Microsoft Promises Sandboxed Apps With the Security of VMs
Microsoft announced this week a new security feature to isolate applications in order to prevent malicious code from harming users’ systems. The feature, Windows Sandbox, will be available only on the Windows Pro and Enterprise editions.
Windows Sandbox will enable users to create lightweight virtual environments to isolate applications at will, somewhat similar to how users have been using third-party applications such as Sandboxie, Shade Sandbox and ReHIPS. However, Windows Sandbox goes a little deeper, creating an virtual machine that uses a “hybrid” approach in the sense that the sandboxed environment doesn’t share the exact same files the host also uses, but dynamically generates “clean” versions of those files. In other words, this is almost like a normal VM, where the VM uses an entirely different OS image than the one on the host, except the Windows Sandbox uses unmodified files of the operating system to save on resources.
With Windows Sandbox, users will also be able to take advantage of fresh Windows installations to test particular applications without any worry that this particular application could harm your computer. After closing the Windows Sandbox, all of the software’s state and files are permanently deleted.
Windows Sandbox seems to take inspiration from Qubes OS, an Linux-based platform that allows multiple operating systems to exist on top of it as virtual machines in order to isolate various user tasks. Qubes OS also allows users to create temporary virtual machines that are completely wiped when they are closed.
Malicious application specifically designed to bypass the Windows Sandbox will likely appear in the future, but the feature significantly raises the bar for most malware out there.
How to Use Windows Sandbox
According to Microsoft, its Sandbox feature has the following features:
- Everything required for this feature ships with Windows 10 Pro and Enterprise.
- Every time Windows Sandbox runs, it’s as clean as a brand-new installation of Windows
- Nothing persists on the device; everything is discarded after you close the application
- Uses hardware-based virtualization for kernel isolation, which relies on Microsoft’s hypervisor to run a separate kernel, which isolates Windows Sandbox from the host.
- Uses integrated kernel scheduler, smart memory management and virtual GPU.
Microsoft recommends an AMD64 system with virtualization capabilities enabled in BIOS, Windows 10 Pro or Enterprise build 18305 or later, an SSD, 8GB of RAM and a quad-core processor. All virtual machines tend to work better when they are assigned faster drives, more RAM, and a higher number of CPU cores, so the more you can improve on these, the better the Windows Sandbox experience should be.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
After the virtualization features are enabled in BIOS, you also have to enable the Windows Sandbox feature in “Windows Features.” Then all you need to do is start the Windows Sandbox application, allow the elevated privileges and copy the executable you wanted to try inside the Sandbox. Installers can also be used inside the Sandbox.
Windows Sandbox Under the Hood
Microsoft said that it used its server technology (such as Hyper-V and containers) to create the Windows Sandbox feature but streamlined it to ensure it requires fewer resources and uses less power in order to be suitable for mainstream laptops.
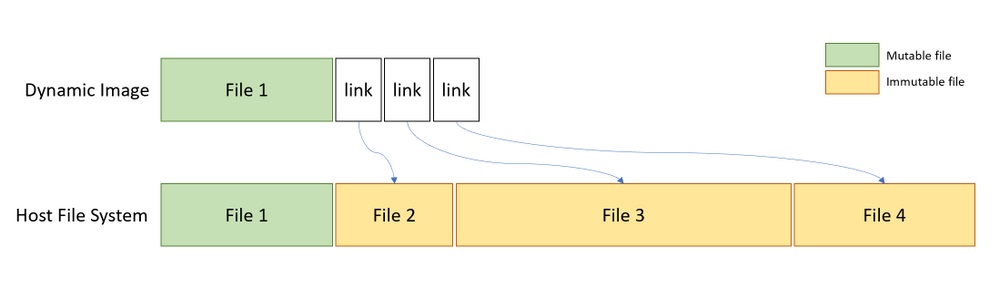
Windows Sandbox doesn’t use a separate Windows 10 image, but instead links to clean/unmodified versions of Windows files. This is what allows the “base image” that is used in a Windows Sandbox environment to be only 100MB, as opposed to several GB, which is what a new Windows installation/image would take. It’s also what enables the higher performance on lower-end devices.
This is clearly a compromise that Microsoft made between maximum security and the need for a usable Sandbox base image that wouldn’t bog down the entire system every time an application is sandboxed. However, sophisticated attackers may be able to take advantage of the fact that this virtual machine image is created out of the original Windows 10 system files, and compromise the Sandbox, in the future. Even so, it shouldn’t be something that will be easy to do.
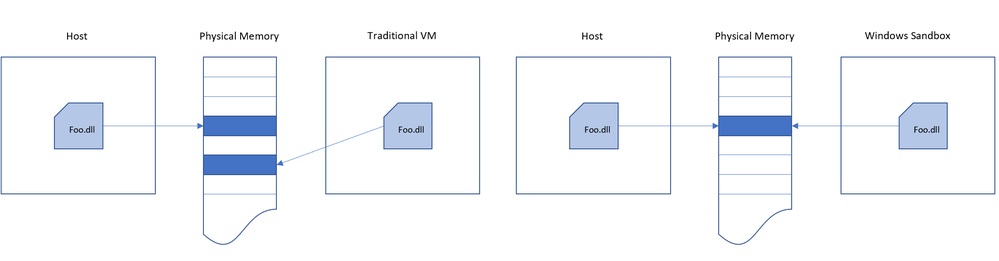
Another “hybrid” design choice that Microsoft made was in how Sandbox shares memory with the host system. The host system will be allowed to reclaim unused memory from the sandboxed applications, something that could one day also be exploited.
The host and the sandboxed applications will also share the same physical memory pages, but Microsoft claimed that this is done in a secure way, so that no secrets are shared. However, this claim will have to be time-tested to be proven right.
Microsoft also integrated a scheduler in the Windows Sandbox, which allows the host to decide when the sandbox should run, creating a more responsive system. The company said that the goal here is to make the sandbox act more like an app rather than another virtual machine, but still have the same (or close to the same) security guarantees as a virtual machine.
After the sandbox environment is created once, a snapshot is taken of the device state, CPU and memory so that it can be started much more quickly later on.
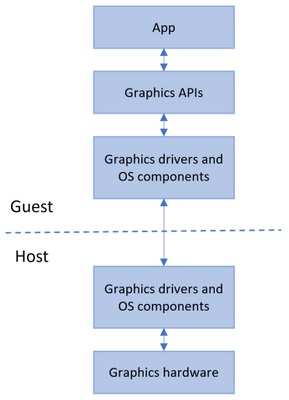
The company worked with graphics ecosystem partners to create drivers (using the Windows Display Driver Model version 2.5) that would allow for the hardware acceleration of the user interfaces within the sandboxes. Normally, virtual machines are not able to access GPUs because they are isolated from the host system.
Only devices that have WDDM 2.5-compatible drivers or newer will be able to use hardware accelerated rendering for sandboxed applications. Others will use the CPU to render these graphics, which should create a slower experience.
Although Windows Sandbox may not offer the exact same security guarantees as virtual machines do, it does seem to come rather close, while still being much more practical to use. Most users will be able to test this themselves in the first half of 2019, when the Windows 10 builder 18305 should arrive.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.