The Rise Of Cryptojacking And How To Stop It
Over the last few months, we've seen multiple reports of websites using cryptocurrency mining scripts that load along with the website and use visitors' CPU cycles to mine various cryptocurrencies. (Some used these tools intentionally; others did not.) This practice is called cryptojacking—a combination of "cryptocurrency" and "hijacking"—and now another tool has been caught engaging in this moneymaking scheme.
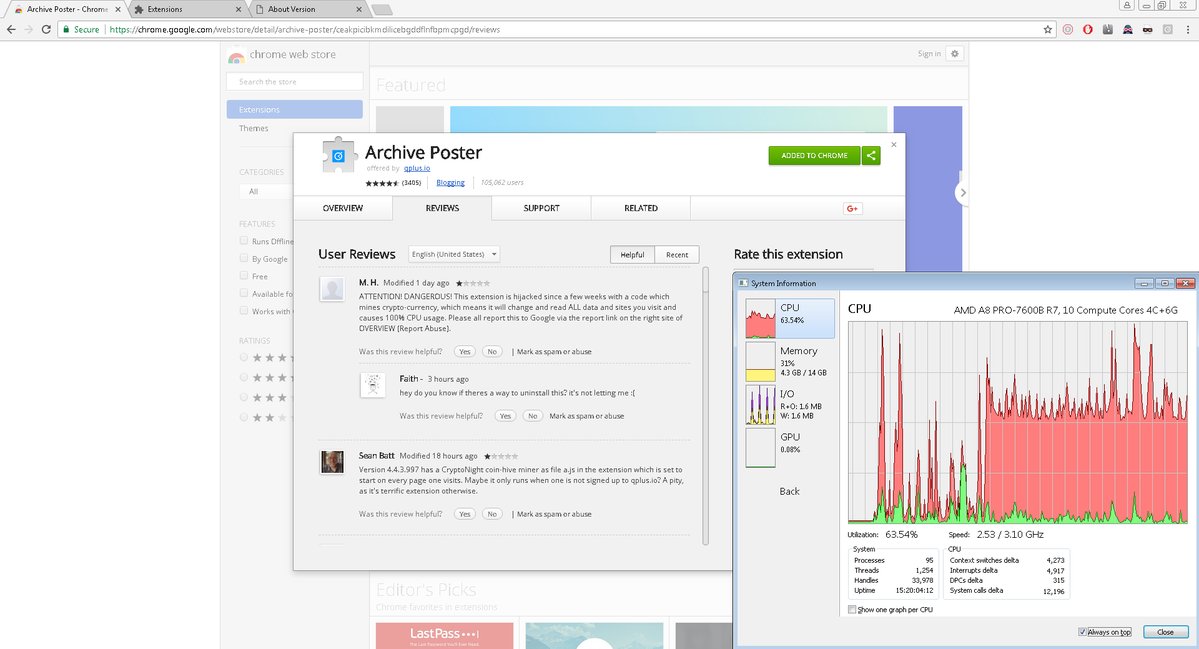
The latest report involves a relatively popular Chrome extension for blogging with over 100,000 users and 3,400 reviews, called “Archive Poster,” which seems to have recently added a crypto-mining script that constantly uses the victims’ CPU resources.
