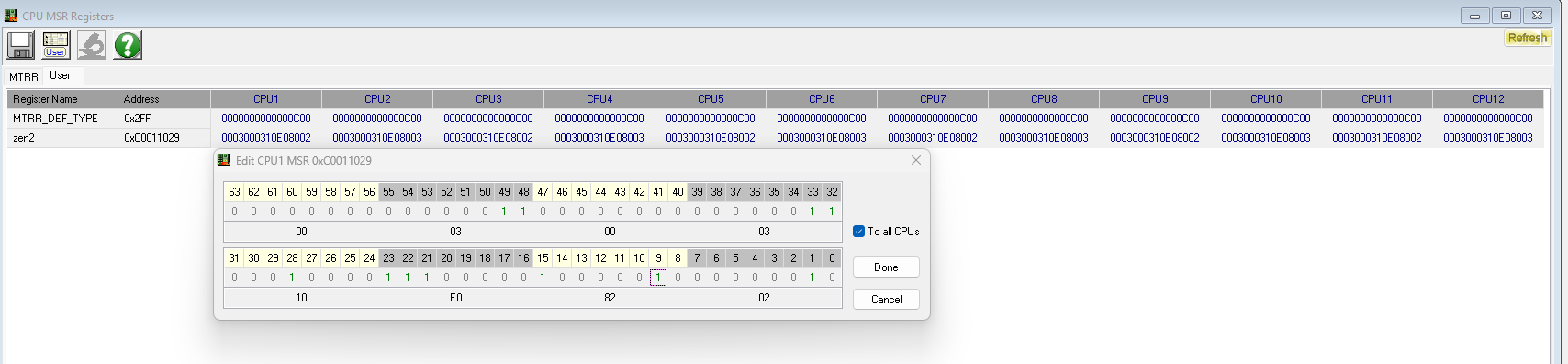
The next step is to select the MSR icon in the program and then click the 'User List' icon to create a register with 'name'=0xC0011029. You can name the register whatever you would like (we chose 'Zen 2'). You then change bit 9 to "1" and click done, and the system will be protected from an attacker attempting to exploit the Zenbleed vulnerability.
The Zenbleed attack steals data at 30Kb/sec per core, so it actually runs faster on chips with higher core counts. As such, we tested two Zen 2-powered processors with different core counts. The 16-core 32-thread Ryzen 9 3950X represents a high core count model, while the Ryzen 5 3600 stands in as a decidedly more mainstream six-core 12-thread chip. We tested both chips on an MSI MEG X570 Godlike motherboard with a fully updated version of Windows 11, a Corsair H150i cooler, and 32GB of DDR4-3200 memory.
