Tested: Windows 11 Pro's On-By-Default Encryption Slows SSDs Up to 45%
BitLocker software encryption slows performance. Here's how to fix it.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
There are few things more frustrating than paying for high-speed PC components and then leaving performance on the table because software slows your system down. Unfortunately, a default setting in Windows 11 Pro, having its software BitLocker encryption enabled, could rob as much as 45 percent of the speed from your SSD as it forces your processor to encrypt and decrypt everything. According to our tests, random writes and reads — which affect the overall performance of your PC — get hurt the most, but even large sequential transfers are affected.
While many SSDs come with hardware-based encryption, which does all the processing directly on the drive, Windows 11 Pro force-enables the software version of BitLocker during installation, without providing a clear way to opt out. (You can circumvent this with tools like Rufus, if you want, though that's obviously not an official solution as it allows users to bypass the Microsoft's intent.) If you bought a prebuilt PC with Windows 11 Pro, there's a good chance software BitLocker is enabled on it right now. Windows 11 Home doesn't support BitLocker so you won't have encryption enabled there.
To find out just how much software BitLocker impacts performance, we ran a series of tests with three scenarios: unencrypted (no BitLocker), software BitLocker (the Windows 11 Pro default), and with hardware BitLocker (OPAL) enabled. While the software encryption increased latency and decreased transfer rates, hardware encryption and no encryption at all were basically tied. If you have software BitLocker enabled, you may want to change your settings (more on that below).
