Do The Meltdown and Spectre Patches Affect PC Gaming Performance? 10 CPUs Tested
VRMark, 3DMark & AotS: Escalation
Comparison CPUs
VRMark & 3DMark
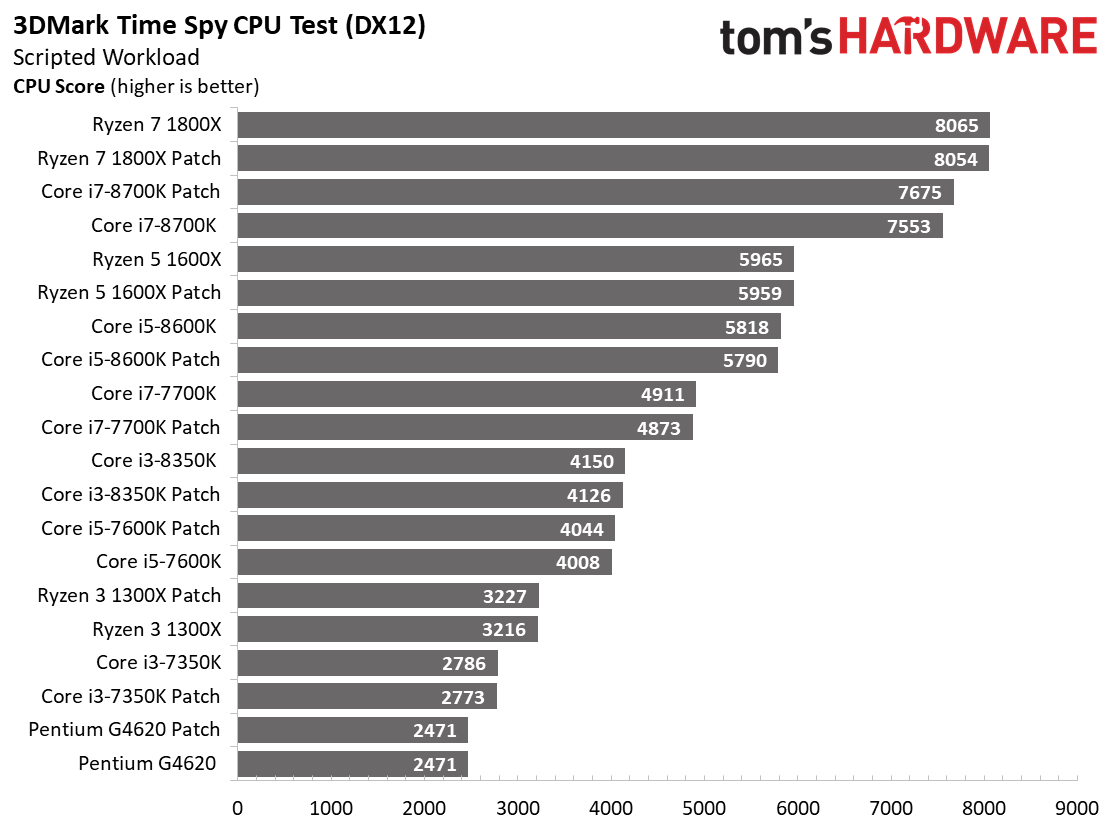
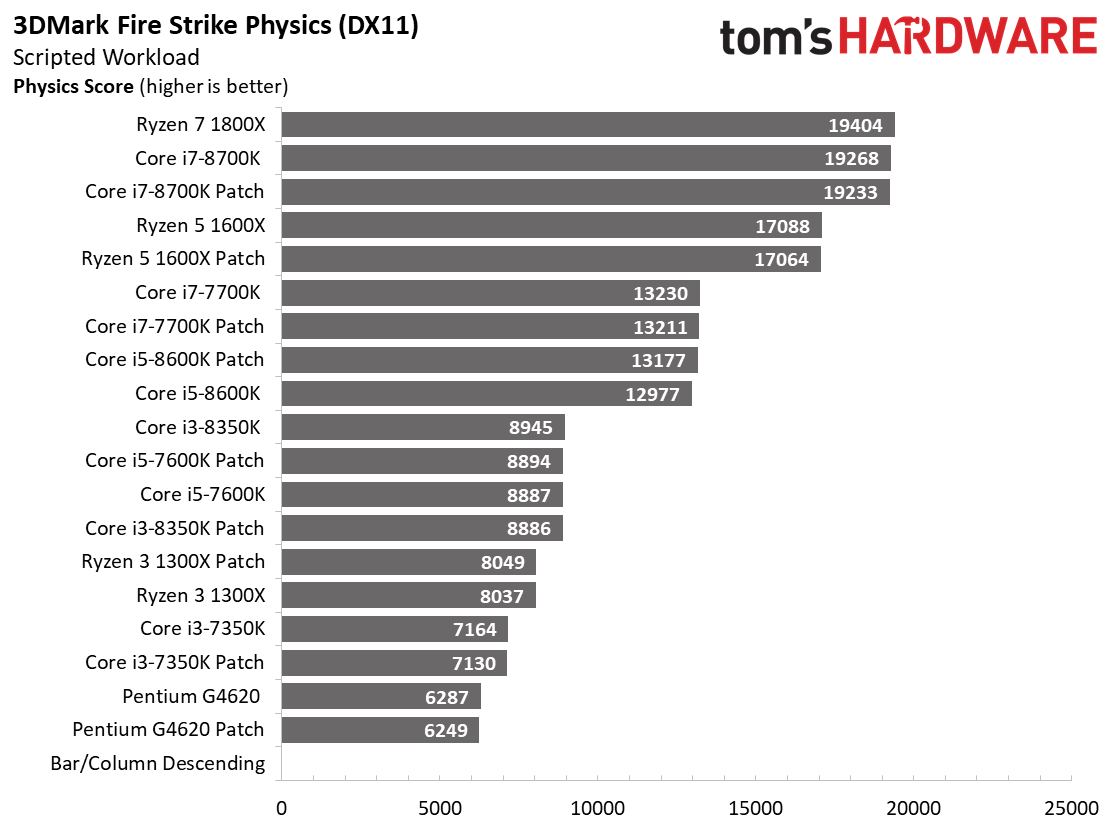
We aren't big fans of using synthetic benchmarks to represent real-world game performance, but 3DMark's DX11 and DX12 CPU tests provide useful insight into the amount of horsepower available to game engines.
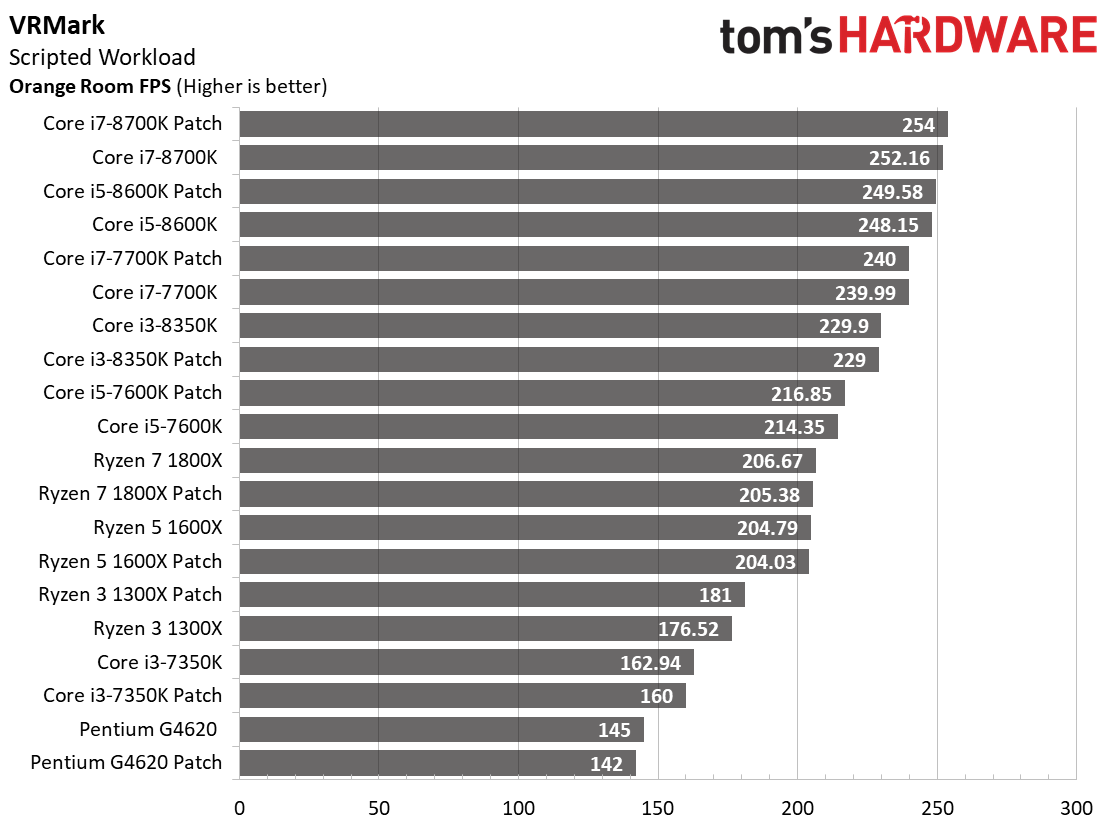
Futuremark's VRMark test lets you gauge your system's suitability for use with the HTC Vive or Oculus Rift, even if you don't currently own an HMD. The Orange Room test is based on the suggested