Archive Poster’s Cryptojacking
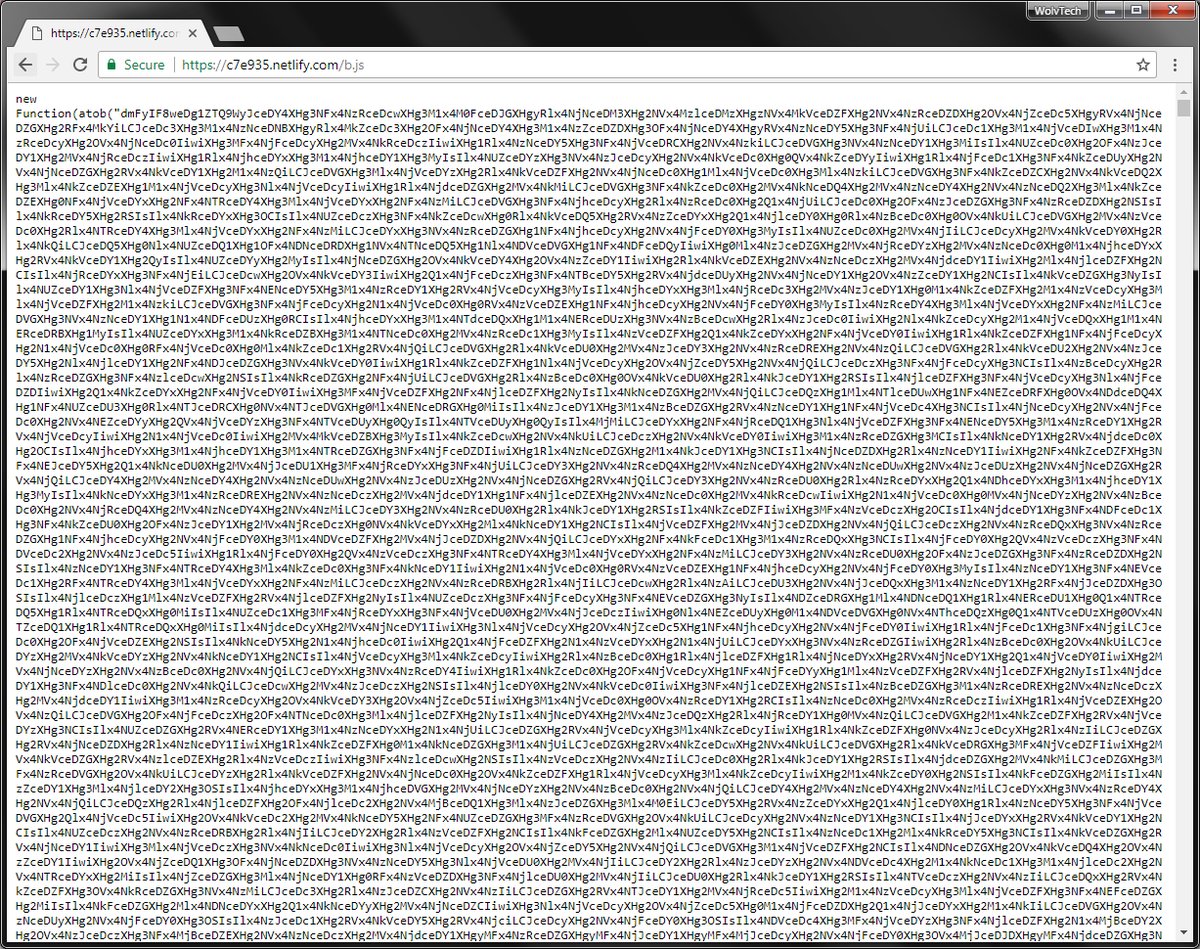
Archive Poster’s cryptojacking was first reported by the “Bad Packets Report” Twitter channel, which covers all the latest cryptojacking security issues. The author of the Archive Poster extension seems to have obfuscated the cryptojacking script to hide it from users and other programmers who may have wanted to take a look at its source code.
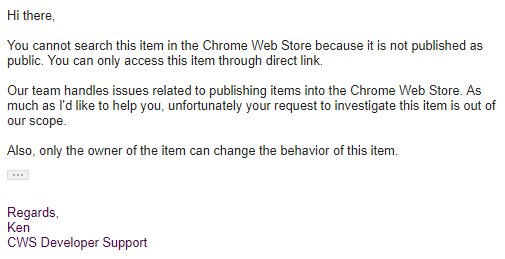
Troy Mursch, who is behind the Bad Packets Twitter account, said that he reported the issue to Google, but Google’s support team ignored it because the extension seems to have been disabled from being found through the store’s search functionality. The extension can only be obtained if you have the direct link.
Back in October, another Chrome extension was caught cryptojacking, but Google eventually removed it from the store after its discovery. As these occurrences become more common, Google may have start looking for ways to prevent cryptojacking extensions from appearing in the store in the first place.
Cryptojacking As A Positive Form Of Monetization?
Some have argued that using scripts to mine cryptocurrencies when people visit websites could be a legitimate form of monetization that could help websites do away with ads. However, this should come with the caveat that website operators must let visitors know that they are using the CPU resources as the visitors browse the website.
The Coinhive JavaScript miner seems to have started the whole recent cryptojacking craze, because it made it easy for website operators as well as more malicious actors to monetize websites and browser extensions. The original authors may have had no malicious intent, but this is how their code was eventually used.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The Coinhive authors eventually developed AuthedMine, which requires permission from the websites’ visitors before it’s enabled. However, this new version of Coinhive doesn’t seem to have caught on with website operators nearly as much as the original did.