How to Tell Whether You Have BitLocker Enabled
To see if you have a problem, you need to know if you have software BitLocker enabled in the first place. If you are on Windows 11 Home, it's not enabled in most cases (though it seems some laptops might still turn it on). If you're on Windows 10 Pro, it's probably not enabled (but it doesn't hurt to check).
For that matter, even if you're running Windows 11 Pro, if you're using a PC you assembled yourself, or one from a smaller boutique builder, there's still a good chance BitLocker is turned off. That's because there are specific requirements for Microsoft's policy of auto-enablement of BitLocker to happen, and most non-OEM PCs don't tend to tick every box.
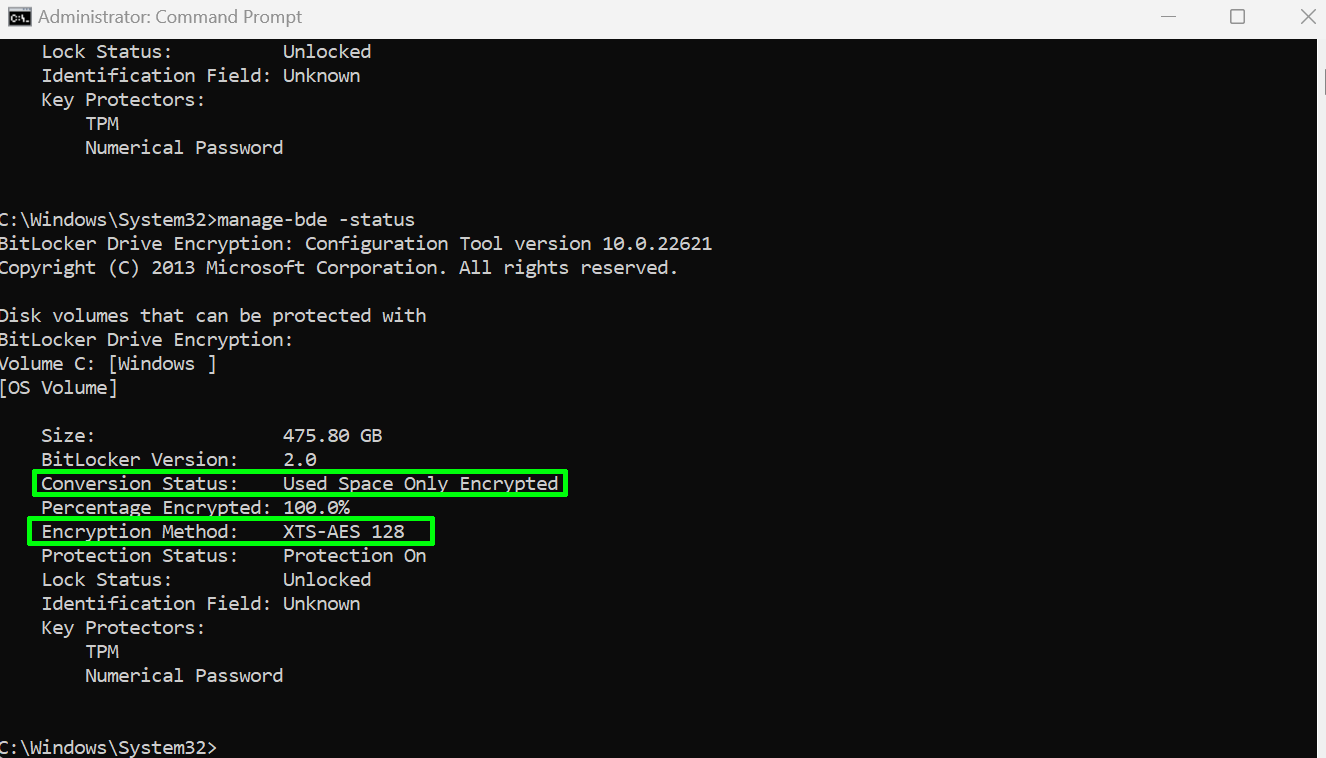
To check your drive's encryption status, launch an elevated command prompt (run CMD as an admin) and then enter the command: manage-bde -status. You'll see a screen like the one below.
So here you need to look at two fields: Conversion Status and Encryption Method. Conversion Status will tell you if you have encryption enabled at all and Encryption Method will tell you if it's hardware or software encryption. If the method says "XTS-AES" like in the shot above, it's software BitLocker. If it says "Hardware Encryption," you have hardware encryption.
If you get a message saying your drive(s) are "Fully Decrypted" and "Protection Off," you're not currently using BitLocker. For home PCs, that's probably fine, though on laptops that could be more easily lost/stolen, you may want to reconsider. There are good reasons for having BitLocker enabled.
Testing Windows 11 BitLocker Performance
