AirVPN Review
AirVPN was the top write-in choice on our VPN survey, and today we're pairing our own test results with your reader assessments.
Interface & Setup
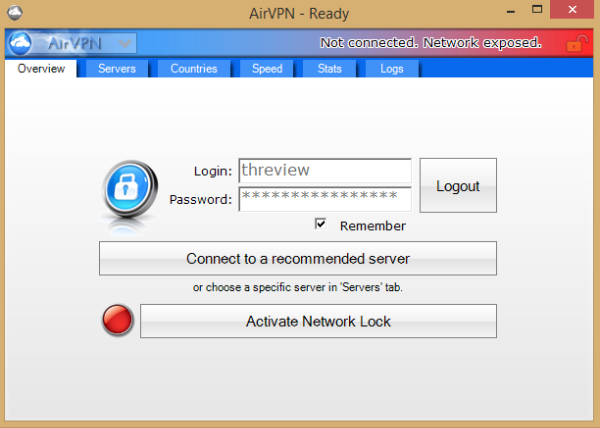
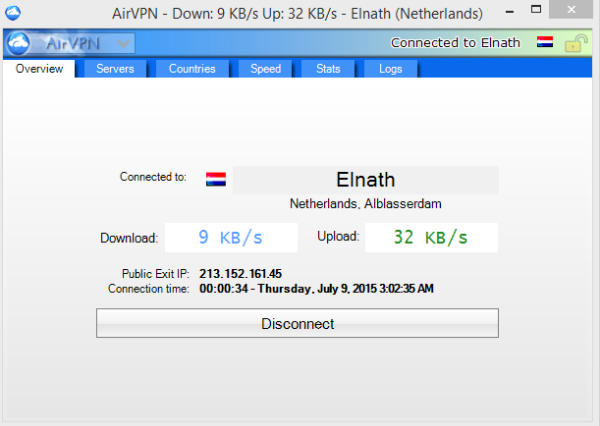
AirVPN offers an open-source client under the GPL license for Windows, Mac OS X and Linux. After you log in to the app, you're given the choice to connect to a recommended random server in the Overview tab or select one from the Servers tab at the top of the application.
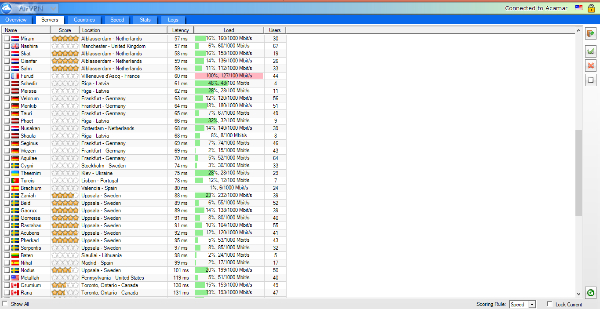
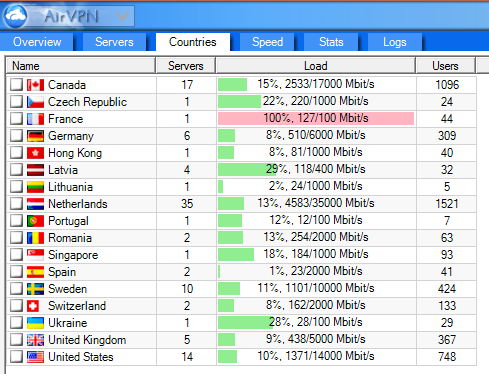
In the Servers tab, you can order the servers by Country, Score, Location (city), Latency, Load or Users, which makes it easy to select exactly the kind of server you want. Then you can double-click on one of them.
Next to the Servers tab, there's a Countries tab as well, where you can whitelist or blacklist certain countries. This can be useful, for instance, if you never want to (randomly) connect to a server in some of those countries. Most are from Europe, a few from Asia, and of course North America (U.S. and Canada). Right now, AirVPN doesn't seem to have servers in the Middle East, Central or South America.
There is also a Speed tab, where you can see a real-time graph of how much bandwidth you're getting at any given time, a Stats tab and a Logs tab, which shows what kind of actions AirVPN is taking in your PC.
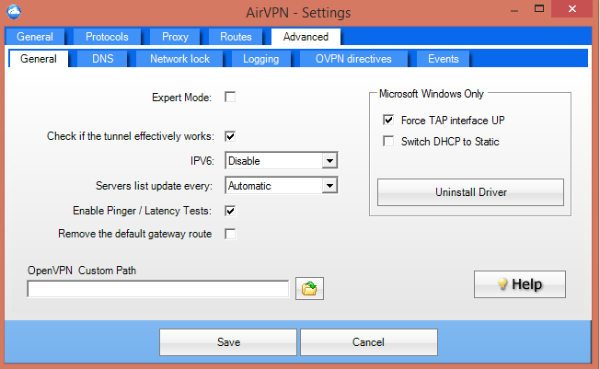
In the top-left corner, when you click on the AirVPN name, you also get a menu with links that seem to open only in Internet Explorer, as well as a Preferences option, where you can further customize your connection settings.
One strong point in AirVPN's care for security is that, even though the recent LogJam paper said up to 66 percent of VPN services could be affected by the vulnerability, AirVPN said that it was never affected by this issue. The company has been using 2048-bit DH primes since its birth in 2010. Then it switched to 4096-bit primes in 2014. It also didn't use the same default primes millions of other sites and services used, which made them most vulnerable to LogJam. Therefore, AirVPN has always been safe against both of the security issues reported in the LogJam paper: using a default prime or one of a small size (under 2048-bit). AirVPN even uses a different 4096-bit for each of its servers.