It’s also not quite clear how effective legitimate cryptojacking would be in the long-term as an ad network-replacement for multiple reasons. One is that the difficulty of mining cryptocurrencies tends to increase steadily over time, which means whoever is doing the cryptojacking will need an increasing number of CPU resources. Therefore, cryptojacking may soon only be worth it for websites and extensions with millions of users. Coinhive mines the privacy-focused Monero cryptocurrency primarily because it also happens to be one of the few cryptocurrencies to allow efficient mining with a CPU, but this efficiency should gradually decrease in the future.
The other reason is that if the website or extension developers tell users how they are using their CPU cycles, then users may stop using that website or extension. The more CPU resources the website would use, the more likely it will be for it to lose its loyal visitors.
Right now, cryptojacking seems to be used mainly in a malicious/hidden way anyway. This means that either the browser vendors themselves will develop built-in protections against this kind of scripts, or users will take the matters in their own hands and block all forms of cryptojacking.
How To Stop Cryptojacking
In regards to browser extensions, the best way to protect yourself is simply to pay attention to either your operating system’s Task Manager functionality or Chrome's own Task Manager, from which you can see the CPU and memory usage for all tabs and extensions.
Ideally, browser vendors such as Google and Mozilla will develop means of automatically blocking extensions that mine cryptocurrency from even appearing in their stores.
When it comes to cryptojacking websites, blocking cryptojacking may already be a little easier, as you can now use extensions such as MinerBlock (Chrome) or No Coin (Firefox and Chrome) to automatically block the most common JavaScript cryptocurrency miners. Of course blocking JavaScript either from the browser settings or through extensions such as uMatrix and NoScript should also work, but most users may find that too much of a hassle.
Unlike JavaScript miners, which mainly have to rely on the CPU, native miners could also use the GPU for one or two orders of magnitude better mining performance. They also benefit from supporting many more cryptocurrencies, which gives malicious actors much more flexibility in choosing the most profitable cryptocurrencies. They could choose anything from Ethereum to brand new coins that benefit from GPU mining and have high potential to rise dramatically in value, as many new cryptocurrencies have done in the past.
This is why we may soon start seeing the threat of ransomware take a back seat to cryptojacking. Unlike ransomware, which requires some “customer service” of sorts, in order to manually unlock people’s computers, cryptojacking is completely automatic after the malware infects the machine.
Otherwise, the infection vectors should remain largely the same. That also means that some of the tools used to prevent ransomware could also work against cryptojacking. That could include anything from Google’s Safe Browsing service, blocking domains known to deliver cryptojacking malware, to users installing various general anti-malware solutions that worked against ransomware and could also work against cryptojacking malware.
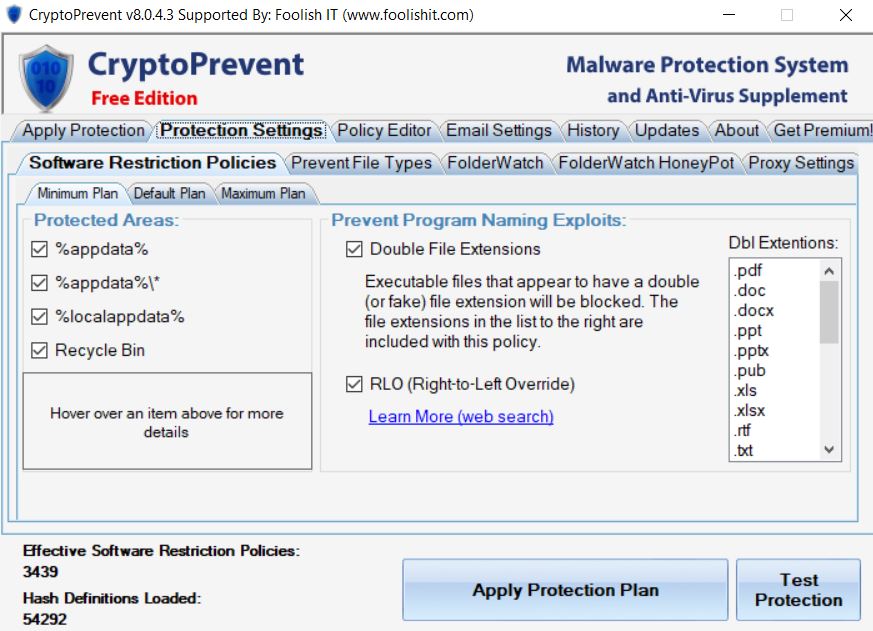
On Windows 7 Pro and newer, you could use third-party tools that use Software Restriction Policies (SRP) such as CryptoPrevent, to block the common folders where ransomware and other malware like it likes to install itself.
