Cybersecurity
Latest about Cybersecurity

Tile exploit could let stalkers follow you with your own tracker
By Nathaniel Mott last updated
Georgia Institute of Technology researchers found design flaws in Tile location trackers that can be abused to stalk their owners.

Teen suspected of holding $1.8 million in bitcoin from hacking Vegas casinos is out on bail
By Sunny Grimm published
The youth is accused of contributing to a Vegas Strip cyberattack that cost casinos over $115 million.

SlimeMoldCrypt relies on gloopy living organism’s ever-changing network of tendrils for its dynamic, biological, encryption engine
By Mark Tyson published
A new device hopes to harden cryptography by leveraging icky-sounding organisms called slime molds.
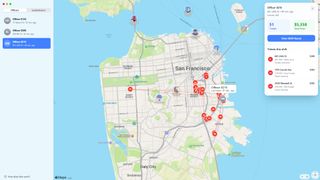
Entire website dedicated to helping San Francisco motorists avoid parking tickets goes live
By Jowi Morales published
This web app tracks the locations of issued parking tickets in real time using the City of San Francisco's own parking ticket payment portal.

Twitch streamer raising money for cancer treatment has funds stolen by malware-ridden Steam game
By Nathaniel Mott published
Twitch streamer "RastalandTV" had $32,000 worth of cryptocurrency stolen via malware hidden in a Steam game.

Hackers attack Europe’s automatic flight check-in systems
By Luke James published
An incident at Collins Aerospace shut down the cloud back-end for its cMUSE platform this weekend, crippling kiosks and forcing manual fallback at Heathrow, Berlin, and Brussels.

$115 million ransomware hacker arrested over extortion attacks
By Jon Martindale published
The British national is accused of hacking over 120 computer networks and attacking close to 50 different U.S. entities.

Pixie Dust wireless exploit lingers 11 years after initial disclosure
By Nathaniel Mott published
Welcome to Never-patched-land.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