We tested with a Samsung 990 Pro 4TB, using the latest release of Windows 11 Pro (22H2, all patched with the latest updates). Our testbed had a Core i9-12900K with 32GB of DDR4 memory, our standard storage test PC.
After installing Windows 11, we also ran a sustained write workload using Iometer to condition the drive, thus assuring repeatable results. The SSD is 4TB, so we ran 1MiB writes for four hours straight to ensure all the flash had been touched. This resulted in about 30TB worth of written data for each of the test scenarios.
In retrospect, while the results we'll show do indicate a potentially significant loss of performance — random IO was hit particularly hard; sequential IO, not so much — part of that is likely due to our high-end desktop PC. The Core i9-12900K is no slouch when it comes to performance, and while it's no longer the fastest chip around, it's fast enough that software-based BitLocker encryption wasn't as massive of a problem as you would see with lesser CPUs that don't have as much processing power. Regardless, the impact is surprising even with our high-end processor, and we suspect laptops, which is what a lot of businesses running Windows 11 Pro will be using, will be hit much harder.
We ran a slightly limited suite of tests than what we use for our SSD reviews, and because the testing required a clean Windows 11 Pro install, results aren't 100% directly comparable to our normal SSD benchmarks. We also can't speak to precisely how BitLocker will impact other SSDs, with or without hardware OPAL encryption support. But let's check the numbers that we do have for the Samsung 990 Pro.
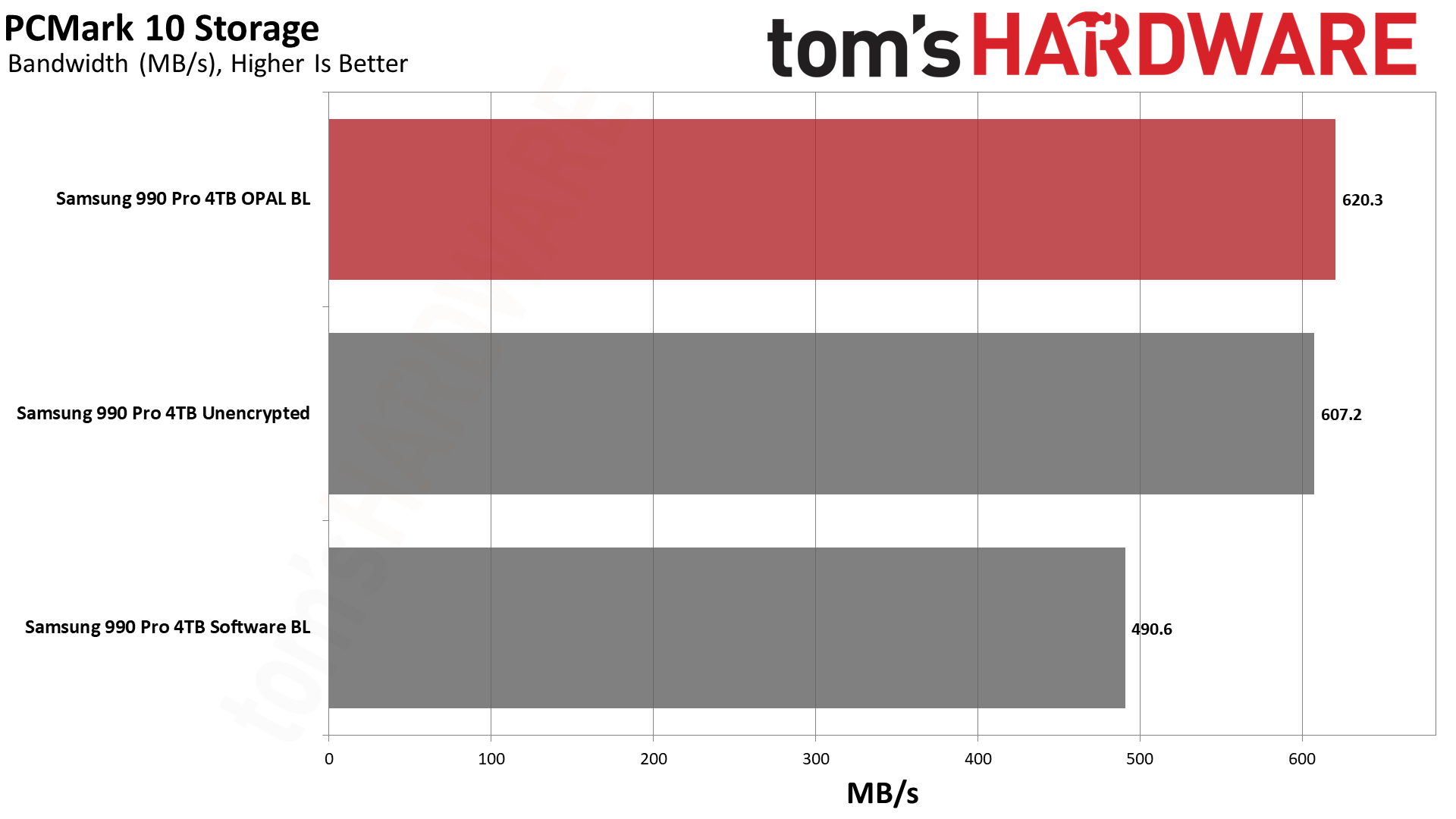
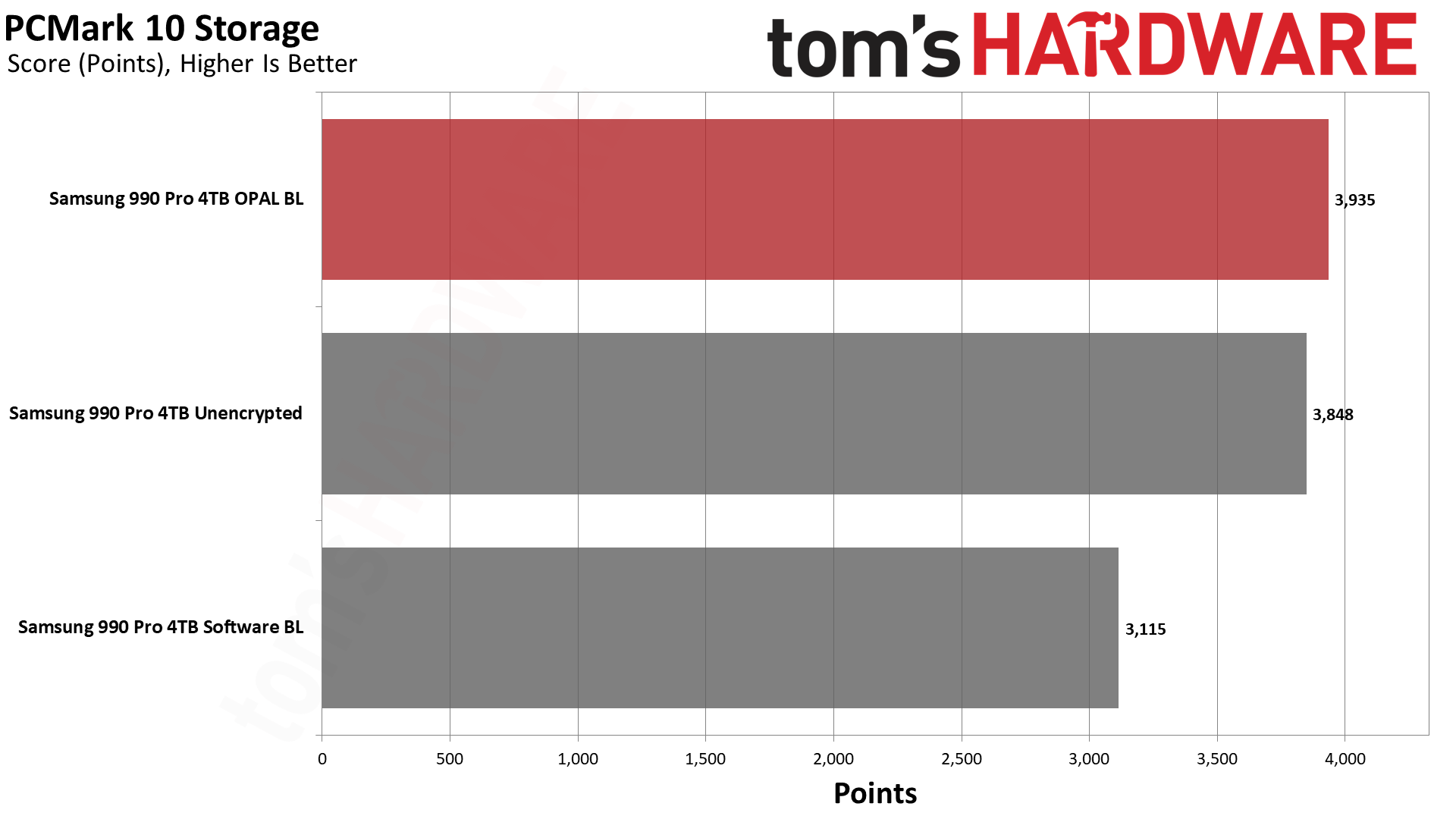
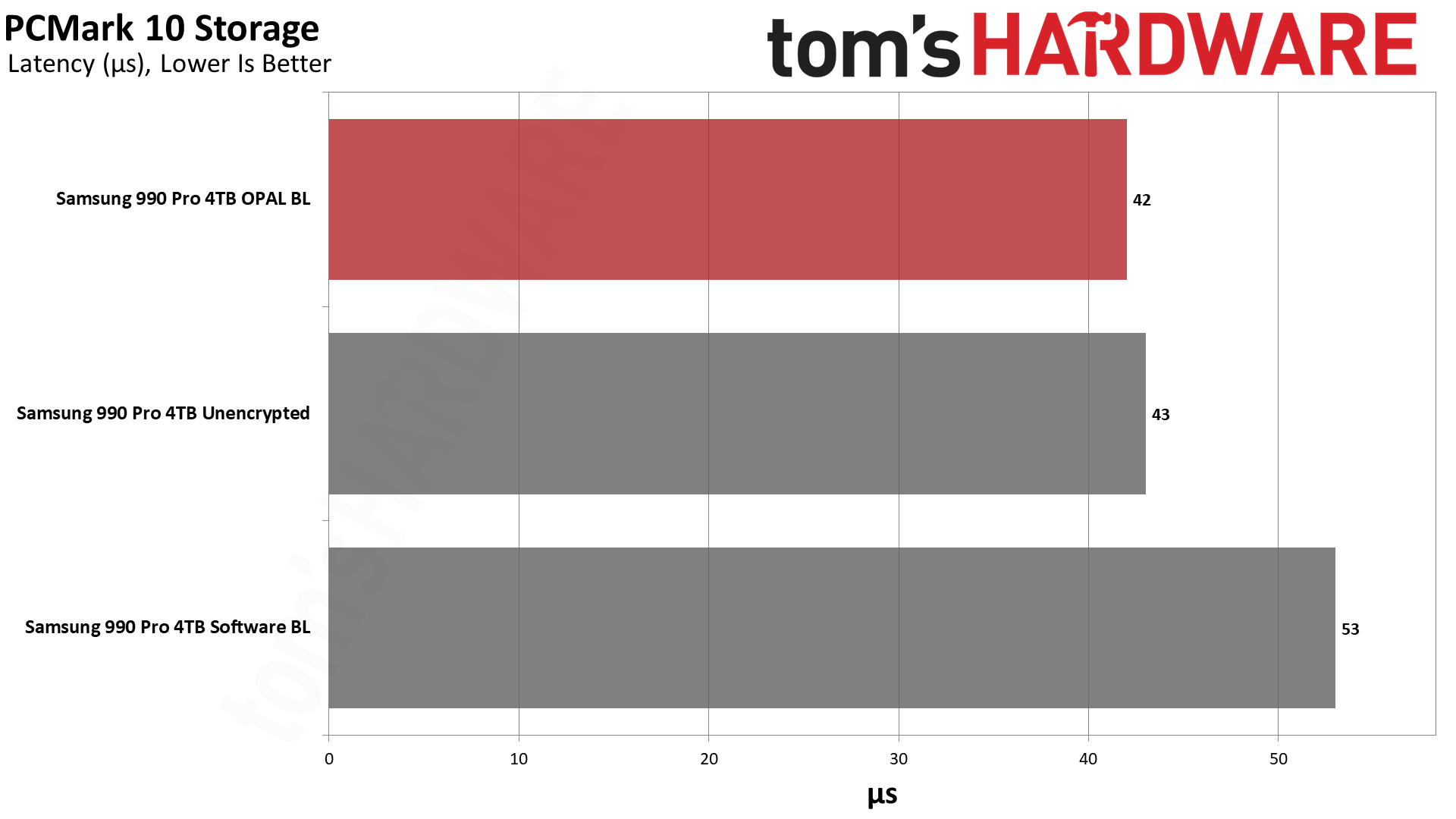