system requirements for current-generation HTC Vive and Oculus Rift HMDs. Futuremark defines a passing score as anything above 109 FPS.
Futuremark specifies a 3% maximum variance between runs if we adhere to normal testing best practices, such as ensuring similar configurations and drivers between systems, allowing the PC to enter an idle state, and conducting tests with the same environmental factors. Of course, there are sub-tests in suites like PCMark 10 that can fall outside the 3% window, at which point we rely upon averages. We didn't encounter those issue with these gaming-focused tests, though.
VRMark reflects a negligible impact from the patches across our entire field of CPUs. At times, the patched operating systems are slightly faster, but these values land within the 3% margin of error. That means those higher results are merely a byproduct of normal run-to-run variability.
The DX11 and DX12 CPU benchmarks respond to core counts and increased parallelism. Frankly, these tests don't show us much of interest. There is some jockeying between patched and unpatched configurations, but the results are uneventful overall.
Ashes of the Singularity: Escalation
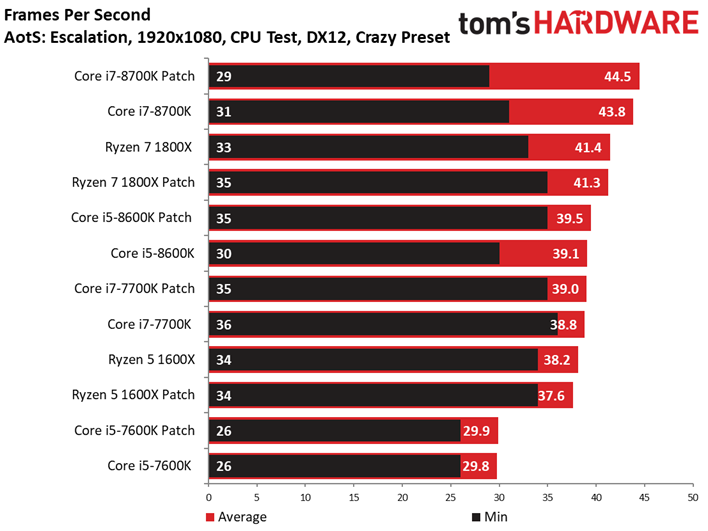
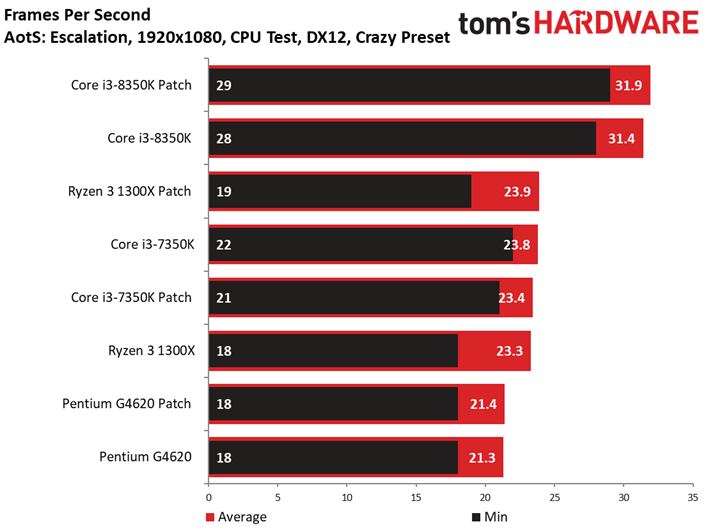
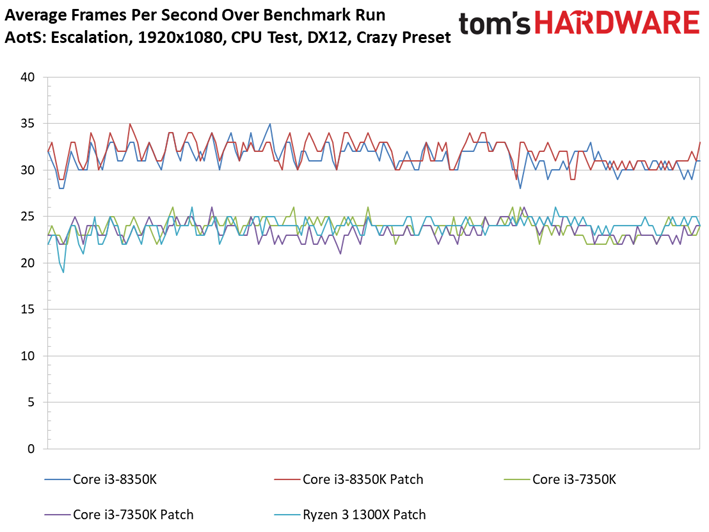
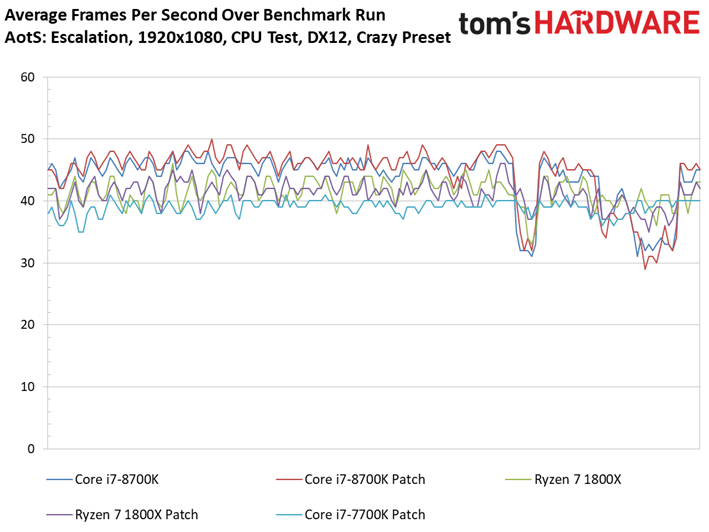