AMD Zenbleed Gaming Performance Impact
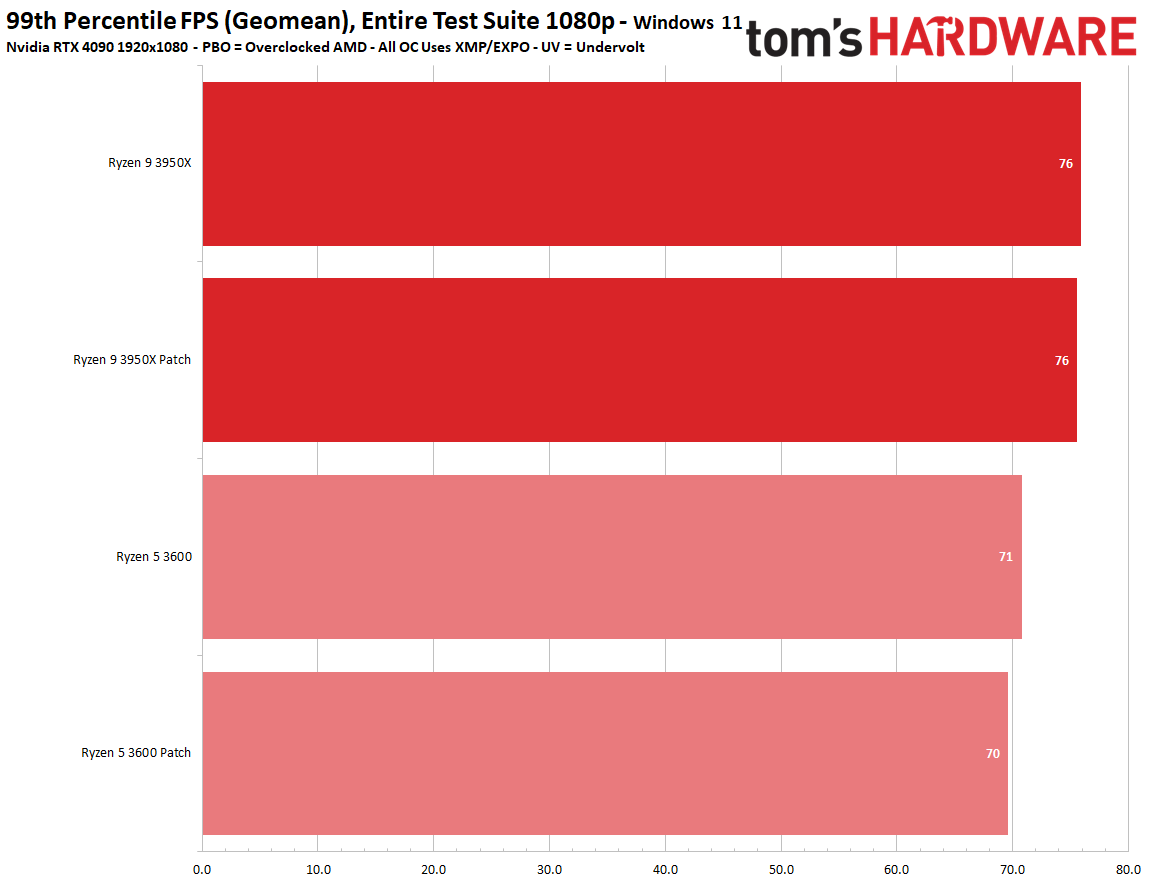
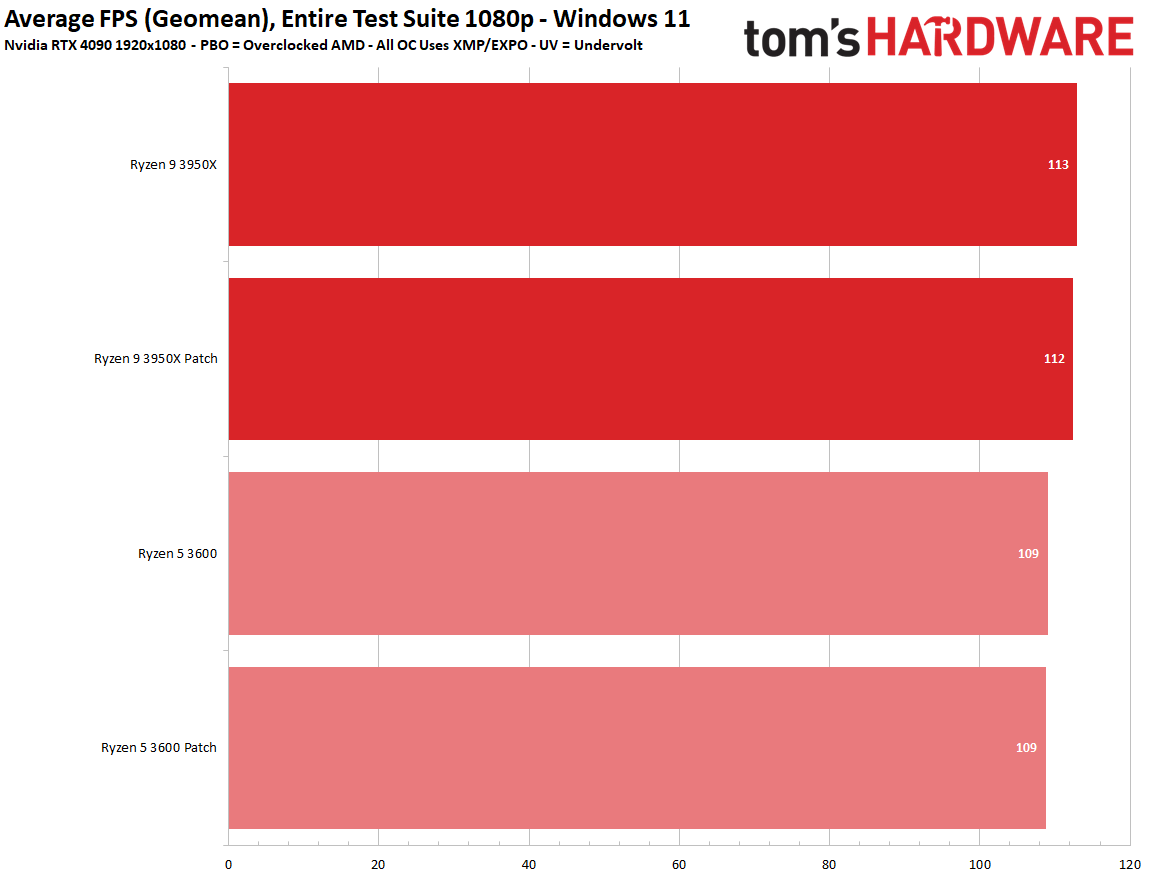
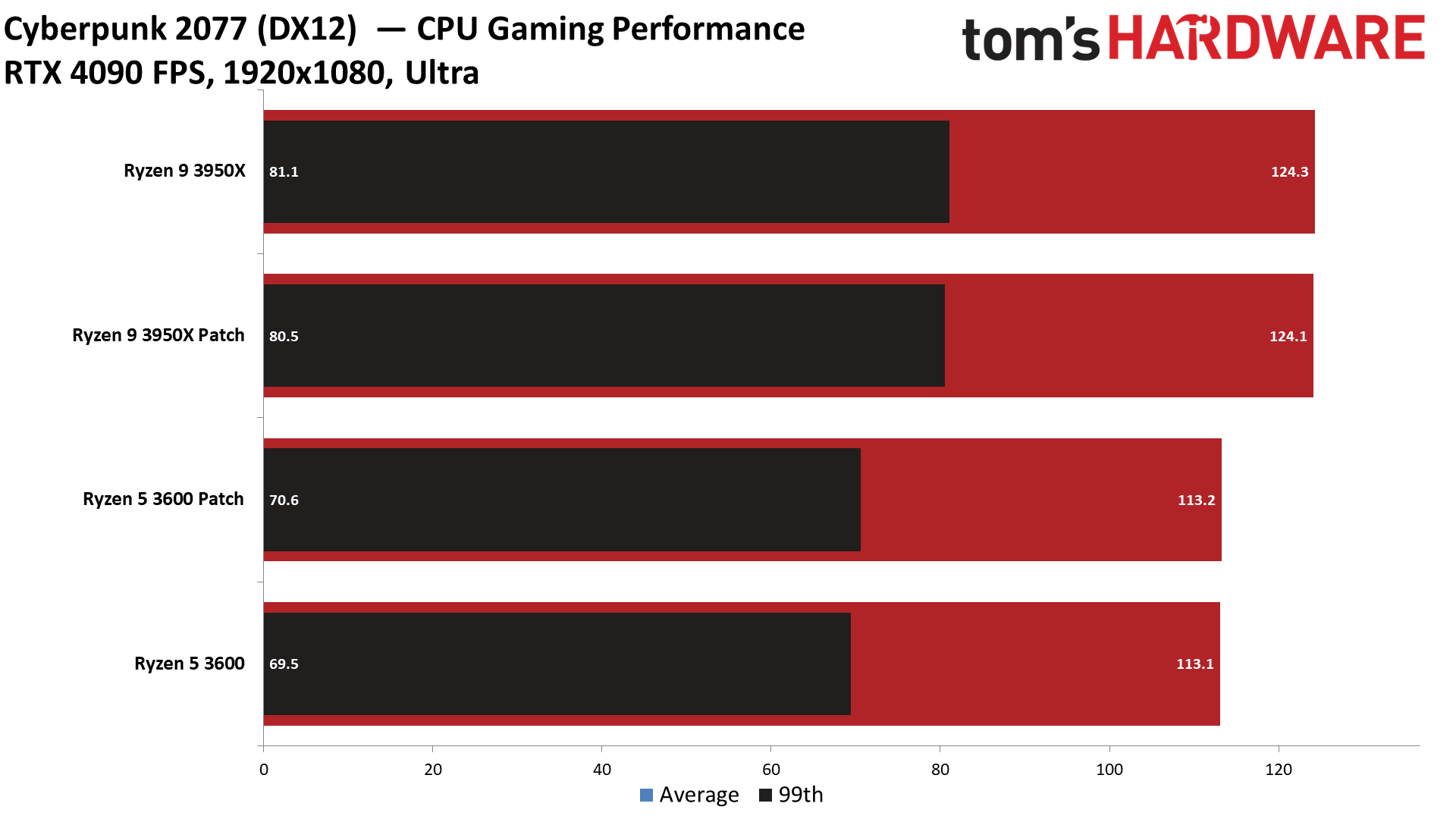
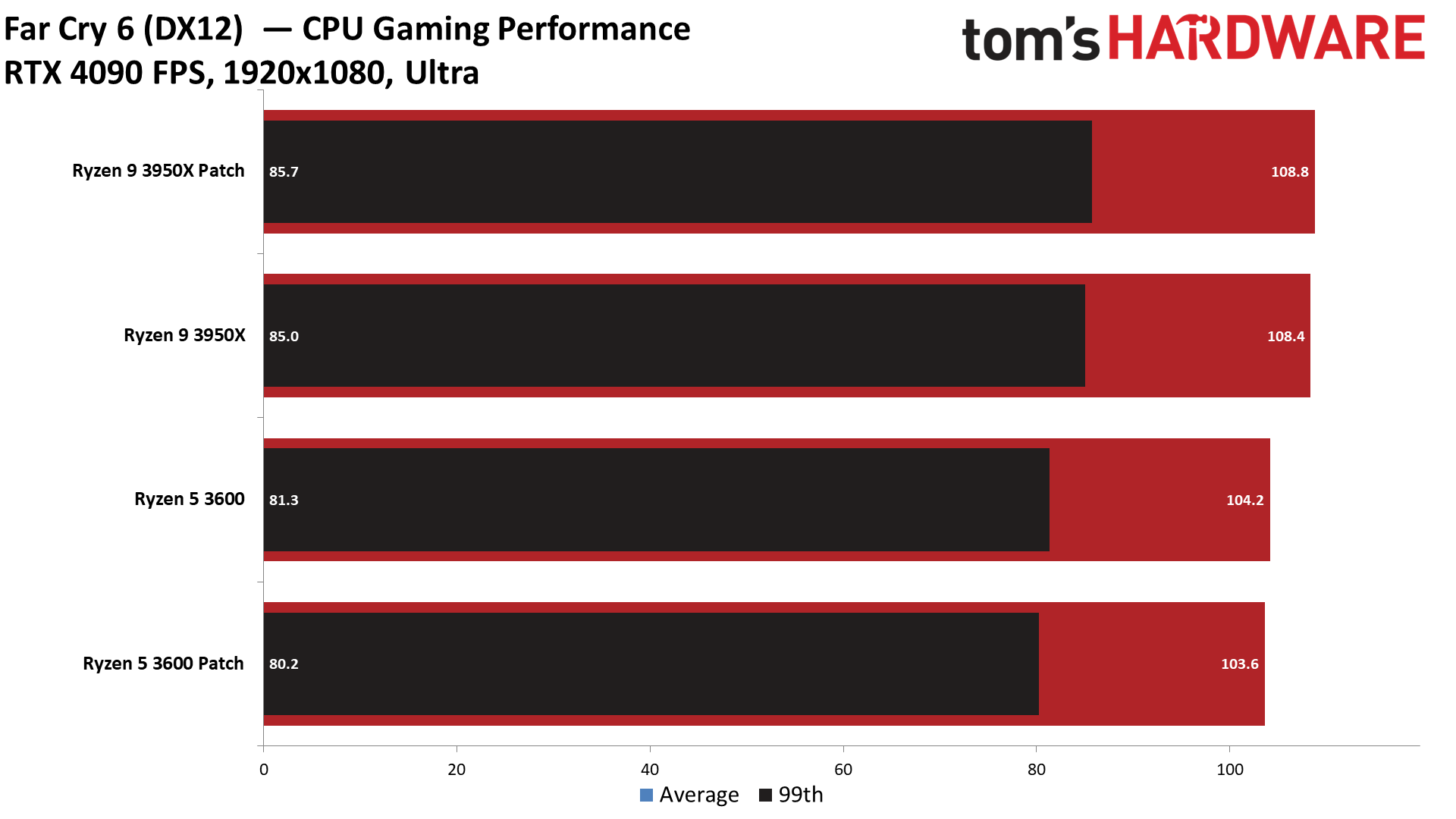
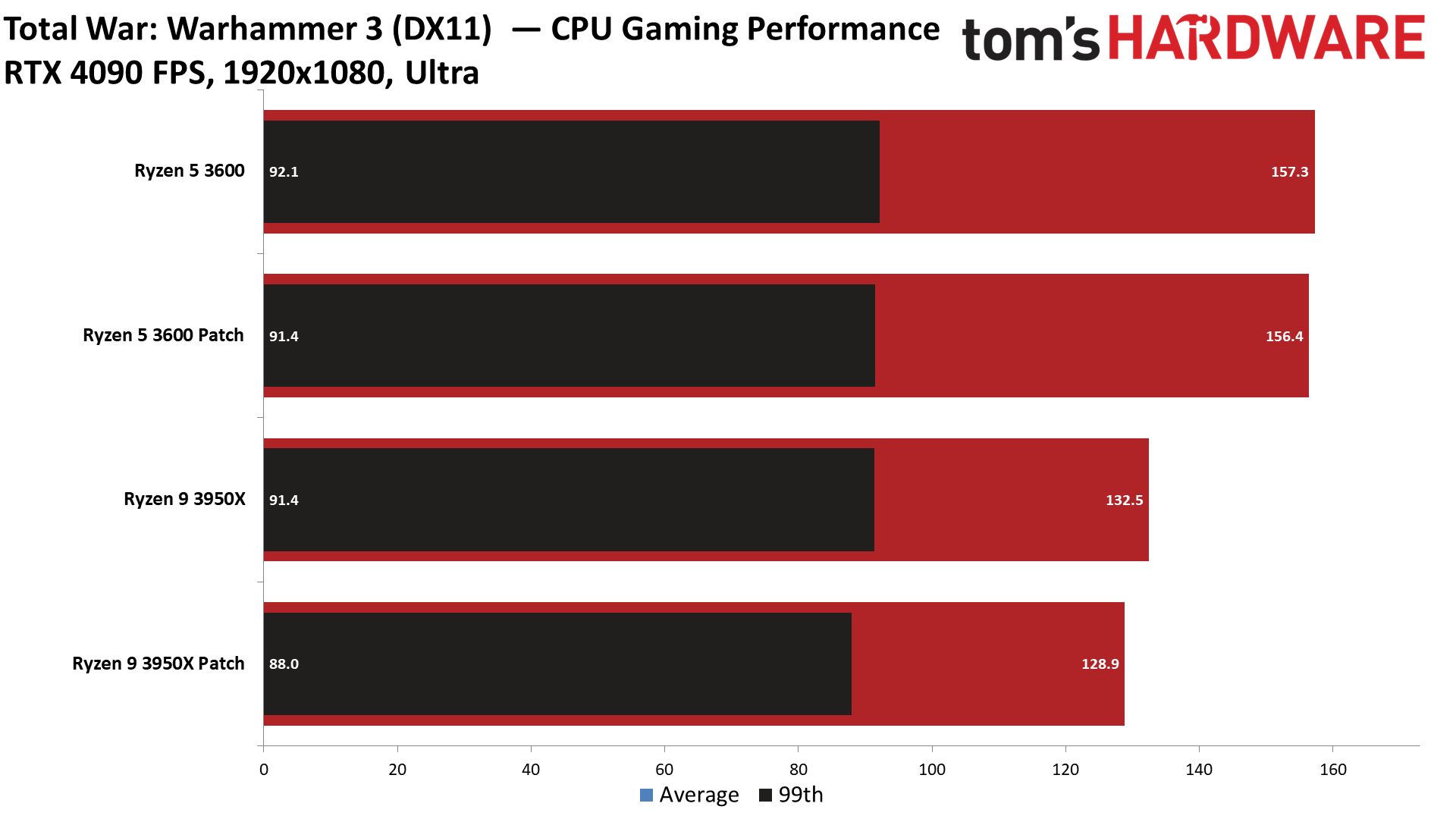
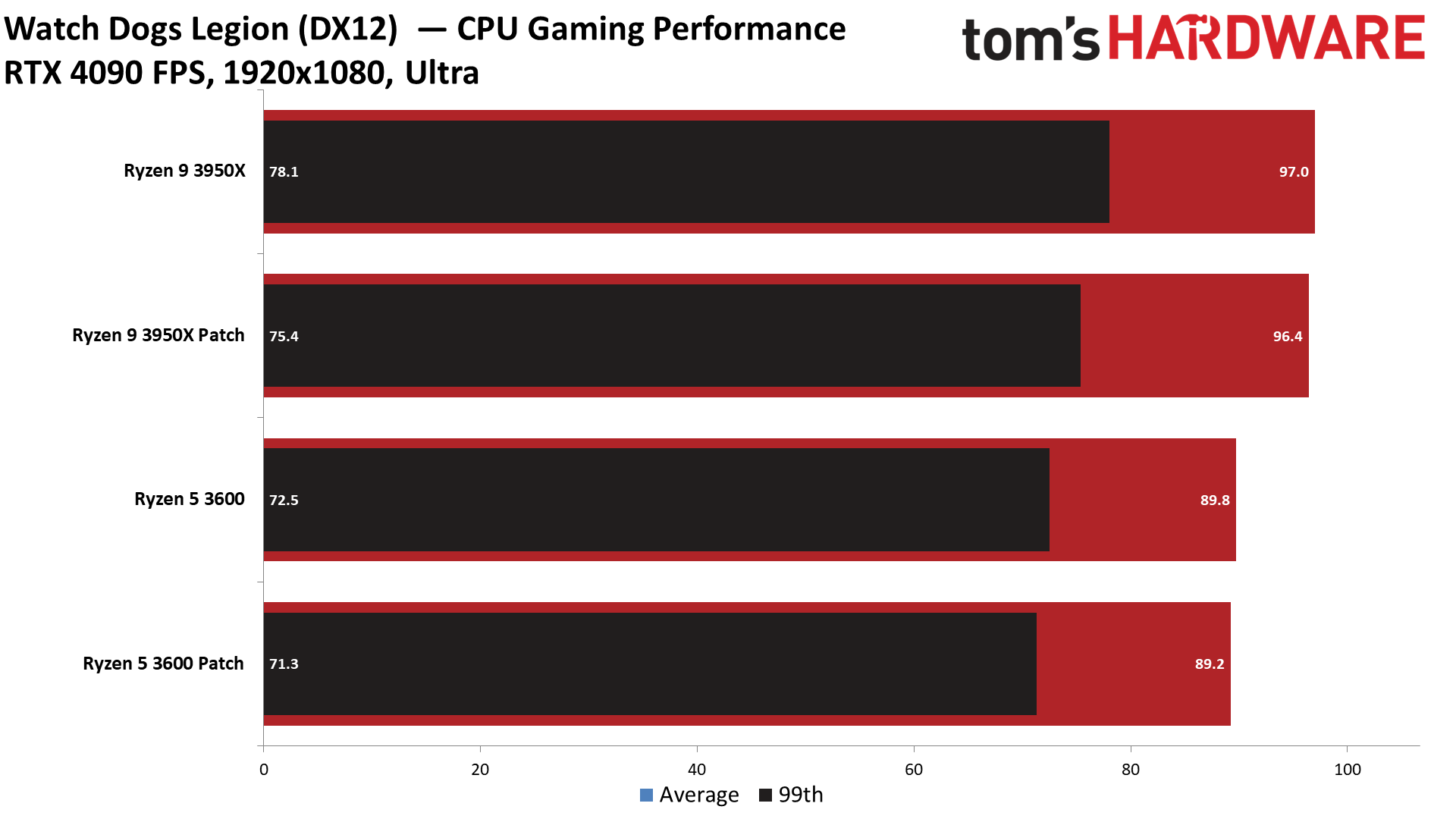
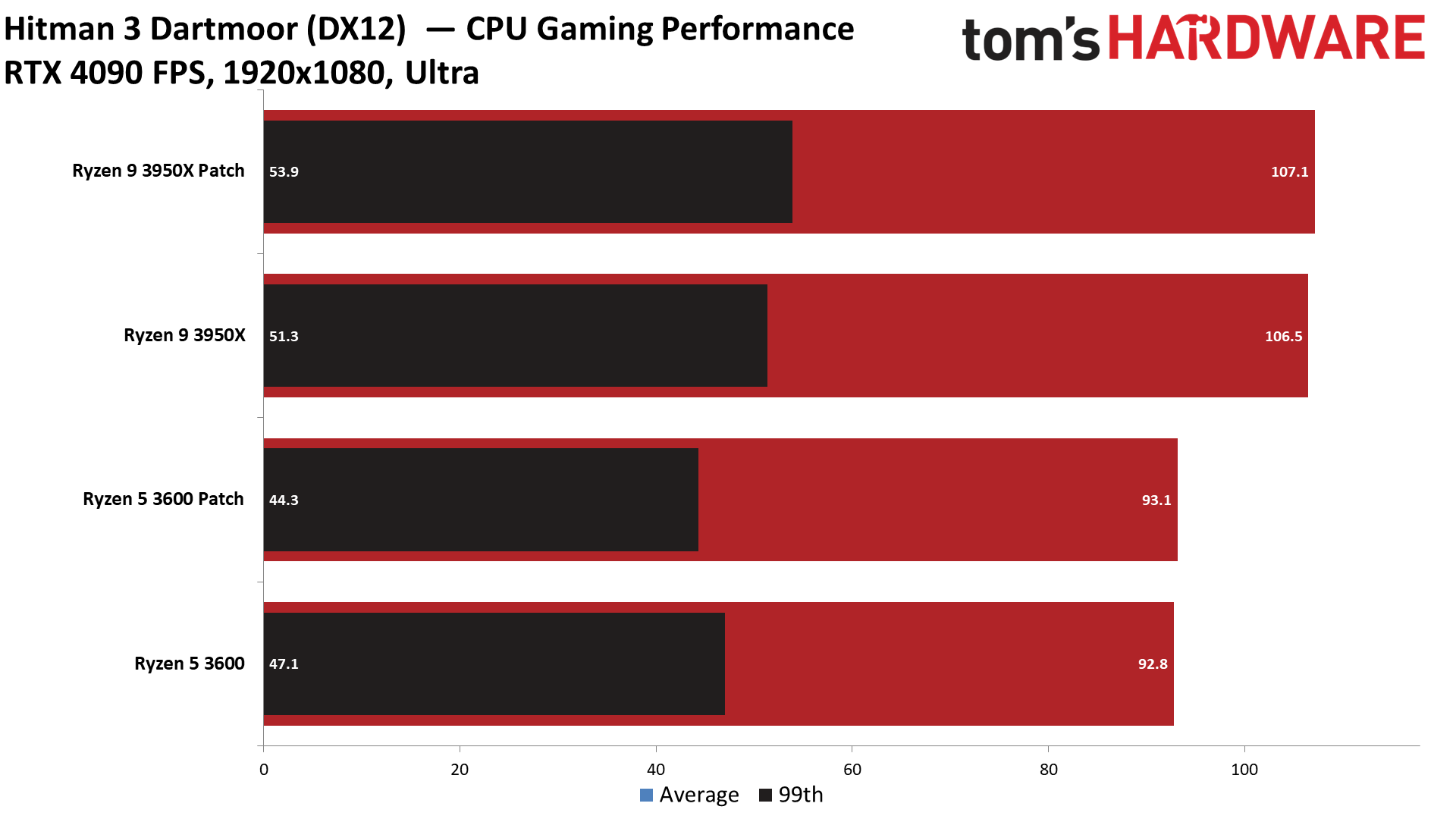
There's good news for gamers: The Zenbleed patch has very little to no discernible overhead in average 1080p and 99th percentile framerates. We recorded less than a 1% variance in our cumulative measurement of average and 99th percentile fps, meaning any difference between the two settings falls into the expected run-to-run variance of the benchmarks.