PCMark 10's Storage Benchmark uses trace testing of popular applications and tasks to measure storage performance. It gives a good overview of the impact you can expect and a taste of things to come.
Curiously, the hardware-based encryption (OPAL) performed slightly higher than even unencrypted (no BitLocker) mode. We repeated the tests multiple times, and the results were reasonably consistent. With OPAL hardware encryption, we saw scores of around 620 MB/s (±10 MB/s); no encryption was nearly as fast at 607 MB/s (again, ±10 MB/s).
However, using software-based BitLocker resulted in 490 MB/s (±10 MB/s). That's a potential 21% drop in performance, and while the drive still felt reasonably fast, people don't buy top-of-the-line hardware only to give up 20% of the potential performance. Put another way, the Samsung 990 Pro dropped from class-leading performance in PCMark 10 down to merely adequate — with software BitLocker, it's about as fast as the Netac NV7000.
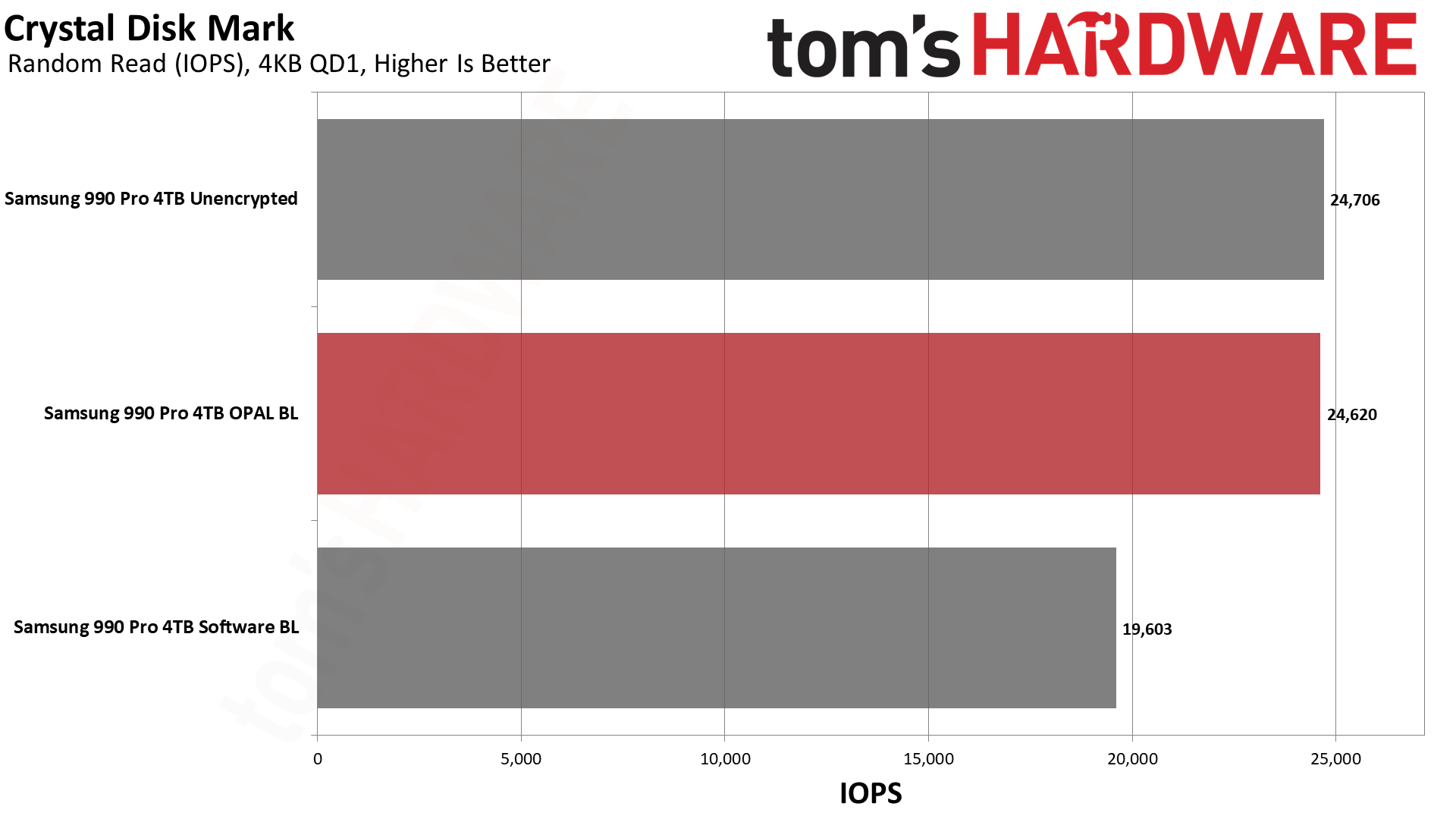
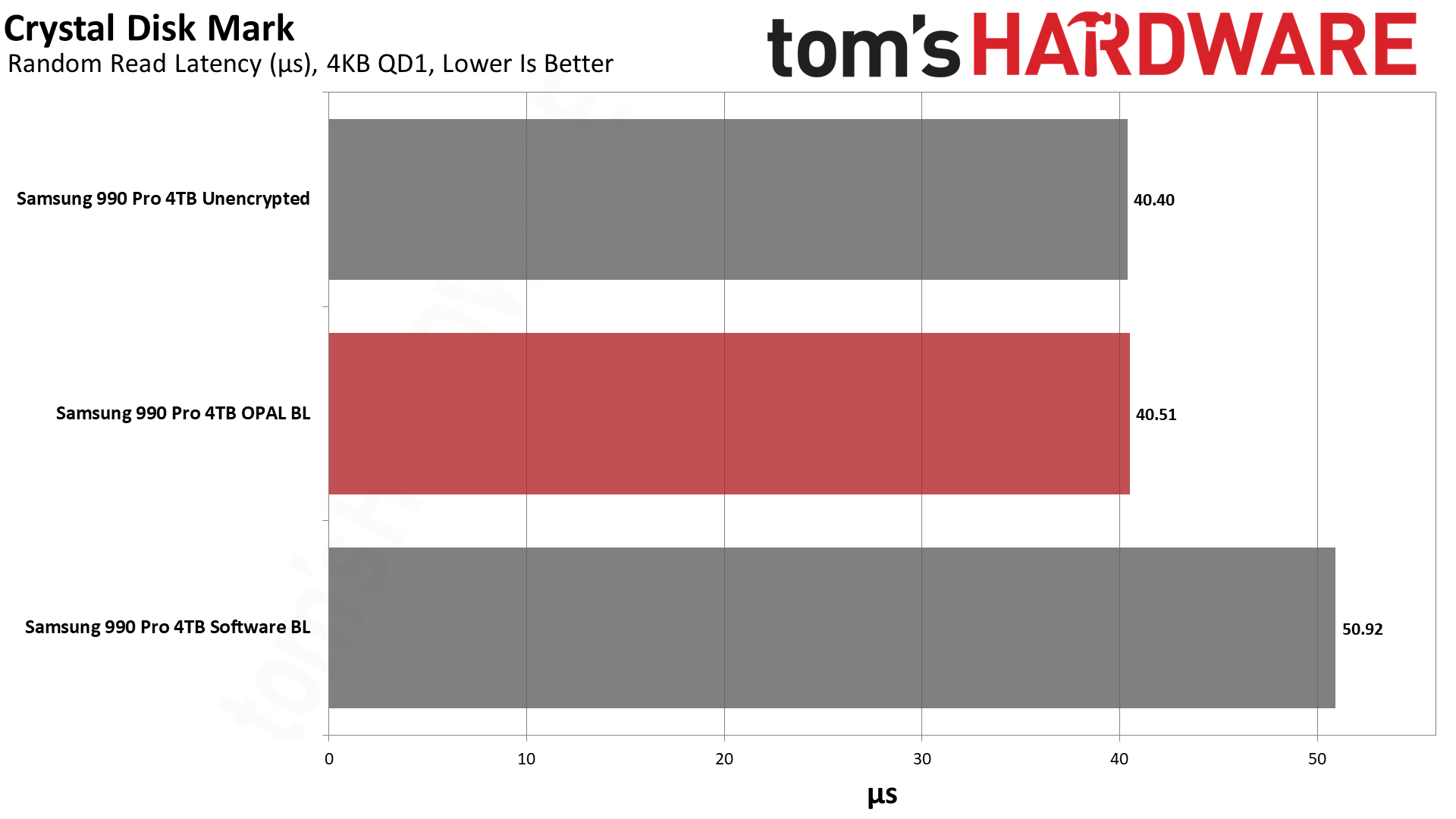
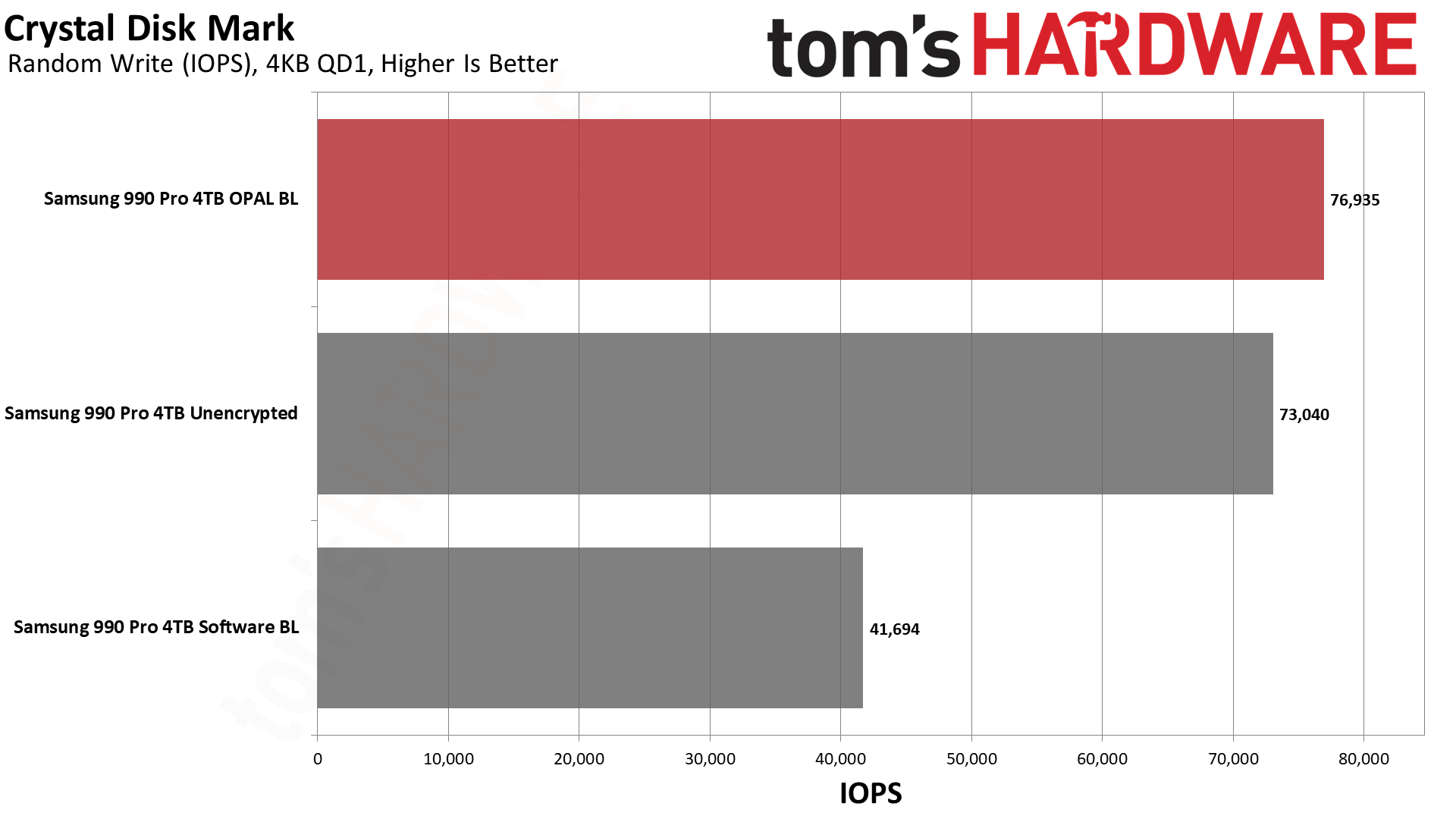
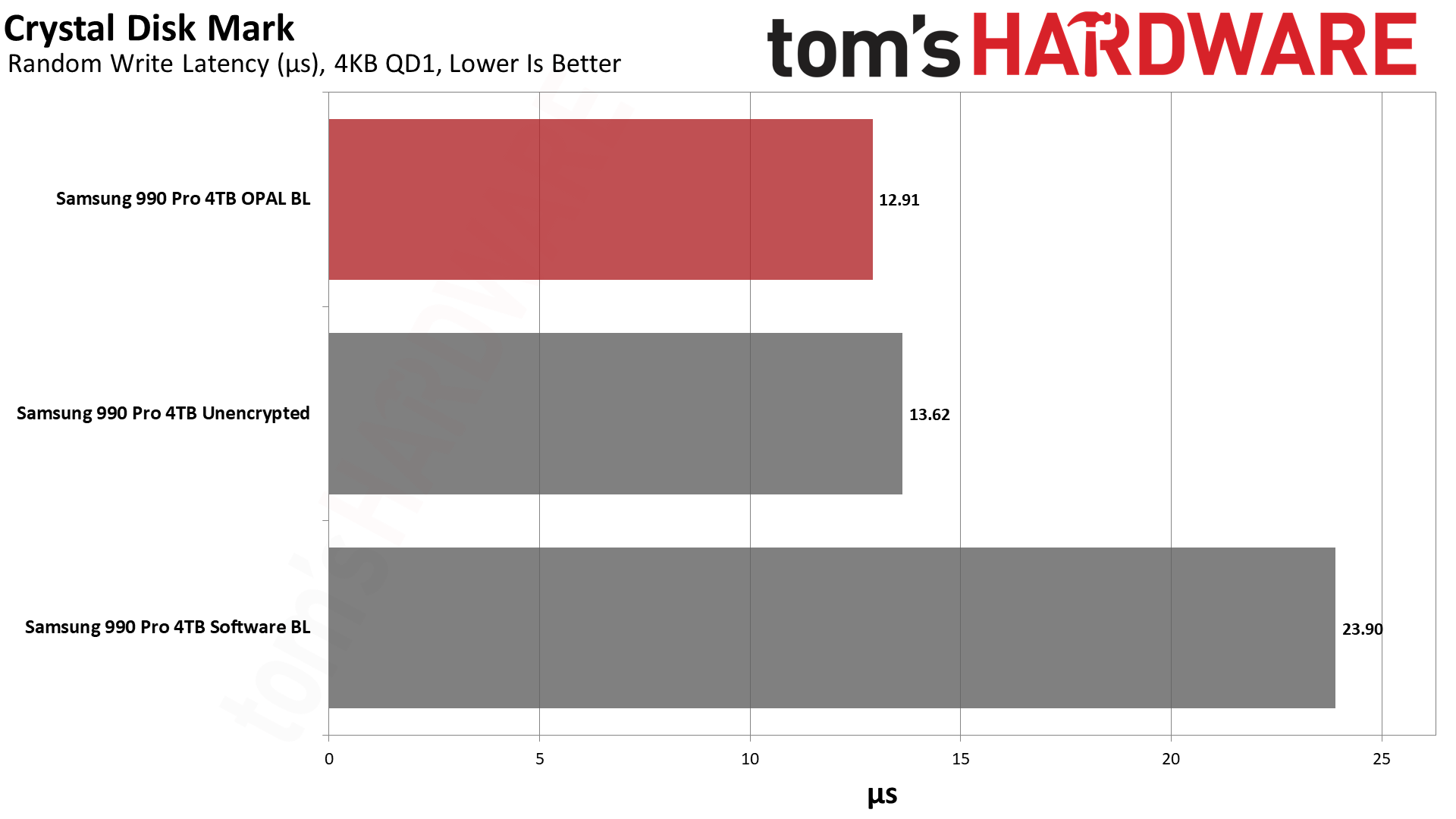
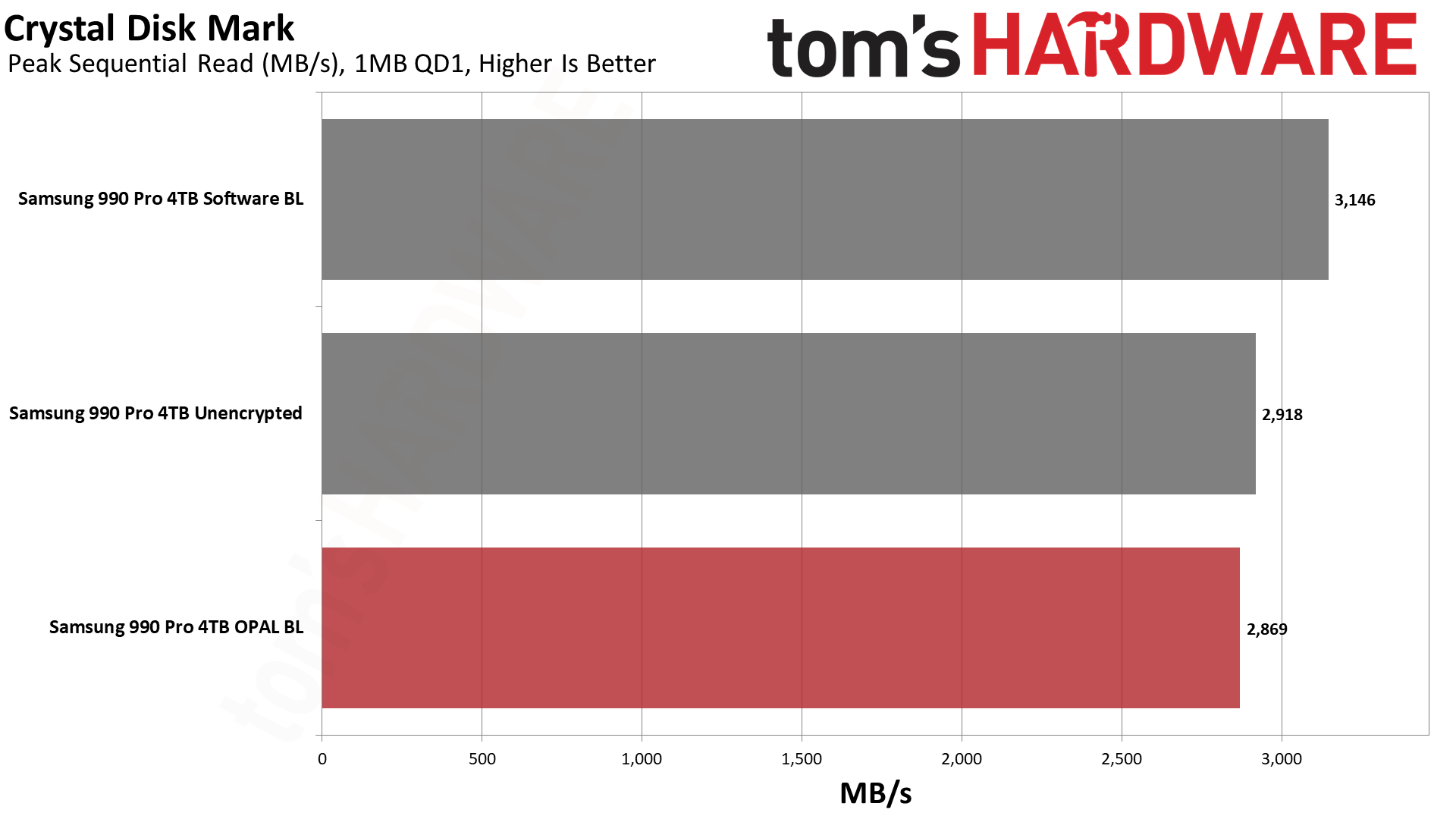
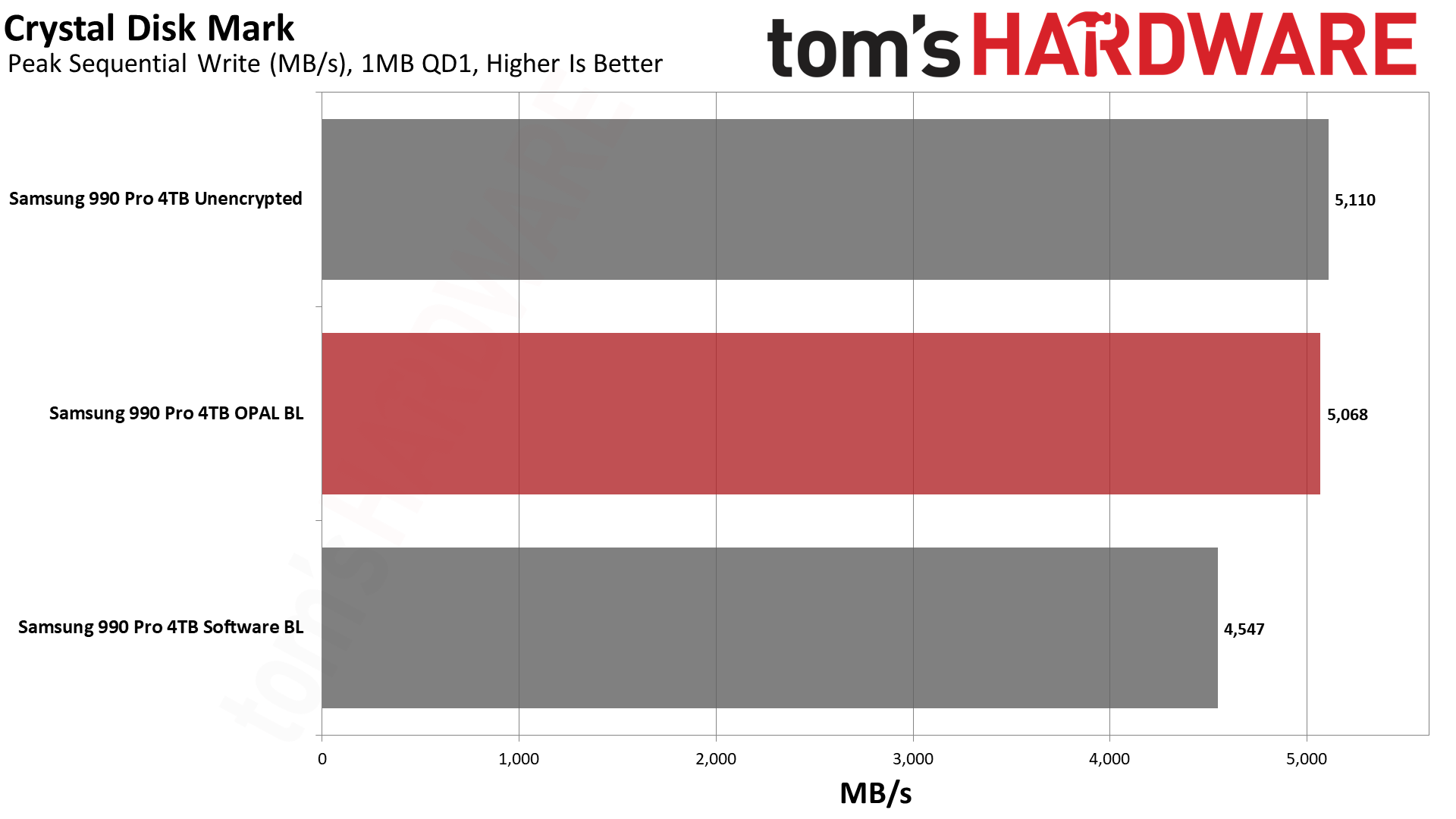
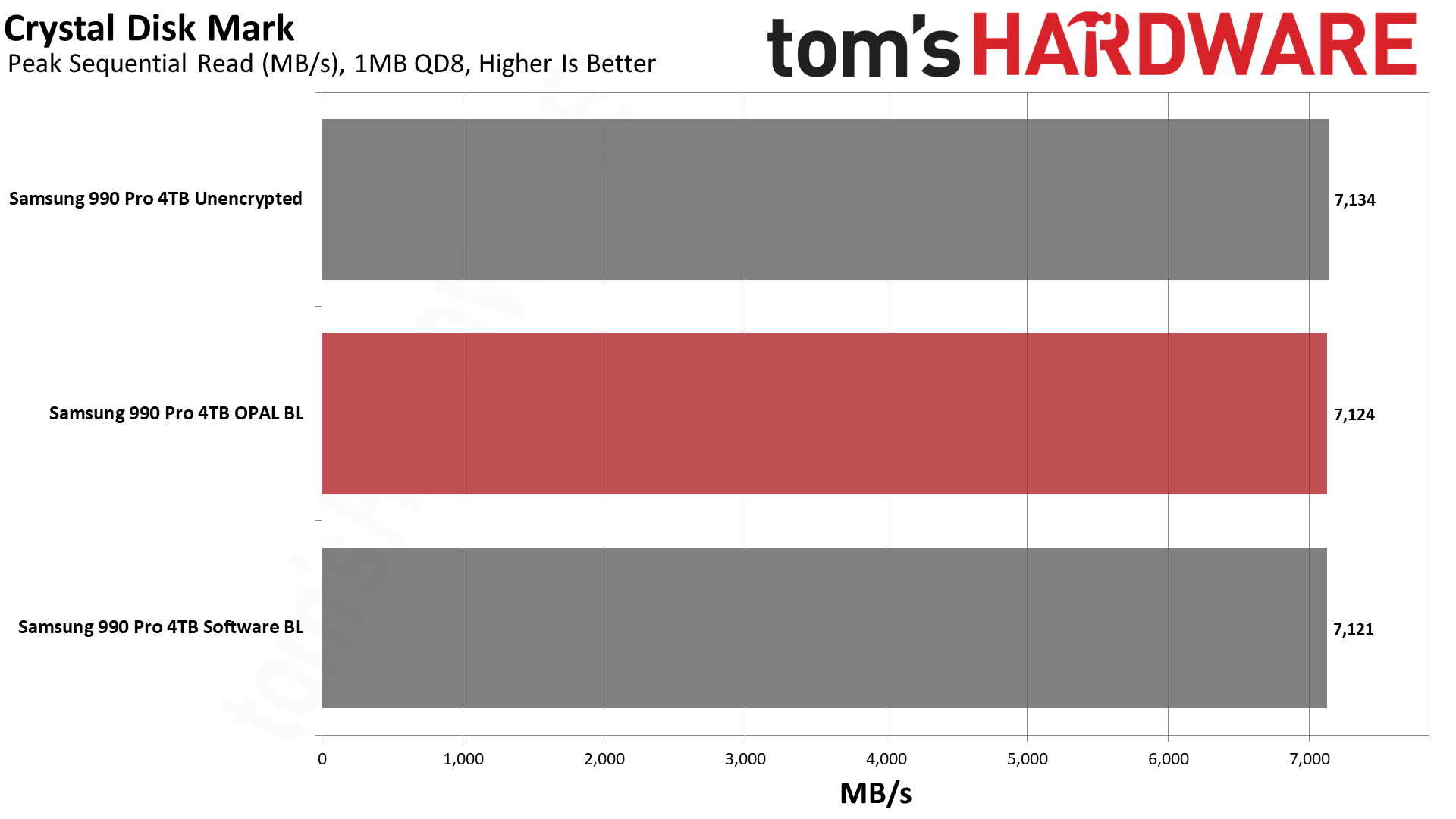
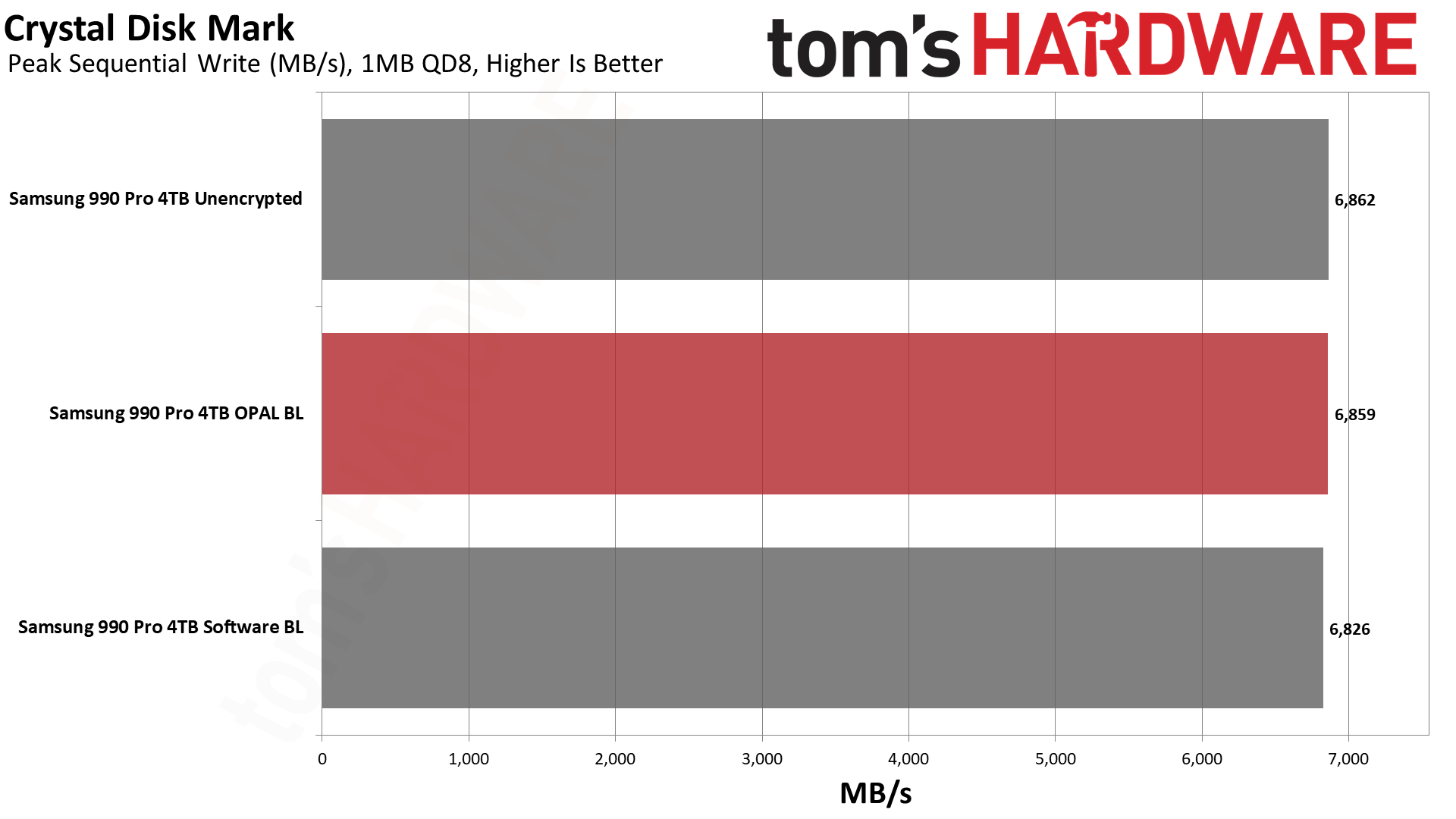
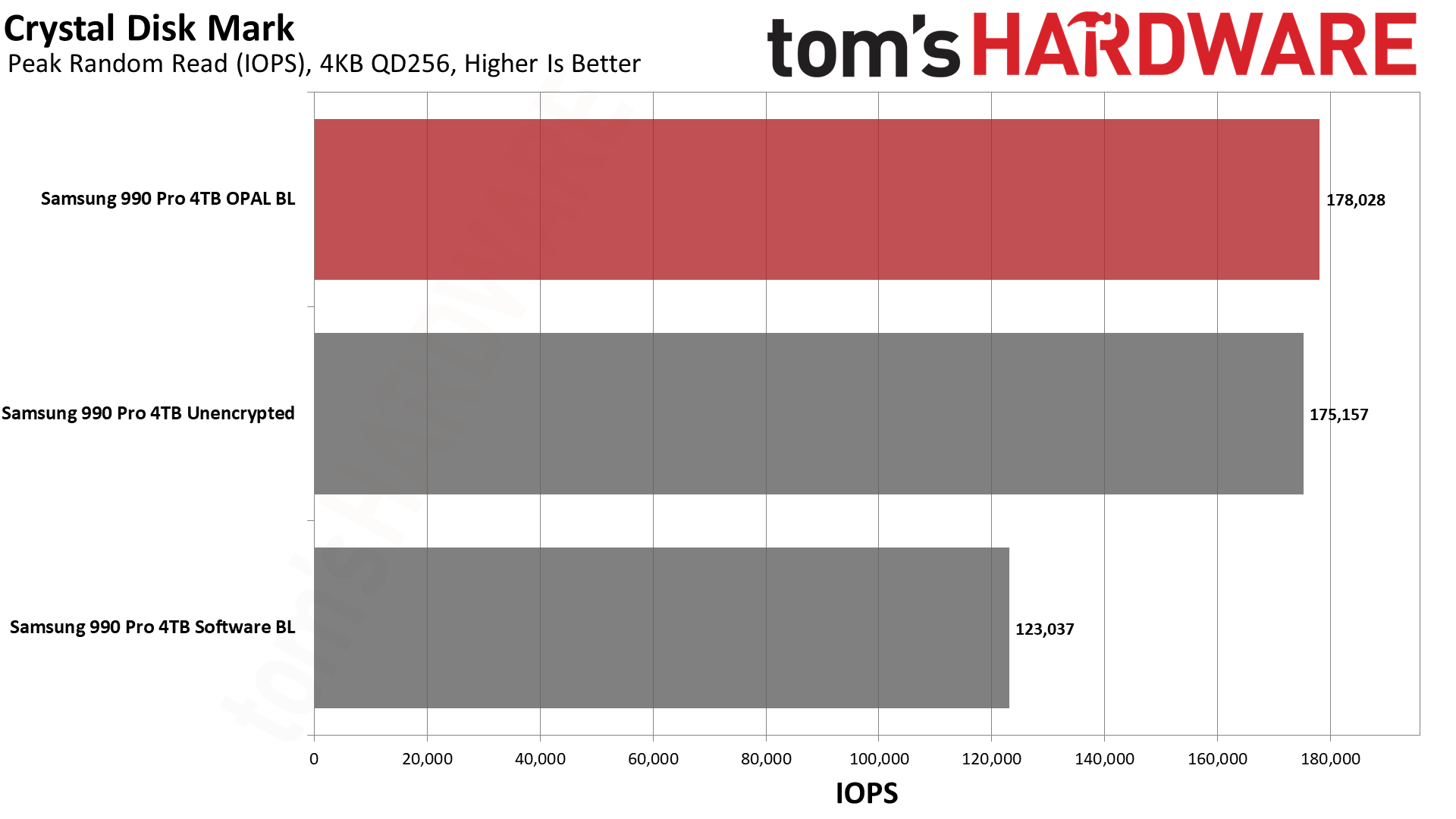
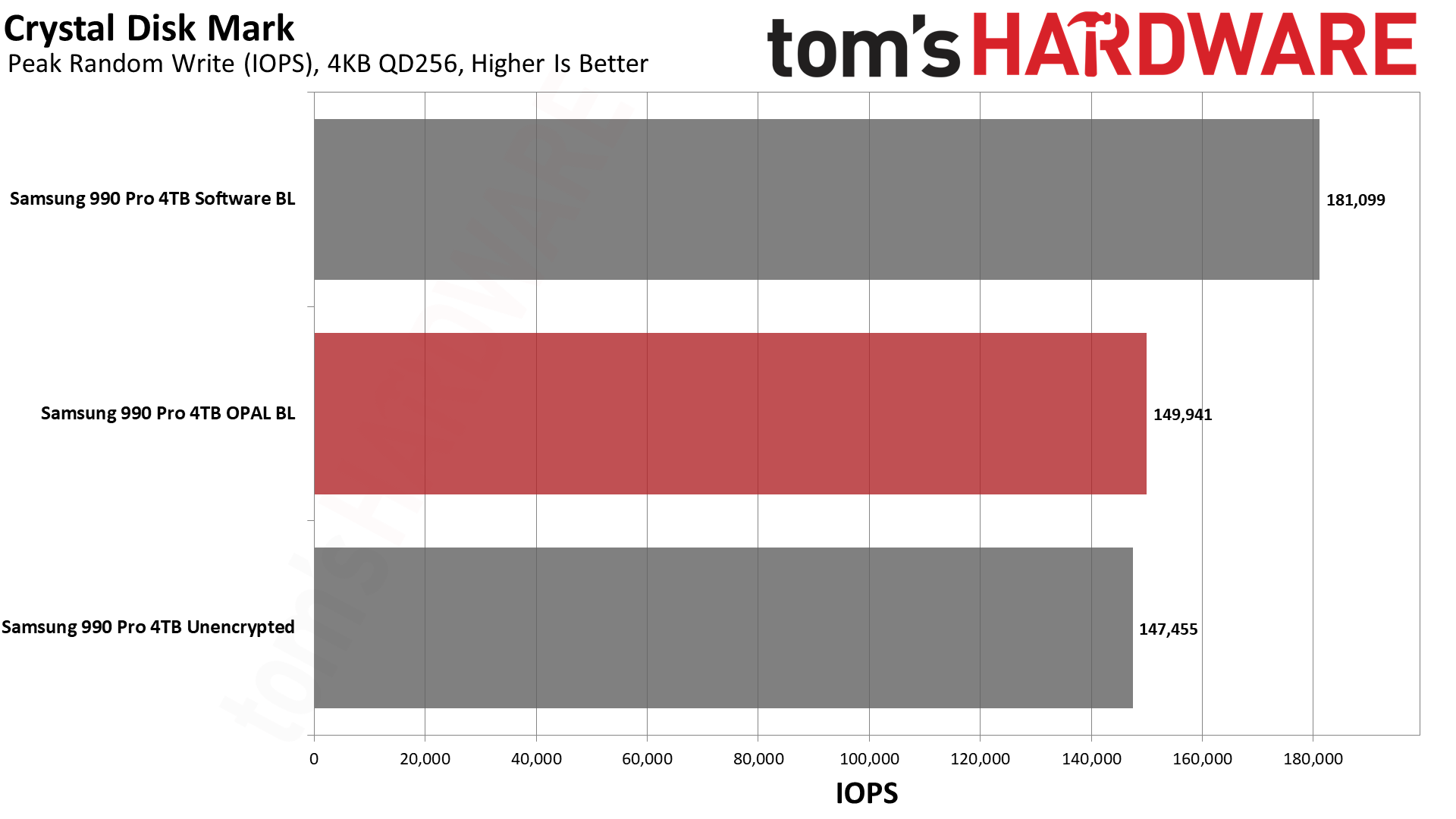
Next, we have CrystalDiskMark 8, a synthetic storage performance test. While we have results for higher queue depths, note that the QD1 numbers are far more meaningful in the real world, as this is the most common type of file access in typical operating system environments... and that's where software BitLocker impacted performance the most.