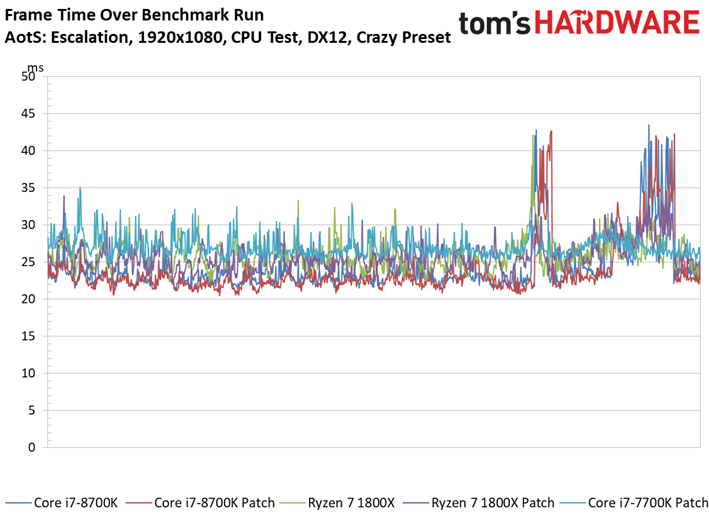
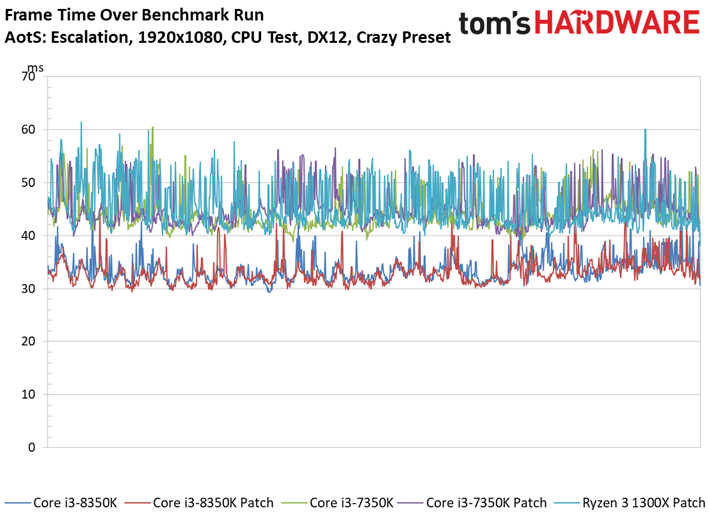
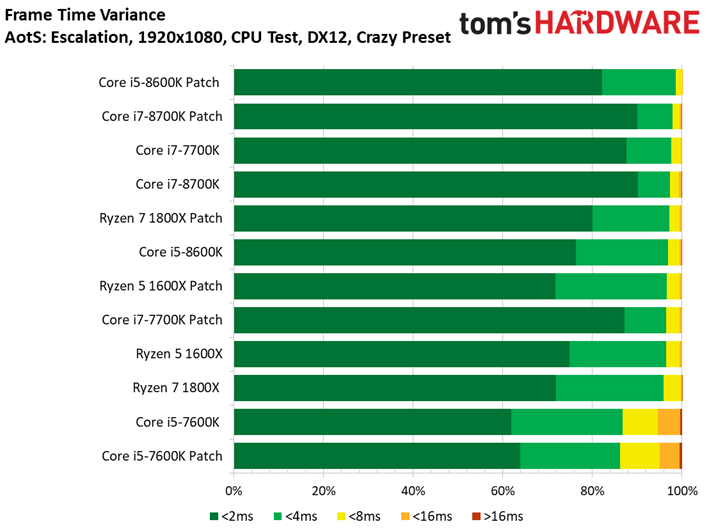
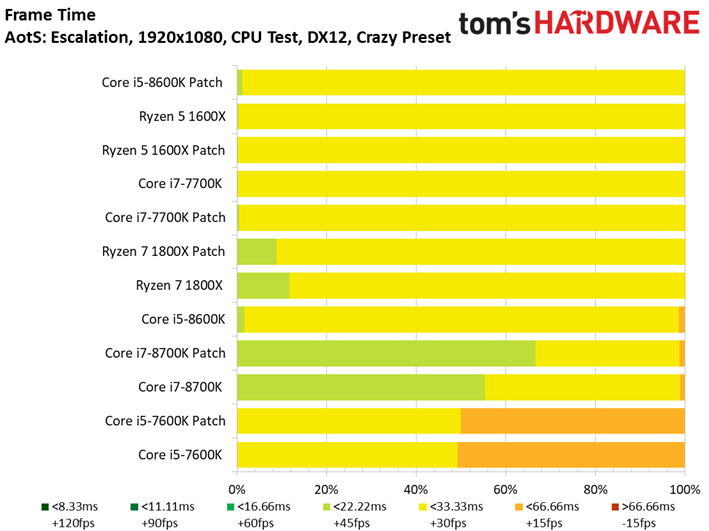
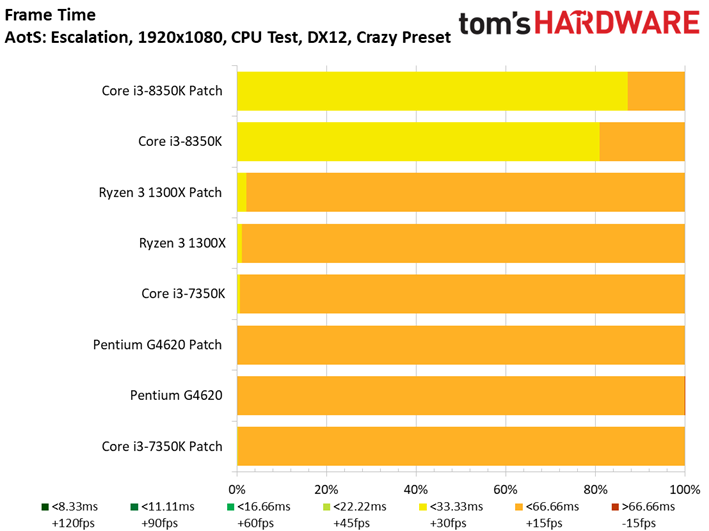
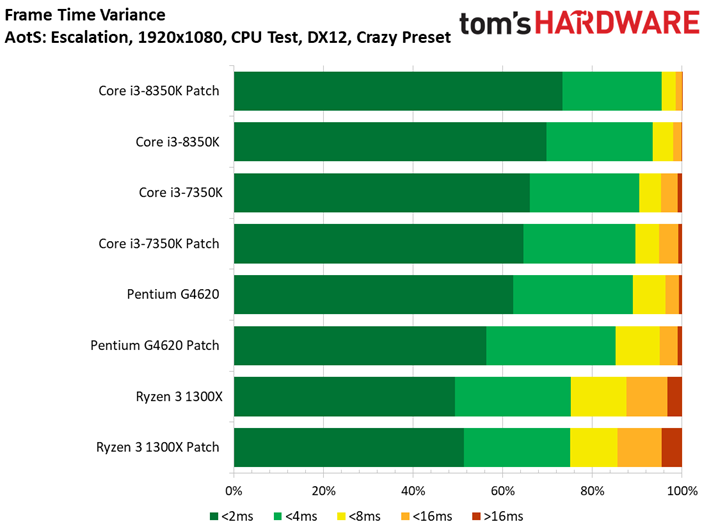
Ashes of the Singularity: Escalation scales nicely with the addition of computational horsepower, so graphics aren't limiting us.
We observe minor variations between the patched and unpatched systems. For instance, a patched Core i7-8700K outpaces the vulnerable configuration. But a 1.6% delta is still within our expectations of normal run-to-run variance. We also don't record any extreme changes to the frame time or frame time variance metrics.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Notice that we split our results into two classes due to the sheer number of tests we ran. Be sure to scroll across the album for our comparison of Core i3, Ryzen 3, and Pentium processors.
MORE: CPU Security Flaw: All You Need To Know About Spectre
MORE: Best Gaming CPUs
Current page: VRMark, 3DMark & AotS: Escalation
Prev Page Test Setup Next Page Civilization VI Graphics & AI, & Dawn of War III
Paul Alcorn is the Editor-in-Chief for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
madvicker The majority of PC users are going to be on older CPUs than the ones you've tested. These results are only pertinent to the small % of people who have recently bought a CPU / new PC. What about the rest, the majority with older CPUs? That would be a much more useful and interesting analysis for most readers....Reply -
arielmansur Newer cpus don't get a performance penalty.. but older ones sure do get a noticeable one..Reply -
salgado18 Reply20680472 said:The majority of PC users are going to be on older CPUs than the ones you've tested. These results are only pertinent to the small % of people who have recently bought a CPU / new PC. What about the rest, the majority with older CPUs? That would be a much more useful and interesting analysis for most readers....
