Trend Micro Finds MediaServer Vulnerability In Android, Affecting Most Devices
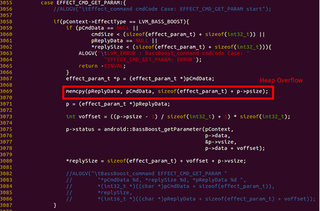
Security researchers from Trend Micro uncovered yet another media-related vulnerability, this time in the MediaServer program. Attackers can exploit this vulnerability to run arbitrary code on the devices, giving it the same permissions as the MediaServer program itself.
The vulnerability affects all Android versions from Android 2.3 to Android 5.1.1, but Trend Micro stated that Google has already pushed a fix to the Android Open Source Project on August 1. Trend Micro made Google aware of the bug on June 19.
The security company also said that it hasn't seen any exploits of this vulnerability in the wild so far. However, knowing the big problem the Android ecosystem has with updates, only a small part of the existing devices will fix this vulnerability in the future, while most of the others will remain vulnerable to it.
The attackers can use the vulnerability to ask Android users to install an app, which doesn't require any permission, making the user think it's safe. The attack can be fully controlled by the malicious hacker, who can start or stop it at any time.
The attacker's code gets the same permissions as the MediaServer program, which has the ability to perform many media-related tasks. This includes taking pictures, reading video files, recording video, all of which can put the user's privacy at risk.
According to the Trend Micro researchers, the attack can be quite stealthy, making it hard to detect and the attacker may not even trigger the attack for months after the device is infected.
The best course of action against this bug would be to upgrade your device once the patch is ready from your phone's manufacturer. If no such patch is received or you don't want to wait until then, Trend Micro's Mobile Security app will also detect malicious apps that want to take advantage of this vulnerability.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
The company also said users could reboot their devices in safe mode, and uninstall the malicious app from there if they have already detected it, but this method may prove too difficult for most users.
Follow us @tomshardware, on Facebook and on Google+.
-
targetdrone ReplyThe best course of action against this bug would be to upgrade your device once the patch is ready from your phone's manufacturer. If no such patch is received or you don't want to wait until then, Trend Micro's Mobile Security app will also detect malicious apps that want to take advantage of this vulnerability.
Well that's just great because T-Moible isn't updating the Note II any more and I'm not buying a Note 5 ever. Also the link to Trend Micro says that software is not available for download to any of my Android device's country, which is strange because I'm in the US. So again, Android uses are left unprotected with no way to fix the problem. With all the hate Microsoft gets, at least when they fix a problem. everyone(with a legit license) can download the fix and are not dependent on OEMs to release their own fix customized for a specific set of hardware.
Most Popular