We tested five titles to look for any meaningful differences, but overall the patched and unpatched configurations were nearly identical in 1080p gaming, with Watch Dogs Legion, Cyberpunk 2077, Far Cry 6, Hitman 3, and Warhammer 3 all delivering comparable performance in our tests. Naturally, some games may be impacted in different ways, but our test results indicate that any impact likely won't be noticeable.
AMD Zenbleed Productivity Application Performance Impact
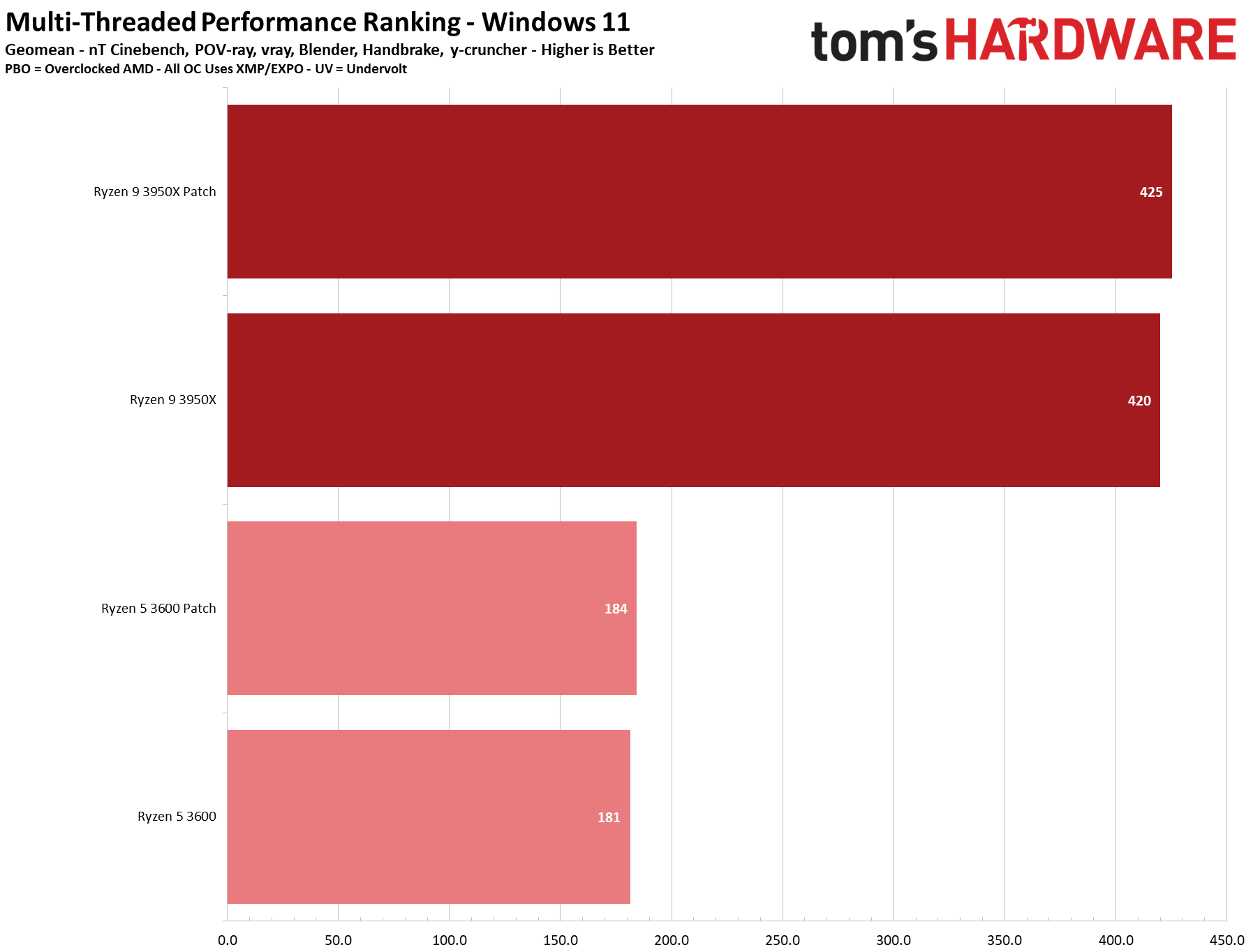
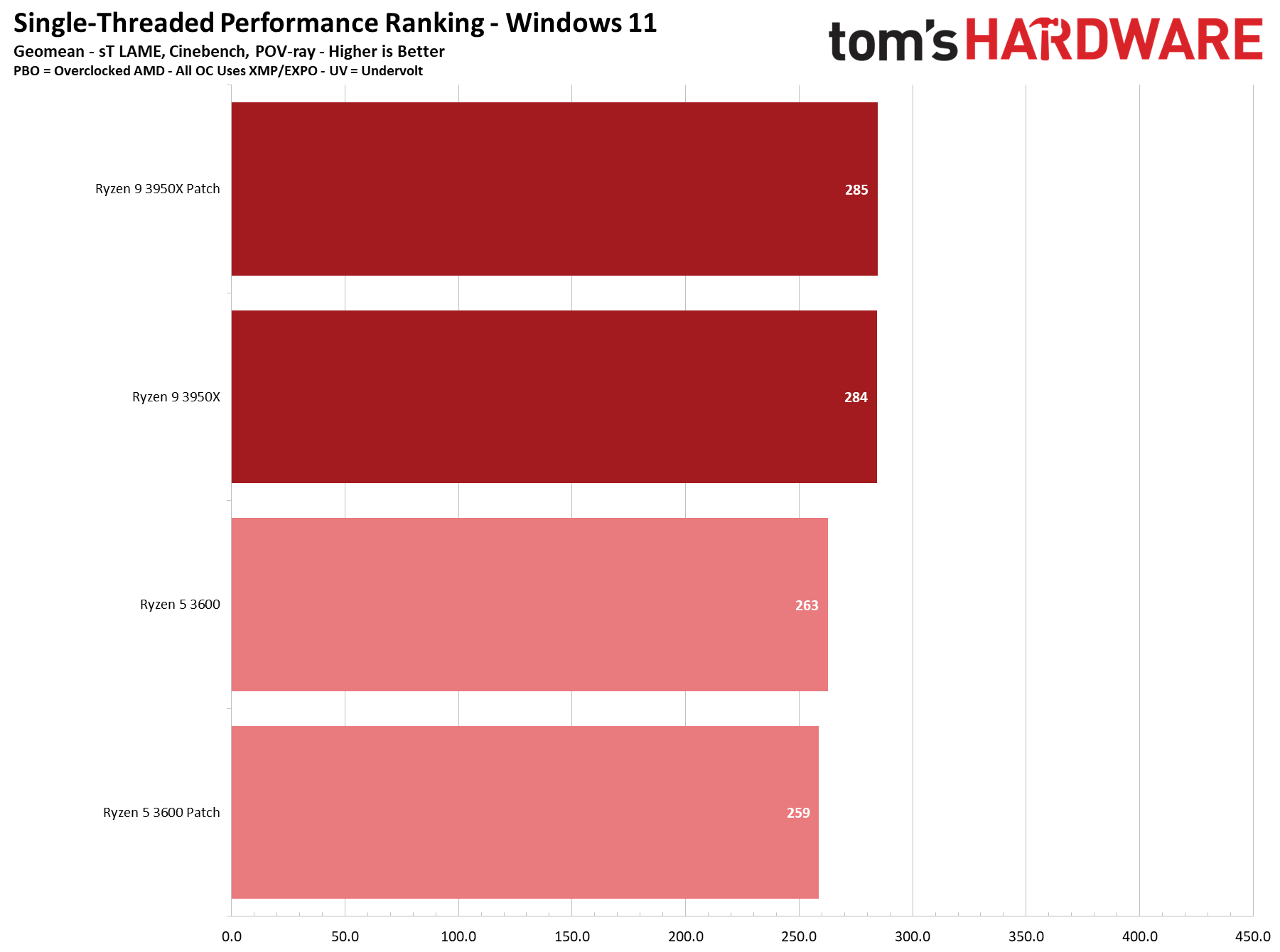
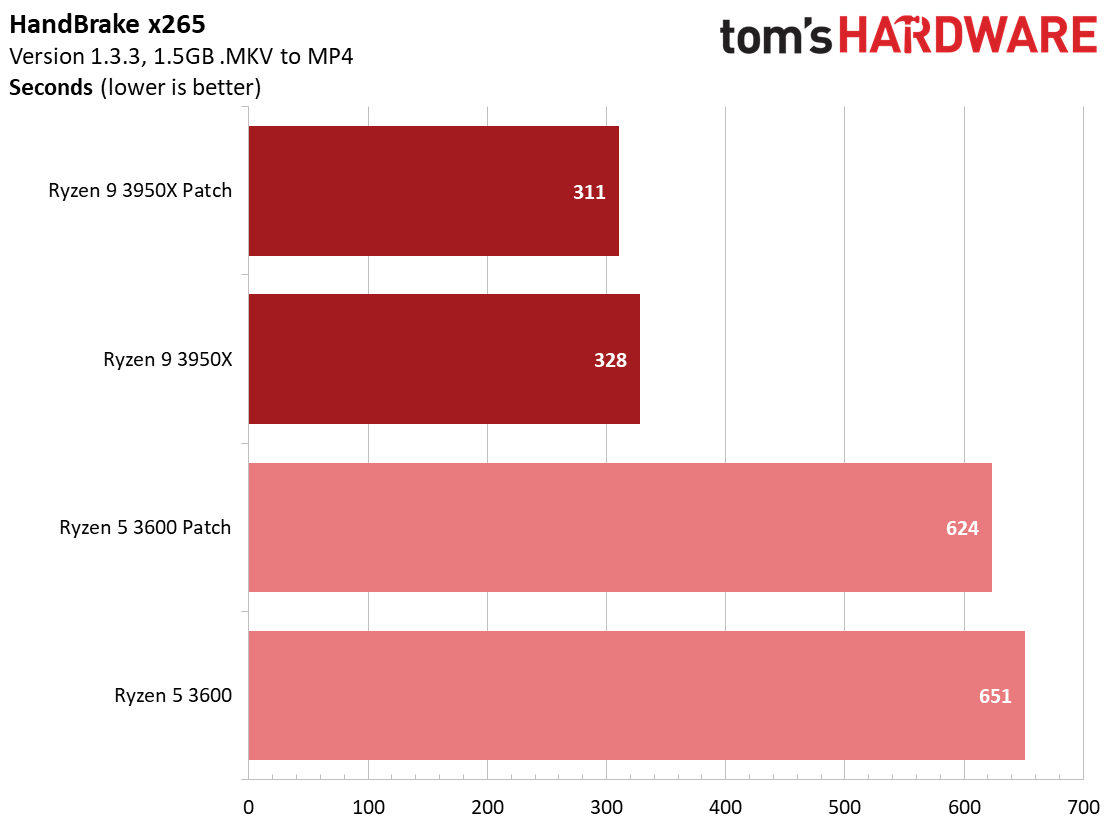
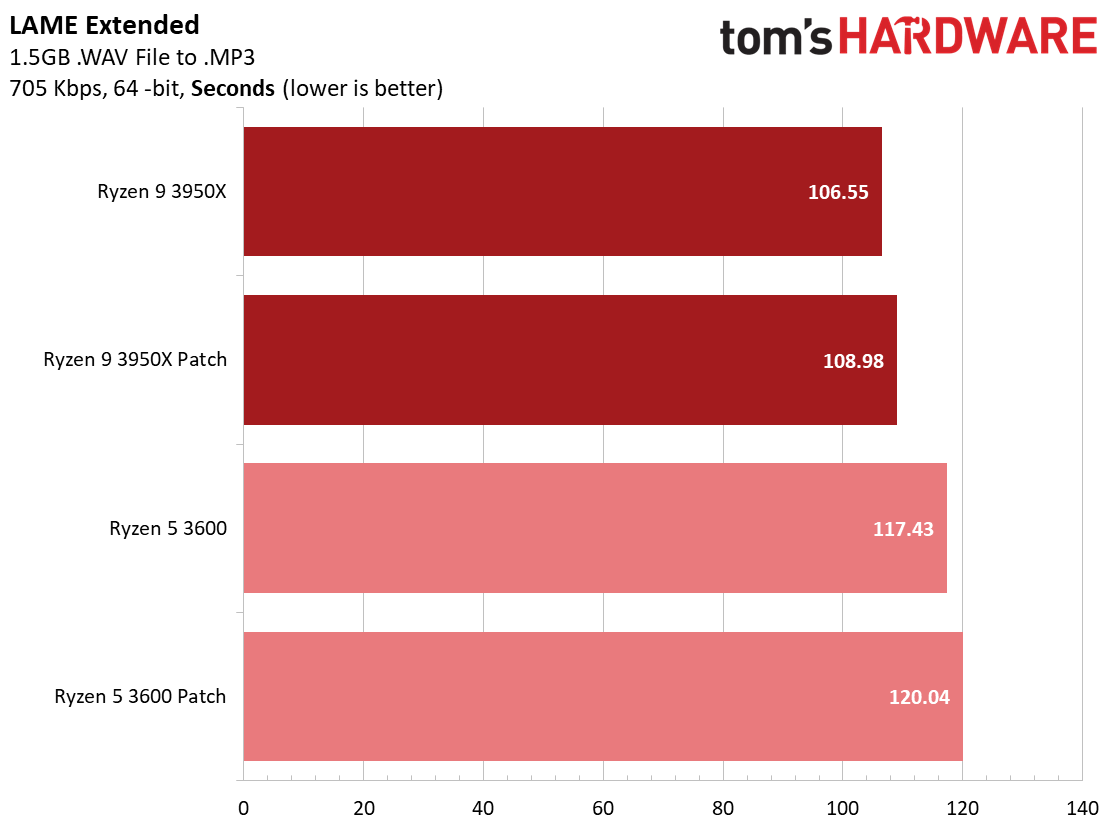
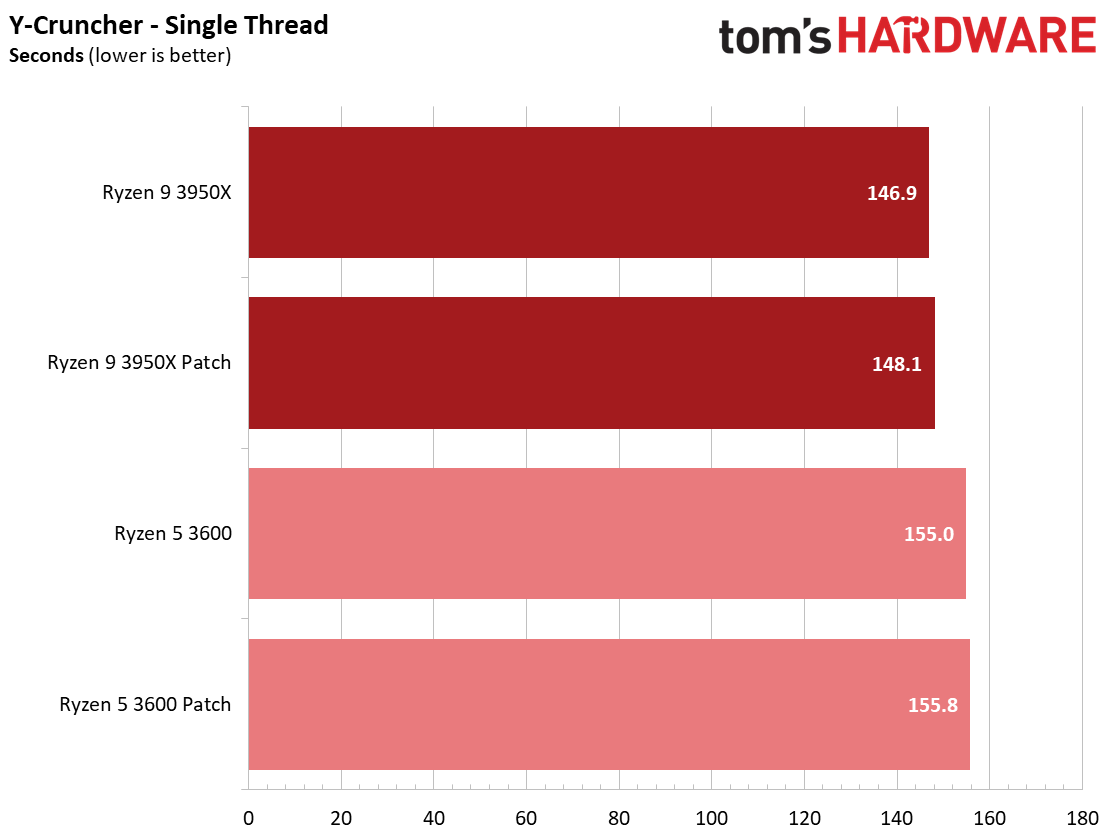