Random read IOPS dropped by 20% again compared to the hardware BitLocker and unencrypted results. Latency for reads also jumped from just over 40 us (microseconds) to nearly 51 us, 25% higher. Lower latency delivers snappier performance in day-to-day use, and it's the primary reason the industry at large has moved from slow rotating hard drives to faster SSDs. Given that this extra layer of latency, albeit at varying degrees, will also be added to slower types of SSDs, like QLC or low-tier drives, this could have a much bigger real-world impact in some systems.
Curiously, write IOPS at QD1 again were slightly higher with OPAL than without — perhaps some caching or command batching is happening in the Samsung controller. But the critical aspect is that software BitLocker dropped random write performance by 45% compared to hardware BitLocker.
That's massive. QD1 random writes were basically half as fast with BitLocker enabled. There are plenty of things you might do that don't hit storage that hard, but again, you don't want to give up a huge portion of your potential SSD performance if you don't have to.
The other results aren't necessarily as bad, and in one case at least (QD256 random 4K writes), software BitLocker consistently generated superior results. Windows 11 disk caching might be a factor there, but QD256 is basically fantasy land for storage workloads (remember, low queue depths are the most common), so we don't put too much weight on it. Plus, random reads are more important than random writes, and the loss in read performance was still 30%.
Sequential read and write speeds were a lot closer, and QD1 reads were actually the fastest with software BitLocker. QD1 writes meanwhile had software BitLocker trailing by 20% again. In general, CrystalDiskMark confirms the PCMark 10 results that show some significant performance degradation.
