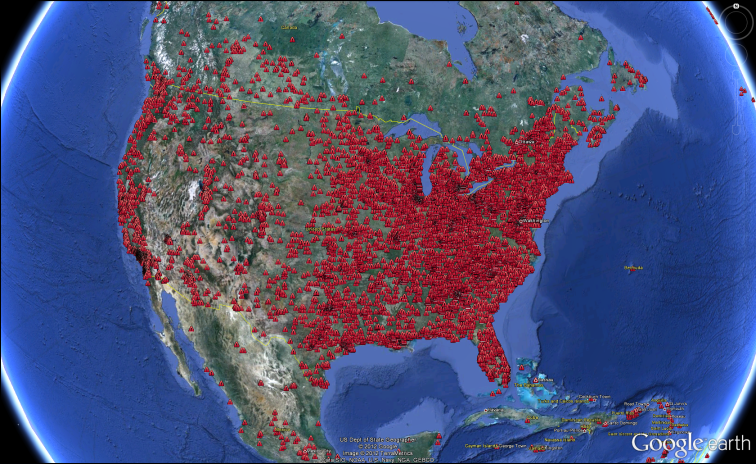
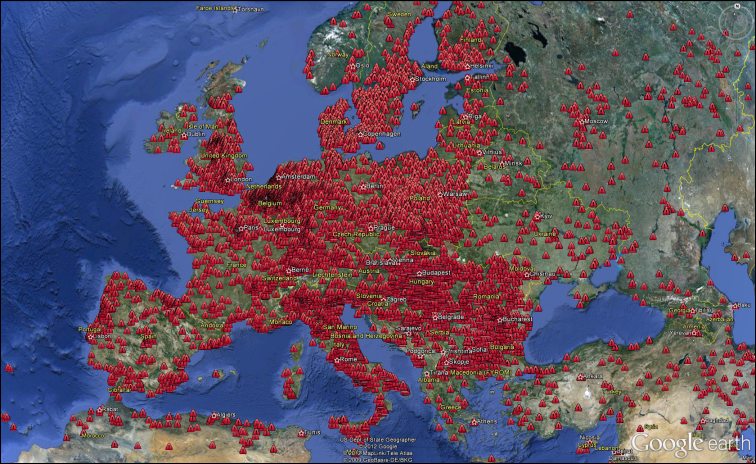
The ZeroAccess Botnet Visualized on Google Earth
F-Secure has posted an impressive map of the ZeroAccess botnet as it spreads across North America and Europe.
According to the security firm, ZeroAccess has infected millions of computers globally and the KML files for Google earth currently show only 139,447 bot locations in the two provided screenshots. F-Secure is providing the KML as well as CSV files for download.
ZeroAccess is a fast spreading botnet that is based on a kernel-mode rootkit that runs on 32-bit and 64-bit Windows systems and acts as a delivery platform for other malware. The main infection technique is to tricking users on social platforms into running an executable file, often under the promise of free software. Sophos published a detailed description of ZeroAccess and the way it works.
Contact Us for News Tips, Corrections and Feedback
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Wolfgang Gruener is an experienced professional in digital strategy and content, specializing in web strategy, content architecture, user experience, and applying AI in content operations within the insurtech industry. His previous roles include Director, Digital Strategy and Content Experience at American Eagle, Managing Editor at TG Daily, and contributing to publications like Tom's Guide and Tom's Hardware.
-
Wamphryi It would be helpful if the article contained information on how to determine infection and in the event of infection what to do about it.Reply -
Pennanen guru_urugI must not be the only one who looked at those images and thought "SkyNet!"First thing that came to my mind was google chrome.Reply -
Gundam288 luciferanoBotnet this, botnet that... They seem very popular with the bad hackers lately.You know what they say, only the bad ones get caught.Reply
The main infection technique is to tricking users on social platforms into running an executable file
And I still remember when some one was convinced to delete his system32 folder to increase his FPS in Counter-Strike....
Are people getting smarter or dumber? I wonder sometimes... -
A Bad Day gundam288And I still remember when some one was convinced to delete his system32 folder to increase his FPS in Counter-Strike....Are people getting smarter or dumber? I wonder sometimes...Reply
One of my friends compressed his boot folder, or deleted it.
His computer didn't boot again...
(If people had as much trouble with books as computers back in the medieval era): http://www.youtube.com/watch?feature=player_embedded&v=pQHX-SjgQvQ -
A Bad Day EDIT: I also forgot to mention,Reply
There's always an equilibrium of stupidity, from Harvard professors to CEOs to average joes. -
thezooloomaster WamphryiIt would be helpful if the article contained information on how to determine infection and in the event of infection what to do about it.Reply
The "Bleeping Computer" are one of the best places to go for that. Getting rid of malware is rarely easy. -
alidan WamphryiIt would be helpful if the article contained information on how to determine infection and in the event of infection what to do about it.Reply
if its based on a root kit than there is basicly no way for the average computer user to figure it out.
granted, using an up to date linux cd boot made specifically for the purposes of diagnostics may be able to figure this crap out, i dont remember its name but i know there was one a while ago that i had on a cd as an in case. -
luciferano alidanif its based on a root kit than there is basicly no way for the average computer user to figure it out.granted, using an up to date linux cd boot made specifically for the purposes of diagnostics may be able to figure this crap out, i dont remember its name but i know there was one a while ago that i had on a cd as an in case.Reply
There are several Linux boot disks that can do that.