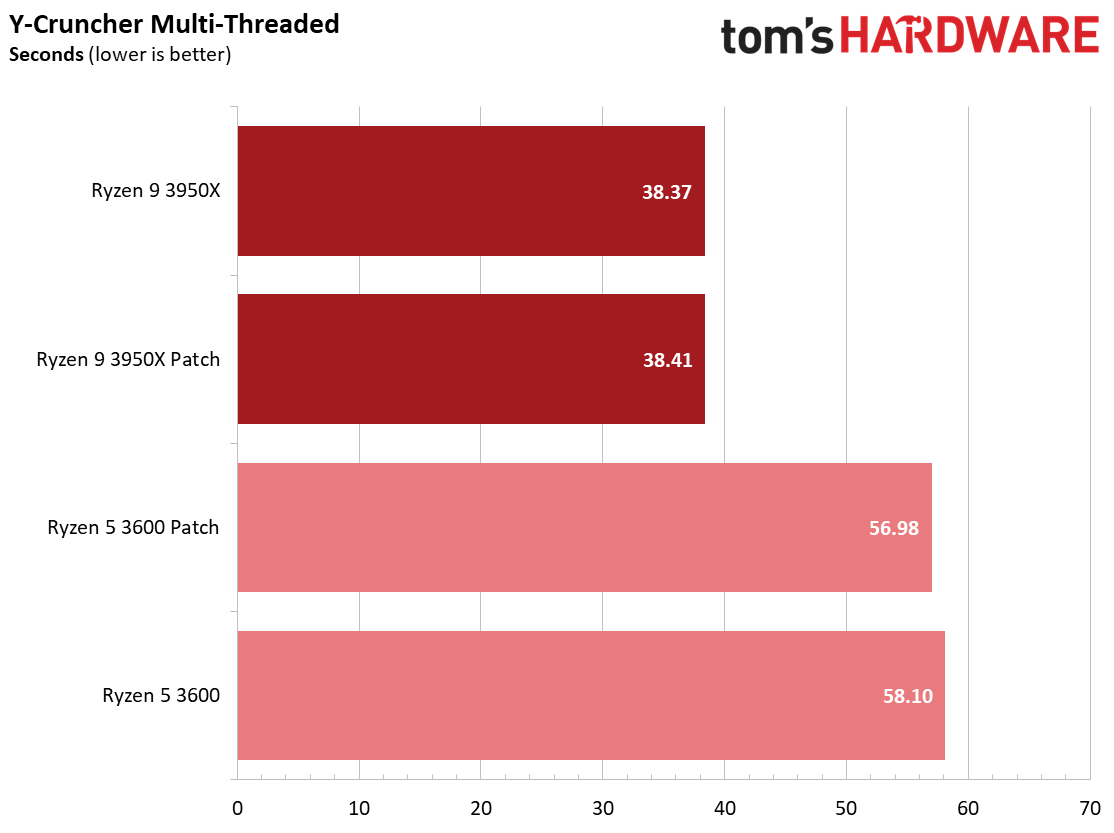
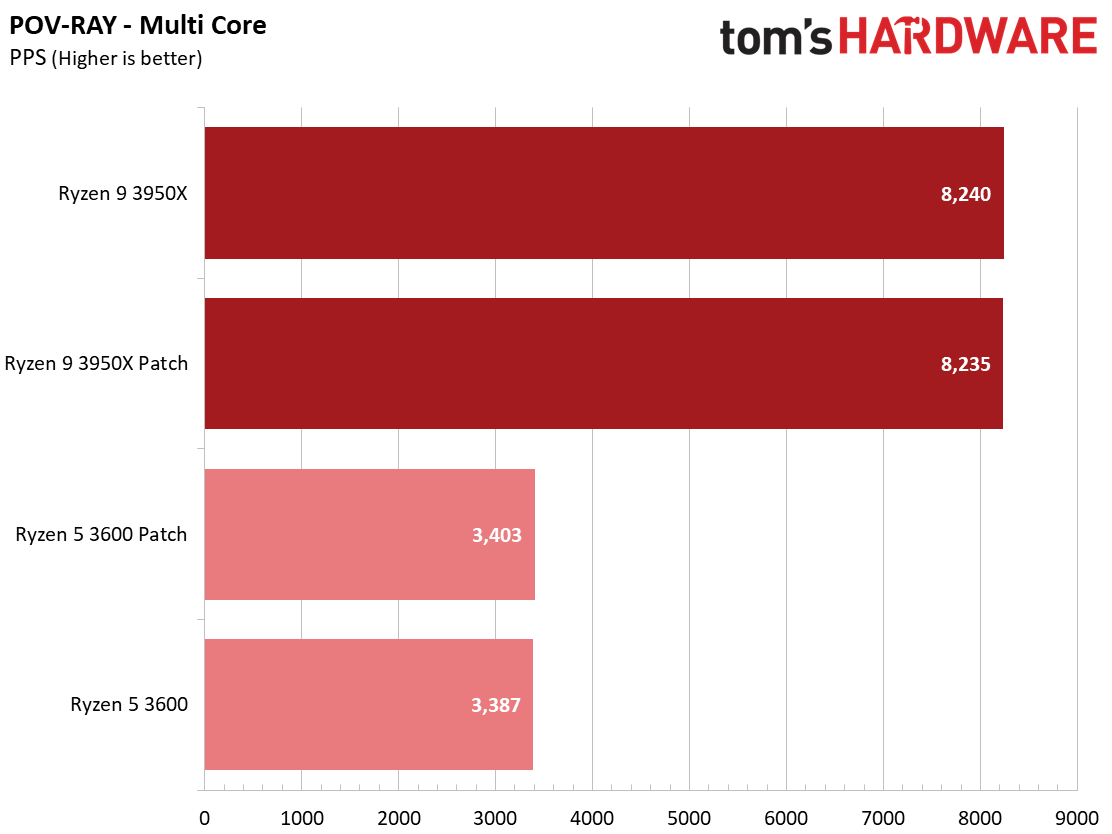
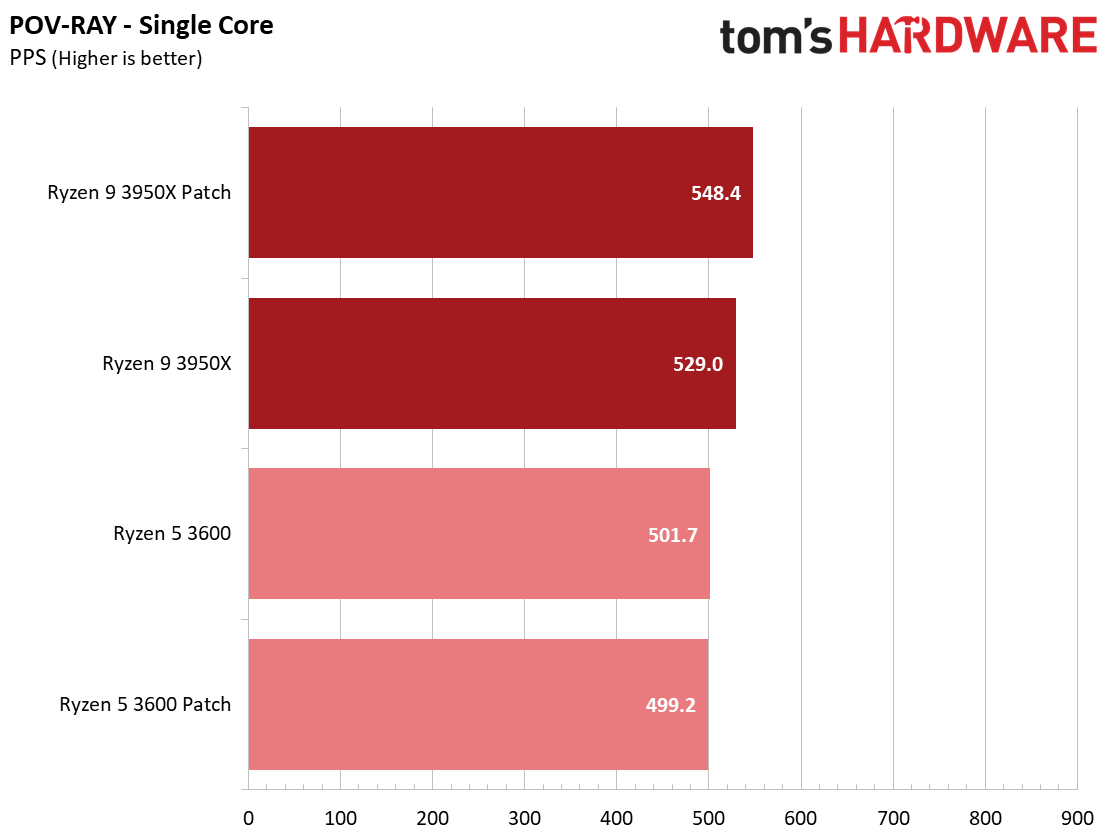
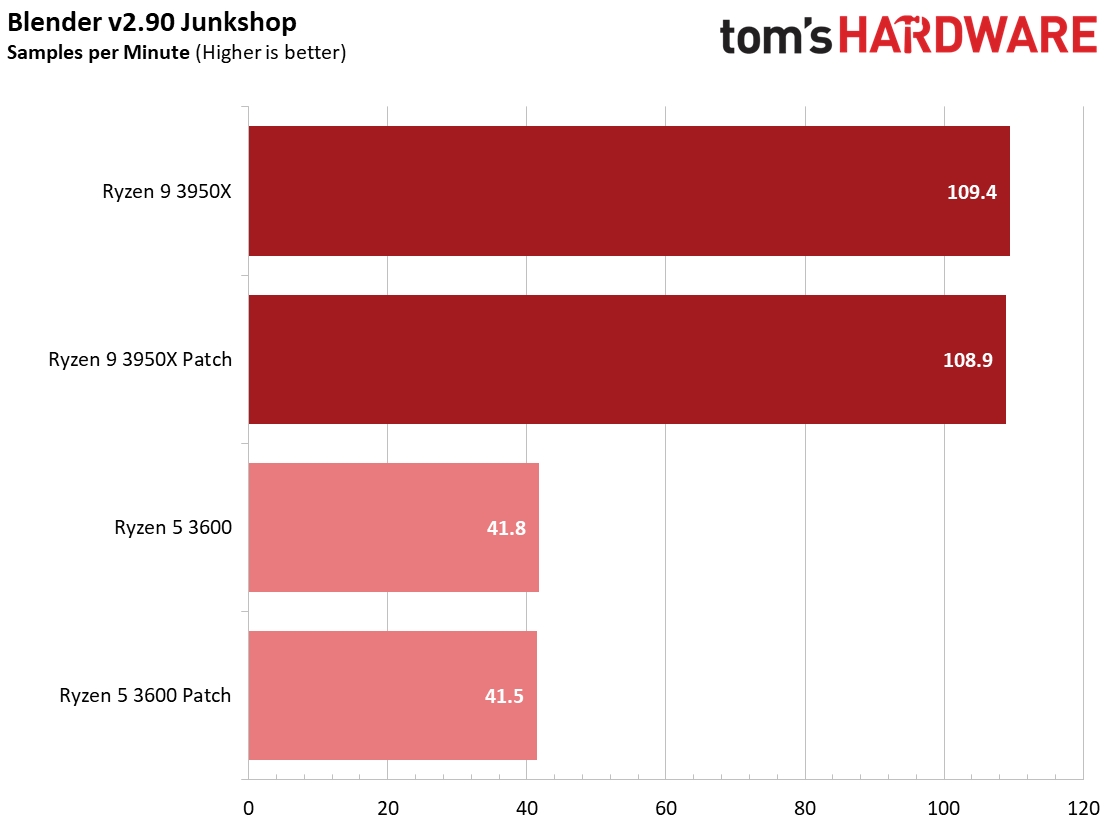
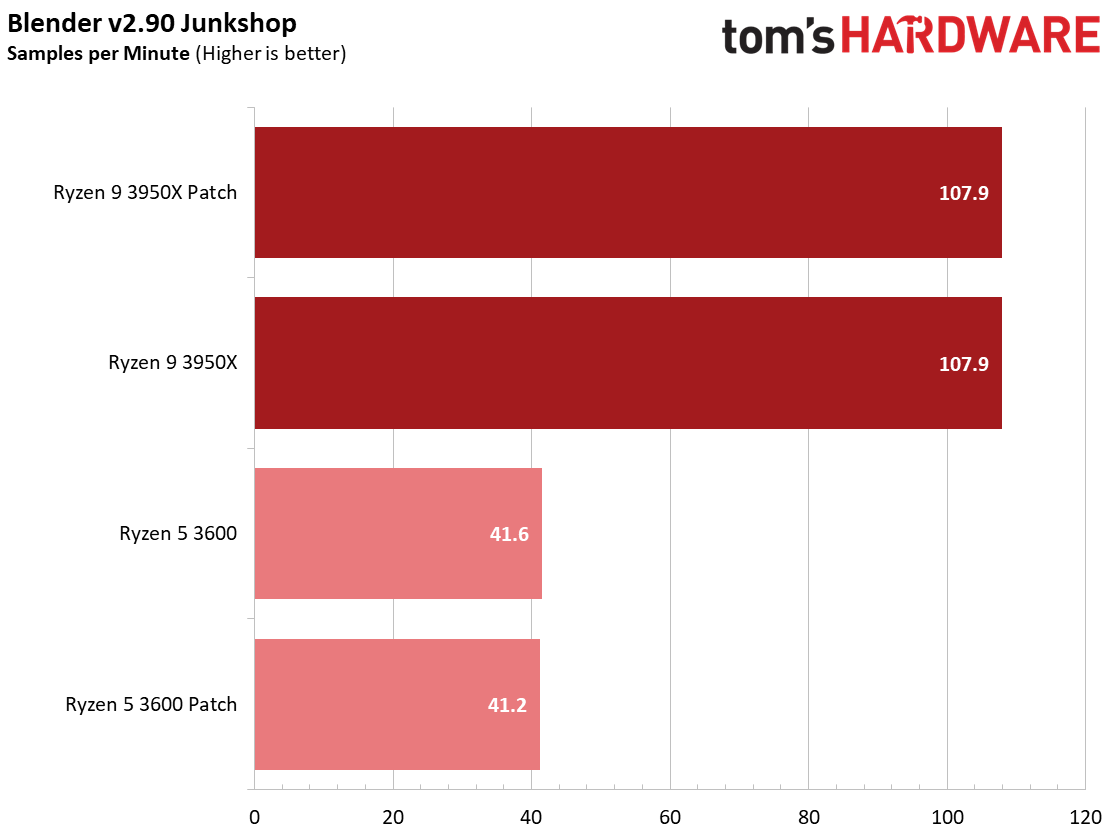
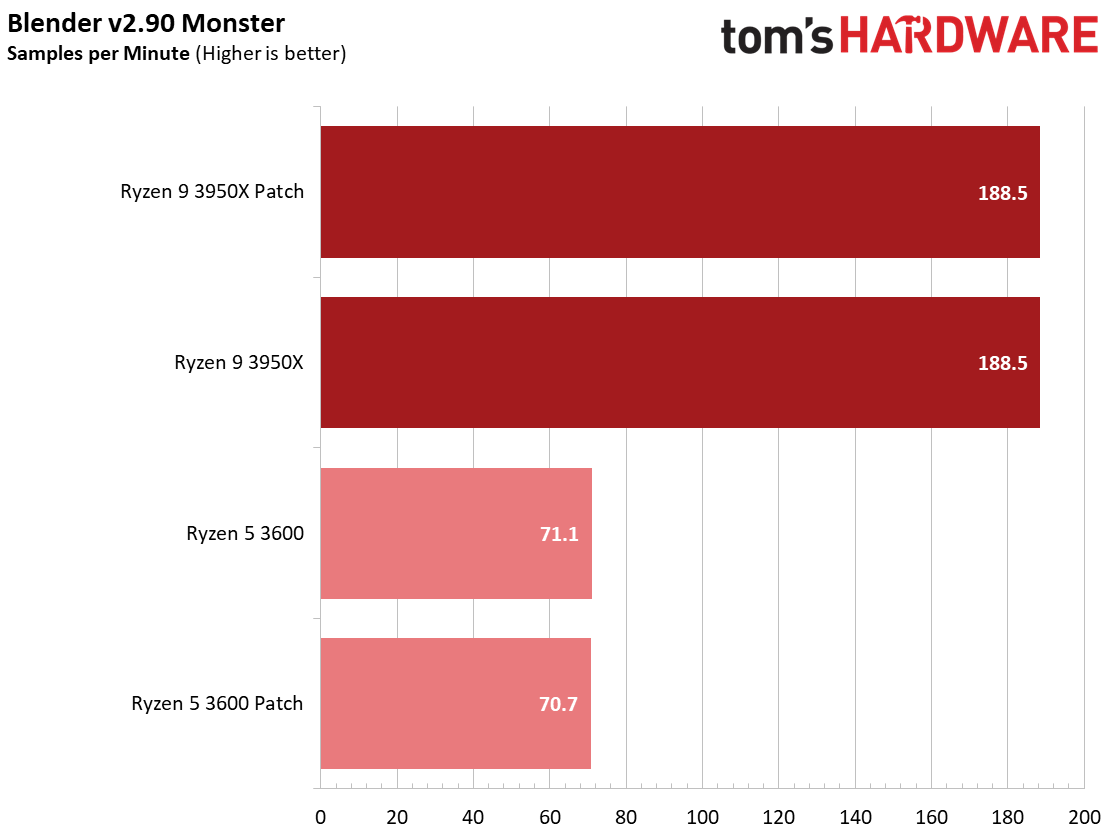
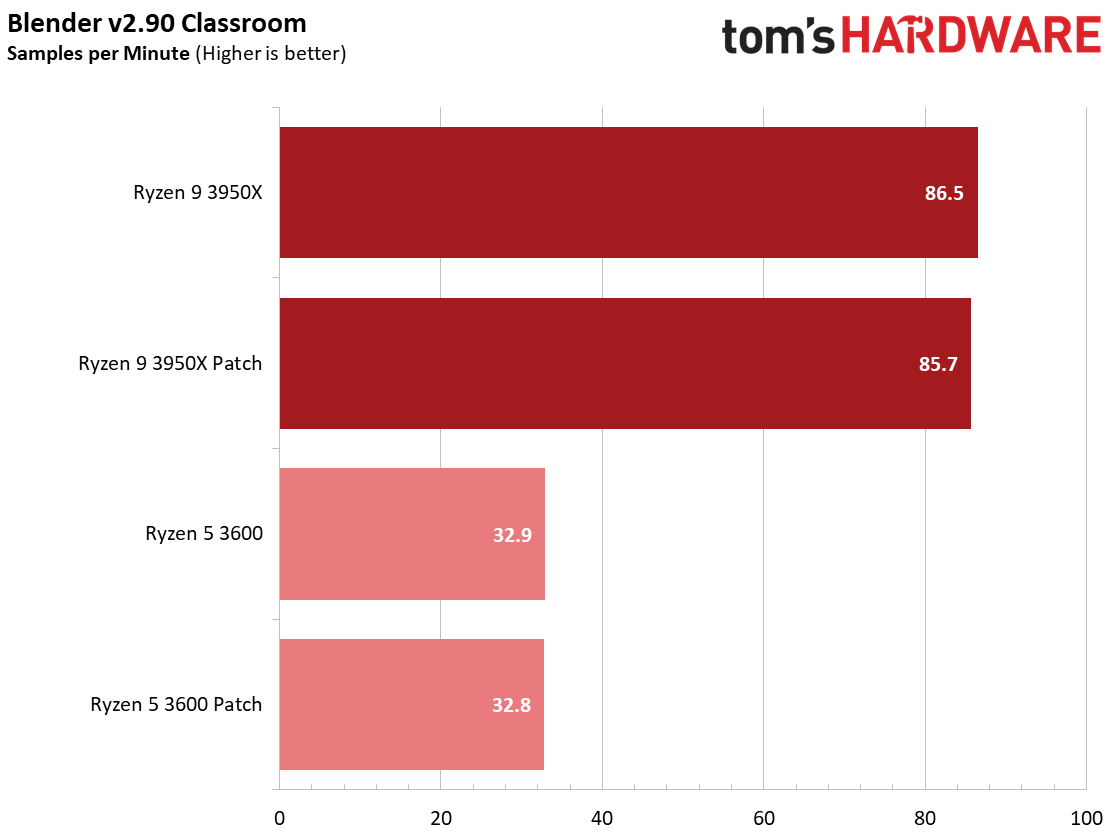
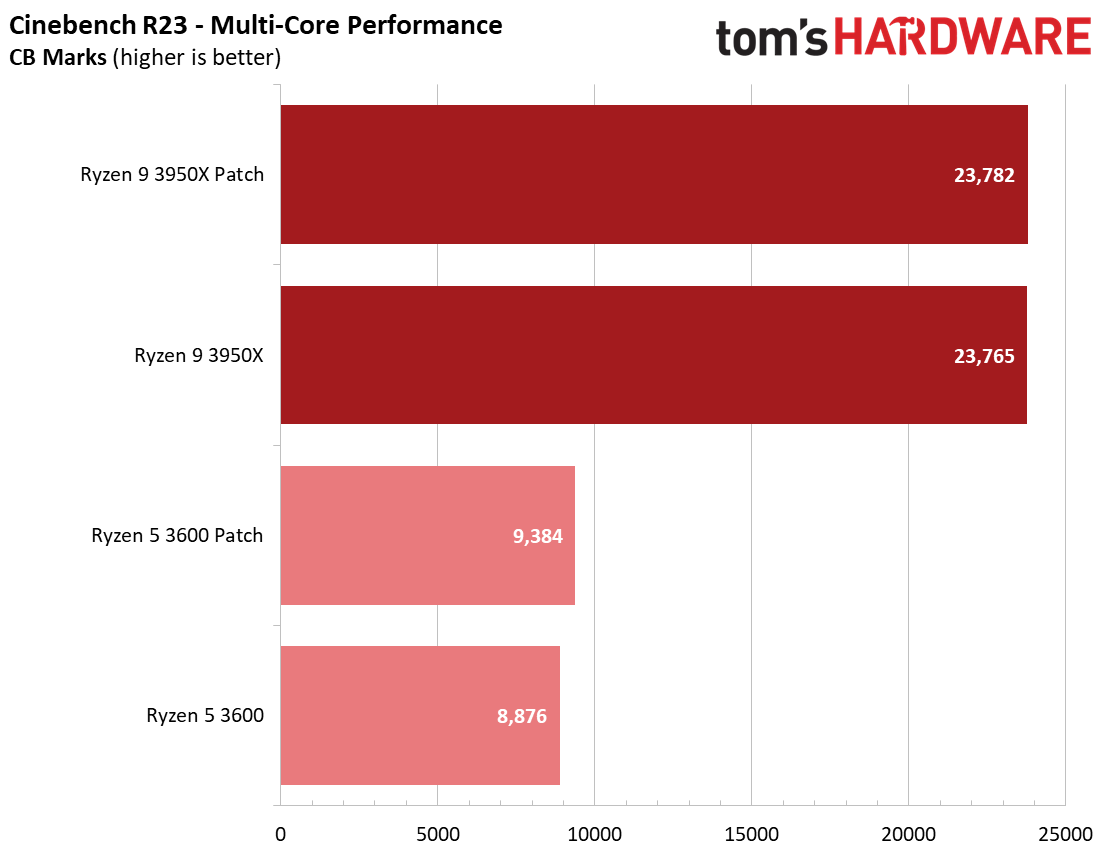
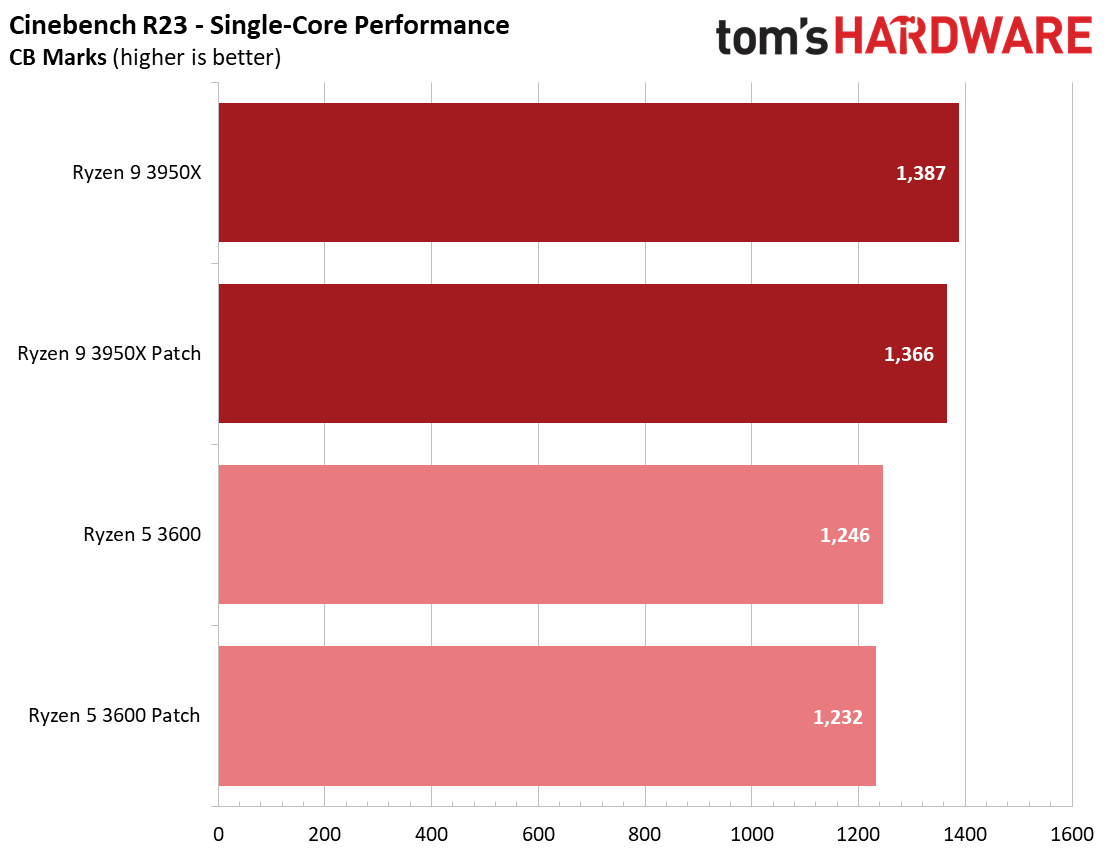
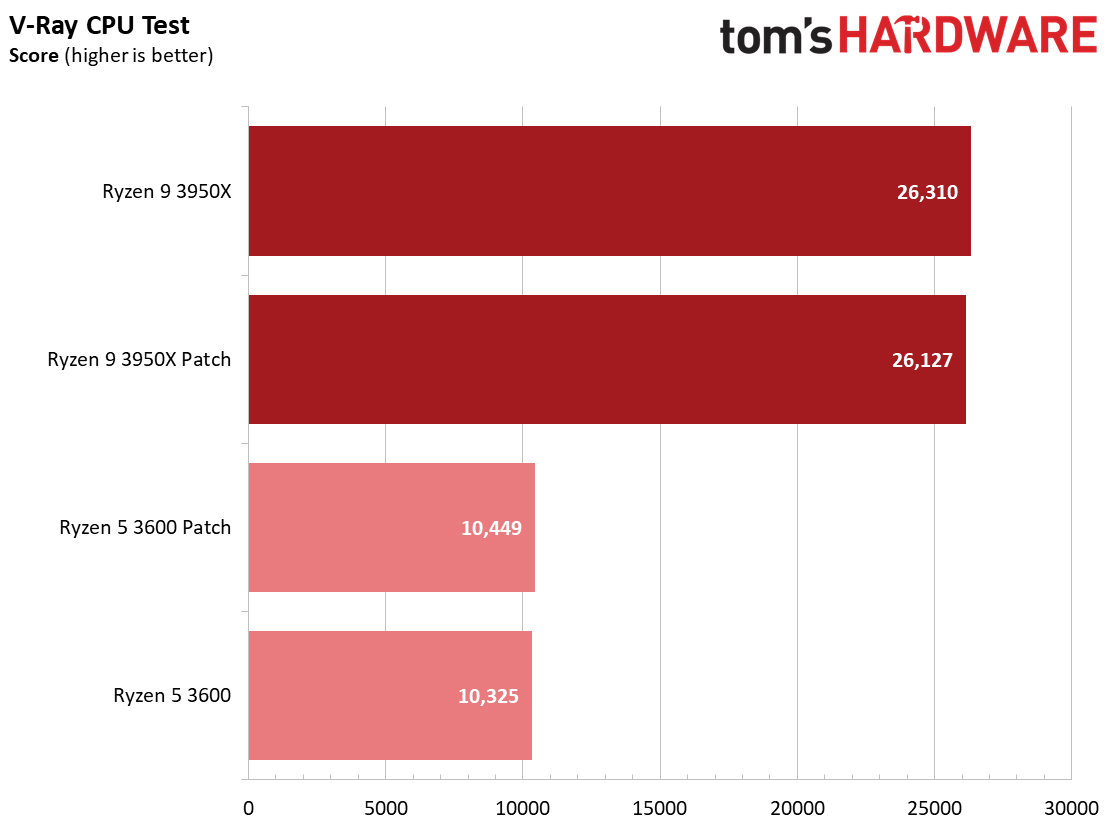
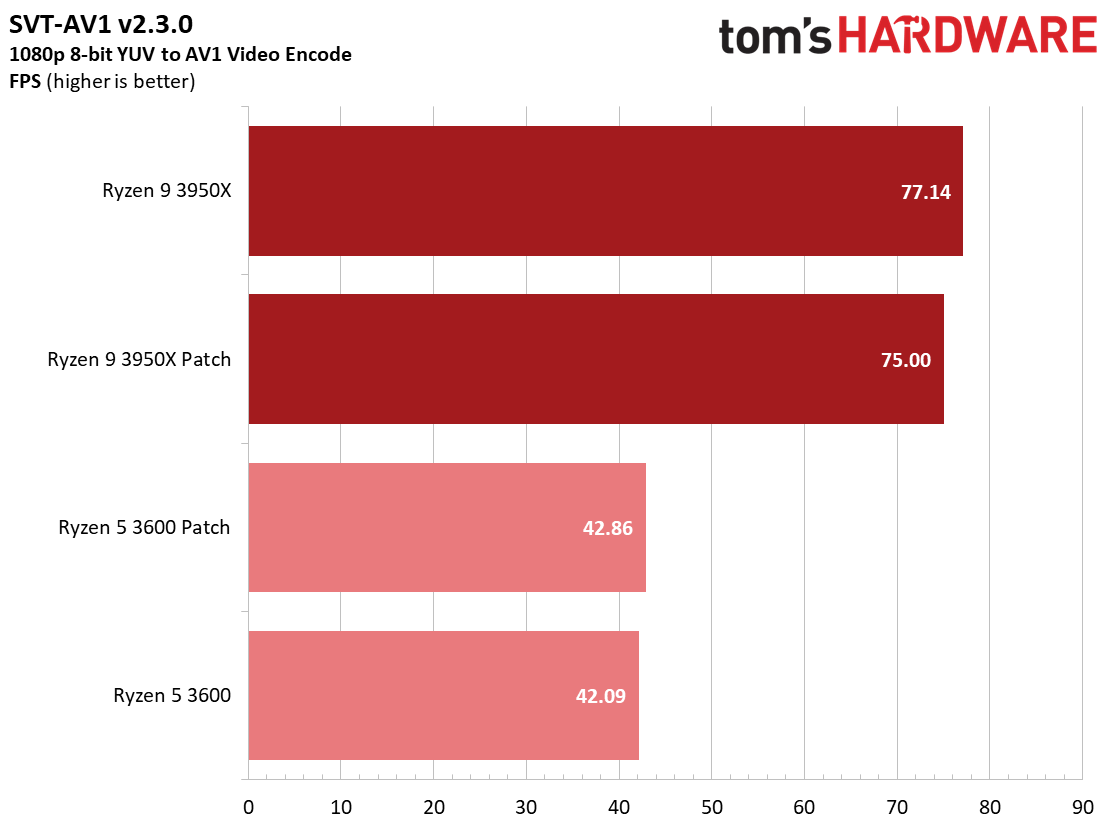
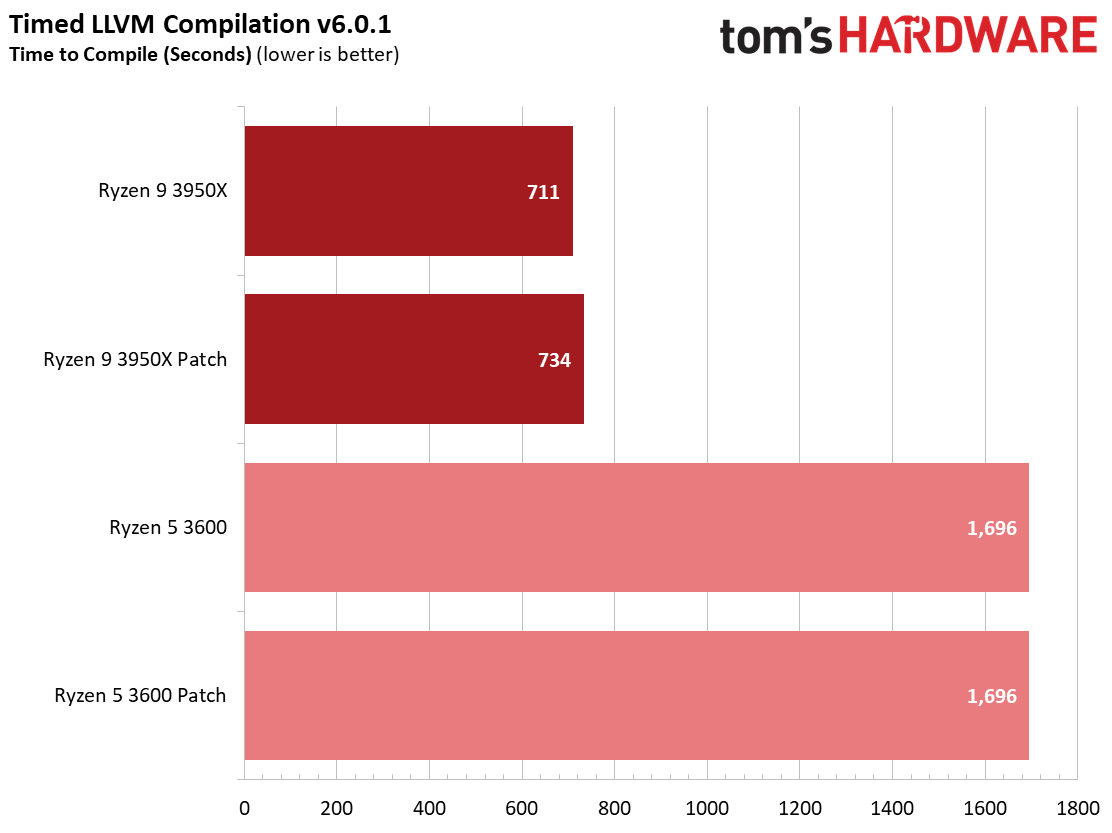
We see a few significant performance differences in select productivity applications, but those don't show up as well in our cumulative single- and multi-threaded performance