Do The Meltdown and Spectre Patches Affect PC Gaming Performance? 10 CPUs Tested
Gaming With Meltdown And Spectre
Imagine that nearly every PC, server, and mobile phone on the planet was suddenly vulnerable to data theft at the hands of nefarious actors. Then, imagine the exploit responsible for this vulnerability couldn't be detected by antivirus software because it merely took advantage of normal CPU operations.
Although this sounds like a bad movie script, it unfortunately became a known truth during the first few days of 2018.
On January 2nd, The Register exposed Intel's then-secret Meltdown and Spectre vulnerabilities through investigative journalism. But unbeknown to most of the world, Google’s Project Zero researchers, along with two other independent teams, discovered the vulnerabilities 200 days earlier. As a courtesy, the researchers gave Intel, AMD, IBM, Qualcomm, and ARM a grace period to develop mitigations before making their findings public. Those companies, along with developers contributing to Windows and Linux, worked together behind a veil of secrecy for months.
Perhaps understandably, the initial response to The Register's report was chaotic because it preempted that planned group disclosure. What happened after, though, appeared to be a comedy of errors, especially given the amount of time affected companies had to prepare.
Then again, the firms were trying to plug holes that were baked into hardware and software for more than a decade. In fact, nearly every Intel processor since 1995 was found to be vulnerable, so fixing the issues without breaking compatibility proved to be a mind-boggling challenge.
The patches supposedly have performance implications. So now that the industry is a month into cleaning up its mess, we're ready to start assessing the damage. First up: game performance.
The Land Of Patch Confusion
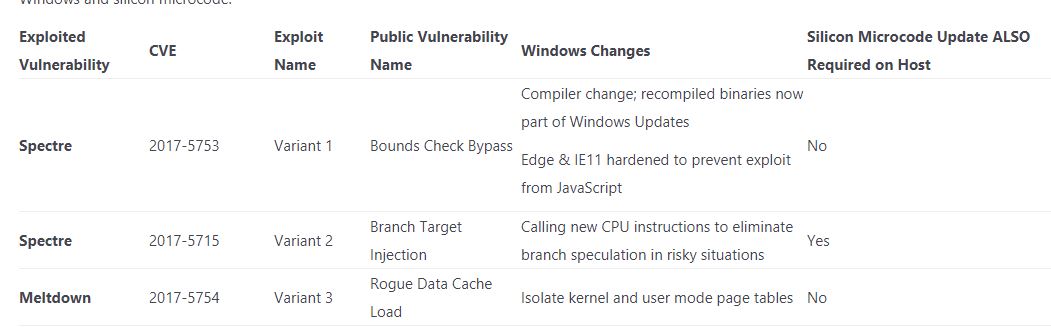
There are two general vulnerabilities in play here, and they're broken up into three categories. Variants 1 and 2 are what we've come to know as Spectre, while Variant 3 is Meltdown. Intel, ARM, and Qualcomm are susceptible to all three, while AMD is only affected by Spectre.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
As we can see, Variant 1 and 3 can be patched in the operating system, while the most nefarious bug, Variant 2, requires both motherboard firmware/microcode and operating system patches.
The initial industry scramble resulted in a flurry of immature and buggy updates. Because the patches weren't distributed as drivers, processor vendors couldn't push them out directly. Instead, they filtered out through Microsoft, Linux-based operating systems, OEMs, and motherboard manufacturers. A rapid sequence of patches, re-patches, and un-patches confused enthusiasts in the know. Everyone else had to have been completely lost.
This is how bad it got: Intel released a motherboard firmware/CPU microcode patch that could cause reboots, system instability, and potential data loss/corruption. Its partners pulled the update. Microsoft published a patch of its own for AMD systems that left some of them unbootable. It, too, had to reverse course, blaming improper documentation from AMD. A fix was released several weeks later.
For now, Intel doesn't have an operating system or microcode patch for Spectre Variant 2. AMD has an OS patch for it, but the company does not have a microcode update to offer. And because microcode patches will have the biggest impact on system performance, today's benchmark results are subject to change.
Intel says it will provide patches for CPUs dating back five years and then move on to older models. Many folks speculate that we may never see patches for those legacy products, though. Both Intel and AMD claim they will have silicon-based mitigations in their next-gen processors. Of course, it remains to be seen how each company works around their security holes without compromising performance.
For now, one thing is for sure: today's patches, particularly those for Spectre Variant 2, affect performance in some workloads. Older CPUs are said to be hit the worst. Microsoft predicts that "some" users with Windows 10 on pre-Broadwell architectures will suffer noticeable slow-downs, while "most" users on Windows 7 and 8.1 on comparable systems will notice a decrease in performance.
Measuring the impact hasn’t been an easy task in our labs. The changing nature of these patches complicates matters: we’ve begun testing several times only to have a patch altered or removed. We’re diligently working on the next round of application benchmarks, and are expanding our scope to include older CPUs. For now, let's focus on gaming with a good selection of recent Ryzen, Kaby Lake-, and Coffee Lake-based processors.
