Welcome to Your Worst Malware Nightmare
Malware Defined
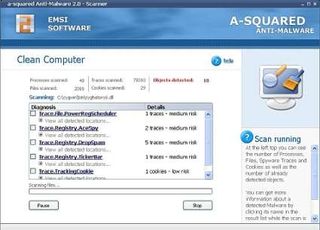
a-Squared's anti-malware product
Malware is an umbrella term that classifies many forms of behavior observed in different kinds of software, all of which share a common modus operandi: disruption, infiltration or subversion of a vulnerable computer system. Such malicious software can be a simple prank (such as the Melissa virus), or more hostile (Apache worm) capable of operating on individual targets or entire networks at a time.
Viruses, worms, Trojan horses, rootkits, browser hijackers, backdoors, botnets, loggers, spam proxies and adware programs make up the bulk of malware that computer users are likely to encounter nowadays. Most arrive by way of email attachments from friends or strangers, borrowed and copied media, as companion or Trojan software alongside (or within) other programs and from scouring the Internet (particularly its less well-patrolled precincts, of which there are many). Each form of malware has its own special function, which ranges from disrupting system resources, to subverting user control, to eavesdropping on sensitive user activities or data. Spyware and adware are two prime categories of malware that often violate user privacy.
Malware has proliferated into a category of software that is sometimes difficult to describe correctly, identify accurately and remove completely. Spyware removal is perhaps the hardest task even when offending items may be clearly and readily identified, because it will continue to reassert its presence following any reboot of a system subsequent to a failed clean-up attempt. Rootkits are another problem - they usually follow behind successful exploitations, or as companion programs to other forms of malware, and are extremely tricky to remove thoroughly (enough so that many experts advocate a "wipe the drive, reinstall the OS and restore a backup" as a more reliable palliative).
Certain types of malware may do one or more of the following:
- call out from your computer (auto-dialer)
- call into your computer (remote control)
- collect your private data (spyware)
- display unwanted data (adware)
- monitor keystrokes (keyloggers)
- ensure stealthy reentry and total control (rootkit)
New variations and combinations of these and other techniques appear in the wild with increasing frequency. Two of the most prominent forms of malware are covered in the next paragraphs.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
Most Popular