slides, which are comprised of the geometric mean of the most important benchmarks for each type of workload, be they single- or multi-threaded. We use these as a general measure, but the metric doesn't encompass every workload in our test suite, and some of our other benchmarks also show a significant impact, as you'll see in the next section.
We see small differences in our overall measurement, with roughly a 1% delta for multi-threaded performance with the Ryzen 9 3950X and a 2.2% variance with the Ryzen 5 3600, but there are exceptions within this series of tests.
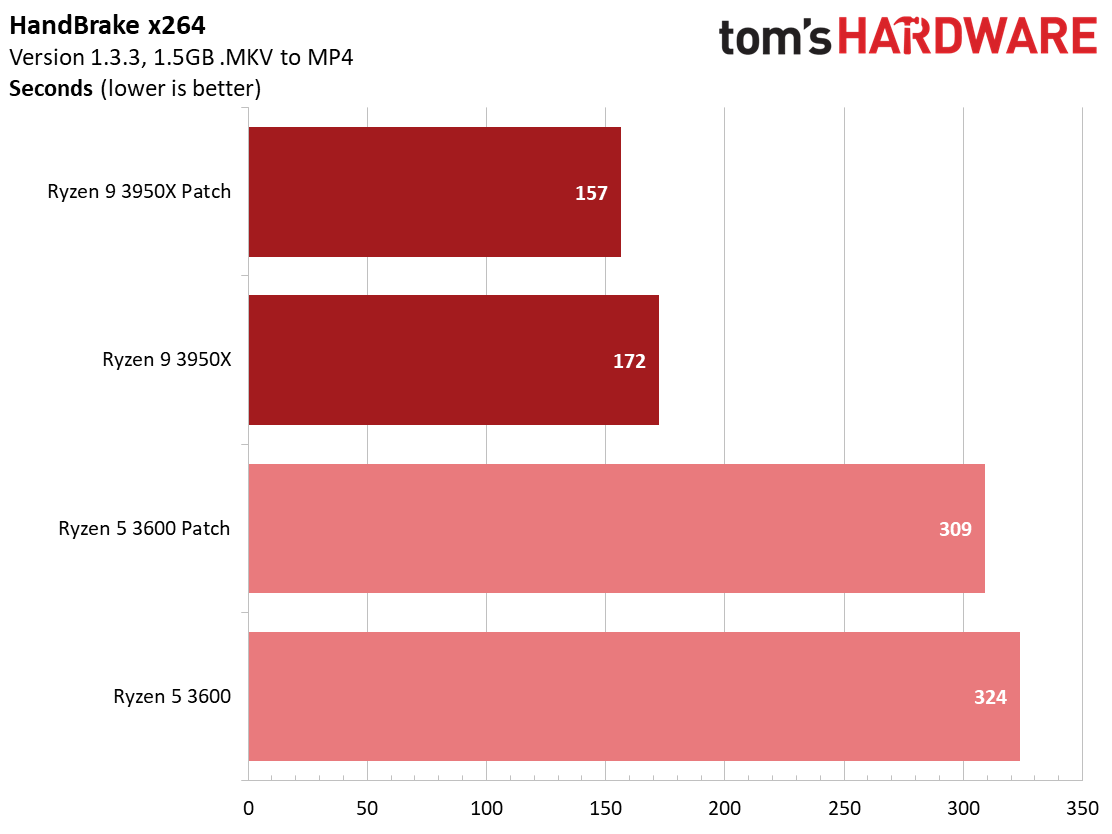
HandBrake shows significant performance losses of around 5% for both chips in the x265 transcode, while using the x264 codec results in a 10% difference between patched and unpatched configurations. These might seem like slight differences in the completion time for these relatively short-duration tests, but longer-duration jobs could result in a noticeable amount of extra time to complete the tasks.
LAME, an audio encoder that is very sensitive to single-threaded performance, is roughly 2.5% slower for both patched chips. However, some benchmarks, like the ray tracing renderer POV-Ray, show a slight uptick in performance, with the patched Ryzen 9 3950X carving out a 3.7% lead over the unpatched configuration.