Another recent paper exposed some security vulnerabilities that could allow DNS hijacking and IPv6 address-leaking by VPN services. AirVPN claimed it wasn't vulnerable to DNS hijacking because the vulnerability only affected an older version of OpenVPN (2.0.9), which the company had already stopped supporting. For those who want to avoid IPv6 address-leaking, the quickest way to do it with AirVPN is to "Activate Network Lock" with a single click. The Network Lock mode also blocks network connections that don't go through AirVPN's secure tunnel (whether you're connected to a server or not) to ensure no other data leaks.
Although not directly related to its VPN service's security, AirVPN's website gets an A+ on Qualys' SSL Labs test, which once again shows the company's commitment to using best-in-class cryptographic protocols. Users would probably be less likely to trust a VPN service that doesn't even use HTTPS for its website, for instance, which is why care for such things matters. Plus, information that identifies users could also be gathered by attackers from those who visit an unencrypted or poorly encrypted VPN website, thus weakening the service's promise of privacy.
AirVPN offers a choice of 17 countries and more than 100 servers, which makes it easier to hide your IP and location. The VPN service also changes your DNS server to DNS servers from other countries so that the domain names you visit aren't resolved by your local ISP, which could help identify you. AirVPN supports the OpenNIC DNS servers, which are part of a project that aims to circumvent censorship and protect people's privacy. Additionally, AirVPN doesn't keep any logs of its users' traffic, so nobody can later hack into its servers or request the logs because the company doesn't have them in the first place.
AirVPN has also taken a strong anti-censorship stance, especially when it comes to what the company considers abusive domain seizures from the past few years by the U.S. ICE (Immigrations and Customs Enforcement) division of the Department of Homeland Security. The VPN service allows all types of protocols, including P2P protocols. It also helps its users get around geo-location bans imposed by some Web services. The circumventing of geo-location restrictions is a major reason why many people use VPN services, so this comes as no surprise. If some ISPs try to disrupt the OpenVPN connections, users of AirVPN could connect over SSH or SSL, which means those ISPs won't be able to differentiate VPN traffic from regular browser traffic.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
mamasan2000 Did not see Astrill mentioned.Reply
Watch that video to get an idea of it's performance (it's very good).
https://www.youtube.com/watch?v=K9bhbEm7JAk
That's what I'd go with. VPN always makes you loose bandwidth, the question is how much. Less the better. -
getochkn On my PC, using the PIA client, I only go down less than 10mb. I get 100mb/s without VPN, 92mb/s with VPN. The problem is trying to get it running on a router, then the speeds drop down to 20-30mbs. Router CPU's just can't handle VPN's with full speed yet. Sucks because I rather my router is VPN'd, then everything that connects goes through that connection. Most VPN's don't give you like 30 accounts and when you have a ton of devices in your house, it sucks. Also things like chromecast, roku's, etc, can't connect to a VPN directly without using a router, then I loose 70mb/s.Reply
Someone needs to make a VPN router. lol. -
Urzu1000 I'm a little surprised to see this article. I just finished a free three-day trial of AirVPN last night.Reply
I've been testing out multiple VPNs over the past year, and I've gone from TorGuard to Private Internet Access, to IPVanish. All three of those were "Meh" in terms of the quality of their services.
Then I tried AirVPN, and no pun intended, I was blown away. It had a proper client, lots and lots of transparency, stability, and best of all, speed.
The other VPNs have been pretty inconsistent speed wise. IPVanish in particular was a bit odd. I did a speed test, and the speeds appeared amazing. However, in practice, I got much less than that on downloads. It could have been coincidence, considering how much that service lost connection, but it still seems a little shady.
All in all though, I'm going to be purchasing a quarterly subscription to AirVPN later today. -
JacFlasche Well Tom's suggestion that PIA was a good service was totally wrong if you are interested in actual P2P speed. As I said in my response to the other article my actual download speed is 15 times faster over iPredator than the damn PIA account I bought on your advice. Unless you do download tests with actual movie files, what does it matter what the speed is, if the service is downgrading or filtering P2P activity. I tried every connection on PIA and the best I could get on a popular movie over P2P was 23Kb compared to over 600 on iPredator.Reply
What do you think the average person uses VPN for? It sure as hell ain't playing games online.
Do a real test with a download over P2P -
Urzu1000 Reply16696463 said:Well Tom's suggestion that PIA was a good service was totally wrong if you are interested in actual P2P speed. As I said in my response to the other article my actual download speed is 15 times faster over iPredator than the damn PIA account I bought on your advice. Unless you do download tests with actual movie files, what does it matter what the speed is, if the service is downgrading or filtering P2P activity. I tried every connection on PIA and the best I could get on a popular movie over P2P was 23Kb compared to over 600 on iPredator.
What do you think the average person uses VPN for? It sure as hell ain't playing games online.
Do a real test with a download over P2P
I can confirm that P2P downloading is extremely fast with AirVPN. They don't throttle it. During my three day trial, I downloaded ~80GB of files via torrents. They weren't the most popular in the world, with only a handful of seeders each, but I got on average around 3-5 MB/s download speed, which leads me to believe they don't throttle it at all. I was lucky get get 800KB/s with the others. -
getochkn Well I guess Tom's isn't interested in the movie torrent piracy aspect of VPN testing.Reply -
ToineF When you click on the AirVPN logo, it doesn't bring you to the right website I think... or is it just me?Reply -
paolob There is a critical mistake in the article, ToineF is right... when you click on the AirVPN logo or in the "Buy" icon you are directed to a totally different VPN web site which has nothing to do with AirVPN! The correct web site is airvpn.orgReply -
Fabrizio76 In more than one week, the article author Lucian Armasu don't read any comment on his article? Unbelievable.Reply