On Windows 10 Creator’s Update and newer, that could mean using Microsoft’s Controlled Folder Access feature to restrict access to common folders such as Downloads and %appdata%, where ransomware and other malware typically download or install themselves.
As cryptojacking using native miners becomes more common, we should also see antivirus and anti-malware developers start to build various tools against this kind of threat.
Updated, 1/06/2018, 7:40am PT: We updated the post to include the name of the Bad Packets Twitter account owner.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
bit_user Browsers should simply idle non-visible tabs & minimized windows by default, as well as throttling scripts on visible tabs. Anything which lowers the mining rate should help. If it gets dropped low enough, I doubt most of these actors would even bother.Reply
BTW, even if an Android app is only accessible via direct link, Google should still at least provide a warning for those apps which have received numerous complaints. They'd hardly have to lift a finger to do that much.
-
Solandri I always thought this sort of thing was better fought by polluting the database (poisoning the well). To discourage mining by prevention, you need to get the prevention measures installed on most of the computers out there. In contrast, a database polluting extension (returns false data) can be effective when installed on only a tiny fraction of the computers out there. If it detects mining and returns a false positive (i.e. pretends it found a bitcoin when it didn't), eventually the miner's database gets filled with so many fakes it takes as much effort to determine the fakes from the real results as mining the coins themselves. Likewise, if marketers' databases are polluted with fake results, it degrades the value of their database, possibly to the point of uselessness. Eventually it becomes not worth it to try this sort of thing on other people's computers.Reply -
studmoose Huh, I wonder if I have a cryptominer in my Firefox. It runs at neat 100% while I'm not even doing anything. Process Explorer shows it's in a Forefox.exe or other Firefox module.Reply -
bit_user Reply
We're not talking about malware that's infected your computer. For that, use a traditional virus scanner.20536307 said:Huh, I wonder if I have a cryptominer in my Firefox. It runs at neat 100% while I'm not even doing anything. Process Explorer shows it's in a Forefox.exe or other Firefox module.
What we're talking about is something that should run when viewing certain pages or sites. Even before this trend started, I would find certain sites just consume lots of CPU. Probably running an ad blocker would help, but I just manually closed tabs until the offender is eliminated.
Anyway, maybe this will help you narrow-down what's spiking your CPU utilization:
https://support.mozilla.org/en-US/kb/firefox-uses-too-many-cpu-resources-how-fix -
USAFRet Reply20536719 said:I don't get why this is a HUGE problem.
For one, this:
https://www.bleepingcomputer.com/news/security/chrome-extension-with-100-000-users-caught-pushing-cryptocurrency-miner/
No big deal right?
Yeah, it is.
Sucking up your electricity and PC resources, for their gain.
Like if your neighbor ran a garden hose from your outside tap, over to his house.
No big deal, until you get your next water bill. -
mrmez Safari has had a feature for a number of years "Stop plug-ins to save power", which is enabled by default I think.Reply -
lperreault21 Reply20536884 said:20536719 said:I don't get why this is a HUGE problem.
For one, this:
https://www.bleepingcomputer.com/news/security/chrome-extension-with-100-000-users-caught-pushing-cryptocurrency-miner/
No big deal right?
Yeah, it is.
Sucking up your electricity and PC resources, for their gain.
Like if your neighbor ran a garden hose from your outside tap, over to his house.
No big deal, until you get your next water bill.
alraight, that makes more sense.
But, The should at least ask first.
-
USAFRet Reply20538549 said:
alraight, that makes more sense.
But, The should at least ask first.
If they "asked", in language that made it clear as to what they were doing, no one would say Yes.
So they sneak it in. -
lperreault21 Reply20538572 said:20538549 said:
alraight, that makes more sense.
But, The should at least ask first.
If they "asked", in language that made it clear as to what they were doing, no one would say Yes.
So they sneak it in.
true