We see an even larger gain in multi-threaded Cinebench for the patched Ryzen 5 3600 configuration, which gains 5.7%. Conversely, both patched configurations are slightly slower in the single-threaded Cinebench benchmark, highlighting that while different types of code will react to the patches differently, parallelism can also introduce variation.
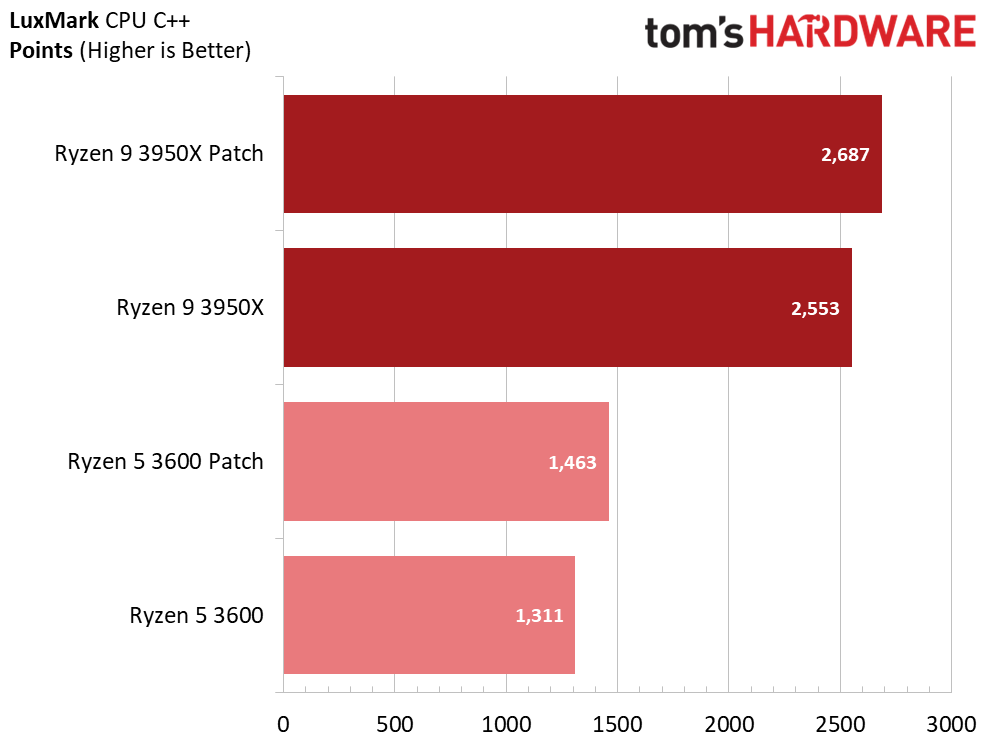
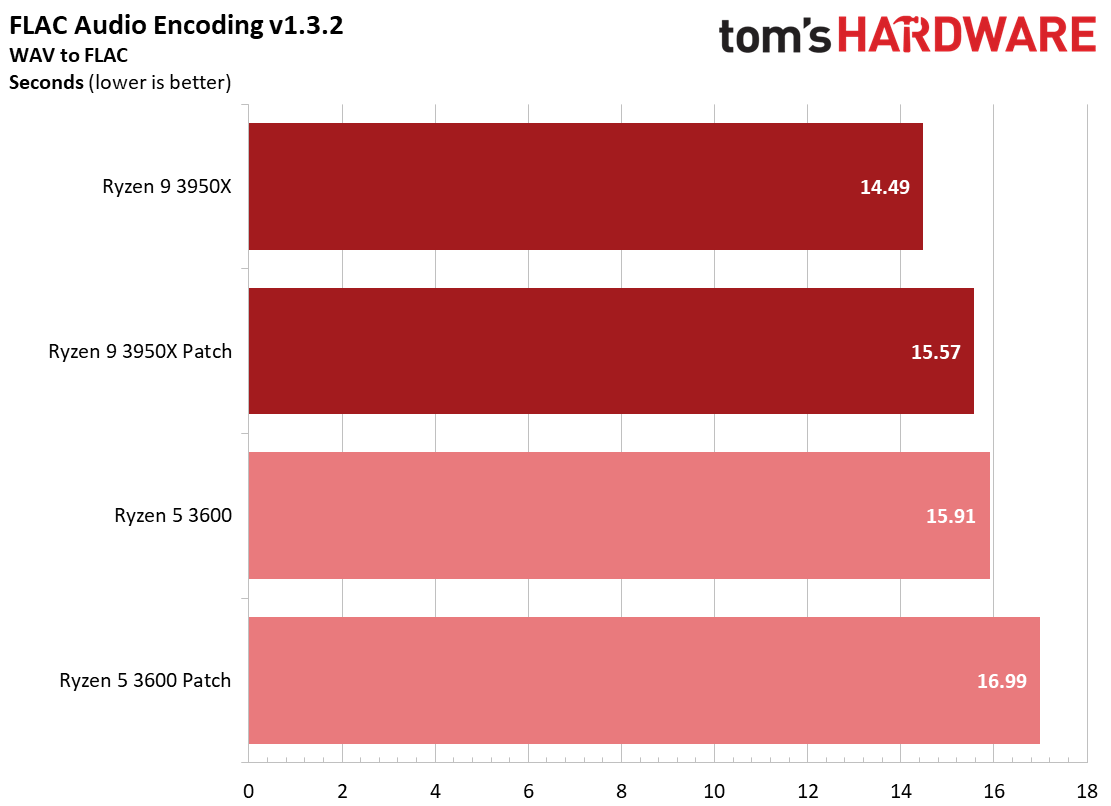
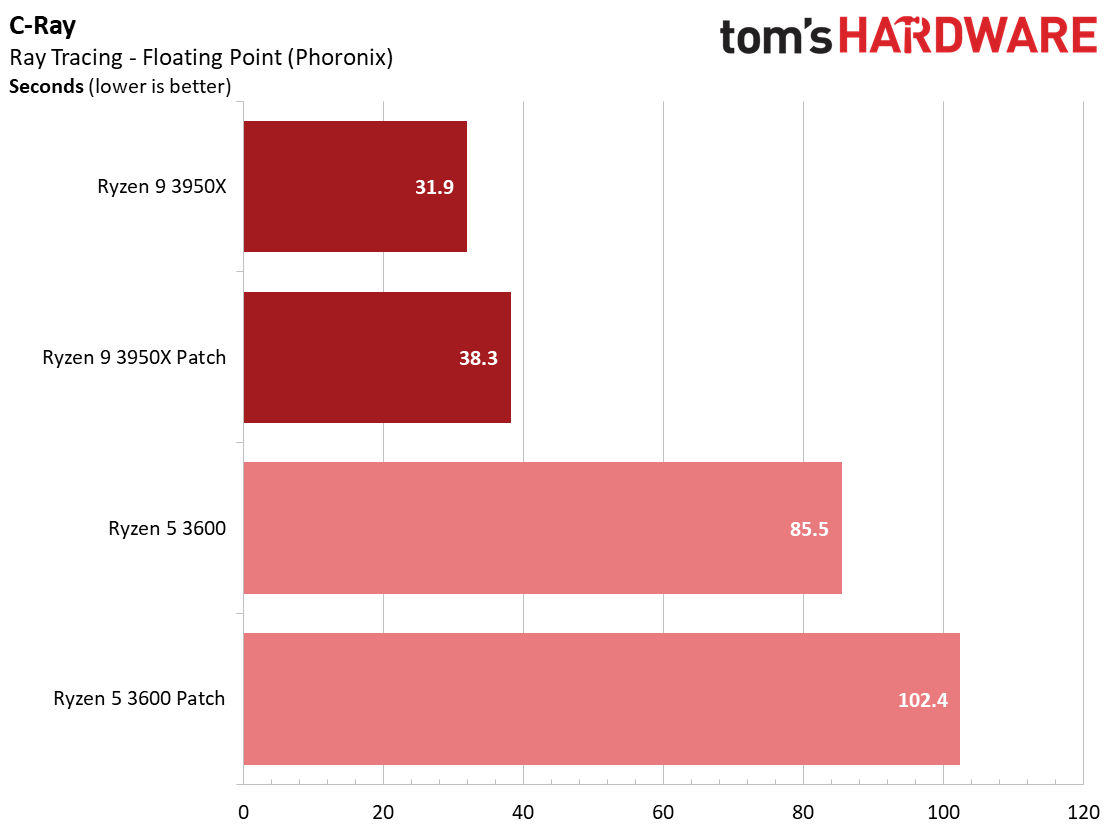
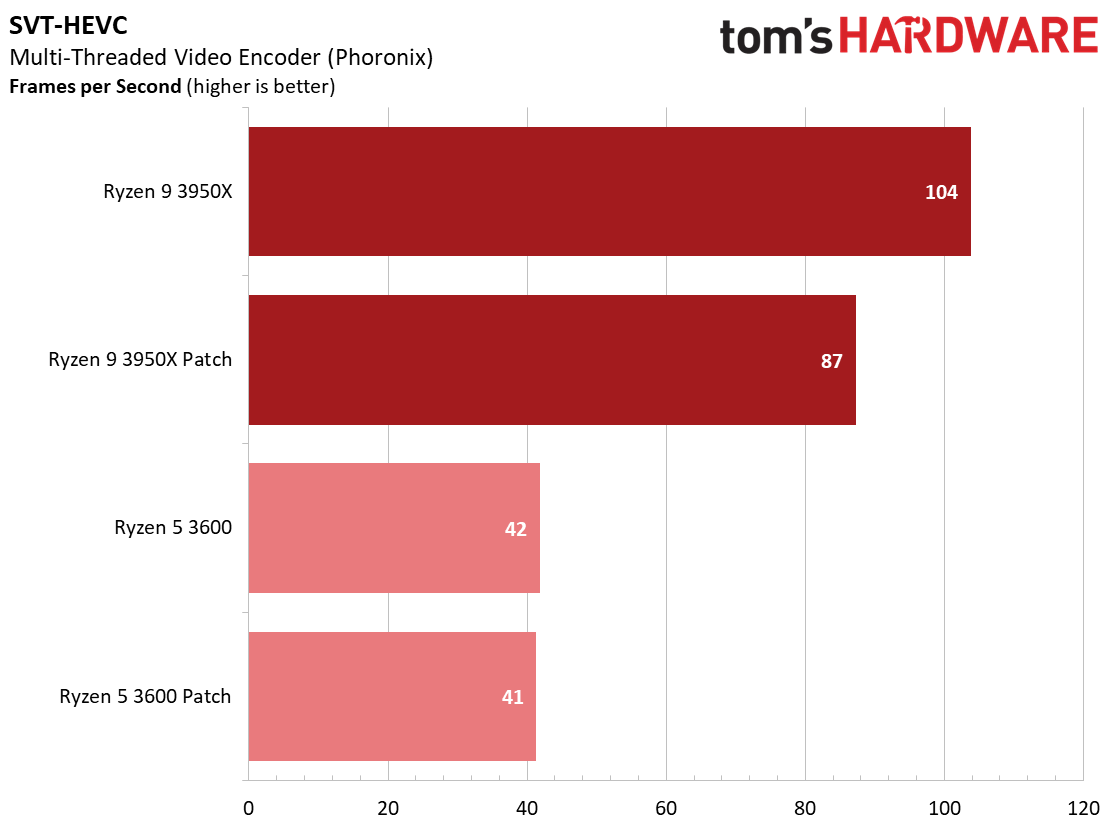
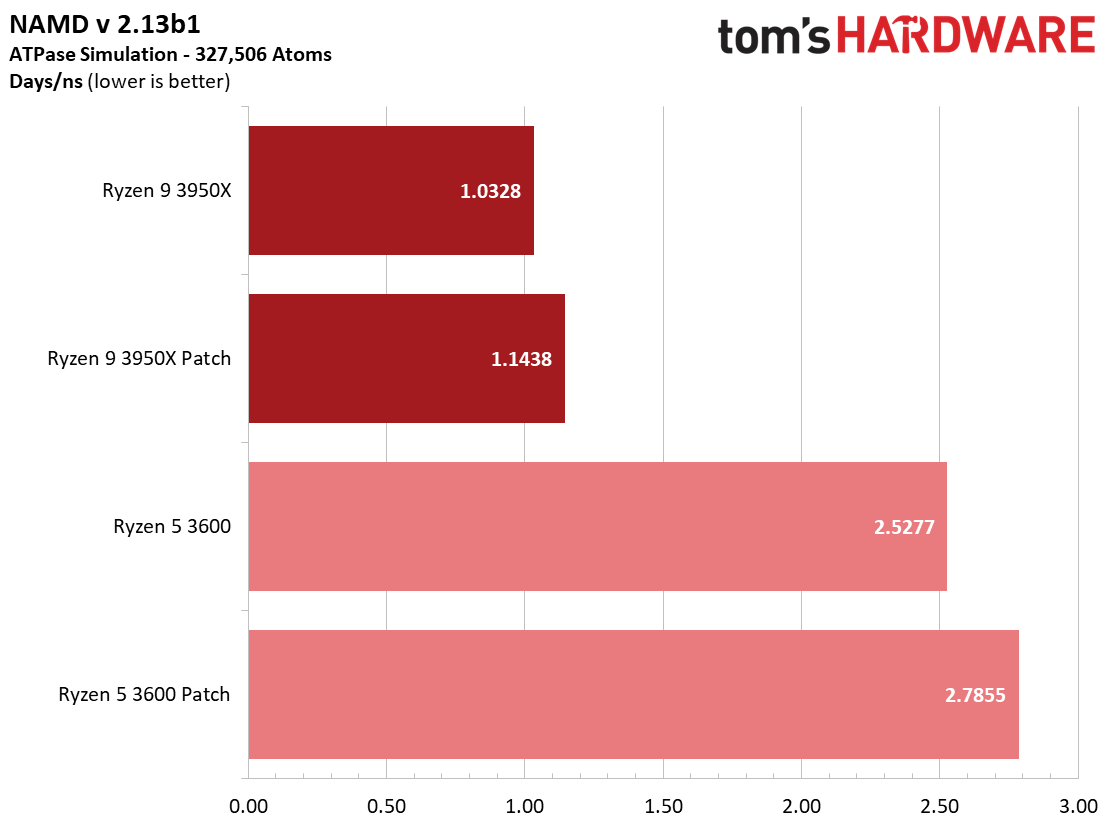
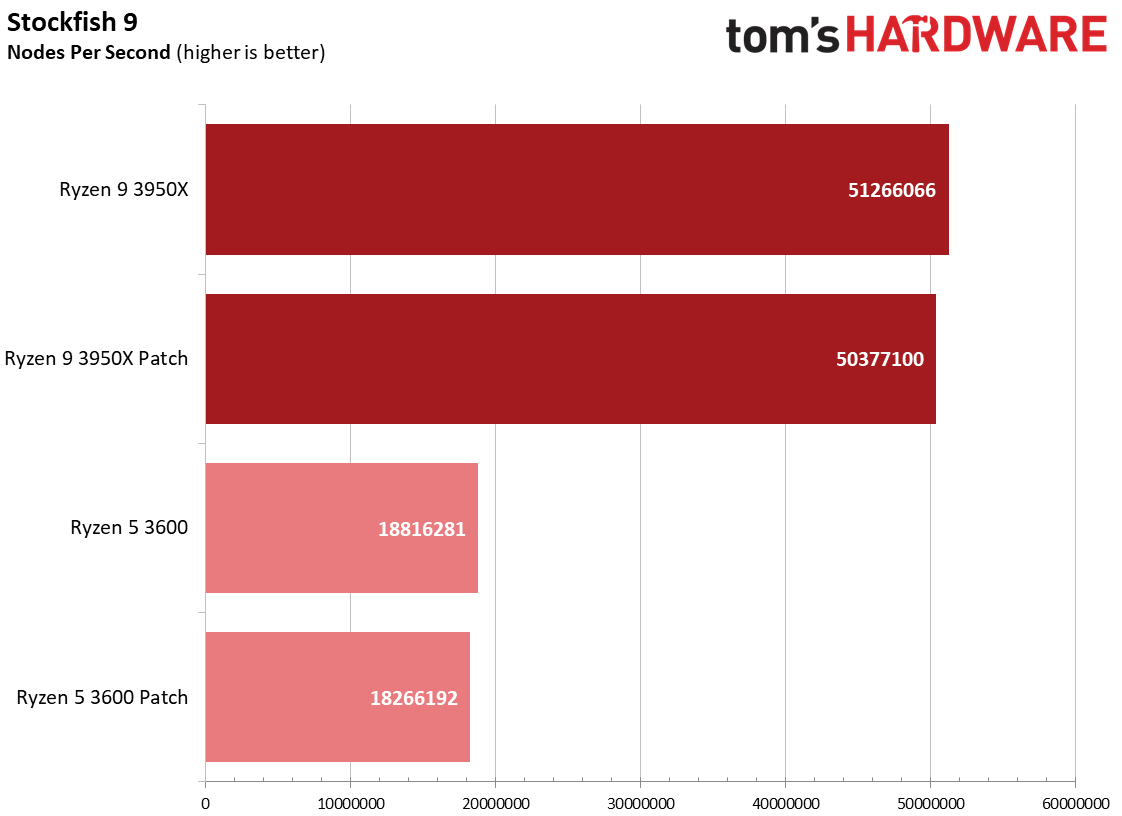
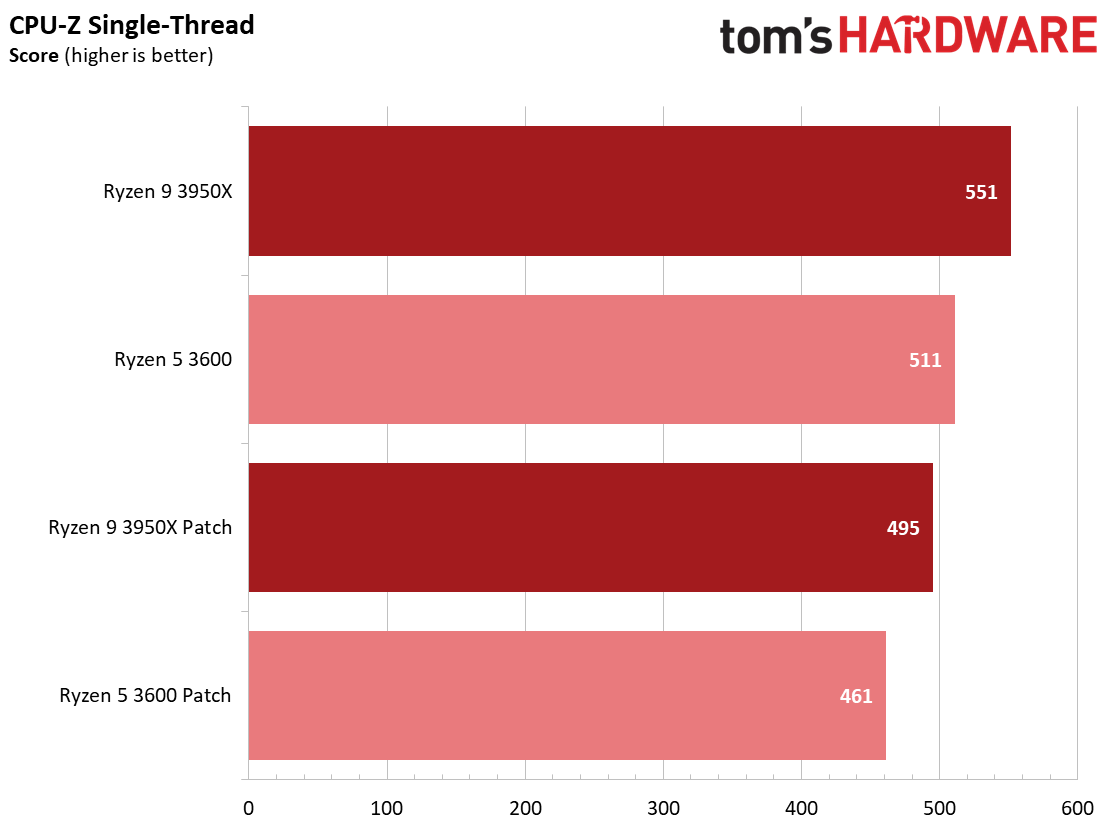
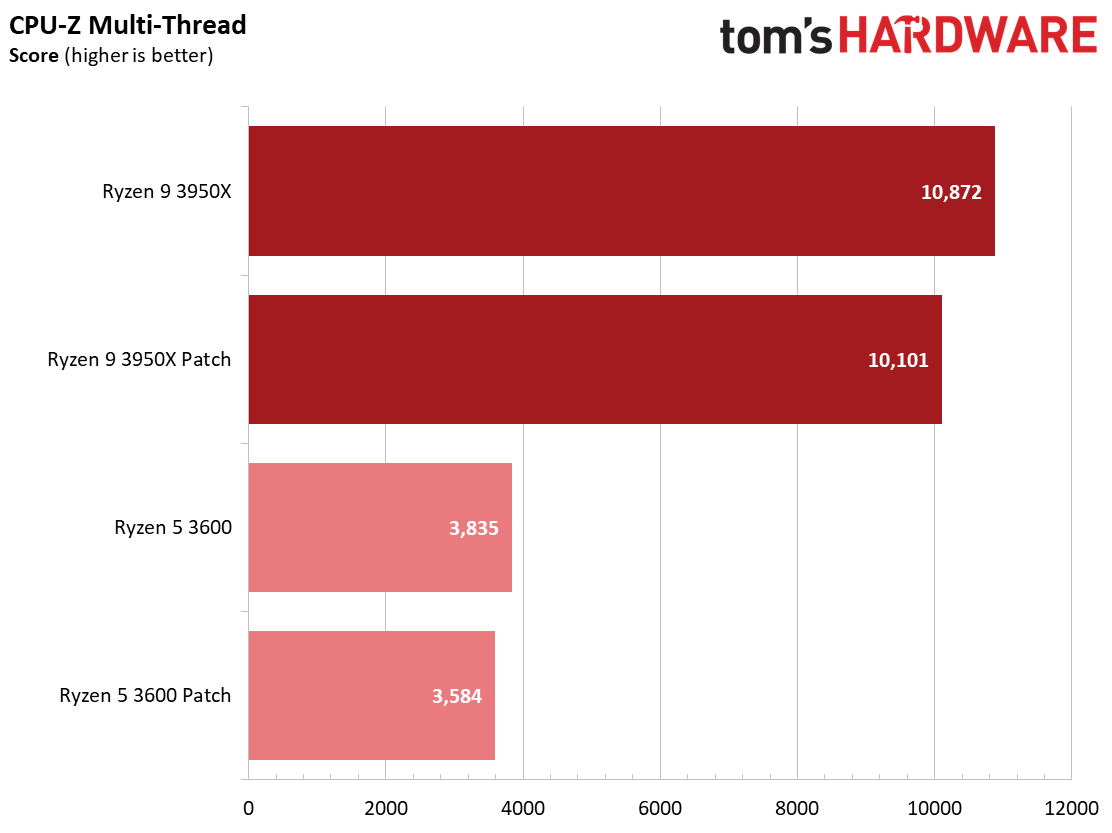
Here's a selection of other workloads that tend to exhibit the largest performance impact from the Zenbleed software patch.
We measured a 7 to 9% impact on the FLAC encoder, as well as a 16% slowdown in the SVT-HEVC encode job for the Ryzen 9 3950X. Taken in context with our HandBrake results in the previous section, it appears that encoders are among the most impacted productivity applications from the patch.
The multi-threaded LuxMark OpenCL C++ renderer, though an older benchmark, reveals a significant performance impact from the patch, with the unpatched Ryzen 9 3950X being 5% faster than the patched configuration while the Ryzen 5 3600 is 10% slower after patching. Again, this highlights that different types of code and Zen 2 processors can respond differently to the patch.
We also see impacts in other workloads, too, like a 16% performance reduction for both patched configurations in the C-Ray ray-tracing renderer, and a 9% delta between patched and unpatched configs in the NAMD simulation code workload.
We also recorded a ~7% delta with both chips in the CPU-Z single- and multi-thread benchmarks, but this widely-cited benchmark isn't a great proxy for any given workload. Instead, it is a purely synthetic benchmark that helps quantify relative performance. While this benchmark doesn't directly correlate to any real-world workload, it shows that the patch can also impact synthetic benchmark software.
Summary
AMD's Zen 2 helped solidify the company's historic comeback against Intel, but as we've seen time and again with chips from both AMD and Intel, researchers continue to poke and prod at chip architectures for any sign of weakness long after their prime. Both chipmakers have fallen prey to both crafty researchers and nefarious actors as the cat-and-mouse chip security game continues, and the resulting patches have led to a drumbeat of performance rollbacks over the years that can essentially remove generational performance advances.
Luckily, the Zenbleed patch doesn't impact gaming, and the majority of applications also don't experience a huge performance impact. However, a few workloads are impacted — we saw significant performance loss in encoders that employ AVX instructions, with a range of a 5% to 15% performance reduction. We also saw an impact in other types of software, like a 16% reduction in performance in the C-Ray ray-tracing renderer, a 9% hit in the NAMD simulation code workload, and a 7% reduction in CPU-Z.
On the whole, aside from the impact on encoders and a select few other applications, the performance impacts of the Zenbleed software patch are minor compared to the big performance rollbacks we saw with other vulnerabilities like Meltdown and Spectre. Still, no one likes to give back any performance on products they've already purchased, and the software patch does result in less performance in certain types of work.