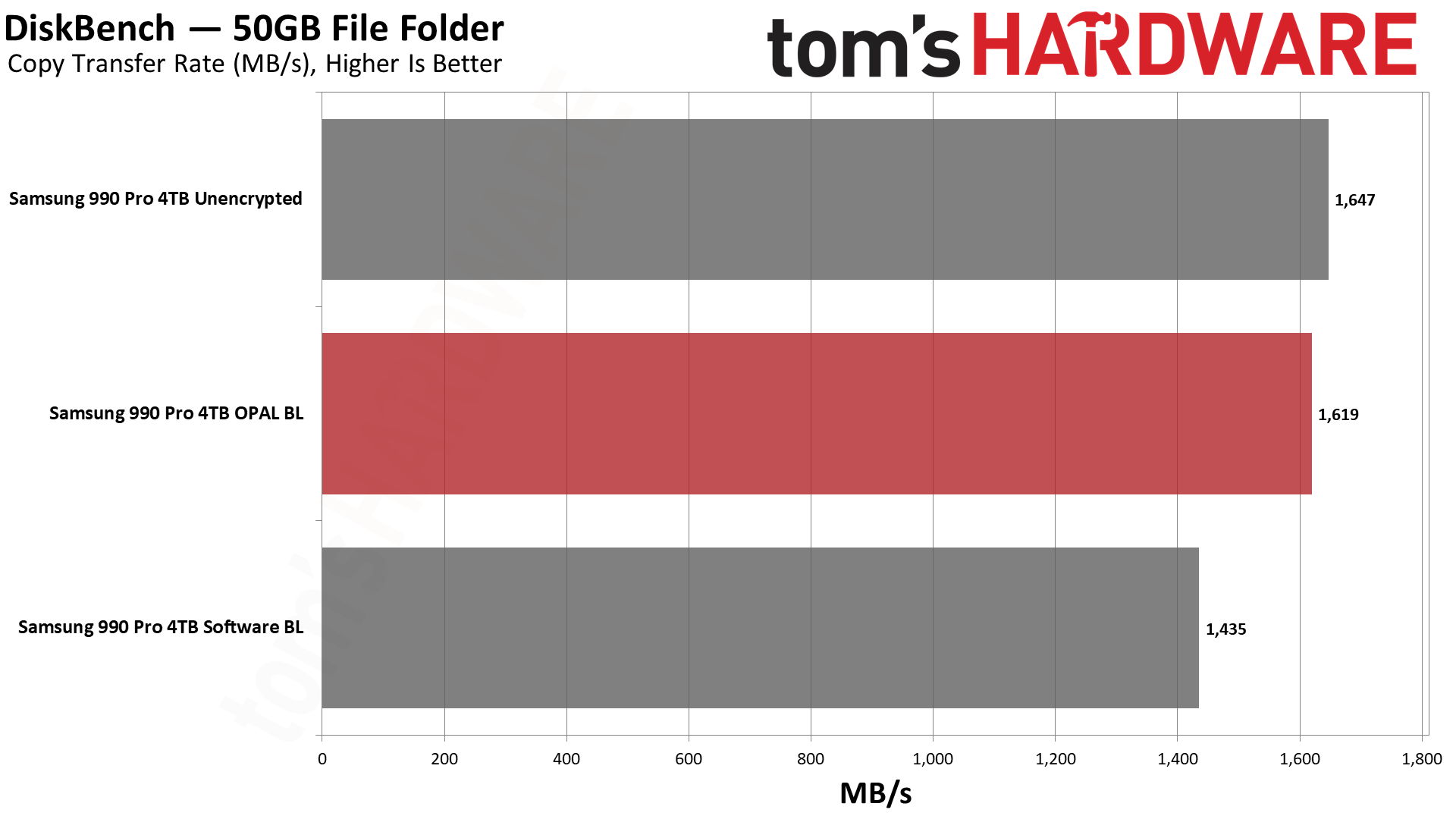
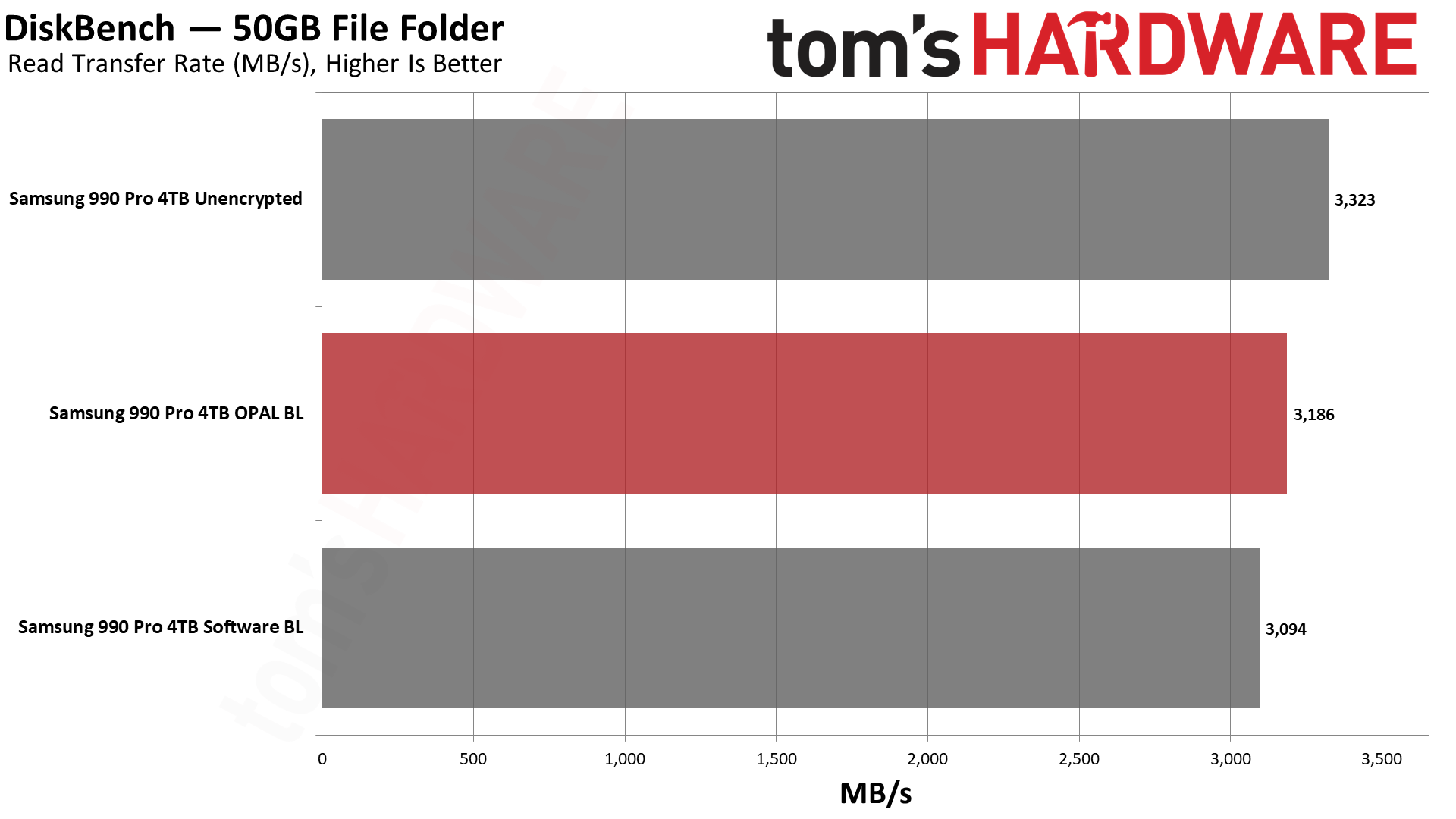
Turning to a real-world workload where we copy or read 50GB of data using DiskBench, read and copy performance for the unencrypted drive was best, followed by the hardware encryption. In this case, we do need to note more variability between runs than we'd like, so we report the median of five runs. The read speeds were more consistent, but copy speeds still showed a wider spread.
Part of that is due to the nature of DiskBench's testing options. You can do write tests of entire folders, and copy tests using entire folders, but the read test will only use a single file. Our copy test consists of 50GiB of data (53,738,970,410 bytes, occupying 53,798,830,080 bytes of disk space), with 31,241 files and 3,607 folders. About half of the data represents large files (100MiB or larger), while the other half consists mostly of thousands of smaller images. Of the two tests, we'd put far more emphasis on the copy results.
Overall, the software BitLocker showed an 11% drop in performance for file copies compared to hardware BitLocker encryption. Read speeds (for a single large 50GB file) were only 3% slower, though we'd expect significantly larger margins if we were reading lots of small files.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
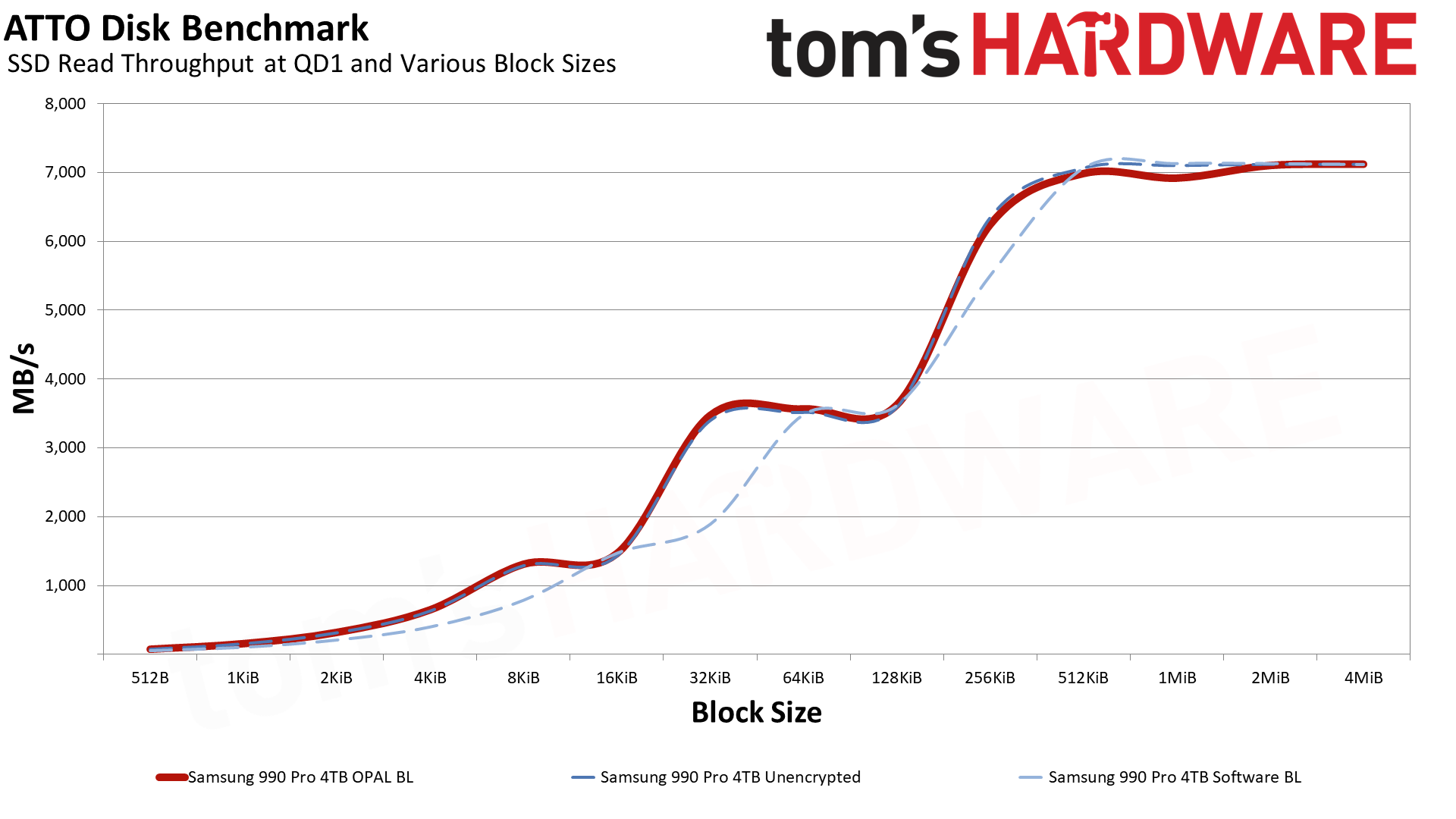
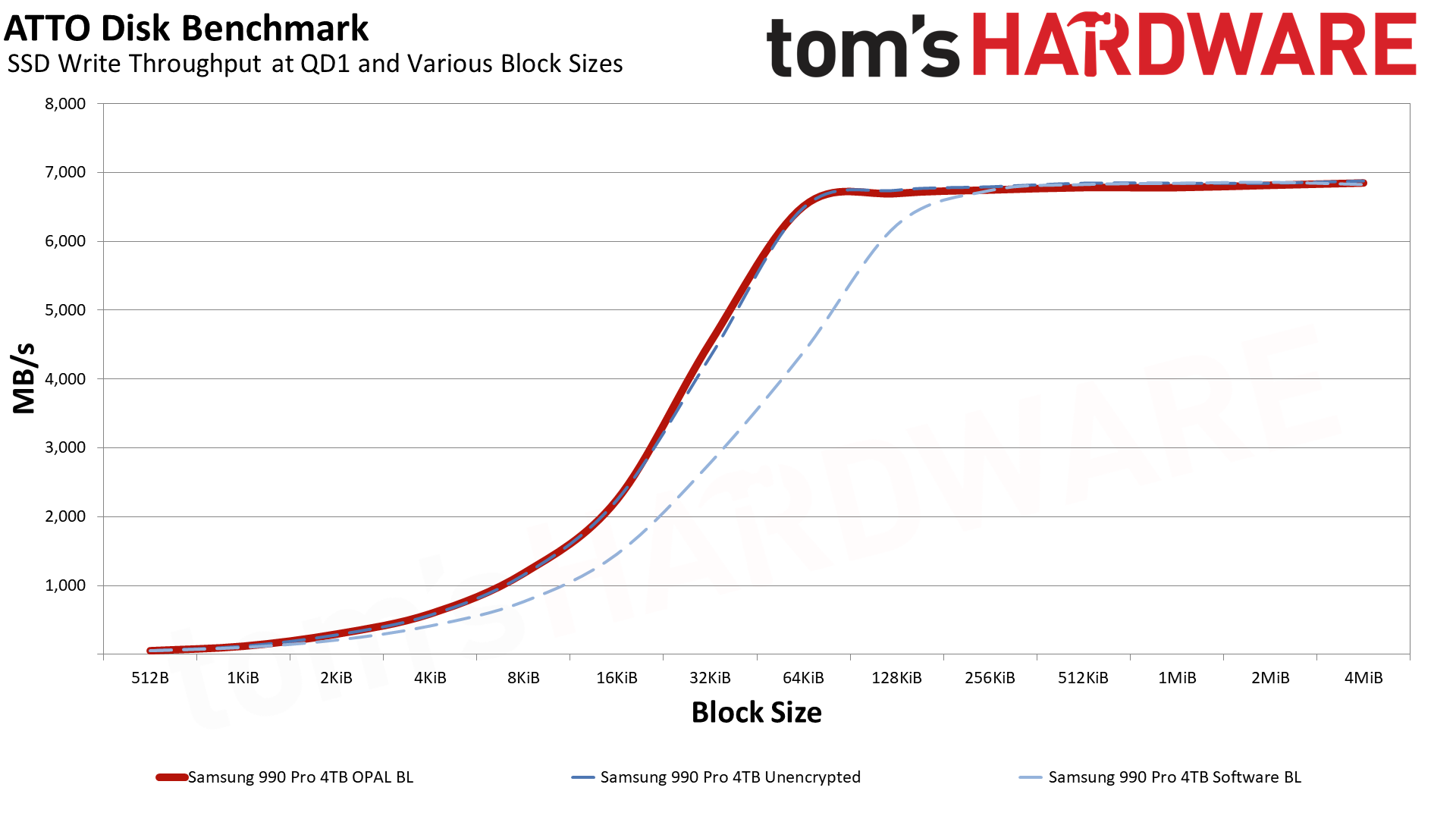
Wrapping up our performance results, we have ATTO read and write speeds at varying block sizes. While peak throughput with larger block sizes isn't affected too much, smaller sizes show the software BitLocker consistently behind the hardware BitLocker and unencrypted lines. There's a curious "bump" with the 990 Pro that we've noted before on the read speeds, but write performance shows a smoother line with the software BitLocker trailing up until the 256KiB block size.