MORE: CPU Security Flaw: All You Need To Know About Spectre
MORE: Best Gaming CPUs
Current page: Gaming With Meltdown And Spectre
Next Page Exploiting The Unexploitable
Paul Alcorn is the Editor-in-Chief for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
madvicker The majority of PC users are going to be on older CPUs than the ones you've tested. These results are only pertinent to the small % of people who have recently bought a CPU / new PC. What about the rest, the majority with older CPUs? That would be a much more useful and interesting analysis for most readers....Reply -
arielmansur Newer cpus don't get a performance penalty.. but older ones sure do get a noticeable one..Reply -
salgado18 Reply20680472 said:The majority of PC users are going to be on older CPUs than the ones you've tested. These results are only pertinent to the small % of people who have recently bought a CPU / new PC. What about the rest, the majority with older CPUs? That would be a much more useful and interesting analysis for most readers....
Last page, third paragraph:
"so it's possible that the impact on older CPUs could be minor as well (game testing on those is in-progress)." -
ddearborn007 HmmmReply
3/4 of all personal computers in the world today are NOT running windows 10. I don't know the exact percentage of gaming systems that are NOT running windows 10, but surely it is substantial.
Why wasn't the performance hit measured on the operating system running 3/4 of all PC's in the world today published immediately? To date, it appears that these numbers are being withheld from the public; the only reason has to be that the performance hit is absolutely massive in many cases.........Oh, and out of the total number of PC's used world wide, "gaming" PC's are a very small percentage, again begging the question of why tests are only being published for windows 10.... -
LORD_ORION Need to test older CPUs... or is this article designed by Intel to stop people from returning recently purchased CPUs.Reply -
RCaron Excellent article Paul!Reply
I have a question.
I read originally that AMD Zen architecture had near-immunity to Spectre variant 2 because a CPU specific code (password if you will) (that changes with each CPU) was required in order to exploit the CPU. Which is why AMD was claiming that Zen was almost immune to Spectre variant 2. Is this not the case?
AMD continues to insist that Spectre 2 is difficult to exploit due to CPU architecture. You left this out, and you continually lumped AMD with Intel with respect to Spectre 2 vulnerability.
This is misleading to your readers, and portrays a bias towards Intel.
https://www.amd.com/en/corporate/speculative-execution -
tripleX Reply20680748 said:Hmmm
3/4 of all personal computers in the world today are NOT running windows 10. I don't know the exact percentage of gaming systems that are NOT running windows 10, but surely it is substantial.
Why wasn't the performance hit measured on the operating system running 3/4 of all PC's in the world today published immediately? To date, it appears that these numbers are being withheld from the public; the only reason has to be that the performance hit is absolutely massive in many cases.........Oh, and out of the total number of PC's used world wide, "gaming" PC's are a very small percentage, again begging the question of why tests are only being published for windows 10....
Global OS penetration for Win 10 and Win 7 is effectively tied.
-
Paul Alcorn Reply20680892 said:Excellent article Paul!
I have a question.
I read originally that AMD Zen architecture had near-immunity to Spectre variant 2 because a CPU specific code (password if you will) (that changes with each CPU) was required in order to exploit the CPU. Which is why AMD was claiming that Zen was almost immune to Spectre variant 2. Is this not the case?
AMD continues to insist that Spectre 2 is difficult to exploit due to CPU architecture. You left this out, and you continually lumped AMD with Intel with respect to Spectre 2 vulnerability.
This is misleading to your readers, and portrays a bias towards Intel.
https://www.amd.com/en/corporate/speculative-execution
From the AMD page (which you linked)
Google Project Zero (GPZ) Variant 1 (Bounds Check Bypass or Spectre) is applicable to AMD processors.
And...
GPZ Variant 2 (Branch Target Injection or Spectre) is applicable to AMD processors.
While we believe that AMD’s processor architectures make it difficult to exploit Variant 2, we continue to work closely with the industry on this threat. We have defined additional steps through a combination of processor microcode updates and OS patches that we will make available to AMD customers and partners to further mitigate the threat.
AMD will make optional microcode updates available to our customers and partners for Ryzen and EPYC processors starting this week. We expect to make updates available for our previous generation products over the coming weeks. These software updates will be provided by system providers and OS vendors; please check with your supplier for the latest information on the available option for your configuration and requirements.
Linux vendors have begun to roll out OS patches for AMD systems, and we are working closely with Microsoft on the timing for distributing their patches. We are also engaging closely with the Linux community on development of “return trampoline” (Retpoline) software mitigations.
AMD hasn't released the microcode updates yet, but to its credit, it's probably better to make sure it is validated fully before release.
-
DXRick Do the OS patches (without the microcode patches) fix the two exploits? If so, why would we even want the Intel patches at all?Reply