Yes, you could choose to leave your system unpatched if you don't feel like you're vulnerable, but that would mean forgoing any future BIOS updates for your chip. Additionally, given the wide availability of POC code, it is likely that attackers will eventually incorporate these attacks into malware at some point.
It certainly doesn't help that the patches aren't coming until later in the year. And even then, it takes time for the ODMs to make those BIOS versions available to customers, leading to an extended amount of time that chips can be vulnerable — and that's assuming motherboard vendors will issue a patch for every board that supports a given chip architecture.
Zenbleed has a limited impact, but the full patches for desktop PCs for the recently disclosed AMD Inception and Intel GDS / Downfall vulnerabilities are also still inbound, and those mitigations will also have a performance impact. We're also putting those patches to the test, too. Stay tuned.

Paul Alcorn is the Editor-in-Chief for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
Makaveli "The Zenbleed flaw (CVE-2023-20593) spans the entire Zen 2 product stack, including AMD's EPYC data center processors and Ryzen 3000/4000/5000 CPUs"Reply
Just to make it more clear this is Zen 2 5000 chips not Zen 3 -
Roland Of Gilead Reply
Yup! Only the U series 5000, which aren't Zen 3. Good spot!Makaveli said:"The Zenbleed flaw (CVE-2023-20593) spans the entire Zen 2 product stack, including AMD's EPYC data center processors and Ryzen 3000/4000/5000 CPUs"
Just to make it more clear this is Zen 2 5000 chips not Zen 3 -
ezst036 Where can I go to see what vulnerabilities are fixed in hardware? - so they do not require these costly software fixes anymore? Is there any website out there which lists these vulnerabilities, perhaps in a table format?Reply -
drajitsh Thanks for covering security so well. This along with guides is the main thing keeping me checking the site on a daily basis.Reply -
dmitche3 My question is, since I really don't care to make this patch on my AMD systerm, how can I avoid having this patched? Will it be a Microsoft behidn the scenes or a MOBO mfg update?Reply -
ghedepere This smells kind of fake, or blown out of proportion like intel and AMD both had fake vulnerabities spun up after spectre and meltdown to affect share price and manipulate the stock market.Reply
This is even more suspect when people urge you to update, even if you are not affected.
This updating for the sake of updating, not reading release notes and just accepting things blindly has to stop, it's paving the way for some very cheap planned software obsolescence through performance reductions and functionality removals.
Curious to see the answers to others' questions about where to find info in a table for all vulnerabilities that are being patches through microcode and their impact, as well as how to tell the OS is going to push for a microcode update or not. -
JakeTheMate Reply
Microsoft patched this on last "Patch Tuesday", so anybody with an up to date Win10/11 system should no longer vulnerable. Don't know if that helps with avoiding the patch.dmitche3 said:My question is, since I really don't care to make this patch on my AMD systerm, how can I avoid having this patched? Will it be a Microsoft behidn the scenes or a MOBO mfg update?