Last page, third paragraph:
"so it's possible that the impact on older CPUs could be minor as well (game testing on those is in-progress)." -
ddearborn007 HmmmReply
3/4 of all personal computers in the world today are NOT running windows 10. I don't know the exact percentage of gaming systems that are NOT running windows 10, but surely it is substantial.
Why wasn't the performance hit measured on the operating system running 3/4 of all PC's in the world today published immediately? To date, it appears that these numbers are being withheld from the public; the only reason has to be that the performance hit is absolutely massive in many cases.........Oh, and out of the total number of PC's used world wide, "gaming" PC's are a very small percentage, again begging the question of why tests are only being published for windows 10.... -
LORD_ORION Need to test older CPUs... or is this article designed by Intel to stop people from returning recently purchased CPUs.Reply -
RCaron Excellent article Paul!Reply
I have a question.
I read originally that AMD Zen architecture had near-immunity to Spectre variant 2 because a CPU specific code (password if you will) (that changes with each CPU) was required in order to exploit the CPU. Which is why AMD was claiming that Zen was almost immune to Spectre variant 2. Is this not the case?
AMD continues to insist that Spectre 2 is difficult to exploit due to CPU architecture. You left this out, and you continually lumped AMD with Intel with respect to Spectre 2 vulnerability.
This is misleading to your readers, and portrays a bias towards Intel.
https://www.amd.com/en/corporate/speculative-execution -
tripleX Reply20680748 said:Hmmm
3/4 of all personal computers in the world today are NOT running windows 10. I don't know the exact percentage of gaming systems that are NOT running windows 10, but surely it is substantial.
Why wasn't the performance hit measured on the operating system running 3/4 of all PC's in the world today published immediately? To date, it appears that these numbers are being withheld from the public; the only reason has to be that the performance hit is absolutely massive in many cases.........Oh, and out of the total number of PC's used world wide, "gaming" PC's are a very small percentage, again begging the question of why tests are only being published for windows 10....
Global OS penetration for Win 10 and Win 7 is effectively tied.
-
Paul Alcorn Reply20680892 said:Excellent article Paul!
I have a question.
I read originally that AMD Zen architecture had near-immunity to Spectre variant 2 because a CPU specific code (password if you will) (that changes with each CPU) was required in order to exploit the CPU. Which is why AMD was claiming that Zen was almost immune to Spectre variant 2. Is this not the case?
AMD continues to insist that Spectre 2 is difficult to exploit due to CPU architecture. You left this out, and you continually lumped AMD with Intel with respect to Spectre 2 vulnerability.
This is misleading to your readers, and portrays a bias towards Intel.
https://www.amd.com/en/corporate/speculative-execution
From the AMD page (which you linked)
Google Project Zero (GPZ) Variant 1 (Bounds Check Bypass or Spectre) is applicable to AMD processors.
And...
GPZ Variant 2 (Branch Target Injection or Spectre) is applicable to AMD processors.
While we believe that AMD’s processor architectures make it difficult to exploit Variant 2, we continue to work closely with the industry on this threat. We have defined additional steps through a combination of processor microcode updates and OS patches that we will make available to AMD customers and partners to further mitigate the threat.
AMD will make optional microcode updates available to our customers and partners for Ryzen and EPYC processors starting this week. We expect to make updates available for our previous generation products over the coming weeks. These software updates will be provided by system providers and OS vendors; please check with your supplier for the latest information on the available option for your configuration and requirements.
Linux vendors have begun to roll out OS patches for AMD systems, and we are working closely with Microsoft on the timing for distributing their patches. We are also engaging closely with the Linux community on development of “return trampoline” (Retpoline) software mitigations.
AMD hasn't released the microcode updates yet, but to its credit, it's probably better to make sure it is validated fully before release.
-
DXRick Do the OS patches (without the microcode patches) fix the two exploits? If so, why would we even want the Intel patches at all?Reply