Software BitLocker Can Seriously Hurt SSD Performance
If you're not a heavy storage user, perhaps a lot of the above seems like it's not a big deal. The problem is Microsoft has forced degraded performance on a lot of Windows 11 Pro users, and the added latency will have an impact on system responsiveness. If you're using Windows 11 Pro on a company-issued laptop, there's a good chance it's underperforming thanks to that decision.
For PC enthusiasts who want maximum performance, it's potentially even worse. Not all SSDs have hardware encryption support, but even if you have it, unless you jump through extra hoops to get it turned on before installing Windows 11, you're going to end up with degraded storage performance. We strongly suspect anyone going out to purchase a drive like the Samsung 990 Pro — or even the previous generation Samsung 980 Pro — didn't buy the drive with the intent to give up 20% or more of the maximum performance. But that's exactly what has happened, if your PC ticks the right boxes to get BitLocker turned on, or if you want to turn it on manually for security reasons.
Microsoft's decision to enable software-based BitLocker as a default option even if hardware-based encryption is available is a bit complicated. The short summary is that there have been issues in the past (starting in 2019) where it was possible to recover the encryption keys on some hardware-encrypted storage solutions. While those flaws were fixed, it's possible future flaws will be discovered. The crux of the issue appears to be that Microsoft is not fully in control of the code and implementation of hardware encryption solutions for BitLocker. With software BitLocker, Microsoft is in charge of the keys and security, and it apparently prefers to keep things that way.
But when did Microsoft start enabling BitLocker by default? That's a bit trickier. It actually started back in 2016, with Windows 8.1 Pro and Windows Server 2012 R2. The catch is that it was only enabled if the system supported TPM, Secure Boot, and Modern Standby/HSTI — and these all had to be enabled, which wasn't usually the case until Windows 11 enforced the TPM requirement. Also, if you do a local account rather than a Microsoft account (which also means if you set up a PC without an active network connection), BitLocker is left off. So having BitLocker software encryption automatically enabled really only became a regular occurrence with Windows 11 in the last couple of years.
Even now, in our testing, there are many motherboards (all enthusiast class) that won't automatically turn on BitLocker. But Microsoft's stance is clear on this: It thinks BitLocker should be on by default for Windows Pro users. Don't be surprised if future updates start enabling the feature on more PCs.
Do You Need SSD Encryption?
Having your storage drive encrypted provides great protection against theft so it's particularly helpful for laptops. If a thief gets ahold of your computer and can't otherwise boot into Windows, they can still remove your SSD, connect it to another computer and attempt to read the data on it.
If the drive is encrypted and the thief doesn't have the encryption key, they can't read the drive. If it's not encrypted, then they can use any SSD enclosure to turn it into an external storage drive and gain full access to your files. If you are working with a desktop PC in your home and you feel really confident that nobody's going to have unauthorized physical access to the computer, you might want to do without encryption.
Disabling BitLocker Encryption
If you don't feel like you need encryption, the easiest thing to do is just to turn BitLocker off. Switching to hardware encryption, which we detail below, requires a complete reinstallation of Windows and all of your applications, a huge hassle.
To turn off BitLocker, all you need to do is launch an elevated command prompt (launch CMD as administrator) and enter manage-bde -off C: — replace the C: with a different drive letter if your encrypted drive is not C. (You can also do this, for individual drives, via the BitLocker control panel: Control Panel -> System and Security -> BitLocker Drive Encryption — or type "manage BitLocker" in the Start Menu search box.)
Switching to Hardware BitLocker Encryption
The real bad news is that if you already have a Windows 11 Pro install running, with or without software BitLocker enabled, you're out of luck. If you have an SSD that supports hardware encryption and you want to use it, you'll need to start fresh with a new OS install — no imaging or other shenanigans will fix what Microsoft broke!
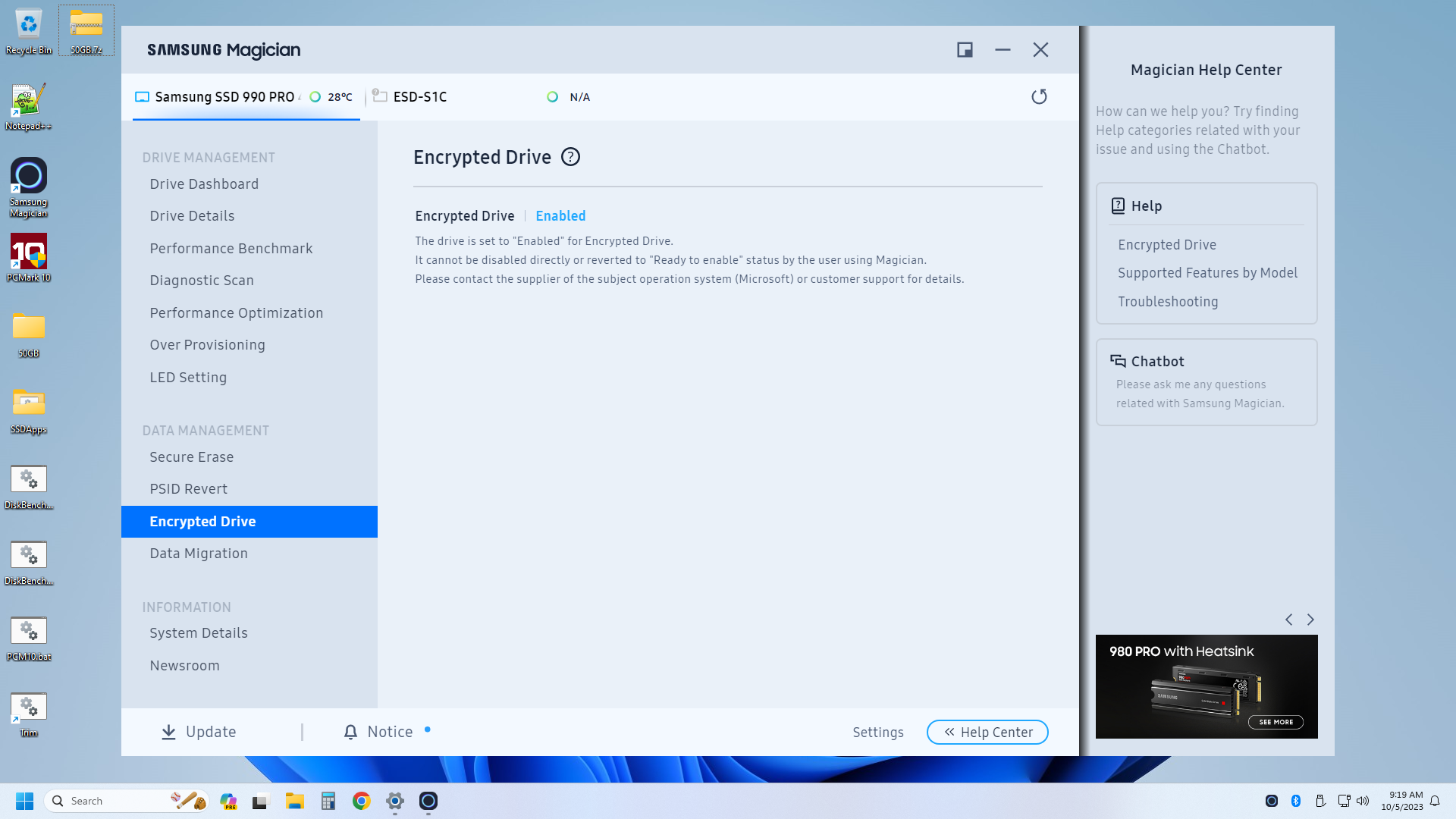
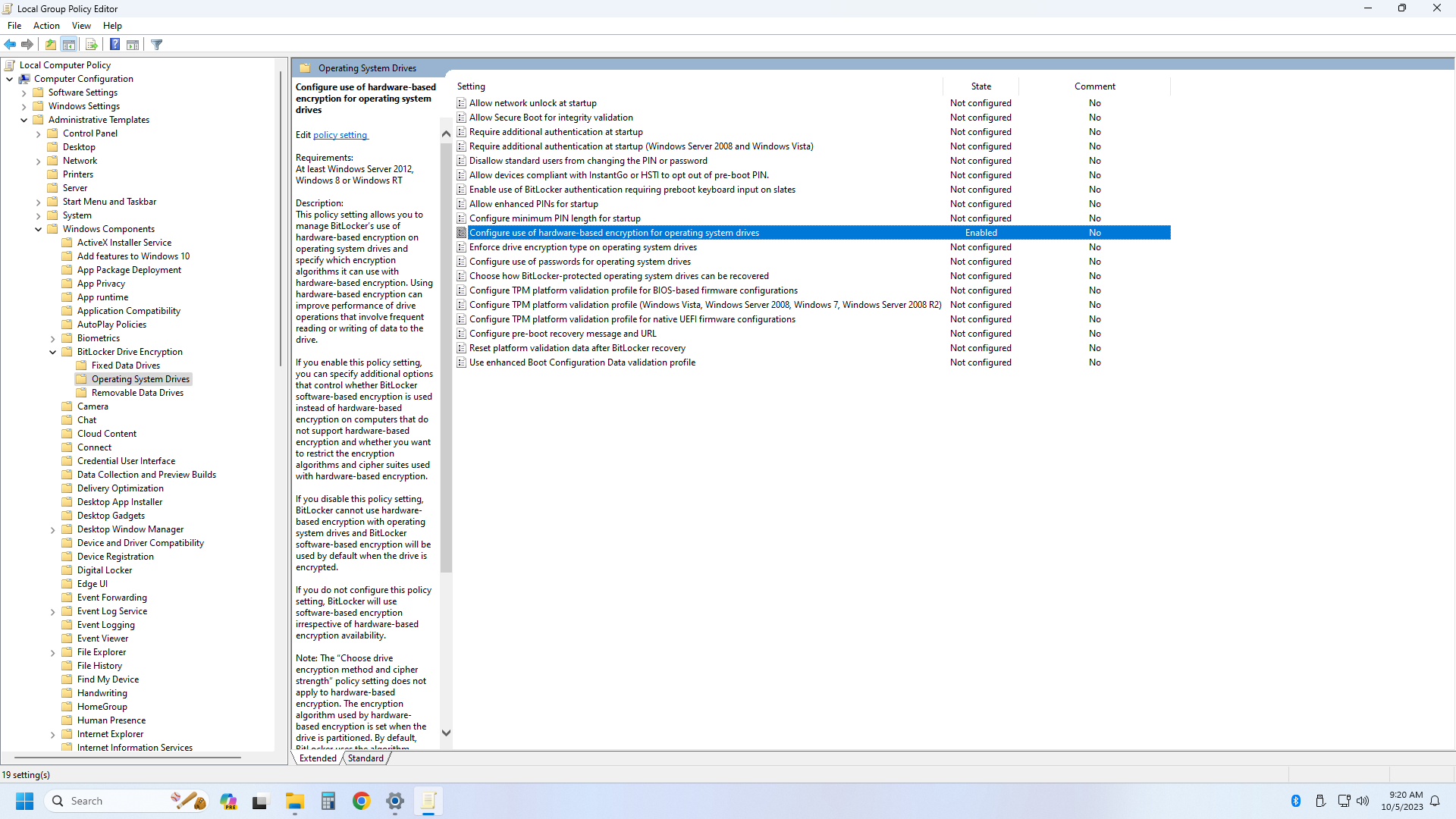
First, you'll need to boot Windows 2 Go (or install the SDD as a secondary drive in a PC — it can't be the OS drive), install Samsung Magician (or a similar utility for other SSDs), and enable encryption on the drive. Then secure erase the drive, generate a new Block ID, create a Windows 11 installation device without BitLocker being enabled (using Rufus USB), and then install Windows 11 Pro. Once installed, open the Group Policy Editor and turn on hardware encryption support for BitLocker.
Reboot, and now if you enable BitLocker, everything should work out, and you'll have hardware encryption from your SSD. The easiest way to check is to open an elevated command prompt (type CMD in the Start Menu, right-click, and select Run as administrator) and then type: manage-bde -status
If everything goes properly, you'll get a screenshot like the one below indicating that hardware encryption is enabled. If it says anything else, like XTS-AES 128... well, you're still in software BitLocker mode. Time to try again with a fresh install.
Here are the full instructions to get hardware BitLocker working that we used, which work for Samsung 980 Pro and 990 Pro (and possibly other Samsung) SSDs. We also used the referenced PDF at the bottom of that page for some additional details. Getting hardware encryption working on non-Samsung drives should follow a similar process, just with a few changes specific to the drive manufacturer's software.
Bottom Line

We reached out to several OEMs, and Dell, HP, and Lenovo told us they ship systems with Windows 11 Pro with software-based encryption unless a user orders an SSD that has hardware-based encryption available. It's not clear if they always enable hardware encryption on every SSD that supports the feature, but if you don't pay extra for such a drive, you'll likely end up with reduced storage performance. We haven't received a response from several other OEMs yet, but we suspect most have similar policies in place.
For those who install their own Windows 11 Pro operating system from scratch on any system, the performance-sapping software-based encryption is the default policy, but many motherboards still don't appear to conform to Microsoft's requirements. Local accounts, lack of network during installation, improperly configured Secure Boot, or other BIOS options or hardware, can all result in BitLocker being off, at least in our own testing. Even if you don't have BitLocker enabled, if you later want to turn it on, you'll be force to use software encryption unless you took steps prior to the installation of Windows 11 Pro.
The simple solution to regain storage performance for anyone currently using software BitLocker is to turn it off. Depending on how full your drive is, it can take a while to unencrypt everything, and of course, that means your files are no longer protected from prying eyes.
If you have a drive with hardware BitLocker support, and you want to use that, you'll need to first copy off all the files you want to keep to a backup drive, then go through the necessary steps to enable hardware BitLocker support on a new Windows 11 installation before copying all your files back — and reinstalling any games or other applications. It's tedious for sure, but if you don't want reduced storage performance caused by the use of software encryption, that's the only real option. Whether an SSD with hardware encryption is actually as secure as BitLocker software encryption is a different matter, and only time will say for sure which drives may have issues.

Jarred Walton is a senior editor at Tom's Hardware focusing on everything GPU. He has been working as a tech journalist since 2004, writing for AnandTech, Maximum PC, and PC Gamer. From the first S3 Virge '3D decelerators' to today's GPUs, Jarred keeps up with all the latest graphics trends and is the one to ask about game performance.
-
macsquirrel_jedi I'm using two partition on SSD drive. "System" (Software Bitlocker) and "Data" (no BitLocker). User folders (pictures, video, music etc.) are set to use "Data" partition as default. So there is a way how to get performence back even when Software Bitlocker is enabled. Because partitions can be managed separately.Reply -
Makaveli In a company provided machine as touched on in the article it will be done on purpose.Reply
Security policy > Performance. -
Missing name I want to add that Microsoft no longer recommends the use of OPAL compliant SSDs in a recent support ticket I had opened with them.Reply
Here are some of the key CVEs related to vulnerabilities in Opal compliant self-encrypting SSDs:
- CVE-2018-12037 - A weakness was reported in the way that Opal self-encrypting SSDs from multiple vendors handle locking. An attacker with physical access could bypass the encryption by issuing ATA commands during boot.
- CVE-2018-12038 - A weakness was reported in the way that Opal self-encrypting SSDs from Crucial and Samsung handle unlocking. An attacker with physical access could bypass the encryption by modifying the SSD firmware.
- CVE-2020-12812 - Multiple Opal self-encrypting SSDs were found to be vulnerable to authentication bypass, allowing an attacker with physical access to bypass the encryption. SSDs from Crucial, Samsung, and others were affected.
- CVE-2021-3277 - Self-encrypting SSDs from multiple vendors were found to be vulnerable to improper cryptographic verification. This could allow an attacker to bypass the encryption.
- CVE-2022-39009 - A vulnerability was reported in the encryption implementation in Opal self-encrypting SSDs from multiple vendors. An attacker with physical access could bypass the encryption and access user data.
The vulnerabilities allow attackers with physical access to bypass the encryption on vulnerable Opal compliant SSDs from various manufacturers. Organizations using these drives should check with their vendor for firmware updates to address the vulnerabilities. Proper physical security controls can also help mitigate against exploitation.
:) -
Dr3ams I have Windows 11 Pro installed on a 2.5" SSD. I have nothing to test any performance deficiency with, so for me the drive works as advertised. ;)Reply -
ttjg I built my PC earlier this year with Windows 11 Pro and 3 2Tb SSD's (a mix of pcie 3 & 4's), and just verified that BitLocker is OFF for all 3 of them. I didn't jump through any hoops when I I did the installations to avoid a BitLocker default that I can remember.Reply -
JarredWaltonGPU Reply
There are many ways, mentioned in the article, that you can avoid the default behavior — intentionally or unintentionally! No network connection during installation means you use a local account, which means no BitLocker. Or using a local account even if you have a network connection. Or using Rufus to create an installation medium with BitLocker turned off. Or using Rufus to create an installation medium that creates a local account for you. I generally test new hardware, so guess what that means: no network connection until after I've created an account.emike09 said:I have four W11 Pro computers at home, none of them are defaulting to Bitlocker encryption. Two modern laptops, and two modern desktops. The title is very misleading, as this is not a default behavior. One system is running W11 Insider Dev build, one running W11 Insider Release Preview build, and the others running standard production builds. So this isn't even a feature that the bleeding edge Dev Insider build is forcing on. All NVMe SSDs. Desktops have HDD storage as well. No Bitlocker.
On top of that, I manage thousands of laptops and desktops at work, half of which are on W11 Pro. Until recently, we didn't have bitlocker enforced through group policies. W11 does not force Bitlocker and is not on by default.
It's obvious the title and article are flexing a bit of clickbait.
I'd be curious to see what happens if you do a PC reset of an existing non-BitLocker system, though. Because that should give you a network connection for the initial setup and so it would likely return to default behavior.
Microsoft's documentation says that BitLocker being turned on for Windows Pro has been the default since Windows 8.1. However, you need TPM, secure boot, and modern standby all supported and enabled. The TPM aspect often meant pre-Win11 systems (laptops) didn't have BitLocker enabled. It was switched to being default software encryption in 2019. But if you miss any of the specific requirements, it may not be enabled — and I wouldn't expect preview builds to always stick to Microsoft's own official guidelines.
Beyond the BitLocker being on or off default behavior, however, there's also the being in default software mode. There's no way to turn on hardware encryption that I know of without doing a clean install and jumping through some hoops along the way. -
HaninTH Bitlocker software sucks! But... OPAL hardware also blows (for known and unknown flaws)... so... are we back to no encryption and reasonable physical security practices as the SOP?Reply -
baboma This response has been re-edited:Reply
I'm using Rufus to clean-install Win11 on all my laptops, which as said will allow disabling the default encryption (among other things like HW requirements and MS acct), so this never comes into play.
This piece goes into considerable technical detail, but IMO it misses the point from the reader's perspective. It's abundantly clear that software-based encryption will substantially sap performance, without all the benchmarking. It's also abundantly clear that for typical home users, said encryption is a Bad Deal(tm), as the perf loss grossly outweighs the risk. That takes two sentences to say.
For the home or small biz user, using drive encryption is almost always inadvisable, whether SW or HW-based. Drive encryption primarily protects the device from physical theft, which is the least likely threat that home users face. It definitely doesn't protect against the more prevalent threats like phishing or ransomware. Coupled with the ~40% perf loss (for SW enc), or the convoluted method above for HW enc, drive encryption should be ignored entirely. Of course, larger enterprises would face different threats, but they have IT people to handle these matters.
Note to Jarred: Windows To Go only exists in Enterprise and Education versions of Windows. It's very much an "unofficial" solution for DIYers. If we were talking about "unofficial" methods, I'm sure there are easier ways to enable HW encryption by default by editing an existing ISO.
From the reader's view, he would want to know three things: 1) what is the simplest way to avoid the default encryption; 2) if encryption is already installed, what is the simplest way to remove it; and 3) what are SSDs with HW-based encryption, if the user decides to opt for that feature (for whatever reason).
#1: the simplest answer is to use Rufus, to clean install Win11 Pro (Home isn't relevant for this discussion). It doesn't involve technical know-how, and is a simple checkmark during the Rufus imaging-to-USB process.
#2: As said in the piece, disable drive encryption with "manage-bde off " in an elevated command prompt (Terminal Admin in Win11 parlance).
The last question #3 (which SSDs have HW-based encryption) is never answered. -
AloofBrit "If you don't feel like you need encryption, the easiest thing to do is just to turn BitLocker off"Reply
but soon after
"The real bad news is that if you already have a Windows 11 Pro install running with software BitLocker encryption, you're out of luck. You need to start fresh with a new OS install"
So which is it?
I haven't played much with 11, but (other than long decryption time if it wasn't a solid state drive) turning off BitLocker was doable in 10 -
jtrox02 Don't modern CPU's handle AES instructions? It is my understanding that disk encryption is hardware accelerated by the CPU in Linux. Why isn't it in Windows?Reply